Acronis Privacy Expert Suite 4
Table of Contents
END-USER LICENSE AGREEMENT ..................................................................................................3
INTRODUCTION...............................................................................................................................6
What is Acronis Privacy Expert Suite?.................................................................................................6
Why is it necessary to keep PC work confidential?..............................................................................6
Standards of guaranteed destruction of confidential information..........................................................7
What's new in Acronis Privacy Expert Suite 7.0?.................................................................................7
What Acronis Privacy Expert Suite enables you to clean up................................................................8
On the contents of the guide, or how to find the necessary information...............................................8
System requirements...........................................................................................................................9
Software use conditions.......................................................................................................................9
Technical support.................................................................................................................................9
CHAPTER 1. INSTALLING ACRONIS PRIVACY EXPERT SUITE...........................................11
1.1 What’s included ........................................................................................................11
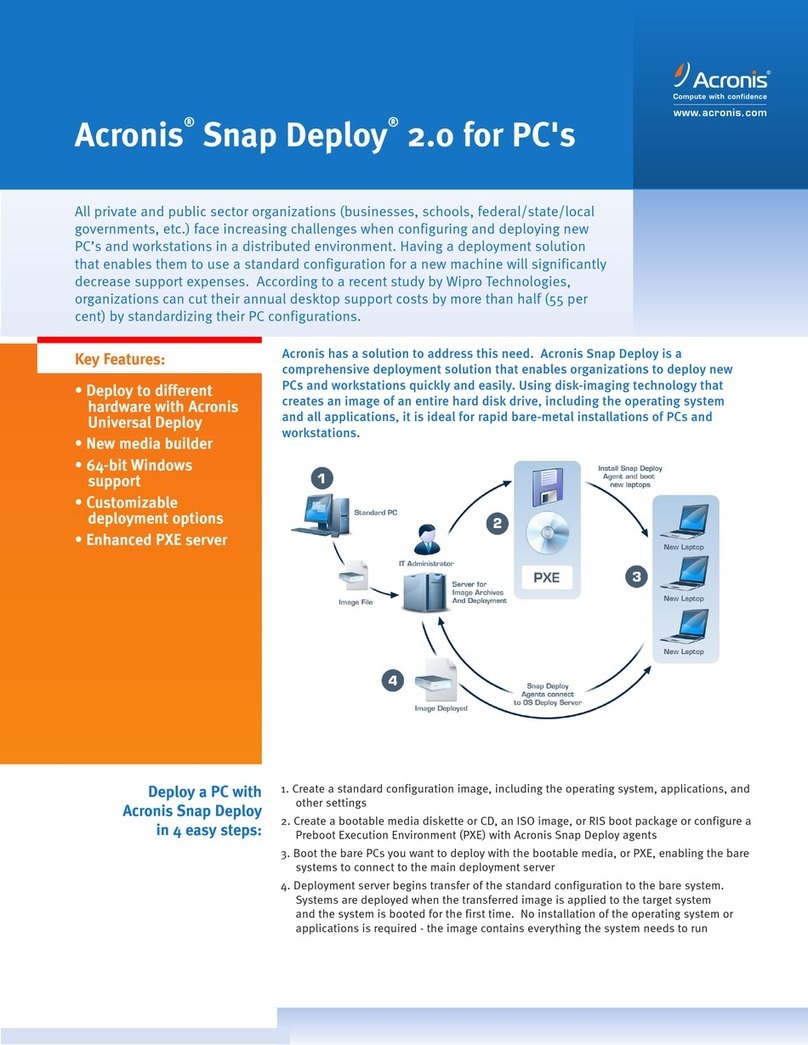
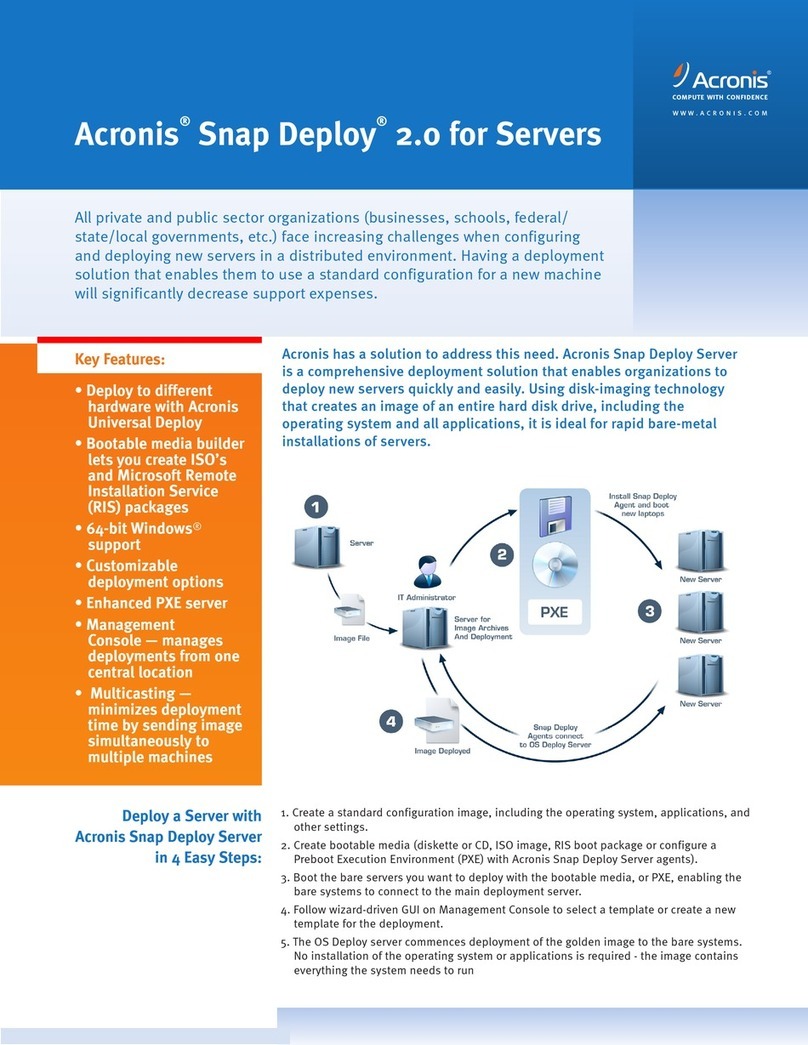
1.2 Installing the system.................................................................................................11
1.3 Recovering Acronis Privacy Expert Suite.................................................................11
1.4 Removing the software.............................................................................................11
CHAPTER 2. WORKING WITH ACRONIS PRIVACY EXPERT SUITE ....................................12
2.1 Getting started..........................................................................................................12
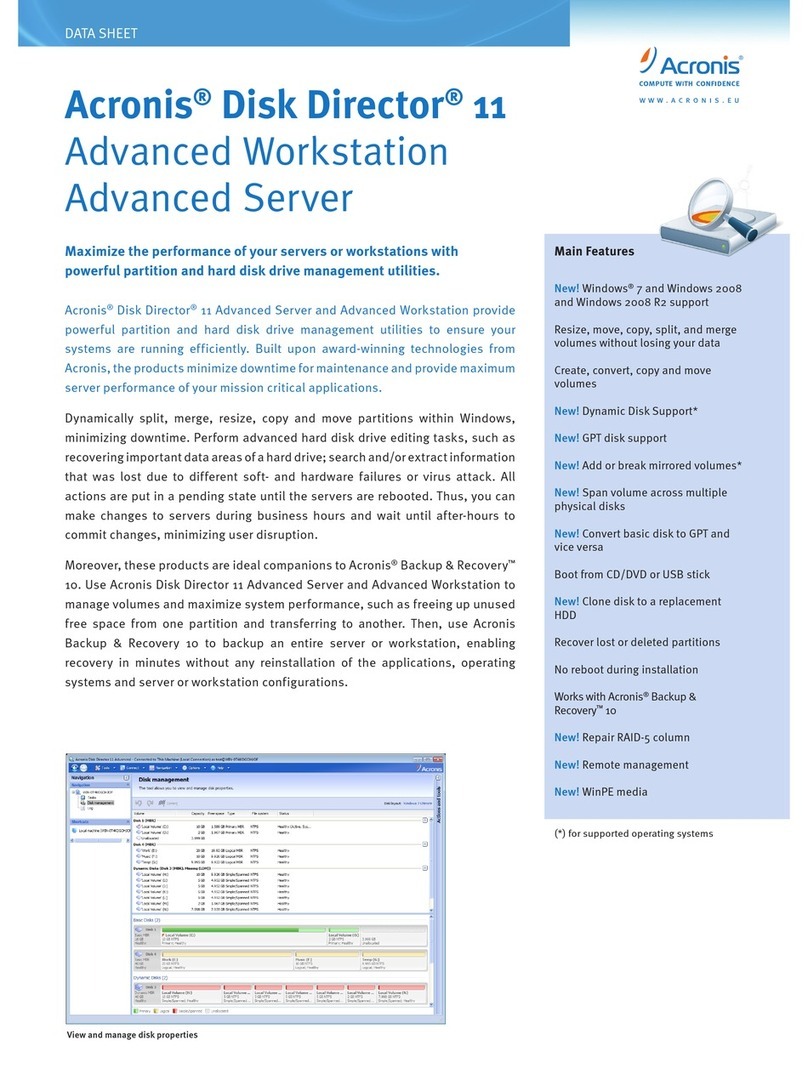
2.2 The main window......................................................................................................12
2.3 Logical software organization: sections....................................................................13
2.3.1 Complex PC clean-up.........................................................................................................13
2.3.2 Cleaning separate system components..............................................................................13
2.3.3 Additional cleanup tools......................................................................................................14
2.4 Acronis Privacy Expert Suite global settings............................................................14
2.4.1 General preferences ...........................................................................................................14
2.4.2 Scheduled tasks..................................................................................................................15
2.5 Executing PC clean-up manually..............................................................................15
2.6 Using File Shredder..................................................................................................15
2.7 Folders/files clean-up through the context menu .....................................................16
2.8 Clean-up settings......................................................................................................17
2.8.1 Clean-up settings editor......................................................................................................17
2.8.2 Setting PC component clean-up with the editor ..................................................................17
2.9 Separate components clean-up settings..................................................................18
2.10 System component clean-up settings...................................................................19
2.10.1 «Data destruction method» setting......................................................................................19
2.10.2 «Files» setting.....................................................................................................................19
2.10.3 «Computers» setting...........................................................................................................21
2.11 Clean-up settings of components related to working on the Internet....................22
2.11.1 «Internet Browsers» setting ................................................................................................22
2.11.2 «Address» setting...............................................................................................................22
2.12 Spyware clean-up preferences .............................................................................23
2.13 Executing scheduled PC clean-up........................................................................23
2.13.1 Invoking the scheduler........................................................................................................24
2.13.2 Scheduled tasks preferences..............................................................................................24
2.14 Paging file..............................................................................................................25
2.15 Renaming clean-up variants .................................................................................25
2.16 Using the Log ........................................................................................................26
CHAPTER 3. COMPLEX PC CLEAN-UP...................................................................................27
3.1 Entire PC clean-up....................................................................................................27
3.2 System clean-up.......................................................................................................28
3.3 Internet clean-up.......................................................................................................28
3.4 Complete spyware clean-up.....................................................................................28
CHAPTER 4. SEPARATE PC COMPONENTS CLEAN-UP......................................................29
4.1 System components.................................................................................................29