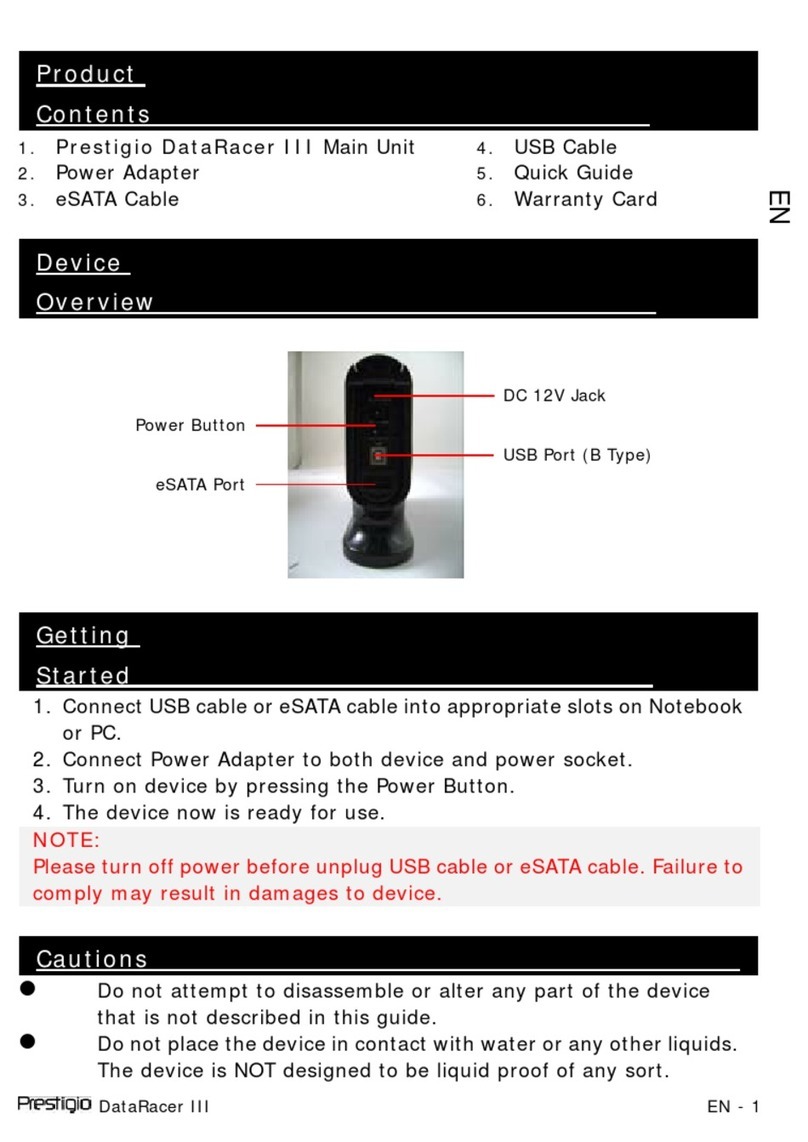
Infineon Cypress S29GL01GS User manual

www.infineon.com
Please note that Cypress is an Infineon Technologies Company.
The document following this cover page is marked as “Cypress” document as this is the
company that originally developed the product. Please note that Infineon will continue
to oer the product to new and existing customers as part of the Infineon product
portfolio.
Continuity of document content
The fact that Infineon oers the following product as part of the Infineon product
portfolio does not lead to any changes to this document. Future revisions will occur
when appropriate, and any changes will be set out on the document history page.
Continuity of ordering part numbers
Infineon continues to support existing part numbers. Please continue to use the
ordering part numbers listed in the datasheet for ordering.

Cypress Semiconductor Corporation • 198 Champion Court • San Jose,CA 95134-1709 • 408-943-2600
Document Number: 001-98285 Rev. *R Revised June 21, 2018
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
1-Gbit (128 Mbyte)/512-Mbit (64 Mbyte)/
256-Mbit (32 Mbyte)/128-Mbit (16 Mbyte),
3.0 V, GL-S Flash Memory
General Description
The Cypress® S29GL01G/512/256/128S are MirrorBit® Eclipse flash products fabricated on 65 nm process technology. These
devices offer a fast page access time as fast as 15 ns with a corresponding random access time as fast as 90 ns. They feature a
Write Buffer that allows a maximum of 256 words/512 bytes to be programmed in one operation, resulting in faster effective
programming time than standard programming algorithms. This makes these devices ideal for today’s embedded applications that
require higher density, better performance and lower power consumption.
Distinctive Characteristics
CMOS 3.0 Volt Core with Versatile I/O
65 nm MirrorBit Eclipse Technology
Single supply (VCC) for read / program / erase (2.7 V to
3.6 V)
Versatile I/O Feature
– Wide I/O voltage range (VIO): 1.65 V to VCC
×16 data bus
Asynchronous 32-byte Page read
512-byte Programming Buffer
– Programming in Page multiples, up to a maximum of
512 bytes
Single word and multiple program on same word options
Automatic Error Checking and Correction (ECC) – internal
hardware ECC with single bit error correction
Sector Erase
– Uniform 128-kbyte sectors
Suspend and Resume commands for Program and Erase
operations
Status Register, Data Polling, and Ready/Busy pin methods
to determine device status
Advanced Sector Protection (ASP)
– Volatile and non-volatile protection methods for each
sector
Separate 1024-byte One Time Program (OTP) array with two
lockable regions
Common Flash Interface (CFI) parameter table
Temperature Range / Grade
– Industrial (-40 °C to +85 °C)
– Industrial Plus(-40 °C to +105 °C)
– Automotive, AEC-Q100 Grade 3 (-40 °C to +85 °C)
– Automotive, AEC-Q100 Grade 2 (-40 °C to +105 °C)
100,000 Program / Erase Cycles
20 Years Data Retention
Packaging Options
– 56-pin TSOP
– 64-ball LAA Fortified BGA, 13 mm × 11 mm
– 64-ball LAE Fortified BGA, 9 mm × 9 mm
– 56-ball VBU Fortified BGA, 9 mm × 7 mm

Document Number: 001-98285 Rev. *R Page 3 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
Performance Summary
Maximum Read Access Times
Density Voltage Range Random Access
Time (tACC)
Page Access Time
(tPACC)
CE# Access Time
(tCE)
OE# Access Time
(tOE)
128 Mb Full VCC = VIO 90 15 90 25
VersatileIO VIO 1002510035
256 Mb Full VCC = VIO 90 15 90 25
VersatileIO VIO 1002510035
512 Mb Full VCC = VIO 1001510025
VersatileIO VIO 1102511035
1 Gb Full VCC = VIO 1001510025
VersatileIO VIO 1102511035
Typical Program and Erase Rates
Buffer Programming
(512 bytes) 1.5 MB/s
Sector Erase (128 kbytes) 477 kB/s
Maximum Current Consumption
Active Read at 5 MHz, 30 pF 60 mA
Program 100 mA
Erase 100 mA
Standby 100 µA

Document Number: 001-98285 Rev. *R Page 3 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
Contents
General Description ............................................................. 2
Distinctive Characteristics .................................................. 2
Performance Summary ........................................................ 3
1. Product Overview ........................................................ 4
2. Address Space Maps ................................................... 6
2.1 Flash Memory Array....................................................... 7
2.2 Device ID and CFI (ID-CFI) ASO ................................... 8
2.3 Device ID and Common Flash Interface (ID-CFI)
ASO Map — Automotive Only ....................................... 9
2.4 Status Register ASO.................................................... 10
2.5 Data Polling Status ASO.............................................. 10
2.6 Secure Silicon Region ASO......................................... 10
2.7 Sector Protection Control............................................. 11
2.8 ECC Status ASO.......................................................... 11
3. Data Protection .......................................................... 13
3.1 Device Protection Methods .......................................... 13
3.2 Command Protection ................................................... 13
3.3 Secure Silicon Region (OTP)....................................... 13
3.4 Sector Protection Methods........................................... 14
4. Read Operations ........................................................ 19
4.1 Asynchronous Read..................................................... 19
4.2 Page Mode Read......................................................... 19
5. Embedded Operations............................................... 20
5.1 Embedded Algorithm Controller (EAC) ........................ 20
5.2 Program and Erase Summary ..................................... 21
5.3 Automatic ECC ............................................................ 22
5.4 Command Set.............................................................. 23
5.5 Status Monitoring ......................................................... 34
5.6 Error Types and Clearing Procedures ......................... 40
5.7 Embedded Algorithm Performance Table.................... 43
6. Data Integrity .............................................................. 54
6.1 Erase Endurance ......................................................... 54
6.2 Data Retention............................................................. 54
7. Software Interface Reference ................................... 55
7.1 Command Summary.................................................... 55
7.2 Device ID and Common Flash Interface (ID-CFI)
ASO Map ..................................................................... 58
7.3 Device ID and Common Flash Interface (ID-CFI)
ASO Map ..................................................................... 63
8. Signal Descriptions ................................................... 64
8.1 Address and Data Configuration.................................. 64
8.2 Input/Output Summary................................................. 64
8.3 Versatile I/O Feature.................................................... 65
8.4 Ready/Busy# (RY/BY#) ............................................... 65
8.5 Hardware Reset........................................................... 65
9. Signal Protocols......................................................... 66
9.1 Interface States............................................................ 66
9.2 Power-Off with Hardware Data Protection ................... 66
9.3 Power Conservation Modes......................................... 67
9.4 Read ............................................................................. 67
9.5 Write ............................................................................. 68
10. Electrical Specifications............................................. 69
10.1 Absolute Maximum Ratings .......................................... 69
10.2 Latchup Characteristics ................................................ 69
10.3 Thermal Resistance...................................................... 69
10.4 Operating Ranges......................................................... 69
10.5 DC Characteristics........................................................ 72
10.6 Capacitance Characteristics ......................................... 74
11. Timing Specifications................................................. 75
11.1 Key to Switching Waveforms ........................................ 75
11.2 AC Test Conditions....................................................... 75
11.3 Power-On Reset (POR) and Warm Reset .................... 76
11.4 AC Characteristics ........................................................ 78
12. Physical Interface ....................................................... 90
12.1 56-pin TSOP ................................................................. 90
12.2 64-Ball FBGA................................................................ 92
12.3 56-Ball FBGA................................................................ 95
13. Special Handling Instructions
for FBGA Package ...................................................... 96
14. Ordering Information.................................................. 97
15. Other Resources ....................................................... 102
15.1 Cypress Flash Memory Roadmap .............................. 102
15.2 Links to Software ........................................................ 102
15.3 Links to Application Notes........................................... 102
16. Revision History........................................................ 103

Document Number: 001-98285 Rev. *R Page 4 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
1. Product Overview
The GL-S family consists of 128-Mbit to 1Gbit, 3.0 V core, Versatile I/O, non-volatile, flash memory devices. These devices have a
16-bit (word) wide data bus and use only word boundary addresses. All read accesses provide 16 bits of data on each bus transfer
cycle. All writes take 16 bits of data from each bus transfer cycle.
Figure 1.1 Block Diagram
:
Note:
** AMAX GL01GS = A25, AMAX GL512S = A24, AMAX GL256S = A23, AMAX GL128S = A22
The GL-S family combines the best features of eXecute In Place (XIP) and Data Storage flash memories. This family has the fast
random access of XIP flash along with the high density and fast program speed of Data Storage flash.
Read access to any random location takes 90 ns to 120 ns depending on device density and I/O power supply voltage. Each random
(initial) access reads an entire 32-byte aligned group of data called a Page. Other words within the same Page may be read by
changing only the low order 4 bits of word address. Each access within the same Page takes 15 ns to 30 ns. This is called Page
Mode read. Changing any of the higher word address bits will select a different Page and begin a new initial access. All read
accesses are asynchronous.
Input/Output
Buffers
X-Decoder
Y-Decoder
Chip Enable
Output Enable
Logic
Erase Voltage
Generator
PGM Voltage
Generator
Timer
VCC Detector
State
Control
Command
Register
V
CC
V
SS
V
IO
WE#
WP#
CE#
OE#
STB
STB
DQ15–DQ0
Sector Switches
RY/BY#
RESET#
Data
Latch
Y-Gating
Cell Matrix
Address Latch
AMax**–A0

Document Number: 001-98285 Rev. *R Page 5 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
The device control logic is subdivided into two parallel operating sections, the Host Interface Controller (HIC) and the Embedded
Algorithm Controller (EAC). HIC monitors signal levels on the device inputs and drives outputs as needed to complete read and write
data transfers with the host system. HIC delivers data from the currently entered address map on read transfers; places write
transfer address and data information into the EAC command memory; notifies the EAC of power transition, hardware reset, and
write transfers. The EAC looks in the command memory, after a write transfer, for legal command sequences and performs the
related Embedded Algorithms.
Changing the non-volatile data in the memory array requires a complex sequence of operations that are called Embedded
Algorithms (EA). The algorithms are managed entirely by the device internal EAC. The main algorithms perform programming and
erase of the main array data. The host system writes command codes to the flash device address space. The EAC receives the
commands, performs all the necessary steps to complete the command, and provides status information during the progress of an
EA.
The erased state of each memory bit is a logic 1. Programming changes a logic 1 (High) to a logic 0 (Low). Only an Erase operation
is able to change a 0 to a 1. An erase operation must be performed on an entire 128-kbyte aligned and length group of data call a
Sector. When shipped from Cypress all Sectors are erased.
Programming is done via a 512-byte Write Buffer. It is possible to write from 1 to 256 words, anywhere within the Write Buffer before
starting a programming operation. Within the flash memory array, each 512-byte aligned group of 512 bytes is called a Line. A
programming operation transfers volatile data from the Write Buffer to a non-volatile memory array Line. The operation is called
Write Buffer Programming.
As the device transfers each 32-byte aligned page of data that was loaded into the Write buffer to the 512-byte Flash array line,
internal logic programs an ECC Code for the Page into a portion of the memory array not visible to the host system software. The
internal logic checks the ECC information during the initial access of every array read operation. If needed, the ECC information
corrects a one bit error during the initial access time.
The Write Buffer is filled with 1’s after reset or the completion of any operation using the Write Buffer. Any locations not written to a 0
by a Write to Buffer command are by default still filled with 1’s. Any 1’s in the Write Buffer do not affect data in the memory array
during a programming operation.
As each Page of data that was loaded into the Write Buffer is transferred to a memory array Line.
Sectors may be individually protected from program and erase operations by the Advanced Sector Protection (ASP) feature set.
ASP provides several, hardware and software controlled, volatile and non-volatile, methods to select which sectors are protected
from program and erase operations.
Table 1.1 S29GL-S Address Map
Type Count Addresses
Address within Page 16 A3–A0
Address within Write Buffer 256 A7–A0
Page 4096 A15–A4
Write-Buffer-Line 256 A15–A8
Sector
1024 (1 Gb)
512 (512 Mb)
256 (256 Mb)
128 (128 Mb)
AMAX–A16

Document Number: 001-98285 Rev. *R Page 6 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
Software Interface
2. Address Space Maps
There are several separate address spaces that may appear within the address range of the flash memory device. One address
space is visible (entered) at any given time.
Flash Memory Array: the main non-volatile memory array used for storage of data that may be randomly accessed by
asynchronous read operations.
ID/CFI: a memory array used for Cypress factory programmed device characteristics information. This area contains the
Device Identification (ID) and Common Flash Interface (CFI) information tables.
Secure Silicon Region (SSR): a One Time Programmable (OTP) non-volatile memory array used for Cypress factory
programmed permanent data, and customer programmable permanent data.
Lock Register: an OTP non-volatile word used to configure the ASP features and lock the SSR.
Persistent Protection Bits (PPB): a non-volatile flash memory array with one bit for each Sector. When programmed, each
bit protects the related Sector from erasure and programming.
PPB Lock: a volatile register bit used to enable or disable programming and erasure of the PPB bits.
Password: an OTP non-volatile array used to store a 64-bit password used to enable changing the state of the PPB Lock
Bit when using Password Mode sector protection.
Dynamic Protection Bits (DYB): a volatile array with one bit for each Sector. When set, each bit protects the related Sector
from erasure and programming.
Status Register: a volatile register used to display Embedded Algorithm status.
Data Polling Status: a volatile register used as an alternate, legacy software compatible, way to display Embedded
Algorithm status.
ECC Status: provides the status of any error detection or correction action taken when reading the selected Page.
The main Flash Memory Array is the primary and default address space but, it may be overlaid by one other address space, at any
one time. Each alternate address space is called an Address Space Overlay (ASO).
Each ASO replaces (overlays) the entire flash device address range. Any address range not defined by a particular ASO address
map, is reserved for future use. All read accesses outside of an ASO address map returns non-valid (undefined) data. The locations
will display actively driven data but the meaning of whatever 1’s or 0’s appear are not defined.
There are four device operating modes that determine what appears in the flash device address space at any given time:
Read Mode
Data Polling Mode
Status Register (SR) Mode
Address Space Overlay (ASO) Mode
In Read Mode the entire Flash Memory Array may be directly read by the host system memory controller. The memory device
Embedded Algorithm Controller (EAC), puts the device in Read mode during Power-on, after a Hardware Reset, after a Command
Reset, or after an Embedded Algorithm (EA) is suspended. Read accesses and command writes are accepted in read mode. A
subset of commands are accepted in read mode when an EA is suspended.
While in any mode, the Status Register read command may be issued to cause the Status Register ASO to appear at every word
address in the device address space. In this Status Register ASO Mode, the device interface waits for a read access and, any write
access is ignored. The next read access to the device accesses the content of the status register, exits the Status Register ASO,
and returns to the previous (calling) mode in which the Status Register read command was received.
In EA mode the EAC is performing an Embedded Algorithm, such as programming or erasing a non-volatile memory array. While in
EA mode, none of the main Flash Memory Array is readable because the entire flash device address space is replaced by the Data
Polling Status ASO. Data Polling Status will appear at every word location in the device address space.

Document Number: 001-98285 Rev. *R Page 7 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
While in EA mode, only a Program / Erase suspend command or the Status Register Read command will be accepted. All other
commands are ignored. Thus, no other ASO may be entered from the EA mode.
When an Embedded Algorithm is suspended, the Data Polling ASO is visible until the device has suspended the EA. When the EA
is suspended the Data Polling ASO is exited and Flash Array data is available. The Data Polling ASO is reentered when the
suspended EA is resumed, until the EA is again suspended or finished. When an Embedded Algorithm is completed, the Data
Polling ASO is exited and the device goes to the previous (calling) mode (from which the Embedded Algorithm was started).
In ASO mode, one of the remaining overlay address spaces is entered (overlaid on the main Flash Array address map). Only one
ASO may be entered at any one time. Commands to the device affect the currently entered ASO. Only certain commands are valid
for each ASO. These are listed in the Table 7.1 on page 55, in each ASO related section of the table.
The following ASOs have non-volatile data that may be programmed to change 1’s to 0’s:
Secure Silicon Region
Lock Register
Persistent Protection Bits (PPB)
Password
Only the PPB ASO has non-volatile data that may be erased to change 0’s to 1’s
When a program or erase command is issued while one of the non-volatile ASOs is entered, the EA operates on the ASO. The ASO
is not readable while the EA is active. When the EA is completed the ASO remains entered and is again readable. Suspend and
Resume commands are ignored during an EA operating on any of these ASOs.
2.1 Flash Memory Array
The S29GL-S family has uniform sector architecture with a sector size of 128 kB. Table 2.1 to Table 2.4 shows the sector
architecture of the four devices.
Table 2.1 S29GL01GS Sector and Memory Address Map
Sector Size (kbyte) Sector Count Sector Range Address Range
(16-Bit) Notes
128 1024
SA00 0000000h–000FFFFh Sector Starting Address
::–
SA1023 3FF0000h–3FFFFFFh Sector Ending Address
Table 2.2 S29GL512S Sector and Memory Address Map
Sector Size (kbyte) Sector Count Sector Range Address Range
(16-Bit) Notes
128 512
SA00 0000000h–000FFFFh Sector Starting Address
::–
SA511 1FF0000h–1FFFFFFh Sector Ending Address
Table 2.3 S29GL256S Sector and Memory Address Map
Sector Size (kbyte) Sector Count Sector Range Address Range
(16-Bit) Notes
128 256
SA00 0000000h–000FFFFh Sector Starting Address
::–
SA255 0FF0000h–0FFFFFFh Sector Ending Address

Document Number: 001-98285 Rev. *R Page 8 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
Note: These tables have been condensed to show sector related information for an entire device on a single page Sectors and their
address ranges that are not explicitly listed (such as SA001-SA510) have sectors starting and ending addresses that form the same
pattern as all other sectors of that size. For example, all 128 kB sectors have the pattern XXX0000h–XXXFFFFh.
2.2 Device ID and CFI (ID-CFI) ASO
There are two traditional methods for systems to identify the type of flash memory installed in the system. One has traditionally been
called Autoselect and is now referred to as Device Identification (ID). The other method is called Common Flash Interface (CFI).
For ID, a command is used to enable an address space overlay where up to 16 word locations can be read to get JEDEC
manufacturer identification (ID), device ID, and some configuration and protection status information from the flash memory. The
system can use the manufacturer and device IDs to select the appropriate driver software to use with the flash device.
CFI also uses a command to enable an address space overlay where an extendable table of standard information about how the
flash memory is organized and operates can be read. With this method the driver software does not have to be written with the
specifics of each possible memory device in mind. Instead the driver software is written in a more general way to handle many
different devices but adjusts the driver behavior based on the information in the CFI table.
Traditionally these two address spaces have used separate commands and were separate overlays. However, the mapping of these
two address spaces are non-overlapping and so can be combined in to a single address space and appear together in a single
overlay. Either of the traditional commands used to access (enter) the Autoselect (ID) or CFI overlay will cause the now combined
ID-CFI address map to appear.
The ID-CFI address map appears within, and overlays the Flash Array data of, the sector selected by the address used in the ID-CFI
enter command. While the ID-CFI ASO is entered the content of all other sectors is undefined.
The ID-CFI address map starts at location 0 of the selected sector. Locations above the maximum defined address of the ID-CFI
ASO to the maximum address of the selected sector have undefined data. The ID-CFI enter commands use the same address and
data values used on previous generation memories to access the JEDEC Manufacturer ID (Autoselect) and Common Flash
Interface (CFI) information, respectively. See Figure 11.16 on page 87 for ASO Entry timing requirements.
For the complete address map see Table7.2 onpage58.
Table 2.4 S29GL128S Sector and Memory Address Map
Sector Size (kbyte) Sector Count Sector Range Address Range
(16-Bit) Notes
128 128
SA00 0000000h–000FFFFh Sector Starting Address
::–
SA127 07F0000h–07FFFFFh Sector Ending Address
Table 2.5 ID-CFI Address Map Overview
Word Address Description Read / Write
(SA) + 0000h to 000Fh Device ID
(traditional Autoselect values) Read Only
(SA) + 0010h to 0079h CFI data structure Read Only
(SA) + 0080h to FFFFh Undefined Read Only

Document Number: 001-98285 Rev. *R Page 9 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
2.3 Device ID and Common Flash Interface (ID-CFI) ASO Map — Automotive Only
Fab Lot # + Wafer # + Die X Coordinate + Die Y Coordinate gives a unique ID for each device.
2.3.1 Device ID
The Joint Electron Device Engineering Council (JEDEC) standard JEP106T defines the manufacturer ID for a compliant memory.
Common industry usage defined a method and format for reading the manufacturer ID and a device specific ID from a memory
device. The manufacturer and device ID information is primarily intended for programming equipment to automatically match a
device with the corresponding programming algorithm. Cypress has added additional fields within this 32-byte address space.
The original industry format was structured to work with any memory data bus width e. g. ×8, ×16, ×32. The ID code values are
traditionally byte wide but are located at bus width address boundaries such that incrementing the device address inputs will read
successive byte, word, or double word locations with the ID codes always located in the least significant byte location of the data
bus. Because the device data bus is word wide each code byte is located in the lower half of each word location. The original
industry format made the high order byte always 0. Cypress has modified the format to use both bytes in some words of the address
space. For the detail description of the Device ID address map see Table 7.2 on page 58.
2.3.2 Common Flash Memory Interface
The JEDEC Common Flash Interface (CFI) specification (JESD68.01) defines a standardized data structure that may be read from a
flash memory device, which allows vendor-specified software algorithms to be used for entire families of devices. The data structure
contains information for system configuration such as various electrical and timing parameters, and special functions supported by
the device. Software support can then be device-independent, Device ID-independent, and forward-and-backward-compatible for
entire Flash device families.
The system can read CFI information at the addresses within the selected sector as shown in Device ID and Common Flash
Interface (ID-CFI) ASO Map on page 58.
Like the Device ID information, CFI information is structured to work with any memory data bus width e. g. ×8, ×16, ×32. The code
values are always byte wide but are located at data bus width address boundaries such that incrementing the device address reads
successive byte, word, or double word locations with the codes always located in the least significant byte location of the data bus.
Because the data bus is word wide each code byte is located in the lower half of each word location and the high order byte is
always 0.
For further information, please refer to the Cypress CFI Specification, Version 1.4 (or later), and the JEDEC publications JEP137-A
and JESD68.01. Please contact JEDEC (http://www.jedec.org) for their standards and the Cypress CFI Specification may be found
at the Cypress Website (http://www.cypress.com/cypressappnotes) at the time of this document’s publication), or contact the local
Cypress sales office listed in the website.
Word Address Data Field # of bytes Data Format Example of
Actual Data
Hex Read Out of Example
Data
(SA) + 0080h Size of Electronic
Marking 1 Hex 19 0013h
(SA) + 0081h Revision of Electronic
Marking 1 Hex 1 0001h
(SA) + 0082h Fab Lot # 7 Ascii LD87270 004Ch, 0044h, 0038h, 0037h,
0032h, 0037h, 0030h
(SA) + 0089h Wafer # 1 Hex 23 0017h
(SA) + 008Ah Die X Coordinate 1 Hex 10 000Ah
(SA) + 008Bh Die Y Coordinate 1 Hex 15 000Fh
(SA) + 008Ch Class Lot # 7 Ascii BR33150 0042h, 0052h, 0033h, 0033h,
0031h, 0035h, 0030h
(SA) + 0093h Reserved for Future 13 n/a n/a undefined

Document Number: 001-98285 Rev. *R Page 10 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
2.4 Status Register ASO
The Status Register ASO contains a single word of registered volatile status for Embedded Algorithms. When the Status Register
read command is issued, the current status is captured (by the rising edge of WE#) into the register and the ASO is entered. The
Status Register content appears on all word locations. The first read access exits the Status Register ASO (with the rising edge of
CE# or OE#) and returns to the address space map in use when the Status Register read command was issued. Write commands
will not exit the Status Register ASO state.
2.5 Data Polling Status ASO
The Data Polling Status ASO contains a single word of volatile memory indicating the progress of an EA. The Data Polling Status
ASO is entered immediately following the last write cycle of any command sequence that initiates an EA. Commands that initiate an
EA are:
Word Program
Program Buffer to Flash
Chip Erase
Sector Erase
Erase Resume / Program Resume
Program Resume Enhanced Method
Blank Check
Lock Register Program
Password Program
PPB Program
All PPB Erase
Engineering Note: The reset and write buffer abort reset commands require very short time to execute so data polling is not
supported for these commands.The Data Polling Status word appears at all word locations in the device address space. When an
EA is completed the Data Polling Status ASO is exited and the device address space returns to the address map mode where the
EA was started.
2.6 Secure Silicon Region ASO
The Secure Silicon Region (SSR) provides an extra flash memory area that can be programmed once and permanently protected
from further changes i. e. it is a One Time Program (OTP) area. The SSR is
1024 bytes in length. It consists of 512 bytes for Factory Locked Secure Silicon Region and 512 bytes for Customer Locked Secure
Silicon Region.
The sector address supplied during the Secure Silicon Entry command selects the Flash Memory Array sector that is overlaid by the
Secure Silicon Region address map. See Figure 11.16 on page 87 for ASO Entry timing requirements. The SSR is overlaid starting
at location 0 in the selected sector. Use of the sector 0 address is recommended for future compatibility. While the SSR ASO is
entered the content of all other sectors is undefined. Locations above the maximum defined address of the SSR ASO to the
maximum address of the selected sector have undefined data.
Table 2.6 Secure Silicon Region
Word Address Range Content Size
(SA) + 0000h to 00FFh Factory Locked Secure Silicon Region 512 bytes
(SA) + 0100h to 01FFh Customer Locked Secure Silicon Region 512 bytes
(SA) + 0200h to FFFFh Undefined 127 kbytes

Document Number: 001-98285 Rev. *R Page 11 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
2.7 Sector Protection Control
2.7.1 Lock Register ASO
The Lock register ASO contains a single word of OTP memory. When the ASO is entered the Lock Register appears at all word
locations in the device address space. See Figure 11.16 on page 87 for ASO Entry timing requirements. However, it is
recommended to read or program the Lock Register only at location 0 of the device address space for future compatibility.
2.7.2 Persistent Protection Bits (PPB) ASO
The PPB ASO contains one bit of a Flash Memory Array for each Sector in the device. When the PPB ASO is entered, the PPB bit
for a sector appears in the Least Significant Bit (LSB) of each address in the sector. See Figure 11.16 on page 87 for ASO Entry
timing requirements. Reading any address in a sector displays data where the LSB indicates the non-volatile protection status for
that sector. However, it is recommended to read or program the PPB only at address 0 of the sector for future compatibility. If the bit
is 0 the sector is protected against programming and erase operations. If the bit is 1 the sector is not protected by the PPB. The
sector may be protected by other features of ASP.
2.7.3 PPB LOCK ASO
The PPB Lock ASO contains a single bit of volatile memory. The bit controls whether the bits in the PPB ASO may be programmed
or erased. If the bit is 0 the PPB ASO is protected against programming and erase operations. If the bit is 1 the PPB ASO is not
protected. When the PPB Lock ASO is entered the PPB Lock bit appears in the Least Significant Bit (LSB) of each address in the
device address space. See Figure 11.16 on page 87 for ASO Entry timing requirements. However, it is recommended to read or
program the PPB Lock only at address 0 of the device for future compatibility.
2.7.4 Password ASO
The Password ASO contains four words of OTP memory. When the ASO is entered the Password appears starting at address 0 in
the device address space. See Figure 11.16 on page 87 for ASO Entry timing requirements. All locations above the forth word are
undefined.
2.7.5 Dynamic Protection Bits (DYB) ASO
The DYB ASO contains one bit of a volatile memory array for each Sector in the device. When the DYB ASO is entered, the DYB bit
for a sector appears in the Least Significant Bit (LSB) of each address in the sector. See Figure 11.16 on page 87 for ASO Entry
timing requirements. Reading any address in a sector displays data where the LSB indicates the non-volatile protection status for
that sector. However, it is recommended to read, set, or clear the DYB only at address 0 of the sector for future compatibility. If the
bit is 0 the sector is protected against programming and erase operations. If the bit is 1 the sector is not protected by the DYB. The
sector may be protected by other features of ASP.
2.8 ECC Status ASO
The system can access the ECC Status ASO by issuing the ECC Status entry command sequence during Read Mode. The ECC
Status ASO provides the status of a Single Bit Error correction when reading the selected page. Automatic ECC on page 22
describes the ECC function in more detail. See Figure 11.16 on page 87 for ASO Entry timing requirements.
The ECC Status ASO allows the following activities:
Read ECC Status for the selected page.
ASO Exit.
2.8.1 ECC Status
The contents of the ECC Status ASO indicates, for the selected ECC page, whether ECC protection has corrected an error in the
eight-bit error correction code or the 16 Words of data in the ECC page. The address specified in the ECC Status Read Command,
provided in Table7.1 onpage55 selects the ECC Page.

Document Number: 001-98285 Rev. *R Page 12 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
Table 2.7 ECC Status Word – Upper Byte
Bit151413121110 9 8
Name RFU RFU RFU RFU RFU RFU RFU RFU
ValueXXXXXXXX
Table 2.8 ECC Status Word – Lower Byte
Bit 7 6 5 4 3 2 1 0
Name RFU RFU RFU RFU RFU Single Bit Error corrected in the 8-bit
error correction code
Single Bit Error corrected in
16 words of data RFU
Value X X X X X 0 = No Error Corrected
1 = Single Bit Error Corrected
0 = No Error Corrected
1 = Single Bit Error Corrected X

Document Number: 001-98285 Rev. *R Page 13 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
3. Data Protection
The device offers several features to prevent malicious or accidental modification of any sector via hardware means.
3.1 Device Protection Methods
3.1.1 Power-Up Write Inhibit
RESET#, CE#, WE#, and, OE# are ignored during Power-On Reset (POR). During POR, the device can not be selected, will not
accept commands on the rising edge of WE#, and does not drive outputs. The Host Interface Controller (HIC) and Embedded
Algorithm Controller (EAC) are reset to their standby states, ready for reading array data, during POR. CE# or OE# must go to VIH
before the end of POR (tVCS).
At the end of POR the device conditions are:
all internal configuration information is loaded,
the device is in read mode,
the Status Register is at default value,
all bits in the DYB ASO are set to un-protect all sectors,
the Write Buffer is loaded with all 1’s,
the EAC is in the standby state.
3.1.2 Low VCC Write Inhibit
When VCC is less than VLKO, the HIC does not accept any write cycles and the EAC resets. This protects data during VCC power-up
and power-down. The system must provide the proper signals to the control pins to prevent unintentional writes when VCC is greater
than VLKO.
3.2 Command Protection
Embedded Algorithms are initiated by writing command sequences into the EAC command memory. The command memory array is
not readable by the host system and has no ASO. Each host interface write is a command or part of a command sequence to the
device. The EAC examines the address and data in each write transfer to determine if the write is part of a legal command
sequence. When a legal command sequence is complete the EAC will initiate the appropriate EA.
Writing incorrect address or data values, or writing them in an improper sequence, will generally result in the EAC returning to its
Standby state. However, such an improper command sequence may place the device in an unknown state, in which case the
system must write the reset command, or possibly provide a hardware reset by driving the RESET# signal Low, to return the EAC to
its Standby state, ready for random read.
The address provided in each write may contain a bit pattern used to help identify the write as a command to the device. The upper
portion of the address may also select the sector address on which the command operation is to be performed. The Sector Address
(SA) includes AMAX through A16 flash address bits (system byte address signals amax through a17). A command bit pattern is located
in A10 to A0 flash address bits (system byte address signals a11 through a1).
The data in each write may be: a bit pattern used to help identify the write as a command, a code that identifies the command
operation to be performed, or supply information needed to perform the operation. See Table7.1 onpage55 for a listing of all
commands accepted by the device.
3.3 Secure Silicon Region (OTP)
The Secure Silicon Region (SSR) provides an extra flash memory area that can be programmed once and permanently protected
from further changes i. e. it is a One Time Program (OTP) area. The SSR is 1024 bytes in length. It consists of 512 bytes for Factory
Locked Secure Silicon Region and 512 bytes for Customer Locked Secure Silicon Region.

Document Number: 001-98285 Rev. *R Page 14 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
3.4 Sector Protection Methods
3.4.1 Write Protect Signal
If WP# = VIL, the lowest or highest address sector is protected from program or erase operations independent of any other ASP
configuration. Whether it is the lowest or highest sector depends on the device ordering option (model) selected. If WP# = VIH, the
lowest or highest address sector is not protected by the WP# signal but it may be protected by other aspects of ASP configuration.
WP# has an internal pull-up; when unconnected, WP# is at VIH.
3.4.2 ASP
Advanced Sector Protection (ASP) is a set of independent hardware and software methods used to disable or enable programming
or erase operations, individually, in any or all sectors. This section describes the various methods of protecting data stored in the
memory array. An overview of these methods is shown in Figure 3.1.
Figure 3.1 Advanced Sector Protection Overview
Every main flash array sector has a non-volatile (PPB) and a volatile (DYB) protection bit associated with it. When either bit is 0, the
sector is protected from program and erase operations.
The PPB bits are protected from program and erase when the PPB Lock bit is 0. There are two methods for managing the state of
the PPB Lock bit, Persistent Protection and Password Protection.
Password Method
(DQ2)
Persistent Method
(DQ1)
Lock Register
(One Time Programmable)
PPB Lock Bit1,2,3
64-bit Password
(One Time Protect)
1 = PPBs Unlocked
0 = PPBs Locked
Memory Array
Sector 0
Sector 1
Sector 2
Sector N-2
Sector N-1
Sector N4
PPB 0
PPB 1
PPB 2
PPB N-2
PPB N-1
PPB N
Persistent
Protection Bit
(PPB)5,6
DYB 0
DYB 1
DYB 2
DYB N-2
DYB N-1
DYB N
Dynamic
Protection Bit
(DYB)7,8,9
7. 0 = Sector Protected,
1 = Sector Unprotected.
8. Protect effective only if corresponding PPB
is “1” (unprotected).
9. Volatile Bits: defaults to user choice upon
power-up (see ordering options).
5. 0 = Sector Protected,
1 = Sector Unprotected.
6. PPBs programmed individually,
but cleared collectively
1. Bit is volatile, and defaults to “1” on reset (to
“0” if in Password Mode).
2. Programming to “0” locks all PPBs to their
current state.
3. Once programmed to “0”, requires hardware
reset to unlock or application of the
password.
4. N = Highest Address Sector.

Document Number: 001-98285 Rev. *R Page 15 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
The Persistent Protection method sets the PPB Lock to 1 during POR or Hardware Reset so that the PPB bits are unprotected by a
device reset. There is a command to clear the PPB Lock bit to 0 to protect the PPB bits. There is no command in the Persistent
Protection method to set the PPB Lock bit therefore the PPB Lock bit will remain at 0 until the next power-off or hardware reset. The
Persistent Protection method allows boot code the option of changing sector protection by programming or erasing the PPB, then
protecting the PPB from further change for the remainder of normal system operation by clearing the PPB Lock bit. This is
sometimes called Boot-code controlled sector protection.
The Password method clears the PPB Lock bit to 0 during POR or Hardware Reset to protect the PPB. A 64-bit password may be
permanently programmed and hidden for the password method. A command can be used to provide a password for comparison with
the hidden password. If the password matches the PPB Lock bit is set to 1 to unprotect the PPB. A command can be used to clear
the PPB Lock bit to 0.
The selection of the PPB Lock management method is made by programming OTP bits in the Lock Register so as to permanently
select the method used.
The Lock Register also contains OTP bits, for protecting the SSR.
The PPB bits are erased so that all main flash array sectors are unprotected when shipped from Cypress. The Secured Silicon
Region can be factory protected or left unprotected depending on the ordering option (model) ordered.
3.4.3 PPB Lock
The Persistent Protection Bit Lock is a volatile bit for protecting all PPB bits. When cleared to 0, it locks all PPBs and when set to 1,
it allows the PPBs to be changed. There is only one PPB Lock Bit per device.
The PPB Lock command is used to clear the bit to 0. The PPB Lock Bit must be cleared to 0 only after all the PPBs are configured
to the desired settings.
In Persistent Protection mode, the PPB Lock is set to 1 during POR or a hardware reset. When cleared, no software command
sequence can set the PPB Lock, only another hardware reset or power-up can set the PPB Lock bit.
In the Password Protection mode, the PPB Lock is cleared to 0 during POR or a hardware reset. The PPB Lock can only set to 1 by
the Password Unlock command sequence. The PPB Lock can be cleared by the PPB Lock Bit Clear command.
3.4.4 Persistent Protection Bits (PPB)
The Persistent Protection Bits (PPB) are located in a separate nonvolatile flash array. One of the PPB bits is assigned to each
sector. When a PPB is 0 its related sector is protected from program and erase operations. The PPB are programmed individually
but must be erased as a group, similar to the way individual words may be programmed in the main array but an entire sector must
be erased at the same time. Preprogramming and verification prior to erasure are handled by the EAC.
Programming a PPB bit requires the typical word programming time. During a PPB bit programming operation or PPB bit erasing,
Data polling Status DQ6 Toggle Bit I will toggle until the operation is complete. Erasing all the PPBs requires typical sector erase
time.
If the PPB Lock is 0, the PPB Program or erase commands do not execute and time-out without programming or erasing the PPB.
The protection state of a PPB for a given sector can be verified by executing a PPB Status Read command when entered in the PPB
ASO.
3.4.5 Dynamic Protection Bits (DYB)
Dynamic Protection Bits are volatile and unique for each sector and can be individually modified. DYBs only control protection for
sectors that have their PPBs erased. By issuing the DYB Set or Clear command sequences, the DYB are set to 0 or cleared to 1,
thus placing each sector in the protected or unprotected state respectively, if the PPB for the Sector is 1. This feature allows
software to easily protect sectors against inadvertent changes, yet does not prevent the easy removal of protection when changes
are needed.
The DYB can be set to 0 or cleared to 1 as often as needed.

Document Number: 001-98285 Rev. *R Page 16 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
3.4.6 Sector Protection States Summary
Each sector can be in one of the following protection states:
Unlocked – The sector is unprotected and protection can be changed by a simple command. The protection state defaults
to unprotected after a power cycle or hardware reset.
Dynamically Locked – A sector is protected and protection can be changed by a simple command. The protection state is
not saved across a power cycle or hardware reset.
Persistently Locked – A sector is protected and protection can only be changed if the PPB Lock Bit is set to 1. The
protection state is non-volatile and saved across a power cycle or hardware reset. Changing the protection state requires
programming or erase of the PPB bits.
3.4.7 Lock Register
The Lock Register holds the non-volatile OTP bits for controlling protection of the SSR, and determining the PPB Lock bit
management method (protection mode).
The Secure Silicon Region (SSR) protection bits must be used with caution, as once locked, there is no procedure available for
unlocking the protected portion of the Secure Silicon Region and none of the bits in the protected Secure Silicon Region memory
space can be modified in any way. Once the Secure Silicon Region area is protected, any further attempts to program in the area will
fail with status indicating the area being programmed is protected. The Region 0 Indicator Bit is located in the Lock Register at bit
location 0 and Region 1 in bit location 6.
Table 3.1 Sector Protection States
Protection Bit Values Sector State
PPB Lock PPB DYB
1 1 1 Unprotected - PPB and DYB are changeable
1 1 0 Protected - PPB and DYB are changeable
1 0 1 Protected - PPB and DYB are changeable
1 0 0 Protected - PPB and DYB are changeable
0 1 1 Unprotected - PPB not changeable, DYB is changeable
0 1 0 Protected - PPB not changeable, DYB is changeable
0 0 1 Protected - PPB not changeable, DYB is changeable
0 0 0 Protected - PPB not changeable, DYB is changeable
Table 3.2 Lock Register
Bit Default Value Name
15-9 1 Reserved
8 0 Reserved
7 X Reserved
6 1 SSR Region 1 (Customer) Lock Bit
5 1 Reserved
4 1 Reserved
3 1 Reserved
2 1 Password Protection Mode Lock Bit
1 1 Persistent Protection Mode Lock Bit
0 0 SSR Region 0 (Factory) Lock Bit

Document Number: 001-98285 Rev. *R Page 17 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
As shipped from the factory, all devices default to the Persistent Protection method, with all sectors unprotected, when power is
applied. The device programmer or host system can then choose which sector protection method to use. Programming either of the
following two, one-time programmable, non-volatile bits, locks the part permanently in that mode:
Persistent Protection Mode Lock Bit (DQ1)
Password Protection Mode Lock Bit (DQ2)
If both lock bits are selected to be programmed at the same time, the operation will abort. Once the Password Mode Lock Bit is
programmed, the Persistent Mode Lock Bit is permanently disabled and no changes to the protection scheme are allowed. Similarly,
if the Persistent Mode Lock Bit is programmed, the Password Mode is permanently disabled.
If the password mode is to be chosen, the password must be programmed prior to setting the corresponding lock register bit. Setting
the Password Protection Mode Lock Bit is programmed, a power cycle, hardware reset, or PPB Lock Bit Set command is required to
set the PPB Lock bit to 0 to protect the PPB array.
The programming time of the Lock Register is the same as the typical word programming time. During a Lock Register programming
EA, Data polling Status DQ6 Toggle Bit I will toggle until the programming has completed. The system can also determine the status
of the lock register programming by reading the Status Register. See Status Register on page 34 for information on these status
bits.
The user is not required to program DQ2 or DQ1, and DQ6 or DQ0 bits at the same time. This allows the user to lock the SSR before
or after choosing the device protection scheme. When programming the Lock Bits, the Reserved Bits must be 1 (masked).
3.4.8 Persistent Protection Mode
The Persistent Protection method sets the PPB Lock to 1 during POR or Hardware Reset so that the PPB bits are unprotected by a
device reset. There is a command to clear the PPB Lock bit to 0 to protect the PPB. There is no command in the Persistent
Protection method to set the PPB Lock bit to 1 therefore the PPB Lock bit will remain at 0 until the next power-off or hardware reset.
3.4.9 Password Protection Mode
3.4.9.1 PPB Password Protection Mode
PPB Password Protection Mode allows an even higher level of security than the Persistent Sector Protection Mode, by requiring a
64-bit password for setting the PPB Lock. In addition to this password requirement, after power up and reset, the PPB Lock is
cleared to 0 to ensure protection at power-up. Successful execution of the Password Unlock command by entering the entire
password sets the PPB Lock to 1, allowing for sector PPB modifications.
Password Protection Notes:
The Password Program Command is only capable of programming 0’s.
The password is all 1’s when shipped from Cypress. It is located in its own memory space and is accessible through the
use of the Password Program and Password Read commands.
All 64-bit password combinations are valid as a password.
Once the Password is programmed and verified, the Password Mode Locking Bit must be set in order to prevent reading or
modification of the password.
The Password Mode Lock Bit, once programmed, prevents reading the 64-bit password on the data bus and further
password programming. All further program and read commands to the password region are disabled (data is read as 1's)
and these commands are ignored. There is no means to verify what the password is after the Password Protection Mode
Lock Bit is programmed. Password verification is only allowed before selecting the Password Protection mode.
The Password Mode Lock Bit is not erasable.
The exact password must be entered in order for the unlocking function to occur.
The addresses can be loaded in any order but all 4 words are required for a successful match to occur.

Document Number: 001-98285 Rev. *R Page 18 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
The Sector Addresses and Word Line Addresses are compared while the password address/data are loaded. If the Sector
Address don't match than the error will be reported at the end of that write cycle. The status register will return to the ready
state with the Program Status Bit set to 1, Program Status Register Bit set to 1, and Write Buffer Abort Status Bit set to 1
indicating a failed programming operation. It is a failure to change the state of the PPB Lock bit because it is still protected
by the lack of a valid password. The data polling status will remain active, with DQ7 set to the complement of the DQ7 bit in
the last word of the password unlock command, and DQ6 toggling. RY/BY# will remain low.
The specific address and data are compared after the Program Buffer To Flash command has been given. If they don't
match to the internal set value than the status register will return to the ready state with the Program Status Bit set to 1 and
Program Status Register Bit set to 1 indicating a failed programming operation. It is a failure to change the state of the PPB
Lock bit because it is still protected by the lack of a valid password. The data polling status will remain active, with DQ7 set
to the complement of the DQ7 bit in the last word of the password unlock command, and DQ6 toggling. RY/BY# will remain
low.
The device requires approximately 100 µs for setting the PPB Lock after the valid 64-bit password is given to the device.
The Password Unlock command cannot be accepted any faster than once every 100 µs ± 20 µs. This makes it take an
unreasonably long time (58 million years) for a hacker to run through all the 64-bit combinations in an attempt to correctly
match a password. The EA status checking methods may be used to determine when the EAC is ready to accept a new
password command.
If the password is lost after setting the Password Mode Lock Bit, there is no way to clear the PPB Lock.

Document Number: 001-98285 Rev. *R Page 19 of 108
S29GL01GS/S29GL512S
S29GL256S/S29GL128S
4. Read Operations
4.1 Asynchronous Read
Each read access may be made to any location in the memory (random access). Each random access is self-timed with the same
latency from CE# or address to valid data (tACC or tCE).
4.2 Page Mode Read
Each random read accesses an entire 32-byte Page in parallel. Subsequent reads within the same Page have faster read access
speed. The Page is selected by the higher address bits (AMAX–A4), while the specific word of that page is selected by the least
significant address bits A3–A0. The higher address bits are kept constant and only A3–A0 changed to select a different word in the
same Page. This is an asynchronous access with data appearing on DQ15-DQ0 when CE# remains Low, OE# remains Low, and
the asynchronous Page access time (tPACC) is satisfied. If CE# goes High and returns Low for a subsequent access, a random read
access is performed and time is required (tACC or tCE).
This manual suits for next models
3
Table of contents
Popular Storage manuals by other brands
IOGear
IOGear Combo ION GHE835C user manual

NetApp
NetApp AFF A900 Installation and setup instructions
POPCORN HOUR
POPCORN HOUR A-210 installation guide

Immergas
Immergas Hercules Condensing 26 2 E manual

Dell
Dell POWER VAULT 130T LIBRARY 130T Safety booklet

Ultra Products
Ultra Products USB Flash Drives FlyDrive Specifications