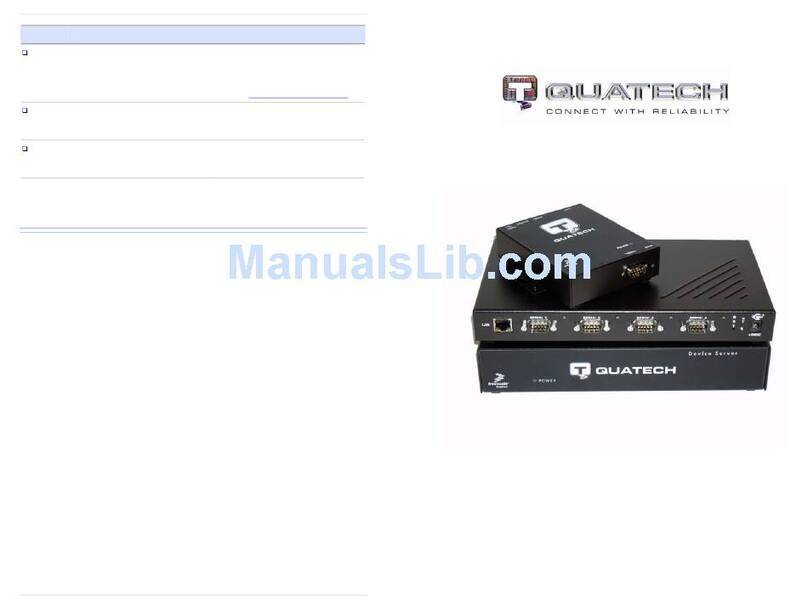
Quatech WLNG-AN-DP500 Series User manual

Reference Manual
Airborne Command Line Interface (CLI)
Enterprise Addendum
WLNG-SE/SP/AN/ET-DP500 Series
Revision 1.0
April 09
File name: airborne enterprise command line reference guide.doc
Document Number: 100-8081-100

Company Confidential Quatech, Inc.
2 Airborne CLI Reference Manual 100-8081-100
<Page Intentionally Left Blank>

Quatech, Inc. Company Confidential
100-8081-100 Airborne CLI Reference Manual 3
Quatech Confidential
Copyright © 2009 QUATECH ®Inc.
ALL RIGHTS RESERVED. No part of this publication may be copied in any form, by photocopy, microfilm, retrieval
system, or by any other means now known or hereafter invented without the prior written permission of QUATECH ®Inc..
This document may not be used as the basis for manufacture or sale of any items without the prior written consent of
QUATECH Inc..
QUATECH Inc. is a registered trademark of QUATECH Inc..
Airborne™ is a trademark of QUATECH Inc..
All other trademarks used in this document are the property of their respective owners.
Disclaimer
The information in the document is believed to be correct at the time of print. The reader remains responsible for the
system design and for ensuring that the overall system satisfies its design objectives taking due account of the information
presented herein, the specifications of other associated equipment, and the test environment.
QUATECH ®Inc. has made commercially reasonable efforts to ensure that the information contained in this document is
accurate and reliable. However, the information is subject to change without notice. No responsibility is assumed by
QUATECH for the use of the information or for infringements of patents or other rights of third parties. This document is
the property of QUATECH ®Inc. and does not imply license under patents, copyrights, or trade secrets.
Quatech, Inc. Headquarters
QUATECH ®Inc..
5675 Hudson Industrial Parkway
Hudson, OH 44236
USA
Telephone: 330-655-9000
Toll Free (USA): 800-553-1170
Fax: 330-655-9010
Technical Support: 714-899-7543 / wirelesssupport@quatech.com
Web Site: www.quatech.com

Company Confidential Quatech, Inc.
4 Airborne CLI Reference Manual 100-8081-100
<Page Intentionally Left Blank>

Quatech, Inc. Company Confidential
100-8081-100 Airborne CLI Reference Manual 5
Contents
1.0 Overview......................................................................................................................................................................9
2.0 Conventions...............................................................................................................................................................10
2.1 Terminology..........................................................................................................................................................10
2.2 Notes.....................................................................................................................................................................10
2.3 Caution..................................................................................................................................................................10
2.4 File Format............................................................................................................................................................10
2.5 Courier Typeface..................................................................................................................................................11
3.0 Scope.........................................................................................................................................................................12
3.1 Overview...............................................................................................................................................................12
3.2 Understanding the CLI..........................................................................................................................................12
3.3 Typical Development System...............................................................................................................................12
3.4 Serial Device Server Use.....................................................................................................................................12
3.5 Ethernet Bridge Use .............................................................................................................................................13
3.6 WLAN Security .....................................................................................................................................................13
3.7 WLAN Roaming....................................................................................................................................................13
3.8 FTP Configuration.................................................................................................................................................13
3.9 Power Management .............................................................................................................................................13
3.10 Command Line Descriptions................................................................................................................................13
4.0 Supported Devices ....................................................................................................................................................14
5.0 Overview....................................................................................................................................................................15
5.1 UART ....................................................................................................................................................................15
5.2 Serial.....................................................................................................................................................................15
5.3 Ethernet.................................................................................................................................................................15
6.0 Understanding the CLI...............................................................................................................................................17
6.1 Connecting to the CLI Server...............................................................................................................................17
6.2 CLI Security ..........................................................................................................................................................17
6.3 CLI Session Modes ..............................................................................................................................................18
6.3.1 CLI Mode ....................................................................................................................................................18
6.3.2 PASS Mode................................................................................................................................................18
6.3.3 PASS Mode for the Serial Interface...........................................................................................................19
6.3.4 PASS Mode for the Wireless Interface......................................................................................................19
6.3.5 LISTEN Mode (Serial/UART/SPI Interface Only)......................................................................................19
6.3.6 CLI Session Startup Modes .......................................................................................................................19
6.4 CLI Server Escape Processing............................................................................................................................20
6.5 Detecting and Executing the Escape Sequence .................................................................................................20
6.6 CLI Conventions...................................................................................................................................................21
6.7 ASCHEX vs. Binary Values..................................................................................................................................22
6.8 Command Responses..........................................................................................................................................22
7.0 A Typical Development System................................................................................................................................23
8.0 Serial Device Server Use..........................................................................................................................................24
8.1 Data Bridging........................................................................................................................................................24
8.1.1 Bridging from the Serial Interface ..............................................................................................................24
8.1.2 Bridging from a TCP connection on the wl-telnet-port..............................................................................26
8.1.3 Bridging from a TCP connection on the wl-tunnel-port.............................................................................27
8.1.4 Bridging Using UDP ...................................................................................................................................29
8.1.5 Data Bridging with XMODEM Guidelines..................................................................................................30
9.0 Ethernet Bridge Use..................................................................................................................................................31
9.1 Public Network Interface ......................................................................................................................................32
9.2 Private Network Interface.....................................................................................................................................34
10.0 WLAN Security ..........................................................................................................................................................36
10.1 Disabled (No Security)..........................................................................................................................................36
10.2 WEP Security........................................................................................................................................................36
10.2.1 WPA Migration Mode .................................................................................................................................37
10.3 WPA Security........................................................................................................................................................37
10.4 WPA2 Security......................................................................................................................................................38
10.5 Managing Certificates and Private Keys..............................................................................................................41
11.0 WLAN Roaming.........................................................................................................................................................46
12.0 FTP Configuration......................................................................................................................................................48
13.0 Power Save................................................................................................................................................................49
14.0 Command Descriptions.............................................................................................................................................50
dev-type ..........................................................................................................................................................................51
wl-security.......................................................................................................................................................................52
get-cert............................................................................................................................................................................53
get-cfg .............................................................................................................................................................................54
put-cert............................................................................................................................................................................55
put-cfg .............................................................................................................................................................................56

Company Confidential Quatech, Inc.
6 Airborne CLI Reference Manual 100-8081-100
ca-cert-filename..............................................................................................................................................................57
ca-cert2-filename............................................................................................................................................................58
client-cert-filename .........................................................................................................................................................59
client-cert2-filename .......................................................................................................................................................60
priv-key-filename ............................................................................................................................................................61
priv-key2-filename ..........................................................................................................................................................62
priv-key-password...........................................................................................................................................................63
priv-key2-password.........................................................................................................................................................64
? [Question Mark] ...........................................................................................................................................................65
help..................................................................................................................................................................................66
dh-parm-filename............................................................................................................................................................67
eap-password .................................................................................................................................................................68
eap-ident .........................................................................................................................................................................69
eap-anon-ident................................................................................................................................................................70
eap-phase1.....................................................................................................................................................................71
eap-phase2.....................................................................................................................................................................72
subject-match..................................................................................................................................................................73
subject-match2................................................................................................................................................................74
clear-cred ........................................................................................................................................................................75
clear.................................................................................................................................................................................76
del-cert ............................................................................................................................................................................77
clear-wep.........................................................................................................................................................................78
default-cfg .......................................................................................................................................................................79
radio-on...........................................................................................................................................................................80
radio-off...........................................................................................................................................................................81
ping..................................................................................................................................................................................82
stats.................................................................................................................................................................................83
ftp-server-address...........................................................................................................................................................84
ftp-server-path.................................................................................................................................................................85
ftp-user............................................................................................................................................................................86
ftp-password ...................................................................................................................................................................87
ftp-filename .....................................................................................................................................................................88
save.................................................................................................................................................................................89
telnet-port........................................................................................................................................................................90
http-port...........................................................................................................................................................................91
eth-ip ...............................................................................................................................................................................92
eth-gateway ....................................................................................................................................................................93
eth-subnet .......................................................................................................................................................................94
eth-mode.........................................................................................................................................................................95
wl-specific-scan...............................................................................................................................................................96
apply-cfg..........................................................................................................................................................................97
wl-assoc-backoff.............................................................................................................................................................99
arp-reachable-time........................................................................................................................................................100
arp-staleout-time...........................................................................................................................................................101
del-cfg............................................................................................................................................................................102
discover.........................................................................................................................................................................103
intf-type .........................................................................................................................................................................104
list-cfg............................................................................................................................................................................105
ssh-keygen....................................................................................................................................................................106
ssh-keysize ...................................................................................................................................................................107
startup-text ....................................................................................................................................................................108
startup-msg...................................................................................................................................................................109
ver-fw.............................................................................................................................................................................110
ver-radio........................................................................................................................................................................111
ver-uboot.......................................................................................................................................................................112
wl-dhcp-vendorid ..........................................................................................................................................................113
wl-udp-ping....................................................................................................................................................................114
wl-wins1 ........................................................................................................................................................................115
wl-wins2 ........................................................................................................................................................................116
cfg-dump .......................................................................................................................................................................117
15.0 Change Log .............................................................................................................................................................119

Quatech, Inc. Company Confidential
100-8081-100 Airborne CLI Reference Manual 7
Figures
Figure 1 - Bridging from the Serial Interface Manually Using the pass Command ................................................................25
Figure 2 - Bridging from the Serial Interface Automatically at Startup Using the Serial-Default Command .........................26
Figure 3 - Bridging from a TCP Connection on the wl-telnet-port...........................................................................................27
Figure 4 - Bridging From a TCP Connection on the wl-tunnel-port.........................................................................................29
Figure 5 - Ethernet Bridge Functionality ..................................................................................................................................31
Figure 6 - Airborne Ethernet Bridge IP Configuration..............................................................................................................33
Figure 7 - Certificate and Private Key Delivery Methods.........................................................................................................43
Tables
Table 1 - Public Network Configuration ...................................................................................................................................32
Table 2 - Private Network Interface Configuration...................................................................................................................34
Table 3 - WEP Configuration Parameters................................................................................................................................36
Table 4 - WPA-Personal (PSK) Configuration.........................................................................................................................37
Table 5 - WPA-LEAP Configuration.........................................................................................................................................37
Table 6 - WPA2-Personal (PSK) ASCII PSK Configuration....................................................................................................39
Table 7 - WPA2-Personal (PSK) Precalculated Key Configuration........................................................................................39
Table 8 - PEAPv0/EAP-MSCHAPv2 Configuration.................................................................................................................39
Table 9 - EAP-TTLS/MSCHAPV2 Configuration.....................................................................................................................40
Table 10 - EAP-TLS/MSCHAPv2 Configuration......................................................................................................................40
Table 11 - Certificate Delivery Commands..............................................................................................................................41
Table 12 - Certificate Management Commands......................................................................................................................43
Table 13 - Commands that Affect Roaming.............................................................................................................................46
Table 14 - FTP Configuration Commands...............................................................................................................................48
Table 15 - FTP Upload Commands .........................................................................................................................................48
Table 16 –Power-Save Modes................................................................................................................................................49
Table 17 - pm-mode Parameters .............................................................................................................................................49

Company Confidential Quatech, Inc.
8 Airborne CLI Reference Manual 100-8081-100
<Page Intentionally Left Blank>

Quatech, Inc. Company Confidential
100-8081-100 Airborne CLI Reference Manual 9
1.0 Overview
Airborne is a line of highly integrated 802.11 radios and device servers, designed to
address the demands of the complex M2M market. Utilizing the latest 802.11, CPU and
network technologies, the Airborne family of products provide a broad, encompassing
solution for wireless applications requiring performance, reliability and advanced
technology.
The Airborne Wireless Device server family includes everything necessary to connect a
Serial or Ethernet device to a high performance 802.11 network. The WLNG-XX-DP500
series includes a full featured 802.11b/g radio and a high performance 32bit ARM9
processor running an embedded OS and Quatech’s exclusive Airborne Device Server
firmware, allowing the wireless network enabling of almost any device or system.
WPA2-Enterprise (AES-CCMP + EAP) is the security standard for leading edge
enterprise networks. The Airborne Enterprise Device Server supports the latest security
standards and more. Fully compliant to the WPA2-Enterprise specification, the device
includes a wide range of EAP methods (with certificates), including support for legacy
functionality including, WPA, WEP and LEAP.
The best security and advanced networking is no good if you cannot connect your device
to the Airborne Device Server. Airborne offers the widest range of Serial and Ethernet
based interfaces in the industry. With flexibility and performance the WLNG-XX-DP500
series lets you decide how you want to use it.
Designed by the Quatech Engineers specifically to meet the demands of the industrial,
automotive and medical markets, the Airborne device server has the widest operating
temperature range and highest level of reliability available, all backed by a lifetime
warranty. Quatech also provides FCC Modular certification potentially removing the need
for further regulatory work.
The two previous generations of Airborne device servers have been integrated and
deployed into a wide range of applications and markets, including Medical, Telematics
and Logistics.
Quatech’s 3rd Generation Device Server extends the reputation of the family further by
drawing on the lessons learned and adding the latest technologies. The Quatech
Enterprise 802.11 Device Server family is the industry leading solution and represents a
breakthrough in 802.11 connectivity for all M2M markets.
The following manual covers a detailed description of the Airborne Command Line
Interface (CLI) used for management, configuration and integration of the Airborne and
AirborneDirect Enterprise Device Server modules into embedded systems.

Company Confidential Quatech, Inc.
10 Airborne CLI Reference Manual 100-8081-100
2.0 Conventions
The following section outlines the conventions used within the document, where
convention is deviated from the deviation takes precedence and should be followed. If
you have any question related to the conventions used or clarification of indicated
deviation please contact Quatech Sales or Wireless Support.
2.1 Terminology
Airborne Enterprise Device Server and AirborneDirect Enterprise Device
Server is used in the opening section to describe the devices detailed in this
document, after this section the term module will be used to describe the
devices.
2.2 Notes
A note contains information that requires special attention. The following
convention will be used. The area next to the indicator will identify the specific
information and make any references necessary.
The area next to the indicator will identify the specific information and make any
references necessary.
2.3 Caution
A caution contains information that, if not followed, may cause damage to the
product or injury to the user. The shaded area next to the indicator will identify
the specific information and make any references necessary.
The area next to the indicator will identify the specific information and make any
references necessary.
2.4 File Format
These documents are provided as Portable Document Format (PDF) files. To
read them, you need Adobe Acrobat Reader 4.0.5 or higher. For your
convenience, Adobe Acrobat Reader is provided on the Radio Evaluation Kit CD.
Should you not have the CD, for the latest version of Adobe Acrobat Reader, go
to the AdobeWeb site (www.adobe.com).

Quatech, Inc. Company Confidential
100-8081-100 Airborne CLI Reference Manual 11
2.5 Courier Typeface
Commands and other input that a user is to provide are indicated with Courier
typeface. For example, typing the following command and pressing the Enter key
displays the result of a command:
wl-info <cr>
Module Firmware Version: 1.00
Radio Firmware Version: 5.0.21-210.p17
Link Status: Connected
SSID: Quatech_Connected
MAC Address: 000B6B77619E
BSSID: 0016B637880D
Transmit Rate (Mb/s): 54
Signal Level (dBm): -40
Noise Level (dBm): -92
IP Address: 192.168.1.100
Subnet Mask: 255.255.255.0
Default Gateway: 192.168.1.1
Primary DNS: 68.107.28.42
Secondary DNS: 68.107.29.42
Up Time (Sec): 48313

Company Confidential Quatech, Inc.
12 Airborne CLI Reference Manual 100-8081-100
3.0 Scope
The CLI Reference Manual documents the Command Line Interface (CLI) for the
Airborne Device Server family of products. This document is an addendum to the
Airborne CLI reference manual and describes the commands introduced with the
Enterprise Class product family. The Enterprise Addendum should be used in conjunction
with the Airborne CLI Reference Manual for a full description of the available Command
Line Interface.
The CLI is one of a number of management interfaces for the product family and
compromises a set of ASCII text commands and parameters used to provision the
module, provide module status and environmental feedback, as well as support firmware
and file delivery to the module.
The reference manual will include the following sections. Please refer to the appropriate
section the required information.
3.1 Overview
In this section we will review the different device configurations and basic
operation and functionality of the Airborne Device Servers and Bridges. Support
for a specific function is dependent upon the device configuration chosen. It will
be noted within each section to which configuration it applies.
3.2 Understanding the CLI
This section will cover the use of the CLI and describe the action and reaction to
the specific functional calls and commands.
Methods of connection and delivery of the CLI will also be reviewed. CLI
conventions, data types and command responses will also be addressed in this
section.
3.3 Typical Development System
An outline and description of a basic development and evaluation system will be
covered in this section. It is not necessary to use this exact configuration
however descriptions of connectivity and use, utilized on other sections of the
manual, will be based upon the system structure described in this section.
3.4 Serial Device Server Use
In this section the base functionality of the device server will be described and
examples of use and configuration will be provided to highlight the best use of
the module and CLI. Refer to this section to understand the differences between
a command port, data tunnel, TCP/IP vs. UDP use and server vs. device
operation.

Quatech, Inc. Company Confidential
100-8081-100 Airborne CLI Reference Manual 13
3.5 Ethernet Bridge Use
A full description of the operation of the Airborne Ethernet Bridge, its place in the
network infrastructure and the required parameters will be covered in this
section.
3.6 WLAN Security
This section will cover the use of the advanced security features available in the
Airborne Enterprise module. Configuration of the module, requirements for
successful deployment, examples of configuration for the use of the advanced
authentication and wireless security options will be provided.
Descriptions of the use of WEP, WPA and WPA2 will be included. Outlines of the
authentication methods supported (EAP) and the certificates delivery and
deployment will be reviewed.
3.7 WLAN Roaming
This section will outline the commands that impact the roaming performance of
the module. Discussion of configuration options based upon application
requirements is also included.
3.8 FTP Configuration
The Airborne Enterprise Device Server family supports delivery of certificates,
private keys, configuration files and module firmware via FTP. This section
describes how to configure and use the FTP capabilities.
3.9 Power Management
A review of the CLI commands impacting device power usage will include a
description of the power save modes and how to utilize them. A discussion on
the impact of power, data latency and module status will be included.
3.10 Command Line Descriptions
This section will describe in detail the syntax, arguments and use of the available
commands.

Company Confidential Quatech, Inc.
14 Airborne CLI Reference Manual 100-8081-100
4.0 Supported Devices
This manual supports the Enterprise set of CLI commands across all platforms. Not all
commands are supported on all platforms; the command descriptions in Section 14.0
provide guidance on which devices support it.
At the time of writing, the CLI command list represents the v1.03 release of the WLRG-
XX-DP500 series of Airborne Device Server firmware. The part numbers supporting the
commands described in this document include the following:
Part No.
Description
WLNG-SE-DP5XX
802.11b/g to RS232/422/485 and UART Serial Device Server Module,
Enterprise Class
WLNG-AN-DP5XX
802.11b/g to UART Serial Device Server Module, Enterprise Class
WLNG-SP-DP5XX
802.11b/g to SPI Serial Device Server Module, Enterprise Class
WLNG-ET-DP5XX
802.11b/g to 10/100 Ethernet Bridge (NAT Level3) Module, Enterprise Class
WLNG-EK-DP5XX
Enterprise Class Airborne Development and Evaluation Kit
ABDG-SE-DP5XX
802.11b/g to RS232/422/485 Device Server, Enterprise Class
ABDG-ET-DP5XX
802.11b/g to 10/100 Ethernet Bridge (NAT Level3), Enterprise Class
ABDG-SE-HD5XX
802.11b/g to RS232/422/485 Heavy Duty Device Server, Enterprise Class
ABDG-ET-HD5XX
802.11b/g to 10/100 Heavy Duty Ethernet Bridge (NAT Level3), Enterprise
Class

Quatech, Inc. Company Confidential
100-8081-100 Airborne CLI Reference Manual 15
5.0 Overview
The Airborne™ WLN Module includes a Command Line Interface (CLI) Server. The CLI
Server is the primary user interface for configuring, controlling, and monitoring Airborne™
WLN Modules. Users and OEM applications can establish CLI Sessions to the CLI
Server via the serial interface or a TCP connection on the wireless interface.
This document describes the CLI in full. Since different Airborne™ devices differ in
functionality, there may be differences in the use of the CLI for particular devices. These
differences are clearly identified as part of this document.
There are four primary module configurations supported by the Airborne Enterprise
Device Server family, these are UART, Serial, SPI and Ethernet. Each device types will
be described below. In some cases multiple interface option are available within a
specific configuration, the functionality of these interfaces does not vary between device
configurations unless specifically noted within the device description.
5.1 UART
The UART (Universal Asynchronous Receiver/Transmitter) interface is a digital
interface that supports full duplex transfer of data serially between the module
and a connected host. It supports the following settings:
BAUD: 300, 600, 1200, 2400, 4800, 9600, 14400, 19200, 28800, 38400,
57600, 115200, 230400, 460800, 921600
Flow Control: None, Hardware (CTS/RTS), Software (XON/XOFF)
Default settings: 9600, N, 8, 1, No Flow Control.
5.2 Serial
The Serial device includes both a UART interface control and I/O lines to
manage external logic for RS232/422/485 line drivers. It supports the following
settings:
BAUD: 300, 600, 1200, 2400, 4800, 9600, 14400, 19200, 28800, 38400,
57600, 115200, 230400, 460800, 921600
Flow Control: None, Hardware (CTS/RTS), Software (XON/XOFF)
Mode (RS232/485), Tx Enable, Rx Enable.
Default settings: 9600, N, 8, 1, No Flow Control.
5.3 Ethernet
The Ethernet interface supports a fully compliant 10/100 Ethernet interface
capable of supporting all full and half-duplex rates. The rates are configurable
through the CLI interface.
The module includes a Broadcom BCM5241A Ethernet PHY, please refer to the
manufacturers datasheet for interface details and appropriate design guidelines.

Company Confidential Quatech, Inc.
16 Airborne CLI Reference Manual 100-8081-100
The interface supports the following settings:
Auto Negotiate, 10Mbps Half Duplex, 10Mbps Full Duplex, 100Mbps Half
Duplex, 100Mbps Full Duplex
Rx+, Rx-, Tx+ and Tx-
Default settings: Auto Negotiate.

Quatech, Inc. Company Confidential
100-8081-100 Airborne CLI Reference Manual 17
6.0 Understanding the CLI
CLI Sessions established to the CLI Server may operate in one of three modes: CLI,
PASS, or LISTEN. Not all modes are supported on all interfaces of the device. A CLI
Session established on the serial interface may operate in any of the three modes. CLI
Sessions established on the wireless interface are restricted to CLI or PASS Modes.
6.1 Connecting to the CLI Server
Users may connect to the CLI Server on the serial interface using a terminal
emulation program such as HyperTerminal. The DPAC default settings for the
serial interface are:
Bits per second: 9600
Data bits: 8
Stop bits: 1
Parity: none
Flow control: none
Users may also connect to the CLI Server on the wireless interface using a
TCP client such as Windows Telnet. The Module’s CLI Server supports a
Telnet connection with the following restrictions:
Telnet option negotiation should be turned off.
Telnet commands such as DO, WONT, and DON, must not be issued.
Network Virtual Terminal codes are not supported.
NUT 7-bit encoding does not allow 8–bit data transfers.
The CLI Server’s wireless interface is characterized as follows:
The CLI Server listens on the TCP port specified by the wl-telnet-port
parameter. The default is 23.
The CLI Server inactivity timer is configured via the wl-telnet-timeout
command.
The CLI Server uses the wl-telnet-timeout value to timeout and close
TCP connections that are inactive.
The CLI Server supports up to three (3) TCP sessions.
6.2 CLI Security
The CLI Server supports five (5) levels of security for each CLI Session. The
security levels provide a safeguard for the set of CLI commands that may be
executed by users. CLI Sessions that are authenticated at a particular security
level may execute all CLI commands specified for that security level and below.
The Module’s five (5) levels of security are:
Level 0 (L0) = connectionless

Company Confidential Quatech, Inc.
18 Airborne CLI Reference Manual 100-8081-100
Level 1 (L1) = connection, not logged in (default)
Level 2 (L2) = data
Level 3 (L3) = config
Level 4 (L4) = OEM
Level 5 (L5) = MFG
Level 0 is the connectionless access level. Access over UDP will use this access
level. The L0 level provides access to the name query services. It is not an
authenticated level.
Level 1 is the default security level for CLI Sessions over TCP or the serial
interface.
CLI Sessions must execute the CLI command auth in order to authenticate the
CLI Sessions to another security level. The CLI command definition tables in the
following chapter include a column labeled Ln that indicates the access level
required to execute each command. The CLI command logout returns the CLI
Session back to security Level 1.
6.3 CLI Session Modes
The mode of the CLI Session governs the set of actions allowed in the CLI
session. The following are descriptions of each mode:
6.3.1 CLI Mode
CLI Mode is the command processing mode of the CLI Session. CLI Mode allows
users and OEM applications to simply execute Airborne™ WLN Module
commands as described in the section, “CLI Commands.”
A CLI Session may transition into CLI Mode automatically at startup of the CLI
Session (if so configured). See section “CLI Session Startup Modes” for details
on startup modes.
CLI Sessions may transition manually to CLI Mode from the other modes via the
use of the CLI escape processing feature in the CLI Server. See section “CLI
Server Escape Processing” for details.
6.3.2 PASS Mode
PASS Mode is an active data bridging mode of the CLI Server. PASS Mode
allows the user or OEM application to transfer data between a CLI Session on
the wireless interface and the CLI Session on the serial interface.
A CLI Session may transition to PASS Mode automatically at startup of the CLI
session (if so configured) or manually from the CLI Mode using the CLI pass
command. See section “CLI Session Startup Modes” for details on startup
modes.
The transition from CLI Mode into PASS Mode differs depending on the attributes
of the CLI session. The following sections describe the two PASS Modes.

Quatech, Inc. Company Confidential
100-8081-100 Airborne CLI Reference Manual 19
6.3.3 PASS Mode for the Serial Interface
When the CLI Session on the serial interface attempts a transition to PASS
Mode, the CLI Server establishes an outbound connection from the Airborne™
WLN Module to a user-specified TCP server and/or UDP server on the wireless
interface. Once a connection is established, data bridging becomes possible
between the CLI Session on the serial interface and the TCP Server and/or UDP
server. If the connection to the primary TCP server failed, the CLI Server will
attempt to connect to a secondary TCP server, if configured. If the transition to
PASS Mode was triggered by the automatic startup configuration, the CLI Server
will use the wl-retry-time configuration parameter to continuously retry
connection to the servers.
The IP addresses of the primary TCP and UDP servers are configured using wl-
tcp-ip and wl-udp-ip CLI commands. The secondary TCP server is
configured using the wl-tcp-ip2 command. The TCP server port is
configured using wl-tcp-port and wl-udp-port CLI commands. The retry
timer is configured using the wl-retry-time CLI command. See section “CLI
Commands” for more details on these commands.
6.3.4 PASS Mode for the Wireless Interface
When the CLI Session on the wireless interface attempts to transition to PASS
Mode, the CLI Server establishes a data bridge to the CLI Session on the serial
interface if the following conditions are both true:
The CLI Session on the serial interface is in LISTEN Mode.
No other CLI Session on the wireless interface is in PASS Mode.
6.3.5 LISTEN Mode (Serial/UART/SPI Interface Only)
LISTEN Mode is a passive data bridging mode of the CLI Session. The LISTEN
Mode is only applicable on the serial interface.When the CLI Session on the
serial interface enters LISTEN Mode, the Airborne™ WLN Module passively
waits for a data bridge to be established over the wireless interface. The data
bridge may be initiated using a CLI Session via the PASS Mode or using the
tunneling feature. The CLI Session may transition to CLI Mode using CLI Server
escape processing. See section “CLI Server Escape Processing” for details.
When the serial interface CLI Session is in LISTEN Mode, the following are
possible:
TCP connections on the wireless interface can use the CLI commands pass,
putget or putexpect to establish a data bridge.
TCP connection can establish a data bridge if tunneling is enabled.
6.3.6 CLI Session Startup Modes
The startup behavior of the CLI Session on each interface is determined as
follows:

Company Confidential Quatech, Inc.
20 Airborne CLI Reference Manual 100-8081-100
The CLI Session on the serial interface startup behavior is determined by the
value of the serial-default parameter.
CLI Sessions on the wireless interface using the TCP port specified by wl-
telnet-port always start in CLI Mode.
CLI Sessions on the wireless interface using the TCP port specified by the
wl-tunnel-port or the UDP port specified by wl-udp-rxport, always
start in PASS Mode. However, if the CLI Session on the serial interface is not
in LISTEN Mode, the TCP connection on the wl-tunnel-port will be
rejected by the Module.
6.4 CLI Server Escape Processing
The CLI Server includes an escape processing feature which allows CLI
Sessions to transition from PASS or LISTEN (data bridging) Mode back to CLI
Mode. Escape processing is configurable to:
disable escape processing
process the receipt of a user-defined escape string as an escape signal
process the receipt of the BREAK signal as an escape signal
When escape processing is disabled, the CLI Server will not parse the data
stream for any escape sequence. When escape processing is configured to use
an escape string, the CLI Server will perform pattern matching for the user-
defined escape string in the data stream. The escape string is a five (5)-character
string configurable via the escape CLI command. When escape processing is
configured to use the BREAK signal, the CLI Server will parse the data stream
for the BREAK signal.
6.5 Detecting and Executing the Escape Sequence
Upon detection of the escape sequence, the CLI Server applies the follow rules
for transitions of the CLI Session on that interface:
If the CLI Session is in LISTEN Mode and there is no data bridge
established, the CLI Session will transition to CLI Mode and send an “OK”
response to the CLI Session.
If the CLI Session is in LISTEN Mode and there is an active data bridge
established, the CLI Server will terminate the active data bridge and the CLI
Session will remain in LISTEN Mode. Basically, two escapes are required to
transition from active data bridge to CLI mode.
If the CLI Session is in PASS Mode, the CLI Server will send an “OK”
response to the CLI Session and transition to CLI Mode.
The following effects of escape processing require the attention of system
implementations:
If the escape sequence is an escape string, the escape string received on
one CLI Session is transmitted to the CLI Session on the other end of the
data bridge prior to performing the CLI Session transition. This allows the
other end to parse the received data and determine when the data bridge is
shutdown.
This manual suits for next models
3
Table of contents
Other Quatech Server manuals

Quatech
Quatech AirborneDirect Wireless Device Server User manual

Quatech
Quatech DSEW-100D User manual

Quatech
Quatech DSE-400D User manual
Quatech
Quatech DSE-100D-EMB User manual

Quatech
Quatech 4-Port USB 2.0 Device Server over IP... User manual

Quatech
Quatech USBN-500NAS User manual

Quatech
Quatech AirborneDirect ABDG-SE-IN5410 User manual

Quatech
Quatech 4-Port USB 2.0 Device Server over IP... User manual

Quatech
Quatech DSE-100D User manual

Quatech
Quatech 4-Port USB 2.0 Device Server over IP... User manual