Table of Contents
1Introduction ...................................................................................................................1
2IE Remote Access...........................................................................................................2
2.1 LAN........................................................................................................................2
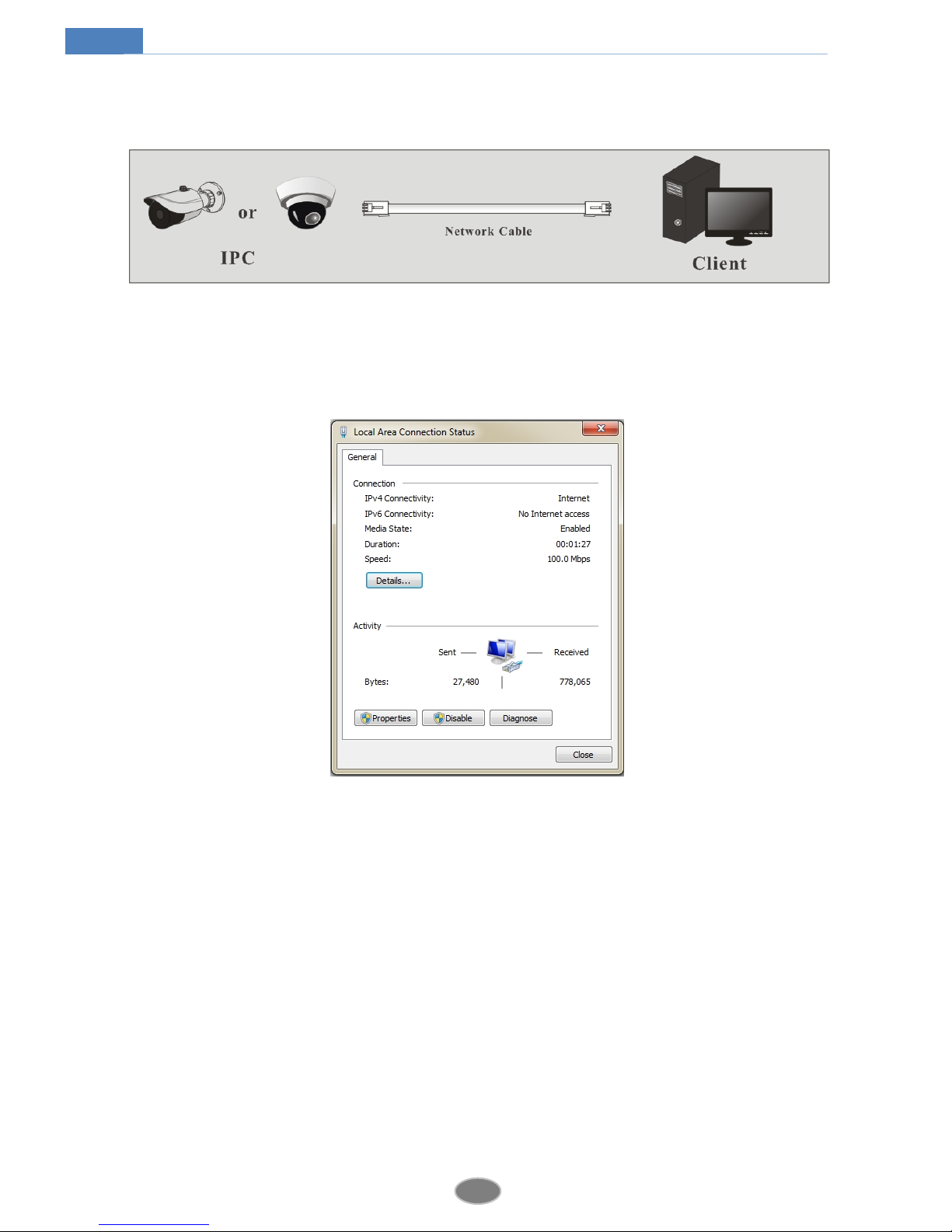
2.1.1 Access through IP-Tool ............................................................................2
2.1.2 Directly Access through IE.......................................................................3
2.2 WAN.......................................................................................................................5
3Remote Preview .............................................................................................................8
4Remote Live Surveillance..............................................................................................9
4.1 System Configuration.............................................................................................9
4.1.1 Basic Information .....................................................................................9
4.1.2 Date and Time ..........................................................................................9
4.1.3 Local Config...........................................................................................10
4.2 Image Configuration.............................................................................................10
4.2.1 Display Configuration ............................................................................10
4.2.2 Video Configuration...............................................................................11
4.2.3 OSD Configuration.................................................................................12
4.2.4 Video Mask ............................................................................................12
4.2.5 ROI Configuration..................................................................................13
4.3 Alarm Configuration ............................................................................................14
4.3.1 Motion Detection....................................................................................14
4.3.2 Alarm Server ..........................................................................................16
4.4 Network Configuration.........................................................................................17
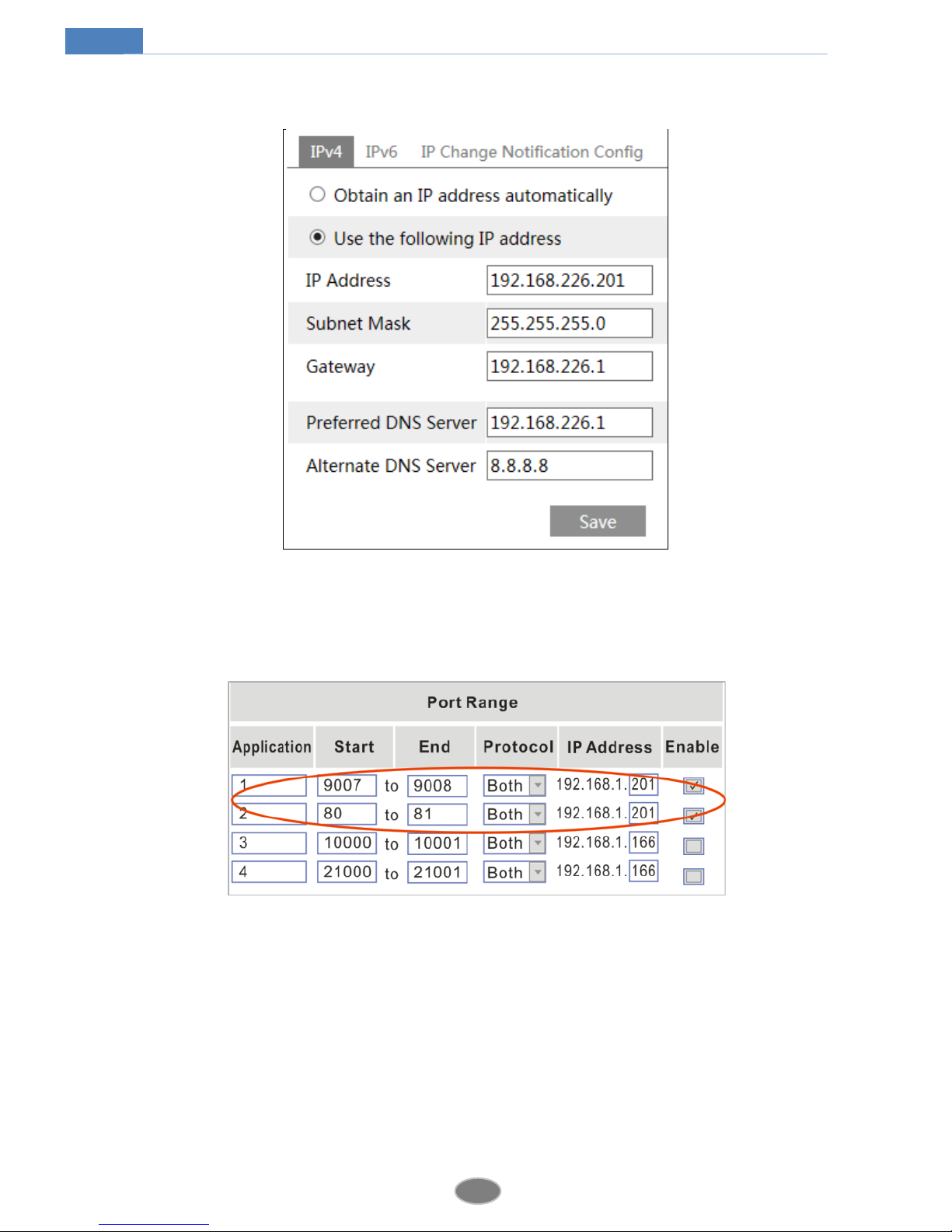
4.4.1 TCP/IP....................................................................................................17
4.4.2 Port .........................................................................................................18
4.4.3 Server Configuration ..............................................................................18
4.4.4 DDNS.....................................................................................................18
4.4.5 RTSP.......................................................................................................20
4.4.6 UPNP......................................................................................................20
4.4.7 Email ......................................................................................................21
4.5 Security Configuration .........................................................................................21
4.5.1 User Configuration .................................................................................21
4.5.2 Online User.............................................................................................23
4.5.3 Block and Allow Lists ............................................................................23
4.6 Maintenance Configuration..................................................................................24
4.6.1 Backup and Restore................................................................................24
4.6.2 Reboot ....................................................................................................25
4.6.3 Upgrade ..................................................................................................25
4.6.4 Operation Log.........................................................................................26
5Record Search..............................................................................................................27
Appendix................................................................................................................................28