Tavve zoneranger User manual

ZoneRanger
User’s Guide
Tavve Software Company
www.tavve.com

Copyright
Copyright © 1999–2013 Tavve Software Company
All rights reserved
Printed in SA.
Document Version 5.5 2013
Restricted rights legend
Software and the accompanying documentation are provided to the .S. Government in a transaction subject
to the Federal Acquisition Regulations with Restricted Rights.
se, reproduction, or disclosure is subject to restrictions set forth in the commercial license terms and
conditions between Tavve Software Company and the Customer.
Trademarks
CiscoWorks is a registered trademark of Cisco Systems, Inc.
CiscoSecure ACS is a registered trademark of Cisco Systems, Inc.
ZoneRanger is a trademark of Tavve Software Company.
HP NNM is a registered trademark of Hewlett-Packard Company.
Tivoli NetView is a registered trademark of Tivoli Systems and IBM company.
OpenVPN is a trademark of OpenVPN Solutions LLC.
Copyright reference
Copyright © 1999-2003 Intalio Inc. All Rights Reserved.
Copyright ©1999-2013 The Apache Software Foundation. All Rights reserved.
Copyright © 2003-2012 Sun Microsystems, Inc. All Rights Reserved.
V1.2.x enhancements, (c) 2005, Multiplan Consultants Ltd.
Copyright © 2000 Just Objects B.V. <just@justobjects.nl>
Copyright © 2000-2004, XDoclet Team. All rights reserved.
Copyright © 1996-2008, The PostgreSQL Global Development Group
Copyright © 1994, The Regents of the niversity of California
Copyright (C) 1991, 1999 Free Software Foundation, Inc.
Copyright (c) 2000 - 2012 The Legion Of The Bouncy Castle
Copyright (c) 2005-2008 Sam Stephenson
Copyright (c) 2002-2008 Atsuhiko Yamanaka, Jcraft, Inc. All rights reserved.
Copyright (c) 2002-2006, A. Abram White. All rights reserved.
Copyright (c) 2002,2003, Stefan Haustein, Oberhausen, Rhld., Germany.
Copyright (c) 2000, 2009 OSGi Alliance.
Third-party software from the following may be included with your product and is subject to the software
license agreement:
Copyright 1998 Carnegie Mellon niversity. All rights reserved. The name of the niversity may not be
used to endorse or promote products derived from this software without specific prior written
permission.
ZoneRanger 5.5 User's Guide 2

ZoneRanger 5.5 User's Guide 3

Preface
About ZoneRanger
The ZoneRanger appliance provides enterprises with a mechanism for extending the reach of
management applications into firewall-protected networks. ZoneRanger, working together with the
Ranger Gateway software component, serves as a proxy firewall for management traffic,
simultaneously enabling the flow of management traffic between applications and devices, and
inspecting/filtering the traffic in order to mitigate security risks.
ZoneRanger has been designed for demilitarized zones (DMZs), which are the most common form
of firewall-protected network, but can also be used in any situation where firewalls prevent the
normal flow of management protocol traffic.
About this Guide
This guide provides detailed information intended to help users successfully deploy, configure and
operate ZoneRangers within their networks. Topics covered include:
•The ZoneRanger architecture
•Deployment arrangements and options for ZoneRanger and Ranger Gateway
•Foundational concepts and mechanisms required to understand, install, configure, and
operate ZoneRangers and Ranger Gateways
•Proxy and management services provided by ZoneRanger
•ZoneRanger and Ranger Gateway user interfaces
Audience
This guide is intended for persons with a good understanding of network protocols and the
management of networks in general.
Technical Support
Technical assistance is available when you purchase a support contract.
Support covers the ZoneRanger device, the Ranger Gateway software, and the technical
documentation. Please have the ZoneRanger serial number located on the back of the device ready
before calling Tavve technical support.
You can contact Tavve technical support at:
•E-mail:support@tavve.com
•Telephone:+1 919-654-1235
•Fax: +1 919-380-7147
ZoneRanger 5.5 User's Guide 4

ocument Organization
This guide is divided into six sections:
•Part I, ZoneRanger and Ranger Gateway Overview, describes the architecture of the
ZoneRanger and Ranger Gateway within a network environment. This section provides the
reader with a framework for how the ZoneRanger and Ranger Gateway are deployed and
operate within the enterprise.
•Part II, ZoneRanger Concepts, describes the high level concepts employed by the
ZoneRanger and Ranger Gateway. nderstanding of ZoneRanger and Ranger Gateway
concepts is a necessary prerequisite for the rest of this guide.
•Part III, ZoneRanger Services, describes the proxy and management services provided by
ZoneRanger and Ranger Gateway. The functionality of each service is described in detail,
along with associated deployment and configuration options.
•Part IV, ZoneRanger User Interfaces, provides reference documentation for the various
user interfaces used to configure and operate the ZoneRanger and the Ranger Gateway.
•Part V, ZoneRanger App ications, describes separately licensed ZoneRanger feature sets
for specific management applications.
•Appendices, provides additional information on miscellaneous topics associated with
ZoneRanger and Ranger Gateway.
ZoneRanger 5.5 User's Guide 5

Table of Contents
Preface ...........................................................................................................................................................................4
Part I. ZoneRanger and Ranger Gateway Overview....................................................................................................8
Chapter 1: Zone Ranger and Ranger Gateway Architecture....................................................................................8
Part II. ZoneRanger Concepts.....................................................................................................................................13
Chapter 2: Address Patterns.....................................................................................................................................15
Chapter 3: Address Transforms...............................................................................................................................16
Chapter 4: Audit.......................................................................................................................................................18
Chapter 5: Backups/Profiles....................................................................................................................................20
Chapter 6: Destination Groups................................................................................................................................22
Chapter 7: Device Groups.......................................................................................................................................23
Chapter 8: GVI/RGVI..............................................................................................................................................25
Chapter 9: Joining....................................................................................................................................................32
Chapter 10: Licensing..............................................................................................................................................34
Chapter 11: Managed Nodes...................................................................................................................................35
Chapter 12: Node Groups........................................................................................................................................36
Chapter 13: Pooling/Redundancy/VIP/Grouping...................................................................................................37
Chapter 14: Proxy Access Control..........................................................................................................................41
Chapter 15: Proxy Caching.....................................................................................................................................46
Chapter 16: Proxy Map............................................................................................................................................48
Chapter 17: Server Groups......................................................................................................................................54
Chapter 18: Whitelist...............................................................................................................................................57
Part III. ZoneRanger Services.....................................................................................................................................58
Chapter 19: Discovery.............................................................................................................................................58
Chapter 20: Forwarding...........................................................................................................................................61
Chapter 21: FTP Proxy............................................................................................................................................65
Chapter 22: HTTP/HTTPS Proxy...........................................................................................................................67
Chapter 23: ICMP Proxy.........................................................................................................................................73
Chapter 24: NTP Proxy............................................................................................................................................74
Chapter 25: Polling..................................................................................................................................................77
Chapter 26: Root Cause...........................................................................................................................................79
Chapter 27: SNMP Proxy........................................................................................................................................80
Chapter 28: TCP Proxy............................................................................................................................................91
Chapter 29: Telnet/SSH Proxy................................................................................................................................93
Chapter 30: TACACS+/RADI S Proxy...............................................................................................................102
Chapter 31: TFTP Proxy........................................................................................................................................108
Chapter 32: Traffic Monitoring.............................................................................................................................110
Chapter 33: Whitelisting........................................................................................................................................111
Part IV. ZoneRanger and Ranger Gateway Interfaces..............................................................................................112
Chapter 34: ZoneRanger Web Interface................................................................................................................113
Chapter 35: Ranger Gateway Viewer....................................................................................................................208
Chapter 36: ZoneRanger Text Interface................................................................................................................240
Chapter 37: Ranger Gateway Command Interface...............................................................................................291
Part V. ZoneRanger Applications..............................................................................................................................340
Chapter 38: HP OM...............................................................................................................................................341
Chapter 39: Web File.............................................................................................................................................347
Appendices.................................................................................................................................................................353
A. SNMP Agent.....................................................................................................................................................353
B. ZoneRanger and Ranger Gateway Traps.........................................................................................................360
C. SOCKS..............................................................................................................................................................365
D. IP Address Aliasing...........................................................................................................................................367
ZoneRanger 5.5 User's Guide 6

E. SSL Communications between ZoneRanger and Ranger Gateway................................................................370
F. Accessing ZoneRanger Though the Ranger Gateway......................................................................................372
G. ZoneRanger Technician Access........................................................................................................................374
H. Installation.........................................................................................................................................................375
I. Installing Ranger Gateway in Solaris 10 Zones................................................................................................377
J. RGVI Client Installation and Configuration.....................................................................................................378
ZoneRanger 5.5 User's Guide 7
Part I. ZoneRanger and Ranger Gateway Overview
Chapter 1: Zone Ranger and Ranger Gateway Architecture
Introduction and eployment Architecture
ZoneRanger is a hardware appliance that provides enterprises with a mechanism for extending the
reach of management applications into firewall-protected networks. ZoneRanger, working together
with the Ranger Gateway software component, serves as a proxy firewall for management traffic,
simultaneously enabling the flow of management traffic between applications and devices, and
inspecting/filtering the traffic in order to mitigate security risks.
ZoneRangers are typically installed in a network zones, such as a DMZ, where there are devices to
be managed that management applications are unable to reach due to firewall-based network
partitioning. The Ranger Gateway software component is typically installed on the same server as
the management application, and acts as the interface between the management application and one
or more ZoneRangers. Ranger Gateway functions as a transparent proxy, intercepting and relaying
management protocol traffic addressed for managed devices, so that the management application
can remain unaware that the Ranger Gateway and ZoneRanger are being used. As a result,
ZoneRanger and Ranger Gateway can be used with a wide variety of management applications.
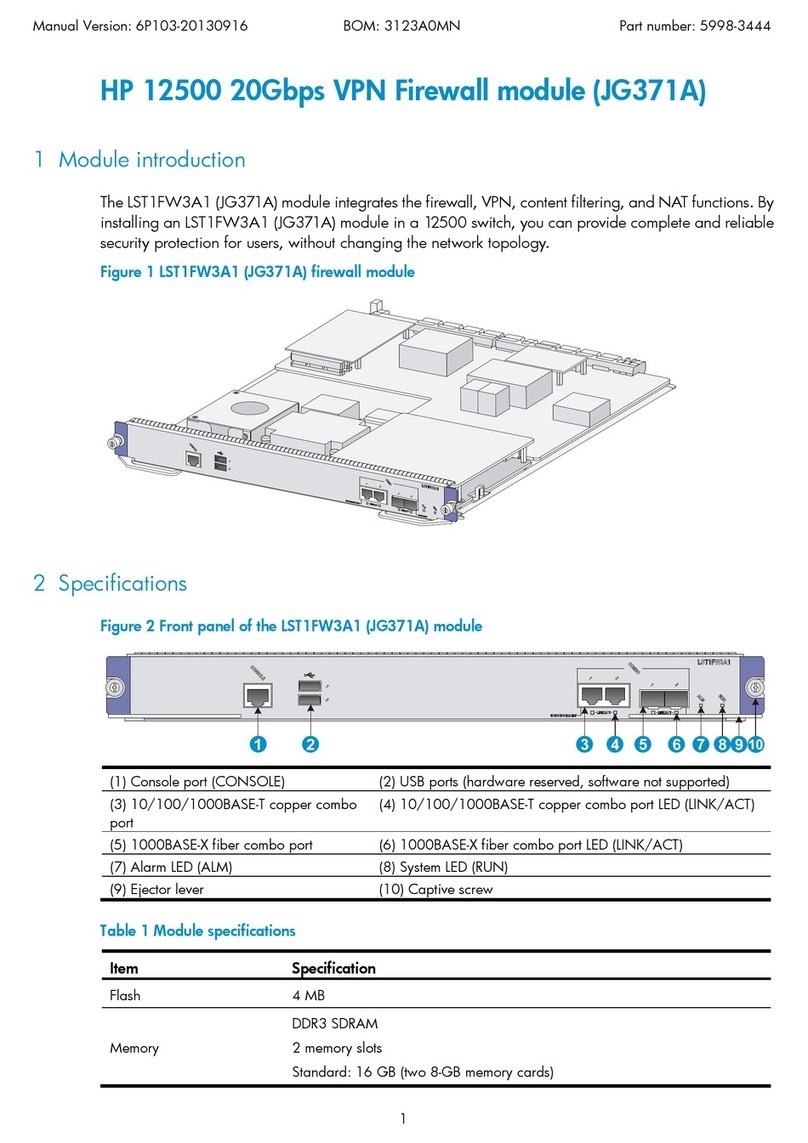
A simple ZoneRanger configuration is illustrated in the following figure.
Figure 1-1. Simple ZoneRanger configuration
Note that the Ranger Gateway software is installed on the same server as the management
application (e.g. CiscoWorks), and that the ZoneRanger is installed in the remote network alongside
the managed devices. The Ranger Gateway and ZoneRanger communicate using a single SSL-
encrypted TCP connection. All management protocol traffic being proxied through the ZoneRanger
is multiplexed over this single connection, resulting in a dramatic reduction in firewall rules and
associated configuration effort.
ZoneRanger 5.5 User's Guide 8

The following figure shows a more advanced ZoneRanger deployment scenario.
Figure 1-2. Advanced ZoneRanger configuration
In this scenario there are multiple remote networks to be managed (i.e. multiple DMZ’s), and
multiple management applications. A redundant pair of ZoneRangers is installed in each DMZ, and
instances of the Ranger Gateway (RG) software have been installed on the majority of the
management application servers. An SSL-encrypted TCP connection is maintained between each
Ranger Gateway instance and each ZoneRanger, so that each management application is able to
reach all of the DMZ devices that need to be managed. As a result, there is a many-to-many
relationship between Ranger Gateways and ZoneRangers: each Ranger Gateway instance can be
joined to multiple ZoneRangers and each ZoneRanger can be joined to multiple Ranger Gateways.
The figure also shows two management application servers, one with CiscoSecure ACS and one
with a Trap/Syslog Receiver, that do not have the Ranger Gateway software installed, but instead
interact with the ZoneRangers using Ranger Gateway software installed on another server.
Depending on the nature of the management application, the management protocols being used, and
the server hardware involved, this simplified approach may be advantageous in some situations. In
most cases, however, installing the Ranger Gateway on the same server as the management
application is the preferred approach.
Ranger Gateway software can be installed on any of the various hardware platforms that support the
following operating systems:
•Centos 5.2 or later
•Red Hat Enterprise Linux version 4.0 or higher
•Solaris 2.8 or higher
•SuSE Linux version 11.1 or higher
•Windows XP, Server 2000, Server 2003, 2008 Server, 2008 Server R2
ZoneRanger Services
The primary function of the ZoneRanger is to act as an application-layer proxy firewall for the
protocols most typically used by management applications. ZoneRanger provides proxy services
covering a variety of protocol scenarios:
ZoneRanger 5.5 User's Guide 9

•Request/response protocols, where the requests are originated by the management
application:
─ICMP
─SNMP
•Request/response protocols, where the requests are originated by the managed devices:
─TACACS+
─RADI S
─NTP
─Generic TCP
•Session-oriented protocols, where the sessions are initiated by the management
applications:
─SSH
─HTTPS
•Event/notification protocols, where events are generated by managed devices and are
filtered and forwarded to management applications:
─SNMP
─Syslog
─NetFlow
─sFlow
─Generic DP
•File transfer protocols, where the transfers are initiated by the management applications:
─FTP
─TFTP1
ZoneRanger’s proxy services are transparent, in that management applications are not specifically
aware that the Ranger Gateway and ZoneRanger are being used, and do not need to be configured in
a special way in order to incorporate the use of the proxy. This approach simplifies management
application configuration, and enables ZoneRanger and Ranger Gateway to be used with a wide
variety of management applications.
In addition to its role as a management proxy firewall, ZoneRanger can also be configured to act as
a remote management station, performing network discovery, IP, SNMP, and TCP polling, and root
cause analysis. As a result, users have the option of having their management applications poll their
managed devices, with the ZoneRanger acting as a proxy firewall for the polling traffic, or having
the ZoneRanger poll the managed devices, and forward status traps to their management
applications.
User Interfaces
Each ZoneRanger and Ranger Gateway instance can be configured and administered using a text-
based, command-line style user interface, or a graphical user interface. The user interfaces for
ZoneRanger and Ranger Gateway are described further in the following sections.
1 ZoneRanger also provides limited support for TFTP transfers initiated by managed devices.
ZoneRanger 5.5 User's Guide 10
ZoneRanger User Interfaces
ZoneRanger provides two primary user interfaces:
•A web based interface that can be accessed directly via HTTP on TCP port 80 or HTTPS on
TCP port 443, or via proxy through a joined Ranger Gateway.
•A text-based command-line interface that can be accessed directly via Telnet on TCP port
23, or SSH on TCP port 22, or via proxy through a joined Ranger Gateway.
When accessing the ZoneRanger through either the web interface or text interface, you will need to
authenticate with a login ID and password. ZoneRangers support two authorization levels
(Administrator and Operator) and are shipped with the following initial user configuration:
User Name Password Access Level
admin admin Administration
operator operator Operator
When using the web interface, the administrator authorization level enables access to all
ZoneRanger configuration and operation menus. sers having operator access are able to view the
ZoneRanger status, and information regarding managed devices and associated protocol traffic, but
are not allowed to configure the ZoneRanger or initiate administrative actions. For security, users
are automatically logged out of the ZoneRanger web interface after 30 minutes of inactivity.
Reference documentation for the ZoneRanger web interface is provided in Chapter 30.
The text interface requires administrator authorization privileges. sers with operator authorization
are not permitted to access the ZoneRanger text interface. Reference documentation for the
ZoneRanger text interface is provided in Chapter 32.
Ranger Gateway User Interfaces
Ranger Gateway provides two user interfaces:
1. A G I-based client application, called the Ranger Gateway Viewer.
2. A text-based command-line interface, consisting of a set of commands that can be executed
from an operating system shell on the server where the Ranger Gateway has been installed.
The Ranger Gateway command interface is implemented as a set of executable commands, installed
in a bin directory. In the case of Solaris and Linux, this directory also includes a command to start
the Ranger Gateway Viewer application. The location of this bin directory is dependent on the
operating system:
Operating System Directory
Linux install_dir/gateway/bin
Solaris install_dir/gateway/bin
Windows install_dir\bin
where <install_dir> is the directory where the Ranger Gateway software was installed.
To start the Ranger Gateway Viewer on a Solaris or Linux system, run the RangerGateway
command from an operating system shell. To start the Ranger Gateway Viewer on a Windows
system, select Programs > Tavve > Ranger Gateway Viewer from the Start menu. Reference
documentation for the Ranger Gateway Viewer is provided in Chapter 33.
All of the commands which comprise the Ranger Gateway command interface are executed from an
operating system shell. You can execute any command with a -? argument to display the usage
information for that command, as illustrated in the following figure.
ZoneRanger 5.5 User's Guide 11
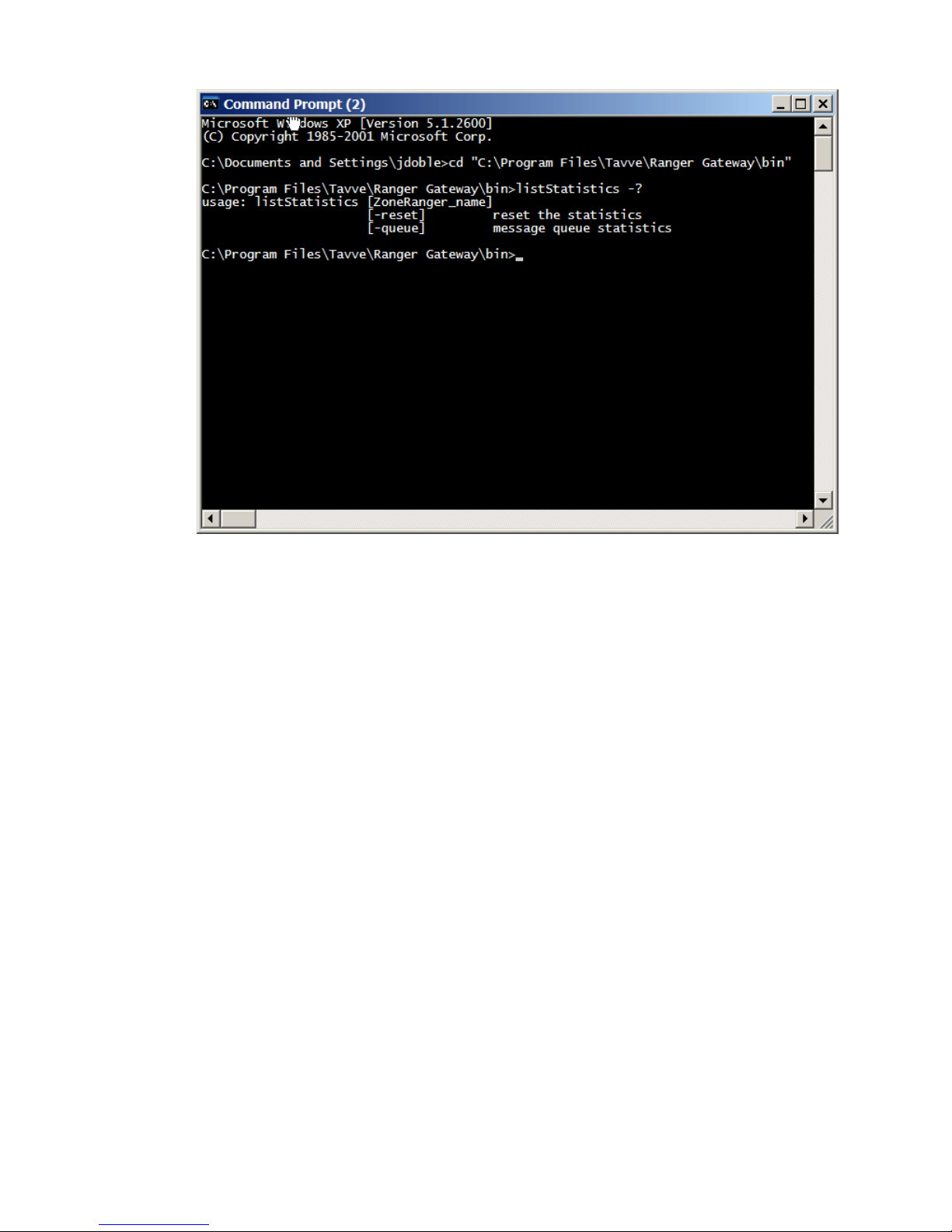
Figure 1-3. Ranger Gateway Command e ample
Reference documentation for the Ranger Gateway command interface is provided in Chapter 36.
ZoneRanger 5.5 User's Guide 12

Part II. ZoneRanger Concepts
This section introduces and describes foundational concepts and mechanisms that are important for
ZoneRanger users to understand, so that they can properly configure and administer their ZoneRangers, and
obtain maximum value from their ZoneRanger deployments. Later chapters will build on these concepts and
mechanisms and will assume that the reader is reasonably familiar with the content of this section.
The following concepts and mechanisms are discussed:
•Address Patterns – IP address or hostname values that contain wild card characters or range
descriptions and thus can describe a range of IP addresses or hostnames.
•Address Transforms – Rules that specify how to transform IP addresses or hostnames to new values
(e.g. to accommodate NAT).
•Audit – The automated process whereby Ranger Gateway and ZoneRanger perform periodic self-
checks, and, where necessary, perform corrective actions.
•Backups/Profiles – Mechanisms for saving and restoring all or part of a ZoneRanger and Ranger
Gateway configuration.
•Destination Groups – ZoneRanger mechanism for defined named groups of Ranger Gateways and
DP packet destinations to be applied to forwarding rules as a means to create and manage fewer
rules.
•Device Groups – Ranger Gateway mechanism for defining named groups of managed devices, and
using these named groups in a variety of configuration rules.
•Node Groups – ZoneRanger mechanism for defining named groups of IP address patterns, and
using these node groups in a variety of configuration rules particularly forwarding and proxy rules.
•Pooling/Redundancy/VIP/Grouping – Mechanisms for providing high availability and/or load-
balancing ZoneRanger deployments.
•Gateway Virtual Interface (GVI) and Remote Gateway Virtual Interface (RGVI) – Mechanisms
whereby the Ranger Gateway intercepts requests generated by management applications that are
destined for managed devices, so that these requests can be relayed through a ZoneRanger to the
target devices.
•Joining – The process by which a working association between Ranger Gateway and a ZoneRanger
is established.
•Managed Nodes – Mechanism whereby a ZoneRanger user identifies the set of nodes (e.g. network
devices, servers) to which ZoneRanger proxy and management services will be applied.
•Pro y Access Control – Mechanism whereby the Ranger Gateway identifies the management
protocol to be used for a given destination address, transport protocol, and destination port. Also can
be used to restrict access to proxy services based on source address, destination address, transport
protocol and destination port.
•Pro y Caching – Mechanism for reducing management traffic by saving the results of recent ICMP
and SNMP proxy requests, and, where appropriate, returning saved values instead of passing the
request along to the managed device.
•Pro y Map – Mechanism whereby the Ranger Gateway selects an appropriate ZoneRanger to proxy
a management protocol transaction, based on configured rules.
•Server Groups – ZoneRanger mechanism for defining named groups of TACACS+/RADI S
servers and associated settings.
ZoneRanger 5.5 User's Guide 13

•Whitelist – ZoneRanger mechanism to define a specific list of devices from which only those
devices will the ZoneRanger either receive data or send data.
Each of these concepts and mechanisms are described in further detail in the following chapters.
ZoneRanger 5.5 User's Guide 14

Chapter 2: Address Patterns
An address pattern is an IP address or hostname value that contains wild card characters or range
descriptions and thus can be used to describe a range of IP addresses or hostnames. Address patterns are
commonly used in Ranger Gateway and ZoneRanger commands and configuration tables, in order to
provide a concise mechanism for specifying a set of related addresses.
For example, all of the IP addresses in the 6 .1.25.0/2 subnet, can be described using the
following address pattern:
62.1.25.*
The * wildcard character can appear in any part of the address. More specific ranges can also be
specified, such as:
6 .[1-2].25.[1-10]
Wildcard characters can also be used with host names. For example:
*.company.com
or
*.*.company.com
Wildcard and non-wildcard characters cannot be combined within a part of the address. For example, the
following address patterns would not be allowed:
abc*.company.com
6 .1.25.1[6-8]
In order for a hostname pattern to match a given address, the number of address parts must match. For
example, the hostname server1.company.com matches the pattern *.company.com, but the
hostname server1.payroll.company.com does not.
ZoneRanger 5.5 User's Guide 15
Chapter 3: Address Transforms
An address transform is a simple rule that specifies how to take a given IP address or hostname value,
and transform it to a new value. Address transforms are used by the Proxy Map service in the Ranger
Gateway in order to accommodate static NAT configurations, where the address for a managed device as
specified by a management application is different from the actual address of the managed device.
Address transforms, in this case, are used to convert the device address as specified by the management
application into the real address that the ZoneRanger will use to communicate with the managed device.
For example, the following address transform indicates that the first three parts of the resulting address
should be 192.168.1, and the wild card character in the last part of the transform indicates that that
the last part of the resulting address should be copied from the original address.
192.168.1.*
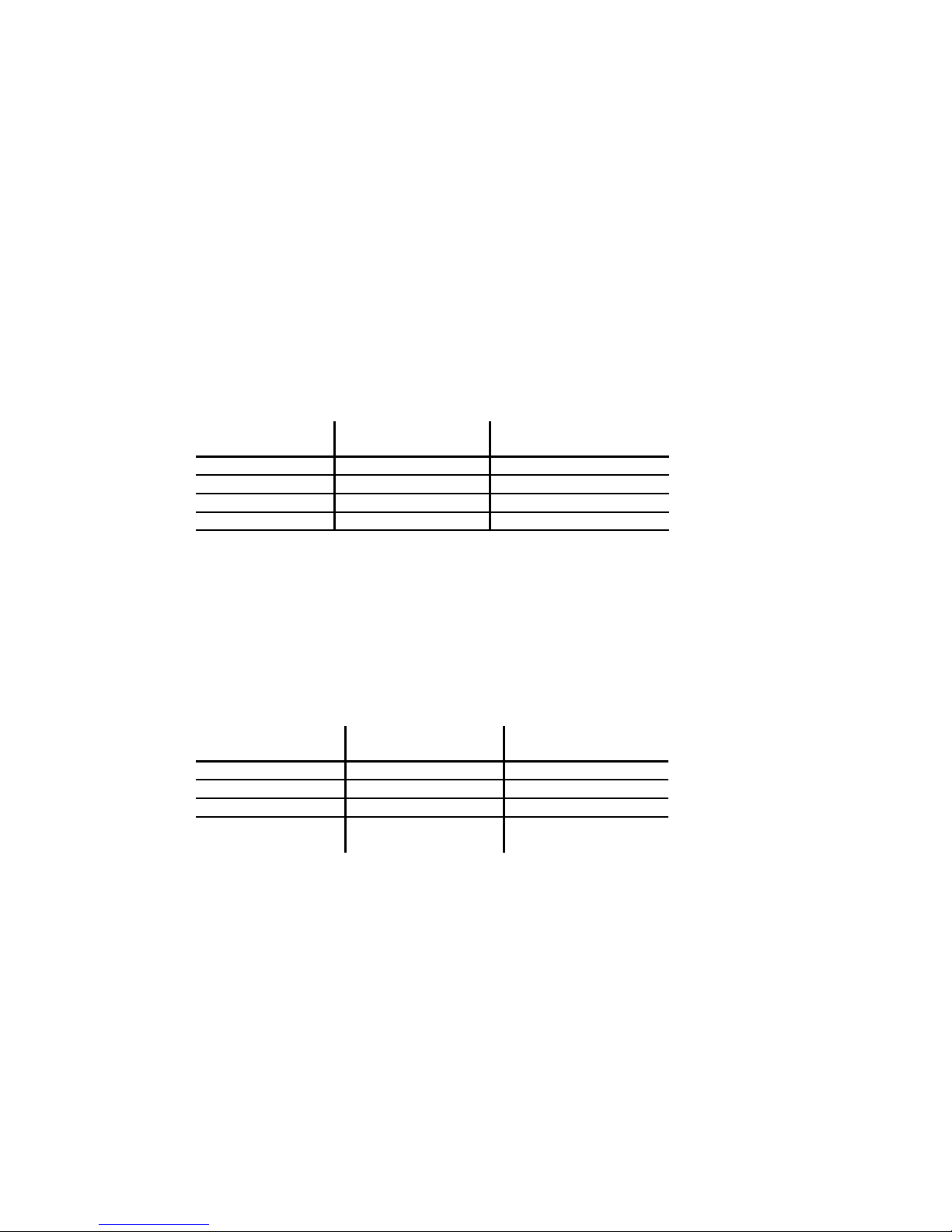
The following table illustrates the addresses that would result from applying a variety of simple address
transforms to a number of input addresses:
Original Address Address Trans orm Resulting Address
127.0.0.3 192.168.1.* 192.168.1.3
6 .2.37. 192.168.1.* 192.168.1.
6 .2.37.55 10.1.*.* 10.1.37.55
192.168.2.10 10.1.*.* 10.1.2.10
Address transforms can also perform simple computations. For example, the following address
transform indicates that the first three parts of the resulting address should be 192.168.1, and the *+2
expression in the last part of the transform indicates that that the last part of the resulting address should
be calculated by taking the last part of the original address and adding 2.
192.168.1.*+2
The following table illustrates the addresses that would result from applying a variety of address
transforms to a number of input addresses:
Original Address Address Trans orm Resulting Address
127.0.0.3 192.168.1.*+2 192.168.1.5
6 .2.37. 192.168.1.*+2 192.168.1.6
6 .2.37.25 10.1.*-2.*+2 10.1.35.27
192.168.3.200 10.1.*-2.*+2 10.1.1.202
192.168.3.25 10.1.*-2.*+10 10.1.1.8
Note that + and – are the only operations allowed, and all arithmetic is modulo 256.
Address transforms can also be used with host names. For example, the following address transform
indicates that the last two parts of the resulting hostname should be dmz1.com, and that the first part of
the hostname should be copied from the original hostname.
*.dmz1.com
The number of parts in the original hostname does not need to exactly match the number of parts in the
address transform. For example, the following table illustrates the addresses that would result from
applying the address transform *.dmz1.company.com to a variety of input hostnames:
ZoneRanger 5.5 User's Guide 16

Original Address Address Trans orm Resulting Address
host1.company.com *.dmz1.company.com host1.dmz1.company.com
host2.company.com host2.dmz1.company.com
host3.net1.company.com host3.dmz1.company.com
host .net2.branch1.company.com host .dmz1.company.com
Note that wildcard characters in address transforms always refer to the corresponding part in the input
address or hostname, as counted from left to right.
Wildcard and non-wildcard characters cannot be combined within a part of an address transform. For
example, the following address transform is invalid:
dmz*.company.com
Examples showing how address transforms can be used when dealing with NAT scenarios, or when
managing network zones with overlapping address spaces, are provided in Chapter 16.
ZoneRanger 5.5 User's Guide 17

Chapter 4: Audit
In order to provide a high level of reliability, the ZoneRanger appliance and the Ranger Gateway
software both incorporate a periodic self-audit process. The audit process in each case runs on a five-
minute interval, performing a series of pre-configured tests, verifying that services are configured
correctly, that components are able to communicate as required, and that the software is operating
properly. In the normal case, where no problems are detected, the audit will simply terminate, and
reschedule itself to run again five minutes later. If any problems are detected, the audit process will
inform the user in a variety of ways:
•The ZoneRanger web interface can be used to view the results of the most recent audit for that
ZoneRanger (on the Information section of the ZoneRanger dashboard, and on the View >
System Audit page).
•The Ranger Gateway Viewer can be used to view the results of the most recent Ranger Gateway
audit, and the results of the most recent audits for any joined ZoneRangers.
•The auditResult command on the Ranger Gateway can be used to view the results of the
most recent Ranger Gateway audit, and the results of the most recent audits for any joined
ZoneRangers.
•The audit process can be configured to send an SNMP trap whenever a problem is detected.
•The audit process can be configured to send a Syslog message whenever a problem is detected.
When audit results are presented to the user, a description of the problem being reported is provided,
along with an assessment of the severity of the problem. Two severity categories are supported:
•Major: The problem that has been detected is significant and may affect the ability of the
ZoneRanger or Ranger Gateway to provide necessary services. Corrective action should be
taken immediately.
•Minor: The problem that has been detected may impair the operation of one or more services,
but does not necessarily require immediate attention.
In addition to informing the user, the audit process may, where appropriate, automatically perform one
or more corrective actions in an attempt to resolve the problem that has been detected. The ability to
automatically correct a problem fundamentally depends on the nature of the problem. For example, if a
ZoneRanger is unable to communicate with a Ranger Gateway, or if a service has been configured
incorrectly, the audit process will notify the user, as described above, but no automatic corrective action
will be taken. If an internal software error has been detected, on the other hand, the audit process will
perform an escalating series of corrective actions, typically beginning with restarting the affected
internal service, and potentially restarting the entire software application, or, in the case of ZoneRanger,
rebooting the appliance, if a problem persists across multiple audit cycles.
It should be noted that the Ranger Gateway Viewer, the ZoneRanger web interface, and the
listAuditResults command all display the results of the most recent audit. As a result,
when a problem detected by the audit process is corrected, that problem will remain in the list of
detected problems until the next audit cycle. When the next audit cycle completes, the problem should
no longer be listed, provided that the corrective action was successful.
ZoneRanger 5.5 User's Guide 18

In addition to the primary audit process, as described above, the ZoneRanger appliance also includes a
secondary audit, which runs every thirty minutes. The goal of the secondary audit is to verify that the
primary audit is doing its job. If the secondary audit determines that the primary audit is no longer
functioning properly, the ZoneRanger appliance will be automatically rebooted. This two-layer audit
approach helps to ensure that ZoneRanger will continue to operate reliably, even when unexpected
software problems occur. Note that the Ranger Gateway does not include a comparable secondary audit,
because the Ranger Gateway software is typically installed on the same server as one or more
management applications, and users will typically prefer to keep these applications running, even if
Ranger Gateway problems are detected.
ZoneRanger 5.5 User's Guide 19

Chapter : Backups/Profiles
ZoneRanger provides two mechanisms for managing sets of configuration information: backups and
profi es. Backups and profiles are similar in that in each case, a set of configuration information for a
ZoneRanger is gathered and saved in a file that can be restored to the same ZoneRanger, or applied to a
different ZoneRanger. The primary difference between backups and profiles is that backups contain the
content of the ZoneRanger’s database of discovered devices, as well as any polling/management
configuration associated with those devices that is also stored in the database, while profiles do not.
ZoneRanger Profiles
Profiles are intended to be used as a form of configuration template, so that a ZoneRanger configuration
can be developed, captured, and easily replicated across a set of ZoneRangers that may be installed in
different network regions, and be managing different sets of devices. Backups, on the other hand, can be
used to roll back a given ZoneRanger’s configuration to a previous state, to auto-configure a new
ZoneRanger that is being added to an existing pool, or to replace an existing ZoneRanger that may have
failed or is being redeployed to another location.
Profiles are created (a.k.a. saved) using the ZoneRanger web interface, from the Administration >
Pro iles page. The user has two options with regards to the location(s) where the profile file will be
stored:
•The profile can be saved on the ZoneRanger only.
•The profile can be saved on the ZoneRanger, and also copied to a joined Ranger Gateway.
When loading (i.e. applying) a profile, the user can choose to load any profile stored on that
ZoneRanger, or stored on any joined Ranger Gateway. Note that a profile can only be loaded on a
ZoneRanger that is at the same software version as the ZoneRanger that created the profile. The
ZoneRanger web interface can also be used to delete profiles from the ZoneRanger or any joined Ranger
Gateway.
ZoneRanger Backups
Backups can be created using the ZoneRanger web interface, from the Administration >
Backup/Restore page, or by executing the Ranger Gateway backup command. When creating a
backup from the web interface, the user has two options with regards to the location(s) where the backup
file will be stored:
•The backup can be saved on the ZoneRanger only.
•The backup can be saved on the ZoneRanger, and also copied to a joined Ranger Gateway.
When creating a backup using the Ranger Gateway backup command, the backup will always be saved
on the ZoneRanger, and copied to the Ranger Gateway where the command was executed. Note that the
backup command is primarily intended to allow users to perform automated periodic backups. For
example, if the Ranger Gateway is installed on a Solaris or Linux operating system, a cron job can be
configured to run this command at scheduled times. In a similar manner, the Schedu ed Tasks
mechanism can be used to automate backups on a Windows operating systems. Backups are stored in
the Ranger Gateway store/zr/backup directory.
Backups can only be restored from the ZoneRanger web interface. When restoring from a backup, the
user can choose any backup file stored on that ZoneRanger, or stored on any joined Ranger Gateway.
Note that a backup file can only be loaded on a ZoneRanger that is at the same software version, model
number (e.g. ZR-50, ZR-200, ZR-500, ZR-SPX, or ZR-MSP) and hardware version as the ZoneRanger
that created the backup file. The ZoneRanger web interface can also be used to delete backup files from
the ZoneRanger or any joined Ranger Gateway.
ZoneRanger 5.5 User's Guide 20
Table of contents
Popular Firewall manuals by other brands
ZyXEL Communications
ZyXEL Communications ZyWALL SEM-DUAL user guide

Stormshield
Stormshield SN series PRODUCT PRESENTATION AND INSTALLATION

Vasco
Vasco Personal aXsGUARD Installation and configuration guide

Fortinet
Fortinet FortiGate-200A install guide

Draytek
Draytek VigorPro 5500 Brochure & specs

H3C
H3C H3C SECPATH F1000-S installation manual

Barracuda Networks
Barracuda Networks Spyware Firewall quick start guide

PaloAlto Networks
PaloAlto Networks ION 2000 Hardware reference

Fortinet
Fortinet FortiGate Voice Series install guide
PaloAlto Networks
PaloAlto Networks PA-415 quick start guide

Nokia
Nokia IP40 - Satellite Unlimited - Security... user guide

Stormshield
Stormshield SN900 installation instructions