Stonesoft StoneGate User manual

STONEGATE 5.2
FIREWALL/VPN REFERENCE GUIDE
FIREWALL
VIRTUAL PRIVATE NETWORKS

2
Legal Information
End-User License Agreement
The use of the products described in these materials is subject to the then current end-user license agreement, which can be found at
the Stonesoft website:
www.stonesoft.com/en/support/eula.html
Third Party Licenses
The StoneGate software includes several open source or third-party software packages. The appropriate software licensing information for
those products at the Stonesoft website:
www.stonesoft.com/en/support/third_party_licenses.html
U.S. Government Acquisitions
If Licensee is acquiring the Software, including accompanying documentation on behalf of the U.S. Government, the following provisions
apply. If the Software is supplied to the Department of Defense (“DoD”), the Software is subject to “Restricted Rights”, as that term is
defined in the DOD Supplement to the Federal Acquisition Regulations (“DFAR”) in paragraph 252.227-7013(c) (1). If the Software is
supplied to any unit or agency of the United States Government other than DOD, the Government’s rights in the Software will be as
defined in paragraph 52.227-19(c) (2) of the Federal Acquisition Regulations (“FAR”). Use, duplication, reproduction or disclosure by the
Government is subject to such restrictions or successor provisions.
Product Export Restrictions
The products described in this document are subject to export control under the laws of Finland and the European Council Regulation (EC)
N:o 1334/2000 of 22 June 2000 setting up a Community regime for the control of exports of dual-use items and technology (as
amended). Thus, the export of this Stonesoft software in any manner is restricted and requires a license by the relevant authorities.
General Terms and Conditions of Support and Maintenance Services
The support and maintenance services for the products described in these materials are provided pursuant to the general terms for
support and maintenance services and the related service description, which can be found at the Stonesoft website:
www.stonesoft.com/en/support/view_support_offering/terms/
Replacement Service
The instructions for replacement service can be found at the Stonesoft website:
www.stonesoft.com/en/support/view_support_offering/return_material_authorization/
Hardware Warranty
The appliances described in these materials have a limited hardware warranty. The terms of the hardware warranty can be found at the
Stonesoft website:
www.stonesoft.com/en/support/view_support_offering/warranty_service/
Trademarks and Patents
The products described in these materials are protected by one or more of the following European and US patents: European Patent Nos.
1065844, 1189410, 1231538, 1259028, 1271283, 1289183, 1289202, 1304849, 1313290, 1326393, 1379046, 1330095,
131711, 1317937 and 1443729 and US Patent Nos. 6,650,621; 6 856 621; 6,885,633; 6,912,200; 6,996,573; 7,099,284;
7,127,739; 7,130,266; 7,130,305; 7,146,421; 7,162,737; 7,234,166; 7,260,843; 7,280,540; 7,302,480; 7,386,525; 7,406,534;
7,461,401; 7,721,084; and 7,739,727 and may be protected by other EU, US, or other patents, or pending applications. Stonesoft, the
Stonesoft logo and StoneGate, are all trademarks or registered trademarks of Stonesoft Corporation. All other trademarks or registered
trademarks are property of their respective owners.
Disclaimer
Although every precaution has been taken to prepare these materials, THESE MATERIALS ARE PROVIDED "AS-IS" and Stonesoft makes
no warranty to the correctness of information and assumes no responsibility for errors, omissions, or resulting damages from the use of
the information contained herein. All IP addresses in these materials were chosen at random and are used for illustrative purposes only.
Copyright © 2010 Stonesoft Corporation. All rights reserved. All specifications are subject to change.
Revision: SGFRG_20101015

3
Table of Contents
TABLE OF CONTENTS
INTRODUCTION
CHAPTER 1
Using StoneGate Documentation . . . . . . . . . . . 13
How to Use This Guide . . . . . . . . . . . . . . . . . . 14
Typographical Conventions . . . . . . . . . . . . . . 14
Documentation Available . . . . . . . . . . . . . . . . . 15
Product Documentation. . . . . . . . . . . . . . . . . 15
Support Documentation . . . . . . . . . . . . . . . . 15
System Requirements. . . . . . . . . . . . . . . . . . 16
Contact Information . . . . . . . . . . . . . . . . . . . . 16
Licensing Issues . . . . . . . . . . . . . . . . . . . . . 16
Technical Support. . . . . . . . . . . . . . . . . . . . . 16
Your Comments . . . . . . . . . . . . . . . . . . . . . . 16
Other Queries. . . . . . . . . . . . . . . . . . . . . . . . 16
CHAPTER 2
Introduction to Firewalls . . . . . . . . . . . . . . . . . 17
The Role of the Firewall. . . . . . . . . . . . . . . . . . 18
Firewall Technologies . . . . . . . . . . . . . . . . . . . 18
Packet Filtering. . . . . . . . . . . . . . . . . . . . . . . 18
Proxy Firewalls . . . . . . . . . . . . . . . . . . . . . . . 19
Stateful Inspection . . . . . . . . . . . . . . . . . . . . 19
StoneGate Multi-Layer Inspection. . . . . . . . . . 19
Additional Firewall Features . . . . . . . . . . . . . . . 21
Authentication . . . . . . . . . . . . . . . . . . . . . . . 21
Deep Packet Inspection and Unified Threat
Management . . . . . . . . . . . . . . . . . . . . . . . . 21
Integration With External Content Inspection. . 21
Load Balancing and Traffic Management. . . . . 22
Logging and Reporting . . . . . . . . . . . . . . . . . 22
Network Address Translation (NAT). . . . . . . . . 23
VPNs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Firewall Weaknesses. . . . . . . . . . . . . . . . . . . . 23
Complexity of Administration . . . . . . . . . . . . . 23
Single Point of Failure . . . . . . . . . . . . . . . . . . 24
Worms, Viruses, and Targeted Attacks . . . . . . 24
CHAPTER 3
Introduction to StoneGate
Firewall/VPN . . . . . . . . . . . . . . . . . . . . . . . . . . 25
The StoneGate Security Platform . . . . . . . . . . . 26
StoneGate Firewall/VPN System Components. . 27
Firewall/VPN Engines . . . . . . . . . . . . . . . . . . 28
Main Benefits of StoneGate Firewall/VPN . . . . . 28
Advanced Traffic Inspection. . . . . . . . . . . . . . 28
Built-in Clustering for Load Balancing and
High Availability . . . . . . . . . . . . . . . . . . . . . . 29
Multi-Link Technology . . . . . . . . . . . . . . . . . . 29
Built-in Inbound Traffic Management . . . . . . . 30
QoS and Bandwidth Management . . . . . . . . . 30
Integration with StoneGate IPS . . . . . . . . . . . 31
Clustered Multi-Link VPNs. . . . . . . . . . . . . . . 31
CHAPTER 4
StoneGate Firewall/VPN Deployment . . . . . . . . 33
Deployment Overview . . . . . . . . . . . . . . . . . . . 34
Supported Platforms . . . . . . . . . . . . . . . . . . 34
General Deployment Guidelines . . . . . . . . . . 34
Positioning Firewalls. . . . . . . . . . . . . . . . . . . . 35
External to Internal Network Boundary . . . . . . 35
Internal Network Boundaries. . . . . . . . . . . . . 36
DMZ Network Boundaries . . . . . . . . . . . . . . . 37
Positioning Management Center Components . 38
INTERFACES AND ROUTING
CHAPTER 5
Single Firewall Configuration. . . . . . . . . . . . . . 41
Overview to Single Firewall Configuration . . . . . 42
Configuration of Single Firewalls . . . . . . . . . . . 42
Dynamic Firewall Interface Addresses . . . . . . 42
Internal DHCP Server . . . . . . . . . . . . . . . . . . 43
Configuration Workflow . . . . . . . . . . . . . . . . . 43
Task 1: Create a Single Firewall
Element . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Task 2: Define Physical Interfaces . . . . . . . 43
Task 3: Define VLAN Interfaces. . . . . . . . . . 43
Task 4: Define an ADSL Interface . . . . . . . . 44
Task 5: Define IP Addresses. . . . . . . . . . . . 44
Task 6: Define Modem Interfaces . . . . . . . . 44
Task 7: Install the Firewall Engine . . . . . . . . 44
Task 8: Install a Firewall Policy . . . . . . . . . . 45
Example of a Single Firewall Deployment . . . . . 45
Setting up a Single Firewall. . . . . . . . . . . . . . 45
Adding a New Interface to an Existing
Configuration. . . . . . . . . . . . . . . . . . . . . . . . 46

4Table of Contents
CHAPTER 6
Firewall Cluster Configuration . . . . . . . . . . . . . 47
Overview to Firewall Cluster Configuration. . . . . 48
Benefits of Clustering . . . . . . . . . . . . . . . . . . 48
Communication Between the Nodes. . . . . . . . 48
Hardware . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Configuration of Firewall Clusters. . . . . . . . . . . 49
Load Balancing. . . . . . . . . . . . . . . . . . . . . . . 49
Standby Operation . . . . . . . . . . . . . . . . . . . . 49
Network Interfaces and IP Addresses. . . . . . . 50
Clustering Modes . . . . . . . . . . . . . . . . . . . . . 51
How Packet Dispatch Works . . . . . . . . . . . . . 51
Configuration Workflow . . . . . . . . . . . . . . . . . 53
Task 1: Create a Firewall Cluster
Element. . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Task 2: Create Physical Interfaces. . . . . . . . 53
Task 3: Define VLAN Interfaces . . . . . . . . . . 53
Task 4: Configure Physical or VLAN
Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . 54
Task 5: Install the Firewall Engines . . . . . . . 55
Task 6: Install a Firewall Policy . . . . . . . . . . 55
Using a Firewall Cluster. . . . . . . . . . . . . . . . . . 55
Internal DHCP Server . . . . . . . . . . . . . . . . . . 55
Node State Synchronization. . . . . . . . . . . . . . 56
Security Level for State Synchronization . . . . . 56
Manual Load Balancing. . . . . . . . . . . . . . . . . 56
Examples of Firewall Cluster Deployment . . . . . 57
Setting up a Firewall Cluster . . . . . . . . . . . . . 57
Adding a Node to a Firewall Cluster . . . . . . . . 58
CHAPTER 7
Routing and Antispoofing. . . . . . . . . . . . . . . . . 59
Overview to Routing and Antispoofing. . . . . . . . 60
Configuration of Routing and Antispoofing . . . . 60
Reading the Routing and Antispoofing Trees . . 60
Multi-Link Routing for Single and Clustered
Firewalls . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Default Elements . . . . . . . . . . . . . . . . . . . . . 62
Configuration Workflow . . . . . . . . . . . . . . . . . 63
Task 1: Add Router or NetLink. . . . . . . . . . . 63
Task 2: Add Network(s). . . . . . . . . . . . . . . . 63
Task 3: Refresh Firewall Policy . . . . . . . . . . 63
Using Routing and Antispoofing . . . . . . . . . . . . 63
Policy Routing. . . . . . . . . . . . . . . . . . . . . . . . 63
Multicast Routing . . . . . . . . . . . . . . . . . . . . . 63
Modifying Antispoofing . . . . . . . . . . . . . . . . . 64
Examples of Routing . . . . . . . . . . . . . . . . . . . . 64
Routing Traffic with Two Interfaces . . . . . . . . . 64
Routing Internet Traffic with Multi-Link . . . . . . 64
Routing Traffic to Networks That Use Same
Address Space . . . . . . . . . . . . . . . . . . . . . . 65
ACCESS CONTROL POLICIES
CHAPTER 8
Firewall Policies . . . . . . . . . . . . . . . . . . . . . . . 69
Overview to Firewall Policies . . . . . . . . . . . . . . 70
Policy Hierarchy . . . . . . . . . . . . . . . . . . . . . . 70
How StoneGate Examines the Packets. . . . . . 70
Configuration of Policy Elements . . . . . . . . . . . 72
Default Elements . . . . . . . . . . . . . . . . . . . . . 74
Configuration Workflow . . . . . . . . . . . . . . . . . 74
Task 1: Create a Firewall Template
Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
Task 2: Create a Firewall Policy. . . . . . . . . . 75
Task 3: Create a Firewall Sub-Policy . . . . . . 75
Task 4: Install the Policy . . . . . . . . . . . . . . 76
Using Policy Elements and Rules. . . . . . . . . . . 77
Validating Policies . . . . . . . . . . . . . . . . . . . . 77
Connection Tracking vs. Connectionless Packet
Inspection . . . . . . . . . . . . . . . . . . . . . . . . . . 77
Policy Snapshots . . . . . . . . . . . . . . . . . . . . . 80
Continue Rules . . . . . . . . . . . . . . . . . . . . . . 80
Adding Comments to Rules. . . . . . . . . . . . . . 80
Examples of Policy Element Use . . . . . . . . . . . 81
Protecting Essential Communications . . . . . . 81
Improving Readability and Performance . . . . . 81
Restricting Administrator Editing Rights . . . . . 82
CHAPTER 9
Access Rules . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Overview to Access Rules. . . . . . . . . . . . . . . . 84
Configuration of Access Rules. . . . . . . . . . . . . 85
Considerations for Designing Access Rules . . 87
Default Elements . . . . . . . . . . . . . . . . . . . . . 87
Configuration Workflow . . . . . . . . . . . . . . . . . 89
Task 1: Define the Source and
Destination . . . . . . . . . . . . . . . . . . . . . . . . 89
Task 2: Define the Service . . . . . . . . . . . . . 89
Task 3: Select the Action and Action
Options. . . . . . . . . . . . . . . . . . . . . . . . . . . 90
Task 4: Select Logging Options. . . . . . . . . . 92
Task 5: Add User Authentication . . . . . . . . . 92
Task 6: Restrict the Time When the
Rule Is Enforced . . . . . . . . . . . . . . . . . . . . 92
Task 7: Restrict the Rule Match Based
on Source VPN . . . . . . . . . . . . . . . . . . . . . 93

5
Table of Contents
Using Access Rules . . . . . . . . . . . . . . . . . . . . 93
Allowing System Communications . . . . . . . . . 93
Configuring Default Settings for Several Rules 94
Using Continue Rules to Set Logging
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Using Continue Rules to set the
Protocol. . . . . . . . . . . . . . . . . . . . . . . . . . . 95
Using Aliases in Access Rules. . . . . . . . . . . . 95
Examples of Access Rules. . . . . . . . . . . . . . . . 96
Example of Rule Order . . . . . . . . . . . . . . . . . 96
Example of Continue Rules . . . . . . . . . . . . . . 98
CHAPTER 10
Inspection Rules . . . . . . . . . . . . . . . . . . . . . . . 99
Overview to Inspection Rules. . . . . . . . . . . . . . 100
Configuration of Inspection Rules. . . . . . . . . . . 101
Considerations for Designing Inspection Rules 102
Exception Rule Cells . . . . . . . . . . . . . . . . . . . 103
Default Elements . . . . . . . . . . . . . . . . . . . . . 104
Configuration Workflow . . . . . . . . . . . . . . . . . 104
Task 1: Activate Deep Inspection in
Access Rules . . . . . . . . . . . . . . . . . . . . . . . 105
Task 2: Activate the Relevant Inspection
Checks . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Task 3: Define the Exceptions . . . . . . . . . . . 105
Task 4: Eliminate False Positives. . . . . . . . . 106
Task 5: Add Custom Inspection Checks . . . . 106
Using Inspection Rules . . . . . . . . . . . . . . . . . . 106
Setting Default Options for Several Inspection
Rules. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
Example of Inspection Rules . . . . . . . . . . . . . . 107
Eliminating a False Positive . . . . . . . . . . . . . . 107
CHAPTER 11
Network Address Translation (NAT) Rules . . . . 109
Overview to NAT . . . . . . . . . . . . . . . . . . . . . . . 110
Static Source Translation . . . . . . . . . . . . . . . 110
Dynamic Source Translation . . . . . . . . . . . . . 111
Static Destination Translation . . . . . . . . . . . . 112
Destination Port Translation . . . . . . . . . . . . . 112
Configuration of NAT . . . . . . . . . . . . . . . . . . . . 113
Considerations for Designing NAT Rules . . . . . 115
Default Elements . . . . . . . . . . . . . . . . . . . . . 115
Configuration Workflow . . . . . . . . . . . . . . . . . 115
Task 1: Define Source, Destination, and
Service . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Task 2: Define Address Translation . . . . . . . 115
Task 3: Define the Firewall(s) that Apply
the Rule. . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Task 4: Check Other Configurations. . . . . . . 116
Using NAT and NAT Rules . . . . . . . . . . . . . . . . 116
NAT and System Communications . . . . . . . . . 116
Example of a Situation Where a
Contact Address is Needed . . . . . . . . . . . . 117
Contact Addresses and Locations . . . . . . . . 118
Outbound Load Balancing NAT . . . . . . . . . . . 118
Proxy ARP and NAT. . . . . . . . . . . . . . . . . . . . 119
Protocols and NAT . . . . . . . . . . . . . . . . . . . . 119
Examples of NAT . . . . . . . . . . . . . . . . . . . . . . 119
Dynamic Source Address Translation . . . . . . . 119
Static Address Translation . . . . . . . . . . . . . . 120
NAT with Hosts in the Same Network. . . . . . . 120
CHAPTER 12
Protocol Agents . . . . . . . . . . . . . . . . . . . . . . . 123
Overview to Protocol Agents . . . . . . . . . . . . . . 124
Connection Handling . . . . . . . . . . . . . . . . . . 124
Protocol Validation . . . . . . . . . . . . . . . . . . . . 124
NAT in Application Data . . . . . . . . . . . . . . . . 125
Configuration of Protocol Agents . . . . . . . . . . . 125
Configuration Workflow . . . . . . . . . . . . . . . . . 125
Task 1: Create a Custom Service with
a Protocol Agent . . . . . . . . . . . . . . . . . . . . 125
Task 2: Set Parameters for the Protocol
Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Task 3: Insert the Service in Access
Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Using Protocol Agents . . . . . . . . . . . . . . . . . . 126
FTP Agent . . . . . . . . . . . . . . . . . . . . . . . . . . 126
H.323 Agent . . . . . . . . . . . . . . . . . . . . . . . . 127
HTTP Agents . . . . . . . . . . . . . . . . . . . . . . . . 127
HTTPS Agent . . . . . . . . . . . . . . . . . . . . . . . . 127
ICMP Agent . . . . . . . . . . . . . . . . . . . . . . . . . 128
MSRPC Agent . . . . . . . . . . . . . . . . . . . . . . . 128
NetBIOS Agent. . . . . . . . . . . . . . . . . . . . . . . 128
Oracle Agent . . . . . . . . . . . . . . . . . . . . . . . . 128
Remote Shell (RSH) Agent . . . . . . . . . . . . . . 128
Services in Firewall Agent . . . . . . . . . . . . . . . 129
SIP Agent . . . . . . . . . . . . . . . . . . . . . . . . . . 129
SMTP Agent. . . . . . . . . . . . . . . . . . . . . . . . . 129
SSH Agent. . . . . . . . . . . . . . . . . . . . . . . . . . 129
SunRPC Agent . . . . . . . . . . . . . . . . . . . . . . . 129
TCP Proxy Agent. . . . . . . . . . . . . . . . . . . . . . 130
TFTP Agent . . . . . . . . . . . . . . . . . . . . . . . . . 130
Examples of Protocol Agent Use . . . . . . . . . . . 130
Preventing Active Mode FTP . . . . . . . . . . . . . 130
Logging URLs Accessed by Internal Users . . . 131

6Table of Contents
CHAPTER 13
User Authentication . . . . . . . . . . . . . . . . . . . . . 133
Overview to User Authentication . . . . . . . . . . . 134
Configuration of User Authentication . . . . . . . . 135
The Internal User Database. . . . . . . . . . . . . . 136
External User Database Integration . . . . . . . . 137
External User Database Without Integration . . 137
User Management . . . . . . . . . . . . . . . . . . . . 137
Authentication Services . . . . . . . . . . . . . . . . 138
RADIUS Authentication . . . . . . . . . . . . . . . . 138
TACACS+ Authentication . . . . . . . . . . . . . . . 138
Default Elements . . . . . . . . . . . . . . . . . . . . . 138
Configuration Workflow . . . . . . . . . . . . . . . . . 139
Task 1: Create an External Authentication
Server Element. . . . . . . . . . . . . . . . . . . . . . 139
Task 2: Create an LDAP Server Element . . . . 139
Task 3: Create an Authentication Service
Element. . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Task 4: Add an LDAP Domain . . . . . . . . . . . 140
Task 5: Add Users and User Groups . . . . . . 140
Task 6: Define User Authentication in
IPv4 Access Rules . . . . . . . . . . . . . . . . . . . 141
Examples of User Authentication . . . . . . . . . . . 143
Using the Internal Database for Authenticating
Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Using StoneGate with a Microsoft Active
Directory Server . . . . . . . . . . . . . . . . . . . . . . 143
Using SecurID Authentication with StoneGate
VPN Clients . . . . . . . . . . . . . . . . . . . . . . . . . 144
CHAPTER 14
HTTPS Inspection . . . . . . . . . . . . . . . . . . . . . . 147
Overview to HTTPS Inspection . . . . . . . . . . . . . 148
Configuration of HTTPS Inspection . . . . . . . . . . 149
Default Elements . . . . . . . . . . . . . . . . . . . . . 149
Configuration Workflow . . . . . . . . . . . . . . . . . 149
Task 1: Create Server Protection
Credentials Elements . . . . . . . . . . . . . . . . . 149
Task 2: Create Client Protection
Certificate Authority Elements . . . . . . . . . . . 150
Task 3: Specify HTTPS Inspection
Options in the Firewall Properties. . . . . . . . . 150
Task 4: Create an HTTPS Inspection
Exceptions Element . . . . . . . . . . . . . . . . . . 150
Task 5: Create a Custom HTTPS
Service . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Task 6: Create an IPv4 Access Rule. . . . . . . 150
Using HTTPS Inspection . . . . . . . . . . . . . . . . . 151
Security Considerations . . . . . . . . . . . . . . . . 151
Virus Scanning of Decrypted HTTPS Traffic . . . 151
Examples of HTTPS Inspection. . . . . . . . . . . . . 151
Server Protection . . . . . . . . . . . . . . . . . . . . . 151
Client Protection . . . . . . . . . . . . . . . . . . . . . 152
CHAPTER 15
Web Filtering . . . . . . . . . . . . . . . . . . . . . . . . . 153
Overview to Web Filtering . . . . . . . . . . . . . . . . 154
Configuration of Web Filtering . . . . . . . . . . . . . 154
Default Elements . . . . . . . . . . . . . . . . . . . . . 155
Configuration Workflow . . . . . . . . . . . . . . . . . 155
Task 1: Prepare the Firewall . . . . . . . . . . . . 155
Task 2: Create User Response Messages . . 155
Task 3: Blacklist/Whitelist Individual URLs . 155
Task 4: Configure Web Filtering Rules
in the Policy. . . . . . . . . . . . . . . . . . . . . . . . 155
Examples of Web Filtering. . . . . . . . . . . . . . . . 156
Allowing a Blocked URL . . . . . . . . . . . . . . . . 156
CHAPTER 16
Virus Scanning . . . . . . . . . . . . . . . . . . . . . . . . 157
Overview to Virus Scanning. . . . . . . . . . . . . . . 158
Configuration of Virus Scanning . . . . . . . . . . . 158
Configuration Workflow . . . . . . . . . . . . . . . . . 158
Task 1: Activate the Anti-Virus Feature
for a Firewall . . . . . . . . . . . . . . . . . . . . . . . 158
Task 2: Select Traffic for Inspection
with Access Rules . . . . . . . . . . . . . . . . . . . 158
Task 3: Define the Content Not to Be
Scanned . . . . . . . . . . . . . . . . . . . . . . . . . . 159
Using Virus Scanning . . . . . . . . . . . . . . . . . . . 159
Integrated Scanning vs. Content Inspection
Server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
Limitations of Virus Scanning on Clusters . . . 159
CHAPTER 17
External Content Inspection . . . . . . . . . . . . . . 161
Overview to Content Inspection . . . . . . . . . . . . 162
Configuration of Content Inspection. . . . . . . . . 163
Default Elements . . . . . . . . . . . . . . . . . . . . . 163
Configuration Workflow . . . . . . . . . . . . . . . . . 164
Task 1: Create a CIS Server Element. . . . . . 164
Task 2: Create a Custom Service for
Content Inspection Server Redirection. . . . . 164
Task 3: Define Access Rules for
Redirection . . . . . . . . . . . . . . . . . . . . . . . . 164
Task 4: Configure NAT Rules for
Content Inspection Server Redirection. . . . . 164
Using Content Inspection . . . . . . . . . . . . . . . . 165
Example of Content Inspection . . . . . . . . . . . . 166
Inspecting Internal User’s Web Browsing and
File Transfers. . . . . . . . . . . . . . . . . . . . . . . . 166

7
Table of Contents
CHAPTER 18
Situations . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
Overview to Situations . . . . . . . . . . . . . . . . . . 170
Configuration of Situations . . . . . . . . . . . . . . . 170
Situation Contexts . . . . . . . . . . . . . . . . . . . . 171
Anti-Virus Contexts . . . . . . . . . . . . . . . . . . . 171
Protocol-Specific Contexts. . . . . . . . . . . . . . 171
System Contexts . . . . . . . . . . . . . . . . . . . . 171
Default Elements . . . . . . . . . . . . . . . . . . . . . 172
Configuration Workflow . . . . . . . . . . . . . . . . . 172
Task 1: Create a Situation Element . . . . . . . 172
Task 2: Add a Context for the
Situation . . . . . . . . . . . . . . . . . . . . . . . . . . 172
Task 3: Associate Tags and/or Situation
Types with the Situation . . . . . . . . . . . . . . . 173
Task 4: Associate the Situation with a
Vulnerability . . . . . . . . . . . . . . . . . . . . . . . . 173
Using Situations . . . . . . . . . . . . . . . . . . . . . . . 173
Example of Custom Situations. . . . . . . . . . . . . 174
Detecting the Use of Forbidden Software . . . . 174
CHAPTER 19
Blacklisting . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Overview to Blacklisting . . . . . . . . . . . . . . . . . 176
Risks of Blacklisting . . . . . . . . . . . . . . . . . . . 176
Whitelisting . . . . . . . . . . . . . . . . . . . . . . . . . 176
Configuration of Blacklisting . . . . . . . . . . . . . . 177
Configuration Workflow . . . . . . . . . . . . . . . . . 177
Task 1: Define Blacklisting in Access
Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
Task 2: Define Analyzer-to-Firewall or
Analyzer-to-Sensor Connections . . . . . . . . . . 178
Task 3: Define Inspection Rules in the
IPS Policy. . . . . . . . . . . . . . . . . . . . . . . . . . 178
Using Blacklisting . . . . . . . . . . . . . . . . . . . . . . 178
Automatic Blacklisting. . . . . . . . . . . . . . . . . . 178
Monitoring Blacklisting . . . . . . . . . . . . . . . . . 179
Examples of Blacklisting . . . . . . . . . . . . . . . . . 179
Blacklisting Traffic from a Specific IP Address
Manually . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Automatic Blacklisting with IPS . . . . . . . . . . . 179
TRAFFIC MANAGEMENT
CHAPTER 20
Outbound Traffic Management . . . . . . . . . . . . . 183
Overview to Outbound Traffic Management . . . . 184
Configuration of Multi-Link. . . . . . . . . . . . . . . . 184
Load Balancing Methods. . . . . . . . . . . . . . . . 185
Standby NetLinks for High Availability . . . . . . 185
Link Status Probing . . . . . . . . . . . . . . . . . . . 185
Configuration Workflow . . . . . . . . . . . . . . . . . 186
Task 1: Create NetLink Elements . . . . . . . . 186
Task 2: Configure Routing for NetLinks . . . . 186
Task 3: Combine NetLinks into Outbound
Multi-Link Elements . . . . . . . . . . . . . . . . . . 186
Task 4: Create NAT Rules for Outbound
Traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Using Multi-Link . . . . . . . . . . . . . . . . . . . . . . . 187
Multi-Link with a Single Firewall. . . . . . . . . . . 187
Multi-Link with a Firewall Cluster . . . . . . . . . . 188
Using Multiple Outbound Multi-Link elements . 189
Examples of Multi-Link . . . . . . . . . . . . . . . . . . 189
Preparing for ISP Breakdown. . . . . . . . . . . . . 189
Excluding a NetLink from Handling a QoS
Class of Traffic. . . . . . . . . . . . . . . . . . . . . . . 189
Balancing Traffic According to Link Capacity . . 190
Balancing Traffic between Internet Connections 190
CHAPTER 21
Inbound Traffic Management. . . . . . . . . . . . . . 191
Overview to Server Pool Configuration . . . . . . . 192
Configuration of Server Pools . . . . . . . . . . . . . 192
Multi-Link for Server Pools . . . . . . . . . . . . . . 193
Default Elements . . . . . . . . . . . . . . . . . . . . . 193
Configuration Workflow . . . . . . . . . . . . . . . . . 194
Task 1: Define Hosts . . . . . . . . . . . . . . . . . 194
Task 2: Combine Hosts into a Server
Pool Element . . . . . . . . . . . . . . . . . . . . . . . 194
Task 3: Configure the External DNS
Server. . . . . . . . . . . . . . . . . . . . . . . . . . . . 194
Task 4: Create an Inbound Load
Balancing Rule . . . . . . . . . . . . . . . . . . . . . 194
Task 5: Set up Server Pool Monitoring
Agents . . . . . . . . . . . . . . . . . . . . . . . . . . . 194
Using Server Pools. . . . . . . . . . . . . . . . . . . . . 195
Dynamic DNS (DDNS) Updates . . . . . . . . . . . 195
Using Server Pool Monitoring Agents . . . . . . . 195
Examples of Server Pools . . . . . . . . . . . . . . . . 197
Load Balancing for Web Servers . . . . . . . . . . 197
Setting up Multi-Link and Dynamic DNS
Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
CHAPTER 22
Bandwidth Management And Traffic Prioritization 199
Overview to Bandwidth Management and Traffic
Prioritization . . . . . . . . . . . . . . . . . . . . . . . . . 200
Bandwidth Management . . . . . . . . . . . . . . . . 200
Traffic Prioritization. . . . . . . . . . . . . . . . . . . . 200

8Table of Contents
Effects of Bandwidth Management and
Prioritization. . . . . . . . . . . . . . . . . . . . . . . . . 200
Configuration of Limits, Guarantees, and Priorities
for Traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Default Elements . . . . . . . . . . . . . . . . . . . . . 202
Configuration Workflow . . . . . . . . . . . . . . . . . 202
Task 1: Define QoS Classes . . . . . . . . . . . . 202
Task 2: Define QoS Policies . . . . . . . . . . . . 203
Task 3: Assign QoS Classes to Traffic . . . . . 204
Task 4: Define QoS for Physical or
VLAN Interfaces . . . . . . . . . . . . . . . . . . . . . 204
Using Bandwidth Management and Traffic
Prioritization. . . . . . . . . . . . . . . . . . . . . . . . . . 205
Implementation Options . . . . . . . . . . . . . . . . 205
Designing QoS Policies . . . . . . . . . . . . . . . . . 205
Communicating Priorities with DSCP Codes . . 206
Managing Bandwidth of Incoming Traffic . . . . . 207
Examples of Bandwidth Management and Traffic
Prioritization. . . . . . . . . . . . . . . . . . . . . . . . . . 208
Ensuring Quality of Important Communications 208
Preparing for ISP Breakdown . . . . . . . . . . . . . 209
Limiting the Total Bandwidth Required . . . . . . 210
VIRTUAL PRIVATE NETWORKS
CHAPTER 23
Overview to VPNs . . . . . . . . . . . . . . . . . . . . . . 213
Introduction to VPNs . . . . . . . . . . . . . . . . . . . . 214
IPsec VPNs . . . . . . . . . . . . . . . . . . . . . . . . . . 215
Tunnels . . . . . . . . . . . . . . . . . . . . . . . . . . . . 215
Security Associations (SA). . . . . . . . . . . . . . . 215
Internet Key Exchange (IKE). . . . . . . . . . . . . . 215
Perfect Forward Secrecy (PFS) . . . . . . . . . . . . 216
AH and ESP . . . . . . . . . . . . . . . . . . . . . . . . . 216
Authentication . . . . . . . . . . . . . . . . . . . . . . . 217
Tunnel and Transport Modes . . . . . . . . . . . . . 217
VPN Topologies. . . . . . . . . . . . . . . . . . . . . . . . 217
CHAPTER 24
VPN Configuration . . . . . . . . . . . . . . . . . . . . . 221
Overview to VPN Configuration. . . . . . . . . . . . . 222
Configuration of VPNs . . . . . . . . . . . . . . . . . . . 222
Default Elements . . . . . . . . . . . . . . . . . . . . . 224
Configuration Workflow . . . . . . . . . . . . . . . . . 224
Task 1: Define the Gateway Settings. . . . . . 224
Task 2: Define the Gateway Profile . . . . . . . 224
Task 3: Define the Gateways . . . . . . . . . . . 225
Task 4: Define the Sites. . . . . . . . . . . . . . . 225
Task 5: Create Certificates . . . . . . . . . . . . . 226
Task 6: Define the VPN Profile . . . . . . . . . . 226
Task 7: Define the VPN Element . . . . . . . . . 226
Task 8: Modify the Firewall Policy . . . . . . . . 227
Task 9: Configure VPN Clients and
External Gateway Devices. . . . . . . . . . . . . . 228
Using VPNs . . . . . . . . . . . . . . . . . . . . . . . . . . 228
VPN Logging . . . . . . . . . . . . . . . . . . . . . . . . 229
Using a Dynamic IP Address for a VPN
End-Point. . . . . . . . . . . . . . . . . . . . . . . . . . . 229
Using a NAT Address for a VPN End-Point. . . . 229
Supported Authentication and Encryption
Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
FIPS Mode. . . . . . . . . . . . . . . . . . . . . . . . . 230
GOST-Compliant Systems . . . . . . . . . . . . . . 230
Message Digest Algorithms . . . . . . . . . . . . 230
Authentication Methods . . . . . . . . . . . . . . . 231
Encryption Algorithms. . . . . . . . . . . . . . . . . 232
Using Pre-Shared Key Authentication . . . . . . . 233
Using Certificate Authentication . . . . . . . . . . 233
Validity of Certificates . . . . . . . . . . . . . . . . 234
Internal VPN Certificate Authority. . . . . . . . . 234
External Certificate Authorities . . . . . . . . . . 235
Configuring VPNs with External Gateway
Devices. . . . . . . . . . . . . . . . . . . . . . . . . . . . 235
Clustering and VPNs. . . . . . . . . . . . . . . . . . . 236
Multi-Link VPN . . . . . . . . . . . . . . . . . . . . . . . 237
Examples of VPN Configurations . . . . . . . . . . . 238
Creating a VPN Between Three Offices. . . . . . 238
Creating a VPN for Mobile Users . . . . . . . . . . 239
Creating a VPN That Requires NAT. . . . . . . . . 240
APPENDICES
APPENDIX A
Command Line Tools . . . . . . . . . . . . . . . . . . . . 245
Management Center Commands . . . . . . . . . . . 246
Engine Commands . . . . . . . . . . . . . . . . . . . . . 254
Server Pool Monitoring Agent Commands. . . . . 259
APPENDIX B
Default Communication Ports . . . . . . . . . . . . . 261
Management Center Ports . . . . . . . . . . . . . . . 262
Firewall/VPN Engine Ports . . . . . . . . . . . . . . . 264

9
Table of Contents
APPENDIX C
Predefined Aliases . . . . . . . . . . . . . . . . . . . . . . 269
Pre-Defined User Aliases. . . . . . . . . . . . . . . . . 270
System Aliases. . . . . . . . . . . . . . . . . . . . . . . . 270
APPENDIX D
Regular Expression Syntax . . . . . . . . . . . . . . . . 273
Syntax for StoneGate Regular Expressions . . . . 274
Special Character Sequences . . . . . . . . . . . . . 276
Pattern-Matching Modifiers . . . . . . . . . . . . . . . 277
Bit Variable Extensions . . . . . . . . . . . . . . . . . . 278
Variable Expression Evaluation . . . . . . . . . . . . 280
Stream Operations . . . . . . . . . . . . . . . . . . . . 282
Other Expressions . . . . . . . . . . . . . . . . . . . . 283
System Variables . . . . . . . . . . . . . . . . . . . . . . 284
Independent Subexpressions. . . . . . . . . . . . . . 285
Parallel Matching Groups. . . . . . . . . . . . . . . . . 286
APPENDIX E
Schema Updates for External LDAP Servers . . . 287
APPENDIX F
SNMP Traps and MIBs . . . . . . . . . . . . . . . . . . . 289
APPENDIX G
Multicasting . . . . . . . . . . . . . . . . . . . . . . . . . . 301
The General Features of Multicasting . . . . . . . . 302
Multicasting vs. Unicasting . . . . . . . . . . . . . . 302
Multicasting vs. Broadcasting . . . . . . . . . . . . 302
IP Multicasting Overview . . . . . . . . . . . . . . . . . 302
Multicasting Applications . . . . . . . . . . . . . . . 303
Internet Group Management Protocol . . . . . . . . 303
Membership Messages. . . . . . . . . . . . . . . . . 303
Ethernet Multicasting . . . . . . . . . . . . . . . . . . . 304
Multicasting and StoneGate . . . . . . . . . . . . . . 304
Unicast MAC . . . . . . . . . . . . . . . . . . . . . . . . 305
Multicast MAC . . . . . . . . . . . . . . . . . . . . . . . 306
Multicast MAC with IGMP . . . . . . . . . . . . . . . 307
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 309
Index. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 339

10 Table of Contents

11
INTRODUCTION
In this section:
Using StoneGate Documentation - 13
Introduction to Firewalls - 17
Introduction to StoneGate Firewall/VPN - 25
StoneGate Firewall/VPN Deployment - 33

12

13
CHAPTER 1
USING STONEGATE DOCUMENTATION
Welcome to StoneGate™ High Availability Firewall/VPN solution by Stonesoft Corporation. This
chapter describes how to use this Guide and related documentation. It also provides
directions for obtaining technical support and giving feedback about the documentation.
The following sections are included:
How to Use This Guide (page 14)
Documentation Available (page 15)
Contact Information (page 16)

14 Chapter 1 Using StoneGate Documentation
How to Use This Guide
This Reference Guide provides information that helps administrators of StoneGate firewalls
understand the system and its features. It provides high-level descriptions and examples of the
configuration workflows.
This guide is divided into several sections. The chapters in the first section provide a general
introduction to StoneGate firewalls. The sections that follow each include chapters related to
one feature area. The last section provides detailed reference information in tabular form, and
some guideline information.
For other available documentation, see Documentation Available (page 15).
Typographical Conventions
The following typographical conventions are used throughout the guide:
We use the following ways to indicate important or additional information:
Tip – Tips provide information that is not crucial, but may still be helpful.
Table 1.1 Typographical Conventions
Formatting Informative Uses
Normal text This is normal text.
User Interface text Text you see in the User Interface (buttons, menus, etc.) and any
other interaction with the user interface are in bold-face.
References, terms Cross-references and first use of acronyms and terms are in
italics.
Command line File names, directories, and text displayed on the screen are
monospaced.
User input User input on screen is in monospaced bold-face.
Command parameters Command parameter names are in monospaced italics.
Note – Notes provide important information that prevents mistakes or helps you complete
a task.
Caution – Cautions provide critical information that you must take into account to prevent
breaches of security, information loss, or system downtime.

15
Documentation Available
Documentation Available
StoneGate technical documentation is divided into two main categories: Product Documentation
and Support Documentation. Each StoneGate product has a separate set of manuals.
Product Documentation
The table below lists the available product documentation. PDF guides are available on the
Management Center CD-ROM and at http://www.stonesoft.com/support/.
Support Documentation
The StoneGate support documentation provides additional and late-breaking technical
information. These technical documents support the StoneGate Guide books, for example, by
giving further examples on specific configuration scenarios.
The latest StoneGate technical documentation is available on the Stonesoft website at http://
www.stonesoft.com/support/.
Table 1.2 Product Documentation
Guide Description
Reference Guide
Explains the operation and features of StoneGate comprehensively.
Demonstrates the general workflow and provides example scenarios
for each feature area. Available for StoneGate Management Center,
Firewall/VPN, and StoneGate IPS.
Installation Guide
Instructions for planning, installing, and upgrading a StoneGate
system. Available for StoneGate Management Center, Firewall/VPN,
IPS, and SOHO firewall products.
Online Help
Describes how to configure and manage the system step-by-step.
Accessible through the Help menu and by using the Help button or
the F1 key in any window or dialog. Available in the StoneGate
Management Client and the StoneGate Web Portal. An HTML-based
system is available in the StoneGate SSL VPN Administrator through
help links and icons.
Administrator’s Guide
Describes how to configure and manage the system step-by-step.
Available as a combined guide for both StoneGate Firewall/VPN and
StoneGate IPS, and as separate guides for StoneGate SSL VPN and
StoneGate IPsec VPN Client.
User’s Guide Instructions for end-users. Available for the StoneGate IPsec VPN
Client and the StoneGate Web Portal.
Appliance Installation Guide
Instructions for physically installing and maintaining StoneGate
appliances (rack mounting, cabling, etc.). Available for all StoneGate
hardware appliances.

16 Chapter 1 Using StoneGate Documentation
System Requirements
The certified platforms for running StoneGate engine software can be found at the product
pages at http://www.stonesoft.com/en/products_and_solutions/products/fw/
Software_Solutions/.
The hardware and software requirements for the version of StoneGate you are running can also
be found in the Release Notes, available at the Stonesoft Support Documentation pages.
Contact Information
For street addresses, phone numbers, and general information about StoneGate and Stonesoft
Corporation, visit our website at http://www.stonesoft.com/.
Licensing Issues
You can view your current licenses at the License Center section of the Stonesoft website at
https://my.stonesoft.com/managelicense.do.
Technical Support
Stonesoft offers global technical support services for Stonesoft’s product families. For more
information on technical support, visit the Support section at the Stonesoft website at http://
www.stonesoft.com/support/.
Your Comments
We want to make our products fulfill your needs as well as possible. We are always pleased to
receive any suggestions you may have for improvements.
•To comment on software and hardware products, e-mail [email protected].
•To comment on the documentation, e-mail [email protected].
Other Queries

17
CHAPTER 2
INTRODUCTION TO FIREWALLS
This chapter introduces and discusses the underlying security principles of firewalls in
general. In this chapter we will discuss what firewalls are, which different types of firewalls
there are, how they are used, what they are capable of, as well as what their possible
weaknesses are.
The following sections are included:
The Role of the Firewall (page 18)
Firewall Technologies (page 18)
Additional Firewall Features (page 21)
Firewall Weaknesses (page 23)

18 Chapter 2 Introduction to Firewalls
The Role of the Firewall
Firewalls are the primary tool for perimeter access control between networks with different
security levels. Firewalls control the traffic between networks and deny access that does not
look like acceptable business use as defined by the administrators.
The generally accepted principle of access control is whatever is not expressly permitted is
denied. The most secure network is achieved when nobody and nothing is permitted entry to the
protected network. In most cases, such a network is naturally too limited, so a firewall must be
introduced to allow specific limited services to pass in a safe way. That means that in order for
any traffic to be allowed into the network, it must first match an explicit “allow” rule.
There are three main types of platforms for running a firewall:
•Dedicated firewall appliances.
•Firewall software installed on a server dedicated to be used as a firewall.
•Firewall software running as a virtual machine in a virtualized server environment.
The StoneGate Firewall/VPN is available on all of these platform types.
Regardless of the type of platform, the network structure in which the firewalls are placed must
be carefully designed so that there are no loopholes or back doors. Firewalls can only control
traffic that actually passes through them; even the most carefully planned firewall system can
be undermined by a single back door that allows traffic to circumvent the firewall.
In addition to access control, modern firewall devices often include a variety of additional
integrated features, such as intrusion prevention systems (IPS), content filtering, and anti-virus.
In this chapter, the additional features are discussed separately, and the main discussion
concentrates on the primary role of access control. Such additional features in StoneGate
firewalls are covered in more detail in section Additional Firewall Features (page 21) and in other
chapters of this book.
Firewall Technologies
This section presents an overview to the main firewall techniques, and explains how StoneGate
uses them. The discussion here is limited to the traditional firewall component of a firewall
system; the various additional inspection features that modern firewalls often incorporate are
discussed separately.
Traditional firewall features are commonly achieved through three main techniques:
•packet filtering
•proxy firewalls
•stateful inspection.
The next sections first discuss these techniques separately and then explains how they can be
utilized together to achieve an optimal balance between performance and security.
Packet Filtering
Packet filtering examines the header information of packets and allows or stops each packet
individually. In addition to firewalls, such simple access control lists (ACLs) are implemented on
most common routing devices. Pure packet filters cannot protect against protocol misuse or

19
Firewall Technologies
other malicious contents in higher levels of the protocol stack. However, for some simple
network protocols, packet filtering can be light on firewall resources and even provide an
adequate level of protection.
Proxy Firewalls
Proxy firewalls are firewalls running application proxy services. Proxies are a man-in-the-middle,
and they establish their own separate connections to both the client and the server. This type of
firewall is fully application-aware, and therefore very secure, but at the same time there’s a
trade-off in performance due to the inevitable increase in overhead.
Illustration 2.1 Proxy Firewall Model
Stateful Inspection
Stateful inspection firewalls are aware of basic networking standards and use historical data
about connections in determining whether to allow or stop a packet. They track the established
connections and their states in dynamic state tables and ensure that the connections comply
with the security policies and protocol standards.
Since stateful inspection understands the context of connections (and therefore can relate the
returning packets to appropriate connections), connections already determined to be “secure”
can be allowed without full examination based on previous packets. This is especially important
with services such as FTP, which can open several related connections that do not match a
single basic profile. Even though Stateful inspection has some application awareness, it
concentrates on protocols, not on inspecting data at the application layer.
StoneGate Multi-Layer Inspection
StoneGate Multi-Layer Inspection combines application layer inspection, stateful inspection, and
packet filtering technologies flexibly for optimal security and system performance. Like stateful
inspection, StoneGate uses state tables to track connections and judge whether a packet is a
part of an established connection or not. The StoneGate firewall also features application-layer
inspection through specific Protocol Agents, when necessary, for enhanced security to inspect
data all the way up to the application layer. The StoneGate firewall can also act as a packet filter
for types of connections that do not require the security considerations of stateful inspection.

20 Chapter 2 Introduction to Firewalls
Illustration 2.2 Multi-layer Inspection Model
By default, all StoneGate firewall Access rules implement stateful inspection, but the
administrator can flexibly configure rules with simple packet filtering or an additional layer of
application level security as needed.
StoneGate firewalls apply application level inspection with or without proxying the connections,
depending on what is required. Application level inspection can be selected to certain types of
traffic by attaching a connection to a protocol-specific Protocol Agent.
Protocol Agents are also used to handle protocols that generate complex connection patterns,
to redirect traffic to content inspection servers, and to modify data payload if necessary. For
example, the FTP Protocol Agent, can inspect the control connection and only allow packets
containing valid FTP commands. If an FTP data connection is opened using a dynamically
assigned port, the Protocol Agent reads the port and allows the traffic. If NAT (network address
translation) is applied to the connection, the Protocol Agent can also modify the IP address and
port transported in the packet payload to allow the connection to continue despite the NAT. The
Protocol Agents are covered in more detail in Protocol Agents (page 123).
This manual suits for next models
1
Table of contents
Popular Software manuals by other brands

Agilent Technologies
Agilent Technologies Agilent NanoSuite 6.2 datasheet

Tadiran Telecom
Tadiran Telecom Coral SeaBeam Installation and configuration reference manual

Altigen
Altigen VRManager manual

Juniper
Juniper JUNOS OS 10.4 - PROTECTED SYSTEM DOMAIN Configuration guide
Waves
Waves Multimaximizer L3-16 user manual
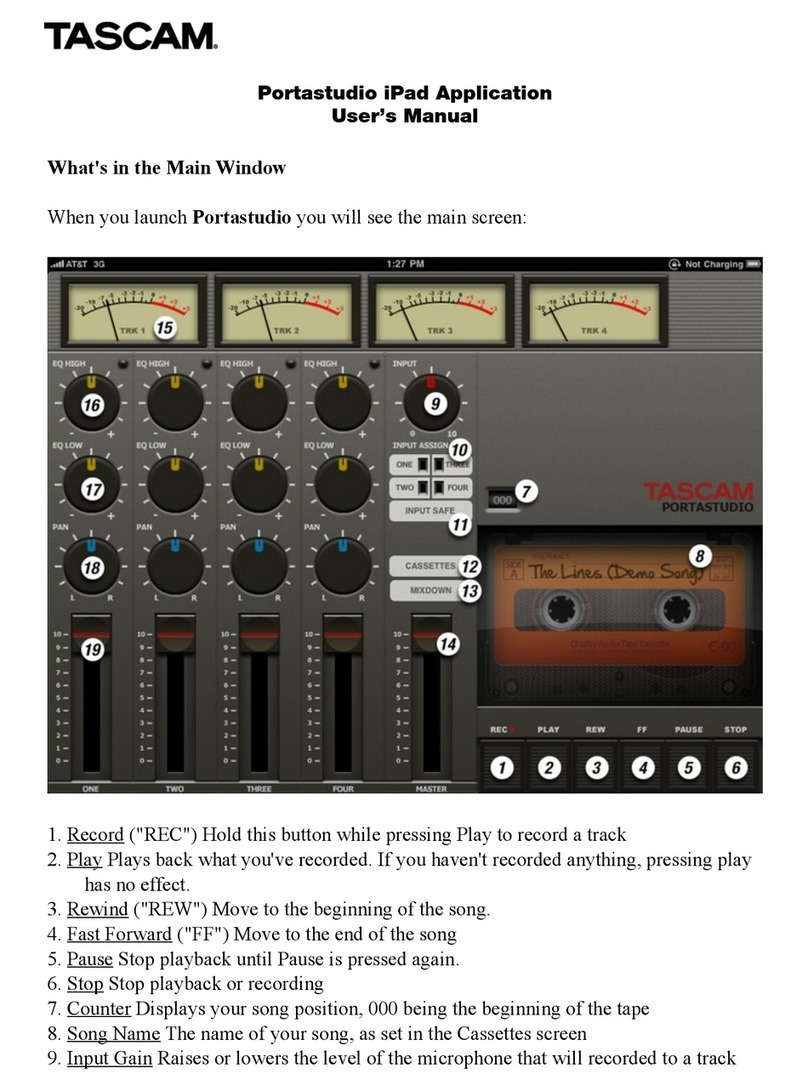
Tascam
Tascam Portastudio iPad Application user manual