Installation and Initial Setup for Versions 6.5+
Cisco Firepower Management Center Getting Started Guide 5
What to Do Next
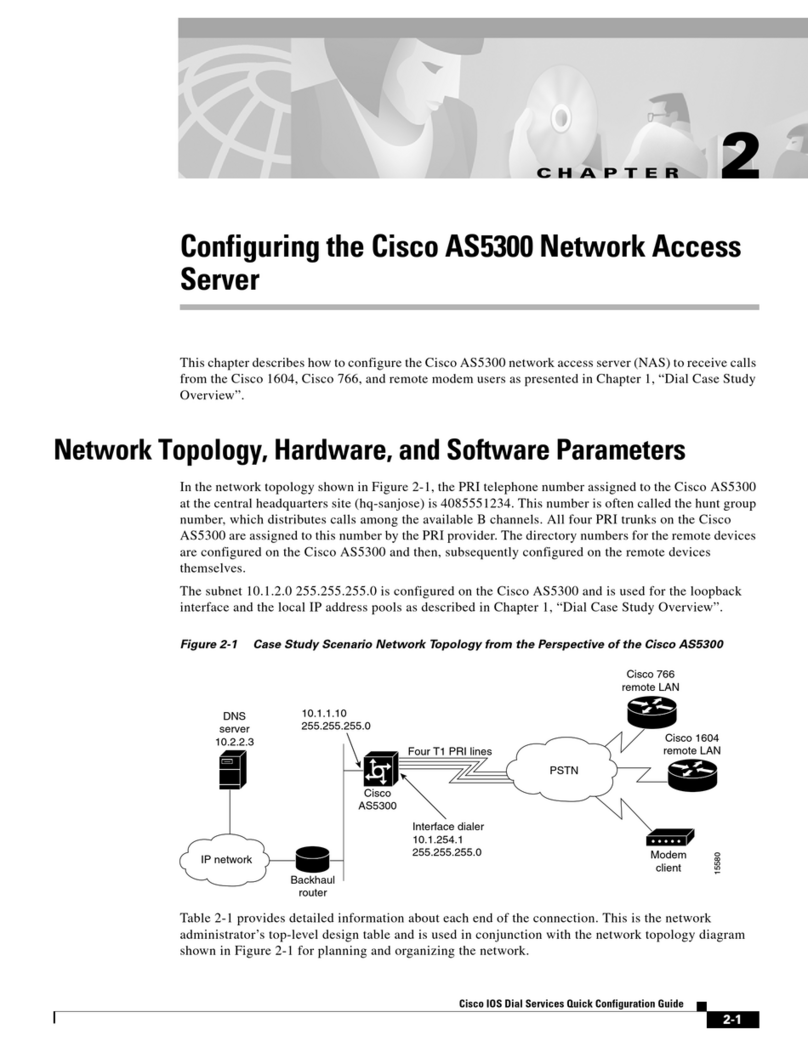
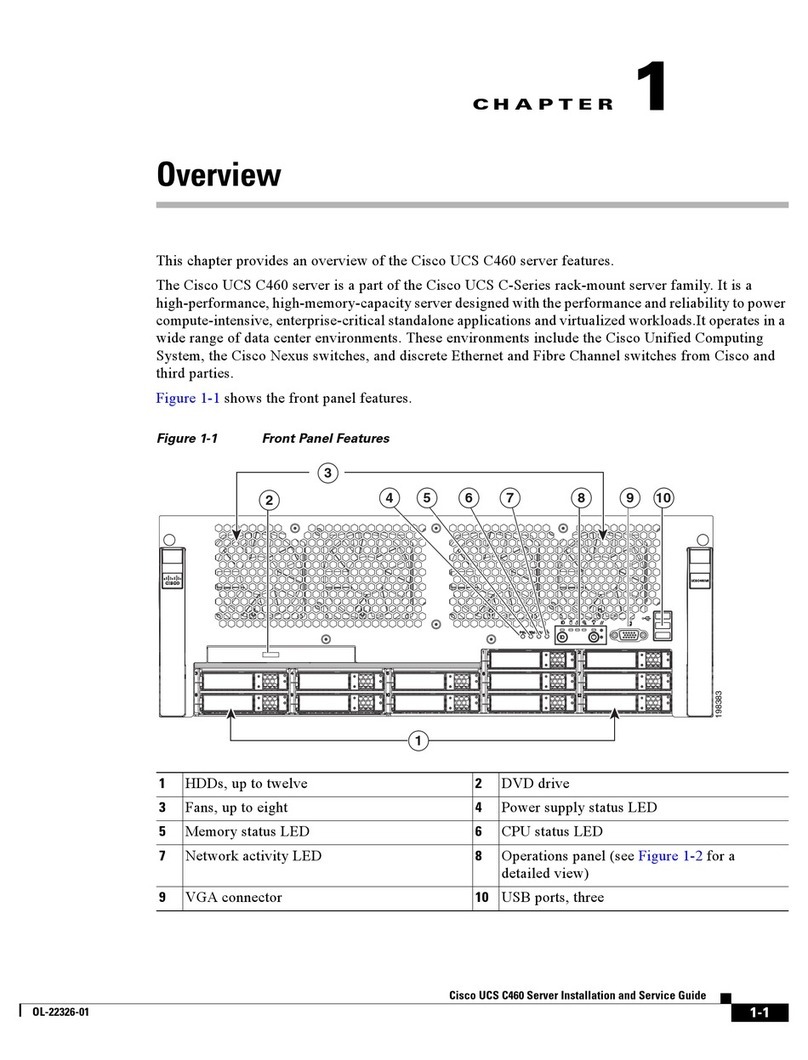
The FMC management interface is pre-configured to accept an IPv4 address assigned by DHCP, but failing to
obtain a DHCP lease, the management interface uses a fallback IPv4 address of192.168.45.45. Or, if you are
connecting to an FMC for the first time after performing a System Restore and you chose to retain license and
network settings, the IP address is the same as it was before you performed the System Restore. Ensure that
you have established one of the following methods of accessing the appliance before proceeding:
—If your network does not use DHCP and your PC cannot reach the fallback address (or the address retained
in a System Restore), we recommend you perform the initial setup by connecting a computer directly to
the FMC’s physical management interface as described in Access the Firepower Management Center
Using the Management Interface, page 5.
—If your local DHCP will assign an address to the FMC, use a keyboard and monitor to set up the appliance;
see Access the Firepower Management Center Using a Keyboard and Monitor, page 6.
Perform the initial configuration process; see Firepower Management Center Initial Configuration Wizard,
page 7.
Optionally use the Smart License pop-up dialog to configure Smart Licensing. See Smart Licensing Dialog,
page 9.
Once you complete the Initial setup process, you can optionally configure the FMC for Serial or Serial over LAN
(SOL) access; see Redirecting Console Output, page 19 and Setting Up Lights-Out Management, page 20.
After you complete setup, you will use the Firepower Management Center‘s web interface to perform most
management and analysis tasks for your deployment. For more information, see Administration
Recommendations, page 17.
Access the Firepower Management Center Using the Management
Interface
The FMC management interface is pre-configured to accept an IPv4 address assigned by DHCP, but in scenarios
where no DHCP is involved, the management interface uses the IPv4 address 192.168.45.45. Or, if you are
connecting to an FMC for the first time after performing a System Restore and you chose to retain license and
network settings, the IP address is the same as it was before you performed the System Restore.
Before You Begin:
Configure a local computer, which must not be connected to the Internet, with the following network settings:
—IP address: 192.168.45.2
—netmask: 255.255.255.0
—default gateway: 192.168.45.1
Determine the IP address assigned to the management interface of the FMC:
—If you are connecting to an FMC for the first time after performing a System Restore (see Restoring a
Firepower Management Center to Factory Defaults, page 22 ) and you chose to retain license and network
settings, the IP address is the same as it was before you performed the System Restore.
—Otherwise the FMC management interface IP address is 192.168.45.45.
Procedure
1. Using the supplied Ethernet cable, connect the network interface on the preconfigured computer directly to
the management interface on the appliance.
Confirm that the link LED is on for both the network interface on the local computer and the management
interface on the appliance.