Elastix SIP Firewall User manual


Elastix SIP Firewall
User Manual

1
Copy Right
Copyright © 2014 Elastix®. All rights reserved.
No part of this publication may be copied, distributed, transmitted, transcribed, stored in a retrieval system,
or translated into any human or computer language without the prior written permission of
http://www.elastix.org. This document has been prepared for use by professional and properly trained
personnel, and the customer assumes full responsibility when using it.
Proprietary Rights
The information in this document is Confidential to Elastix®and is legally privileged. The information and
this document are intended solely for the addressee. Use of this document by anyone else for any other
purpose is unauthorized. If you are not the intended recipient, any disclosure, copying, or distribution of this
information is prohibited and unlawful.
Disclaimer
Information in this document is subject to change without notice and should not be construed as a
commitment on the part of http://www.elastix.org. And does not assume any responsibility or make any
warranty against errors. It may appear in this document and disclaims any implied warranty of
merchantability or fitness for a particular purpose.
!
!
!

2
1.1. About this manual
This manual describes the Elastix® product application and explains how to work and use
it major features. It serves as a means to describe the user interface and how to use it to
accomplish common tasks. This manual also describes the underlying assumptions and
users make the underlying data model.
1.1. Document Conventions
In this manual, certain words are represented in different fonts, typefaces, sizes, and
weights. This highlighting is systematic; different words are represented in the same style
to indicate their inclusion in a specific category. Additionally, this document has different
strategies to draw User attention to certain pieces of information. In order of how critical
the information is to your system, these items are marked as a note, tip, important,
caution, or warning.
Icon!
Purpose!
!
Note!
!
Tip/Best!Practice!
!
Important!
!
Caution!
!
Warning!
!
!
•Bold indicates the name of the menu items, options, dialog boxes, windows and
functions.
•The color blue with underline is used to indicate cross-references and hyperlinks.
•Numbered Paragraphs - Numbered paragraphs are used to indicate tasks that need
to be carried out. Text in paragraphs without numbering represents ordinary
information.
•The Courier font indicates a command sequence, file type, URL, Folder/File name
e.g. http://www.elastix.org

3
1.2. Support Information
Every effort has been made to ensure the accuracy of the document. If you have
comments, questions, or ideas regarding the document contact:
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!

4
Table of Contents
About this manual .................................................................................................. 2
Document Conventions........................................................................................... 2
Support Information ............................................................................................... 3
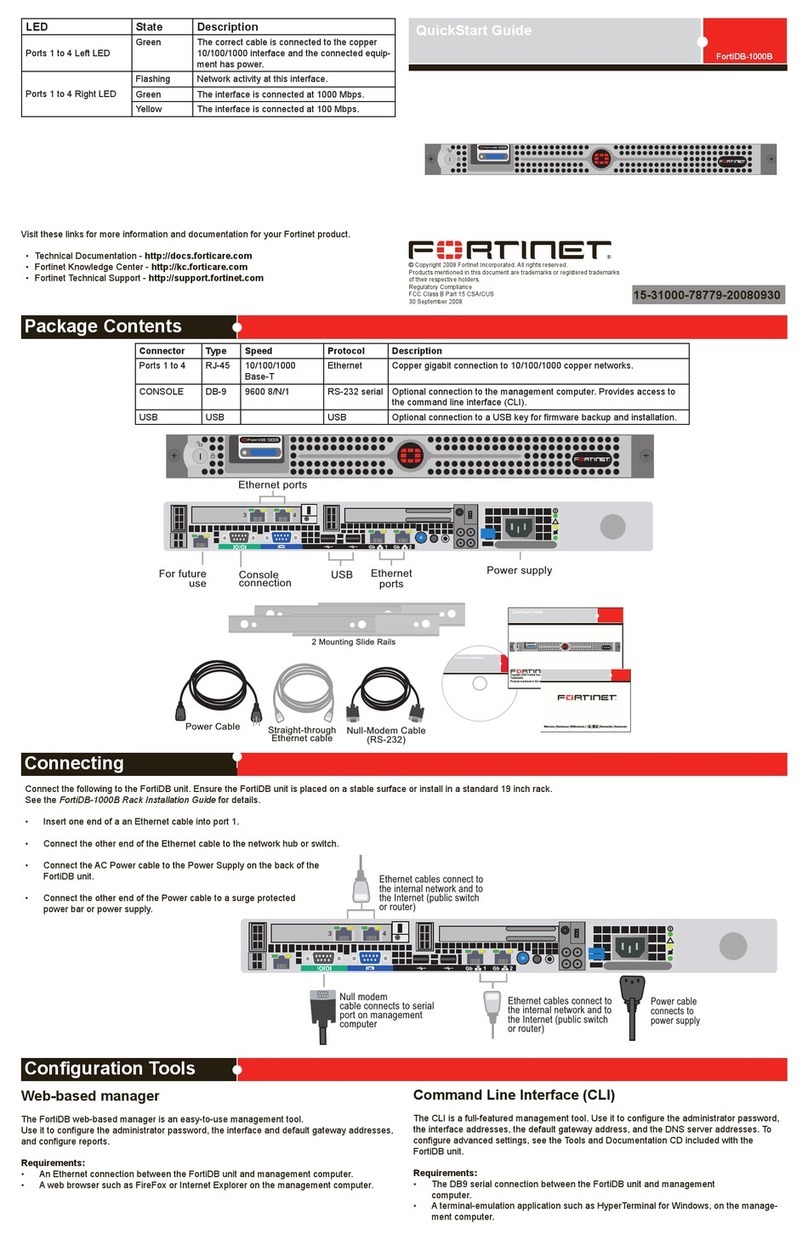
1. Introduction ........................................................................................................... 6
1.1. Overview: ......................................................................................................... 6
1.1.1. Notification LEDs (On the Front Panel of the SIP Firewall) ........................ 8
1.1.2. SIP Firewall Rear View:.............................................................................. 9
1.1.3. SIP Firewall Deployment Considerations ................................................... 9
2. Initial Setup & Configuration.............................................................................. 11
2.1.Default Configuration ...................................................................................... 11
2.2. Accessing the WebUI..................................................................................... 11
2.4 WebUI Session timeout .................................................................................. 14
2.5 WebUI Settings ............................................................................................... 14
2.4 Dashboard ...................................................................................................... 15
3. Device Configuration .......................................................................................... 16
3.1. General Settings ............................................................................................ 17
3.2. Time Settings ................................................................................................. 18
3.3. Management Access ..................................................................................... 18
3.4. Signature Update ........................................................................................... 20
3.5. Logging .......................................................................................................... 20
4. Configuring the SIP Security Policies............................................................... 22
4.1. SIP Attacks Detection Policies....................................................................... 22
4.2. SIP Protocol Compliance ............................................................................... 24
4.3. Firewall Rules ................................................................................................ 26
4.4. Firewall Settings............................................................................................. 27
4.5. White list Rules .............................................................................................. 28
4.6. Blacklist Rules (Static) ................................................................................... 29
4.7. Dynamic Blacklist Rules................................................................................. 30
4.8. Geo IP Filter................................................................................................... 30

5
5. Status ................................................................................................................... 32
5.1. Security Alerts................................................................................................ 32
6. Tools..................................................................................................................... 33
6.1. Administration ................................................................................................ 33
6.2. Diagnostics .................................................................................................... 34
6.3. Ping................................................................................................................ 35
6.4. Trace route..................................................................................................... 35
6.5. Troubleshooting ............................................................................................. 36
6.6. Firmware Upgrade ......................................................................................... 37
6.7. Logs Archive .................................................................................................. 38
7. Appendix A – Using Console Access ............................................................... 39
8. Appendix B – Configuring SIP Firewall IP Address via Console.................... 40

6
1. Introduction
1.1 . Overview:
This User manual describes the steps involved in setting up the Elastix®SIP Firewall
Appliance. Elastix®SIP Firewall is an appliance based VoIP threat prevention solution
dedicated to protect the SIP based PBX/Telecom Gateway/IP Phones/Mobile device
deployments. The appliance runs the Real time Deep Packet Inspection on the SIP
traffic to identify the VOIP attack vectors and prevents the threats impacting the SIP
based devices. The appliance has been made to seamlessly integrate with the existing
network infrastructure and reduces the complexity of deployment.
The appliance feature set includes,
!Analyze SIP packets using the Realtime Deep Packet inspection engine.
!SIP Protocol Anomaly detection with configurability of detection parameters.
!Detection and Prevention of the following categories of SIP based Attacks.
•Reconnaissance attacks (SIP Devices Fingerprinting, User enumeration,
Password Cracking Attempt)
•Dos/DDos Attacks
•Cross Site Scripting based attacks.
•Buffer overflow attacks
•SIP Anomaly based attacks
•3rd Party vendor vulnerabilities
•Toll Fraud detection and prevention
•Protection against VOIP Spam & War Dialing
!Attack response includes the option for quietly dropping malicious SIP packets to
help prevent continued attacks
!Dynamic Blacklist Update service for VOIP, SIP PBX/Gateway Threats
!Configurability of Blacklist/White list/Firewall rules.
!Support for Geo Location based blocking.
!Provide the option to secure against PBX Application vulnerabilities
!Operate at Layer 2 device thus transparent to existing IP infrastructure - no changes
required to add the device to your existing network
!Web/SSL based Device Management Access which will allow managing the device
anywhere from the Cloud.
!Ability to restrict the device management access to specific IP/Network.
!Provide System Status/Security events logging option to a remote Syslog server.
!Provides the SIP throughput up to ~10Mbps.
!Support for Signature update subscription and automated signature update
mechanism.

7
!The device has been made to operate with default configuration with just powering
on the device. No administrator intervention is required to operate the device with
default configuration.
!USB based power supply
!Optional support for security events logging on the USB based storage.
Technical Specifications
Functional Mode
Transparent Firewall with SIP Deep Packet
Engine.
SIP Intrusion/Prevention
~400+ SIP Attack Signatures Support
Throughput
~10Mbps
No of concurrent calls supports
Up to 50 concurrent calls
Logging
Local Security Event Console, Remote Syslog
Device Management
Web GUI via Https & SSH CLI
Hardware
MIPS based 32bit Processor Single core,
300MHz
Primary Storage
16 MB Flash
RAM
64MB
Secondary Storage
USB Storage devices support for logging (
Optional)
Interfaces
Two Fast Ethernet Interfaces.

8
1.1.1. Notification LEDs (On the Front Panel of the SIP Firewall)
LED 4-Alert Status
Power ON/OFF LED 3-DPI Status
Button
LED 2- Interface Status
Power LED LED 1- System Status
Indicator
Figure 1: Front Panel LED Notifications
The SIP Firewall package includes:
•1 SIP Firewall Appliance
•1 USB Power Adapter
•1 Serial Console Cable
•2 Ethernet Cables

9
1.1.2. SIP Firewall Rear View:
LAN Port Reset Button
WAN Port USB Power Plug
Console Port
USB Storage Plug
Figure 2: SIP Firewall Rear View
1.1.3. SIP Firewall Deployment Considerations
The SIP Firewall has been made to protect the SIP based PBX/Gateway Servers against
SIP based network threats and anomalies. Thus it is recommended to deploy the SIP
Firewall along with the PBX/Gateway deployment as given in the following scenarios
based on what is applicable in the user’s setup.
Deployment Scenario 1
Figure 1: Scenario 1
Some of the PBX/Gateway devices may have an exclusive LAN/Mgmt Interface for
device management purpose other than the Data Interface (also referred as WAN/Public
Interface). In such cases LAN Port of the SIP Firewall should be connected to the Data
Interface (WAN/Public Interface).

10
Deployment Scenario 2
In the case of IPPBX deployed in the LAN Setup, the following setup is recommended as
it would help to protect against the threats from both Internal Network as well as the
threats from the Public Cloud penetrated the Non SIP aware Corporate Firewall.
Figure 2: Scenario 2
Deployment Scenario 3
In the case of multiple IPPBX/ VOIP Gateways are deployed in the LAN Setup, the
following setup is recommended as it would help to protect against the threats from both
Internal Network as well as the threats from the Public Cloud penetrated the Non SIP
aware Corporate Firewall.
Figure 3: Scenario 3

11
2. Initial Setup & Configuration
1. Unpack the items from the box
2. Check that you have all the items listed in the package content.
3. Connect the WAN port of the SIP Firewall to the untrusted/public network.
4. Connect the LAN port of the SIP Firewall to the PBX/VOIP Gateway.
5. Connect the appliance to the power socket using the USB power cable.
6. The device will take about a minute to boot up & will be fully functional with the
default configuration.
Some of the PBX/Gateway devices may have an exclusive LAN/Mgmt Interface for
device management purpose other than the Data Interface (also referred as WAN/ public
Interface). In such cases LAN port of the SIP Firewall should be connected to the Data
Interface (WAN/ Public Interface).
2.1 .Default Configuration
The device operates as a transparent bridging firewall with Deep Packet Inspection
enabled on the SIP traffic. By default, the appliance has been configured with static IP of
10.0.0.1 (Net mask 255.255.255.0)
The device has been made to be fully functional with the default configuration. However if
the user needs to tune the device settings & the DPI policies, user can tune the
configuration via the Device WebUI.
The device all provides the command line interface accessible via SSH, which will allow
to configure the basic settings and view device status.
Management Access
Login Credentials
WebUI
admin/admin
SSH CLI
admin/stmadmin
Management Vlan IP
192.168.100.1/255.255.255.0
Default Device IP
10.0.0.1/255.255.255.0
2.2. Accessing the WebUI
The user can connect to the device via management Vlan to access WebUI during initial
setup. The management Vlan configured on the device, is accessible via the LAN/WAN
ports & is made assigned to the default IP address ‘192.168.100.1’

12
Use the procedure given below to access the WebUI,
1. Connect the LAN port of the SIP Firewall to a PC.
2. Assign the IP Address 192.168.100.2 to the PC. Set the Net mask as
255.255.255.0.
Now you can access the device from the browser using the URL https://<192.168.100.1>
Configure the SIP Firewall Device IP Address from the “Device Settings” Page as per
your local network range. Verify the IP address set to SIP Firewall from the dashboard
page. Once the user assigns the SIP Firewall Device IP Address successfully, he can
access the device using that IP address further.
Now he can disconnect the PC and connect the LAN Port to the PBX/PBX Network that
needs to be protected.
The WebUI has been made accessible only via HTTPS. The recommended
browser for accessing SIP Firewall WebUI is Mozilla Firefox.
The UI allows the administrator to configure the management Vlan IP addresses. In
case if the user has changed the management Vlan IP address, he needs to assign the
corresponding network address to his PC for the management access subsequently.
On launching the SIP Firewall WebUI, the web application will prompt to enter the
administrator credentials to login.
Alternatively the user can access the device via the static IP 10.0.0.1 and configure
the network settings during first time installation. Connect a PC to the LAN port of the SIP
Firewall and assign the IP address 10.0.0.100/255.255.255.0 to the PC. Now you can
access the device from the browser using the URL https://<10.0.0.1>
If the device is not accessible after configuring the new network configuration, Try
rebooting the device and check the device dashboard accessing via Management Vlan.

13
Figure 4: Login Page
The WebUI login session has been made to time out and if the user does not enter the
login credentials for 30 seconds and will redirect to the informational page. The user can
click the hyperlink named as ‘login’ appearing on the information page, to visit the login
page again.
Figure 5: Timeout message
If somebody is already logged in to SIP Firewall WebUI session, the subsequent attempts
to login will notify the details previous login session as illustrated below and will prompt
the user to override the previous session and continue OR to discard the attempt the
login.

14
Figure 6: Select Login attempt
2.4 WebUI Session timeout
After logging into the WebUI, if there is no activity until the WebUI session timeout period
(By default, the WebUI session timeout is set to 900 seconds), then the login session will
automatically terminated and browser will be redirected to login page again.
2.5 WebUI Settings
To change the WebUI settings, click the settings icon that appears top right corner (below
the Apply Changes button). The WebUI settings dialog will be displayed in the browser
and allow the administrator to configure WebUI session timeout & WebUI login password.
To configure the WebUI login password, the user needs to enter the previously set
administrator password.
Figure 7: WebUI Settings

15
2.4 Dashboard
Figure 8: Dashboard
On logging into the SIP Firewall WebUI, the dashboard will be shown.
The user can visit the dashboard page from the any configuration page in the SIP Firewall
WebUI, by clicking the SIP Firewall Product Icon that appears in the left corner of the Top
panel.
The status panel that appears below the top panel shows the time settings on the device
and SIP Firewall firmware version, Page refresh icon and Setting icon.
On clicking the page refresh button, the main content area in the current page will be
refreshed.
On clicking the settings icon, the pop menu which contains menu options logout, WebUI
settings will be shown.
System Status Panel shows Device up time, Memory Usage, Flash Usage & CPU Usage.
Sig Update Version Panel shows the SIP Firewall Signature version and Release State.
Network Status Panel shows IP, LAN MAC, WAN MAC and Gateway of the device.
Security Alert Summary Panel shows hyperlinks for viewing of Top 10 Signatures hit, Top
10 Categories hit, Top Attacker IP Addresses & Top 10 target destinations.

16
3. Device Configuration
Configuration pages of the SIP Firewall WebUI have been made as self- intuitive and
easy to configure.
All the configuration pages have been made to work with the two-phase commit model.
The two-phase commit model is not applicable to time settings and signature
update settings. In these settings, the changes will be applied directly by clicking the
‘Apply’ in the content area of the configuration editor.
I.e. When the administrator changes the settings in the configuration pages and click the
Save button, the settings will be saved in a temporary buffer location on the device. On
saving the configuration changes, the ‘Apply Changes’ button that appears in the right top
corner will be enabled & the ‘Ignore Changes’ button will appear next.
Figure 9: Device Configuration
The number of configuration changes will appear on the immediate left to the ‘Apply
Changes’ button. To view the details of the configuration changes, the user can click the
number icon, which will open the configuration changes listing.
The user can apply the configuration changes to the device, by clicking ‘Apply Changes’
button. On clicking the ‘Apply Changes’ button, the configuration changes will be applied
to the system and updated configuration will be persisted permanently onto the device.

17
In case if the user wants to abandon the configuration changes made, he can click the
Ignore Changes button. On clicking the ‘Ignore Changes’ button, the configuration
changes stored in the temporary buffer location will be discarded.
To apply the configuration changes, the ‘Ignore Changes’ button will be displayed
and they cannot choose to ignore configuration changes. The ‘Ignore Changes’ button will
be disabled, only when there are pending configuration changes that need to be applied
yet to the device.
If the administrator tries to configure a configuration element to the inappropriate
value, the tooltip icon that appears next to each configuration element will provide the
details on the error.
On clicking the help icon that appears next to the configuration title, the help section
corresponds the current configuration page will be launched.
3.1. General Settings
The General settings page will allow configuring the host/network settings of the SIP
Firewall appliance. The device that has been made to work in bridging mode can either
choose to work with static IP assignment or to acquire the device IP via DHCP.
The page also allows to enable/disable the SSH Access to the device. The ‘Allow ICMP’
option will configure the device to respond to the ICMP ping messages sent to SIP Firewall
appliances or not.
By the SSH Access and ICMP Ping messages are allowed to the SIP Firewall appliance.
Figure 10: General Settings

18
3.2. Time Settings
The administrator can choose to set the manual time settings on the device or configure
the device to sync the time settings from an NTP server. Appropriate time settings/time
zone should be set on the device to the correct timestamp to appear on the SIP security
alerts generated by the device.
Figure 11: Date/Time Settings
3.3. Management Access
The access the SIP Firewall Device management (SSH CLI / WebUI Access) can be
restricted with the management access filters. By default, the access has been allowed to
any global address and management VLAN network configurations on the device. The
administrator can override these settings.
Other manuals for SIP Firewall
1
Table of contents
Other Elastix Firewall manuals
Popular Firewall manuals by other brands

ZyXEL Communications
ZyXEL Communications ZyWALL 110 Series Handbook
ZyXEL Communications
ZyXEL Communications ZyWall quick start guide

ZyXEL Communications
ZyXEL Communications ADSL 2+ Security Gateway user guide

3Com
3Com 3CRFW102 user guide
Fortinet
Fortinet FortiGate FortiGate-100A quick start guide

Huawei
Huawei USG6000 Series Upgrade guide