Cryptophone 100 User manual

SECURE indicator
DELAY indicator Line type indicator
Security code
GSM Signal
strength meter Battery meter
Configuration
menu button Mute button Delete button
Down
Up
Talk Hang up
System menu
Contacts Calendar
Speaker
Microphone
Antenna

Inhalt
3 … Unpacking
4 … General
5 … Charging
6 … Insert your SIM
6 … Switch on
7 … Enter your PIN
7 … Standby
8 … Flight Mode
9 … Power down
10 … General Mobile Phone Security Advice
10 … Setting the volume
10 … Mute during call
11 … Using the Headset
12 … Placing a Secure Call
13 … Call Quality during Secure Calls
14 … Problems with setting up a Secure Call
15 … Secure Calls while moving
16 … Redialing
16 … Calling from the Contacts list
17 … Calling contacts stored on SIM card
17 … Troubleshooting
18 … Security Updates
19 … Security, Storage and Handling
20 … Repairs
21 … Accessories
22 … 3rd Party Software Install

3
Unpacking
Suitcase.a •3•
Unpacking
Your CryptoPhone was packaged using several tamper-evident seals to
ensure that nobody manipulated with your device while it was in transit.
Please take a minute to follow the security verification procedure outlined
on the Anti-Tamper Verification Instructions that are placed above the
CryptoPhone inside the suitcase.
To open suitcase, place it in front of you, so that the handle faces you.
Then use a sharp knife to cut the seals.Now open the suitcase by lifting
upwards the levers on the front. The levers are robust and at first use
might require a bit of force to move.
Inside the suitcase you will find your CryptoPhone packaged in a security
sealed, transparent plastic filme nested in the foam pad. Please also
verify the plastic filme and seal for tampering. The uneveness of the film
and the seal are intentional and a method of individualization to make
tampering harder. You can verify the authenticity with the Anti Tamper
Verification procedure. You will also find the headset, desk stand, power
supply, direct charge adaptor and headset ear clip in the suitcase. (Suitcase.a
•3•)
Behind the foam pad in the lid of the suitcase you will find the headset
manual, the Admin Policy Password and printed documentation. It is
recommended to store this manual also in the lid behind the foam, so
it wont get lost.

4General
General
Your CryptoPhone is based on a generic GSM equipped PDA that is sold
under different brands, and uses the PocketPC 2002 operating system.
On this device, a few additional applications besides the necessary
components for the CryptoPhone are installed, like an address book, an
agenda and an unencrypted phone mode.
The firmware and operating system have been modified to accommodate
the CryptoPhone functionality and provide added security, so a number
of things that you might know from other PocketPC PDAs are not available
on the GSMK CryptoPhone for security reasons. We supply the original
PocketPC2002 manuals, license sticker and CD with the GSMK CryptoPhone
100, but you need to be aware that some functionality of the the PocketPC
OS have been disabled by us for security reasons. Installing 3rd party
applications requires an Admin Policy Password.

5
Charging
Direct-charge adaptor •5•
Charging
Before using your CryptoPhone, we recommend you charge the battery
until full. In order to do this, you must connect the power supply to the
CryptoPhone. Depending on your location, you may need a plug adaptor
to use the power supply if the plug does not fit in your outlet. The power
supply is rated 100-240V, which means it will accept your line voltage
without conversion as long as it lies within this range. The LED in the
upper right corner of your CryptoPhone will change color to yellow while
it is charging and to green when fully charged. You can either charge the
CryptoPhone in the desk stand or using the small direct-charge adaptor
(Direct-charge adaptor •5•).
You will see a battery warning when the battery charge is below 50%.
You can see the current battery status at the right bar of the CryptoPhone
display. The battery of the CryptoPhone has a standby time of 150 hours
and a talk time of 3 hours 15 minutes in secure mode. Due to the higher
power consumption of the built-in PDA and the display backlight, this is
less then what you might be used to from normal GSM phones. Also
please note that these times may vary depending on your distance to
the nearest GSM base station: the further away the base station, the
more power your phone needs to use to reach it.
Note: we recommend you charge your GSMK CryptoPhone every night,
so you will not run out of battery unexpectedly. For security reasons
explained later in the chapter ‘Security, Storage and Handling’, we
suggest you place the CryptoPhone next to your bed while it is charging.
If the phone rings, or you need to place a call, while the phone is charging,
you can leave it plugged in while operating the phone.

6Insert your SIM • Switch on
Power down •6•
Stylus.a •6•
Stylus.b •6•
Insert your SIM
You need to insert a valid GSM card (SIM) into the CryptoPhone in order
to be able to place calls. Use the tip of the stylus to carefully open the
rubber flap on the lower right side of your CryptoPhone and insert the
SIM card. Then close the flap with some pressure, so it snaps into the
right position again. If the flap is not seated correctly, you might not be
able to power on the phone. See the enclosed PocketPC2002 manual for
more details on inserting the SIM.
Switch on
To power up your CryptoPhone for the first time, get the stylus out (its
nested inside the antenna) (Stylus.a •6•), unscrew the black plastic part of
the stylus (Stylus.b •6•) and press the small thin end of the plastic part into
the tiny hole on the right of the lower part of the CryptoPhone (Power
down •6•). Now the screen will lighten up and the GSMK CryptoPhone
100 begins its firmware initialization. This may take a moment. You will
be then requested to calibrate the touchscreen of the GSMK CryptoPhone
100 by clicking a few markers. To do this, simply follow the instructions
on the screen.
7
Enter your PIN • Standby
Enter PIN •7•
Standby button •7•
Standby button
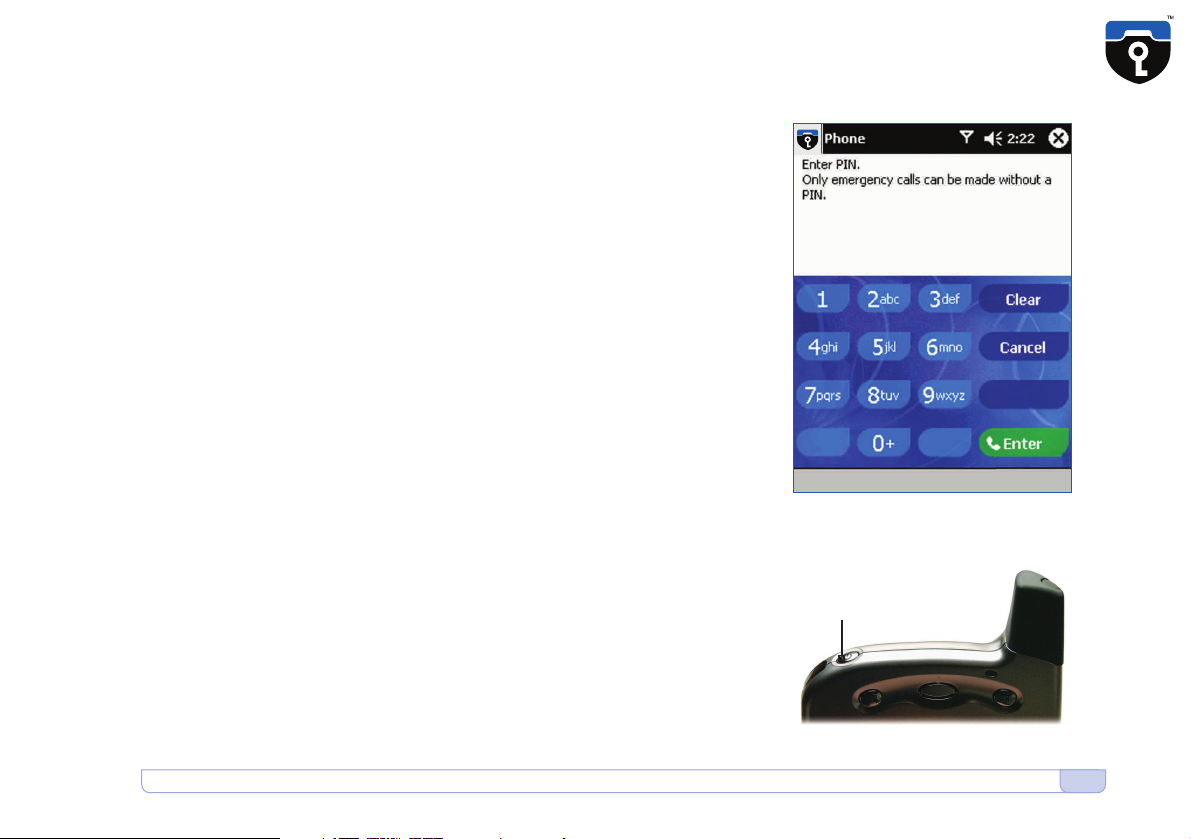
Enter your PIN
Most GSM SIM cards require you to enter a PIN number. (Enter PIN •7•)
After you have booted the CryptoPhone hardware, the application for
unencrypted phone calls shows up and asks you to enter your PIN.
After you entered the PIN, press the green Enter button. The CryptoPhone
will finish initialization and provide the secure telephony mode. If your
GSM card does not require a PIN, the secure telephony mode will be
enabled right away.
Standby
The GSMK CryptoPhone has four basic modes of operation. It can be
either completely switched off, in ‘standby mode’, switched on, or in
‘flight mode’.
In normal operation the CryptoPhone is in ‘standby mode’. In standby
mode, you can switch the device on at any time by briefly pressing the
button on top of the device (towards the left). (Standby button •7•)
Now the screen will become illuminated. To put the GSMK CryptoPhone
100 back into standby mode, press the switch again, and the screen
becomes dark. The GSMK CryptoPhone will still receive incoming calls
when it is in standby mode. In other words: standby mode will not disable
the radio.

8Flight Mode
GSM.a •8•
Turn phone off •8•
GSM.b •8•
Turn phone off •8•
Flight Mode
It is not safe to enter a airplane, hospital or other no-phone area with the
GSMK CryptoPhone switched on, or even in standby mode. To ensure
the radio is off, you need to enter ‘flight mode’. To enter flight mode, first
turn the device on by pressing the button on the top. Then use the stylus
to click the antenna symbol in the top bar of the screen. (GSM.a •8•)
Click the »Turn phone off«-Button to disable the GSM radio part (Turn
phone off •8•). This may take a minute. When the antenna symbol has
changed to off (GSM.b •8•), the radio is switched off. You can still work
with the address book, schedule, notes and the other PDA functions, but
cannot place or receive calls. To switch the GSM back on, click on the
antenna symbol in the top bar again, and select the »Turn phone on«
button in the popup window. (Turn phone on •8•)

9
Power down
Power down •9•
Power down
To completely power down the GSMK CryptoPhone, unscrew the black
part of the stylus and insert the little pin into the power-down hole on
the right underside of the device. (Power down •9•)
Power down erases the content of the volatile memory (which contains
your address book, list of last calls, notes, your SMS messages and
everything else you stored on the device). A power-down can also happen
when you forget to charge your CryptoPhone and the battery runs
completely empty. The GSMK CryptoPhone firmware is unaffected by a
power-down as it resides in non-volatile memory.
Initiating a Power down is recommended in emergency situations where
the capture of the device by an adversary is imminent, to get rid of any
data stored in volatile memory that might compromise your security.
Power down will not erase the contacts and SMS messages stored on
your SIM card.
Note: no key material that might compromise the security of your
past calls is stored anywhere on your device. Upon completion of a
secure call, all key material for the call is destroyed and permanently
erased. The recommendation for a Power down in emergency
situations only relates to other data like notes, contacts, SMS, call
history etc. stored on the device.

10 General Mobile Phone Security Advice • Setting the volume • Mute during call
Mute •10•
Button up •10• Button down •10•
General Mobile Phone Security Advice
The use of mobile phones and other radio transmission equipment in
certain areas is prohibited or restricted. Because of the risk of interference
with life-support equipment, the use of mobile phones is also banned in
most hospitals. Using a mobile phone in an airplane is a felony in most
countries. You are responsible for adherence to the local rules.
Setting the volume
To change the audio volume during a call, use the Up (Button up •10•) and
Down (Button down •10•) buttons.
If you set the volume too high, your partner may experience an echo
because his voice from the speaker gets fed back into your microphone.
In noisy environments the use of the included headset is recommended.
With the headset, you can set the volume to any desired level without
experiencing noticeable echo.
Mute during call
If you need to switch off the microphone during a call, press the mute
button. To switch the microphone on again, press the mute button again.
The mute button (Mute •10•) can be used only during a secure call.

11
Using the Headset
Headset •11•
Using the Headset
For hands free operation a professional quality headset is included with
the GSMK CryptoPhone. You can plug it in any time, before or during a
call. The headset has two modes, either with the headband or with a ear
clip. See the enclosed Plantronics M170 headset manual for details how
to change the headset mount from headband to ear clip. The headset
cable connector socket is on the lower right side of the device. (Headset
•11•)
You will notice that the headset is connected through a small adaptor
cable. If you wish to use a different headset, connect it to this adaptor.
Please note that standard 2.5 mm headset plugs will fit mechanically
directly into the GSMK CryptoPhone, but that the headset will not work
if plugged in without the adaptor cable. GSMK does not provide user
support for issues that are caused by the use of other than the supplied
headset.
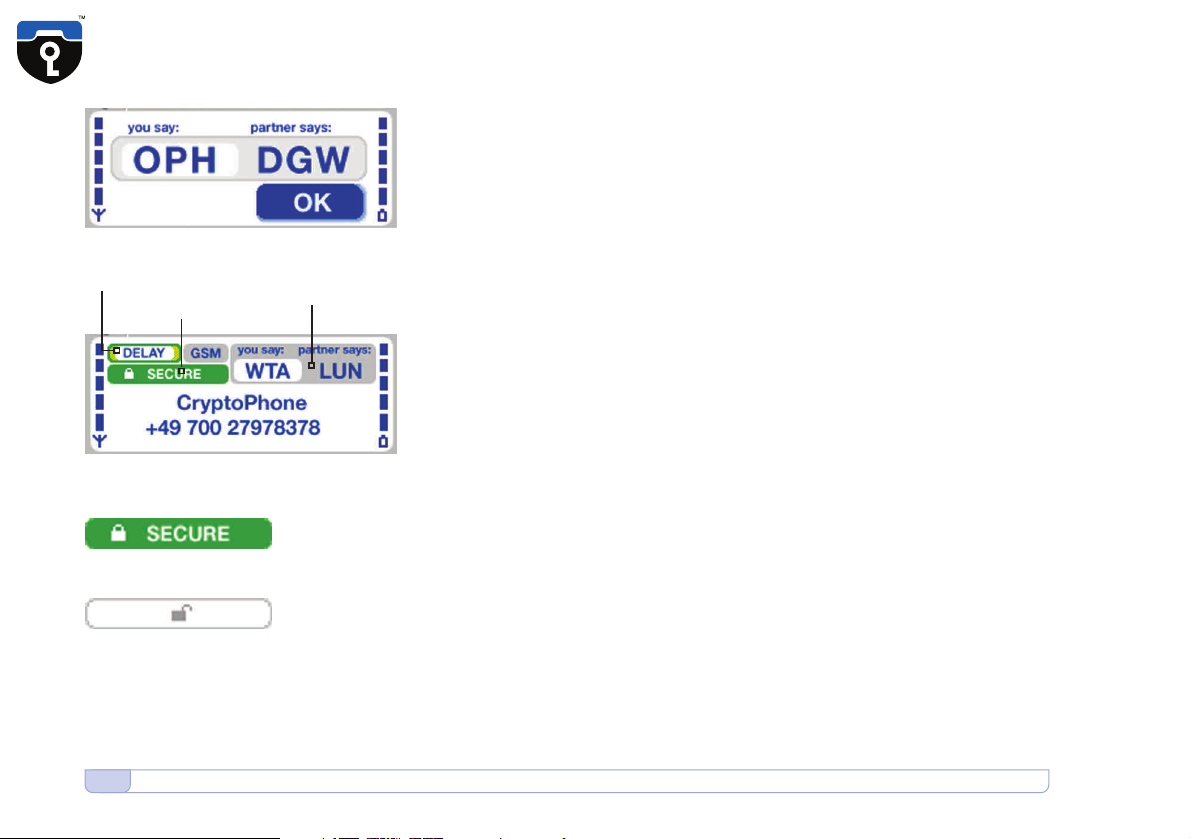
12 Placing a Secure Call
Hash •12•
Display •12•
Secure •12•
Unsecure •12•
Call delay indicator
SECURE indicator
Security code for
the current call
Placing a Secure Call
In order to place a secure call, the following conditions need to be met:
• your partner has either a CryptoPhone GSM or a CryptoPhone for
Windows up and running
• there is sufficient GSM coverage
•the GSM operator supports ‘GSM data calls’ (technically called ‘CSD’)
Now enter the number of your partner and press the Talk button (lower
left corner). You will hear a bit of comfort noise in the speaker, followed
by the normal ringing tone. It may take a bit longer then normal before
the other end picks up, so please let it ring.
After your partner has pressed the Talk button on his end, you will hear
a ditt-dutt ditt-dutt sound that signals to you that the ‘key setup’ procedure
for the secure connection is in progress. Key setup may take from 5 to
15 seconds, depending on line quality.
Once key setup is completed you hear a »Ping« sound and can start
talking to your partner. In order to verify the authenticity of the Key,
Please take a look at the display and read the three letters under »you
say« to your partner and verify the three letters under »partner says«.
Then press the OK button. (Hash •12•)
After you pressed OK, the display will look like this: (Display •12•)
The green SECURE indicator (Secure •12•) is only visible when a secure
call is established. During all other times it is shown in grey with a open
lock. (Unsecure •12•)

13
Placing a Secure Call • Call Quality during Secure Calls
Quality •13•
Reading the three letters and verifying what your partner says is meant
to protect you against so-called ‘man-in-the-middle attacks’ on the secret
session key. The letters are mathematically derived from the unique secret
key that is used during each call. By reading and verifying them with your
partner, you make sure that you are indeed communicating using the same
key. Please pay attention to the voice of your partner when he reads his
three letters. To be completely on the safe side against very sophisticated
voice impersonation during the key verification, you can just read your
letters unexpectedly in the middle of your call again and ask him to verify.
Call Quality during Secure Calls
The call delay indicator changes color in five steps between green over yellow
to red. Green indicates the best call quality, red the worst. (Quality •13•)
Delay describes the period of time it takes for your voice to reach your
partner. This time gets longer if the transmission of the encrypted voice
over the telephone network takes longer, or transmission errors occur.
Reasons for longer then normal delay are usually either bad GSM coverage
or network congestion.
Network congestion can often be circumvented by setting up the call
again, sometimes you just get a »bad line«. The GSM data call mode, used
by the CryptoPhone to transport the encrypted voice data during a call,
has a certain delay, caused by the architecture of the GSM network. The
GSM network handles data with lower priority than voice transmissions.
So even if the delay indicator is green, there is always a certain noticeable
delay, much like on some transcontinental phone calls.
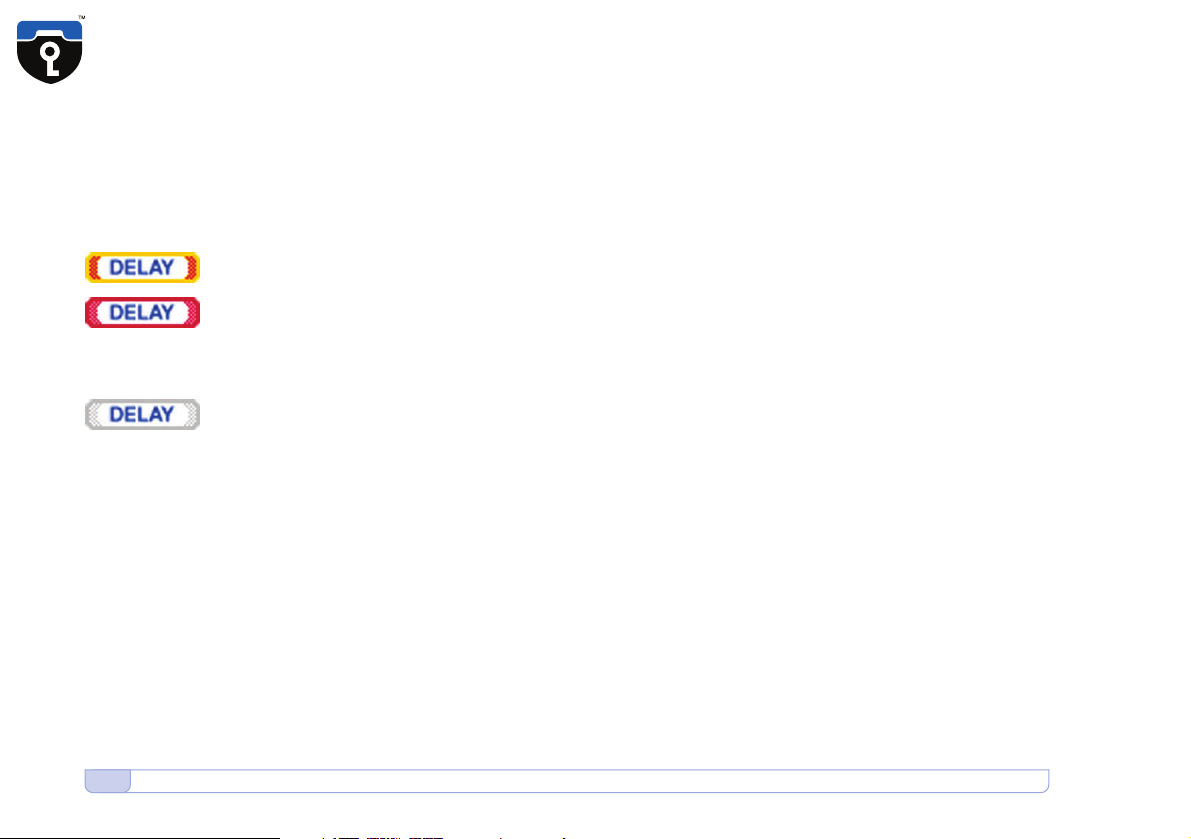
14 Call Quality during Secure Calls • Problems with setting up a Secure Call
Indicator.a •14•
Indicator.b •14•
If the overall line quality becomes bad, the delay raises and you may
experience »drop outs«. Note that the quality on international calls might
be not as good as on domestic calls. The multiple operators involved
into a international call often try to minimize their costs by technical
measures that can affect the quality of the call. If the call quality is
unacceptable, please try calling again. Call quality can also be adversely
affected when using certain GSM providers or while driving in a car or
train.
If the Delay indicator becomes reddish or red (Indicator.a •14•), please try
to find a place with better GSM coverage. Use the signal strength indicator
on the left side of the display to find a better spot. If the delay indicator
turns and stays solid red, please hang up and set up the call again.
When no call is in progress, the delay indicator is shown grey. (Indicator.b •14•)
Problems with setting up a Secure Call
Some providers restrict the reception of GSM data calls, such as needed
for the CryptoPhone. The practice is becoming increasingly rare, but a
GSM-provider may only allow incoming data calls to subscribers that
have a special ‘data subscription’, which comes with a special second
phone number to call to reach the CryptoPhone.
Some providers may not recognize that a number you are calling is a
GSM/ISDN number, and erroneously try to handle the call via a modem.
This can be recognized by the called party because he/she hears a modem
sound when picking up the phone.
Some providers may not pass data calls to certain other providers at all.

15
Problems with setting up a Secure Call • Secure Calls while moving
All of the above conditions may make it impossible to use the CryptoPhone
in one or both directions between two CryptoPhones. As a work-around
if you are roaming try switching providers. If secure calling only works
in one direction, you could use an unencrypted call to tell the other party
to call you using CryptoPhone. These problems are inherent to using the
CSD data call facility and apply to all encrypted telephony over GSM. We
will attempt to periodically publish new information as to what providers
are affected on our website.
Secure Calls while moving
Please note that when using the GSMK CryptoPhone while moving fast
(doing more then 80km/h in a car or a train), you may experience a
general degradation in call quality and periodic short dropouts every few
minutes during a call. These dropouts are the result of a so called handover
that occurs when you move from the coverage zone of one GSM tower
to the next. During the handover the data connection is interrupted for
a longer period than a voice transmission would be. To prevent important
call contents from getting lost, the GSMK CryptoPhone, unlike other
encrypted voice systems, accelerates the speed of decoding for a moment
after the dropout to catch up with the lost transmission time. This results
in the voice of your partner rising in pitch (the »Mickey Mouse effect«)
for a moment. After a short time the pitch returns to normal.
In general it is recommended that you place secure calls while driving
slower then 80 km/h.

16 Secure Calls while moving • Redialing • Calling from the Contacts list
Button up/down •16•
Talk button •16•
Adress button •16•
Note: In many countries the use of mobile phones while driving is
regulated or completely prohibited. You are responsible for adherence
to local regulations on telephone use while driving a car. We strongly
recommend the use of the enclosed headset while driving, even if
local regulations may not require this.
Redialing
The CryptoPhone has a call history of the last dialed 10 numbers. You
can redial a number by scrolling through the last dialed numbers with
the Up/Down keys (Button up/down•16•) and press the Talk button (Talk
button •16•) once the desired number is shown in the display.
Calling from the Contacts list
The Contacts list can be accessed by pressing the button on the CryptoPhone
that is placed to the left of the speaker (Adress button•16•). To place a secure
call to a contact, tap and hold on it with the stylus and select the entry
‘CryptoPhone’ from the small menu that appears. The selected contact’s
phone number is now displayed into the CryptoPhone. Now press the
talk button to establish the secure connection.

17
Calling contacts stored on SIM card • Troubleshooting
Downside •17•
Reset Power down
Calling contacts stored on SIM card
To use phonebook information stored on your SIM card, you need first to
copy them into the main contacts database on the CryptoPhone. To do so
click on the lock symbol in the upper left corner and select SIM Manager
from the menu. The SIM Manager will now load all contact information
from the SIM. After this is completed, select the ‘Tools’ menu on the lower
screen menu and tap ‘Select All’. Then select the Tools Menu once more
and tap ‘Save to Contacts’. Now all contacts will be copied into the volatile
memory of the GSMK CryptoPhone, and you can call them as described
above (in the chapter »Calling from the Contacts List«).
Note that storage of contact information on the CryptoPhone is not encrypted.
Troubleshooting
In the event the CryptoPhone shows unexpected behaviour, device
response becomes very slow, or it does not connect to a GSM network,
you can quickly reset it by pushing the stylus into the reset hole on the
left underside of the device. The GSMK CryptoPhone will restart without
erasing the memory. (Downside •17•)
In the unlikely event such a problem persists, you can completely power
down the device by inserting the small pin from the black part of the
stylus into the power down hole on the right lower side. Note that this
operation will erase the content of the volatile memory (including adresses
not stored on SIM, SMS, notes etc.) and bring the GSMK CryptoPhone
back to factory default condition.

18 Security Updates
Security Updates
In the event anyone discovers a flaw in the CryptoPhone, we will provide
a firmware update, as well as a detailed and honest report on the possible
security impact. As bad as security problems with cryptographic products
can be, we believe the only way to handle them properly is open and
transparent communication with our customers. You are the one best
suited to determine potential damage to your interests, so we will provide
you with all the known facts.
Security is not a state but a process. And this process requires constant
checking against emerging risks and new attack methods. Since the
CryptoPhone comes with full published source code, the chances are much
higher for a flaw to be discovered and fixed quickly then with any closed
source cryptographic products. Our advisory board of distinguished
cryptographers and security researchers aids us in identifying and countering
potential threats based on their intimate knowledge of upcoming academic
research and new emerging cryptanalysis methods.
In case a firmware update is needed for security reasons, you will get
notified either via the e-mail address that you supplied when purchasing
the CryptoPhone online, or directly by your reseller. If you receive a notice
about an upcoming security update, please verify it directly at our website
htttp://www.cryptophone.de/ to prevent attackers from slipping you a
malicious »update«. Please note that we will describe the details of the
update procedure directly on the website.
The firmware update mechanism is secured cryptographically using a
4096 bit public key signature system, which ensures only signed CryptoPhone
updates will be accepted by your CryptoPhone. If you receive suspicious

19
Security Updates • Security, Storage and Handling
communication regarding CryptoPhone updates (such as an e-mail with
an update file as attachment), please inform us immediately, as this may
be an attempt to insert malicious software into your CryptoPhone.
Please see our Frequently Asked Questions (FAQ) section on the website
http://www.cryptophone.de/ for further detailed information on the benefits
of published source cryptography.
Security, Storage and Handling
Your CryptoPhone is a Communication Security (COMSEC) device. It can
only be regarded as secure as long as you have permanent and
uninterrupted physical control over the CryptoPhone. Once an adversary
could have gained physical possession of the CryptoPhone, it must be
regarded as compromised. There is a variety of potential methods that
would allow an adversary to listen into your calls after he manipulated
the CryptoPhone and gave it back to you. So never let the CryptoPhone
fall into his hands. Have it always with you, in your immediate personal
sphere of control. Optimally, you should take it with you to the bathroom,
put it beside your bed when you sleep and not leave it alone in the hotel
room. The black plastic suitcase the CryptoPhone is shipped in is watertight
and you could even take it with you while swimming (although any
damages resulting from doing so are not covered by the warranty. Check
the rubber lips on the suitcase for sand and other objects that could
impair the watertight sealing before using it for transport in wet or damp
environments.)
Table of contents
Other Cryptophone Cell Phone manuals