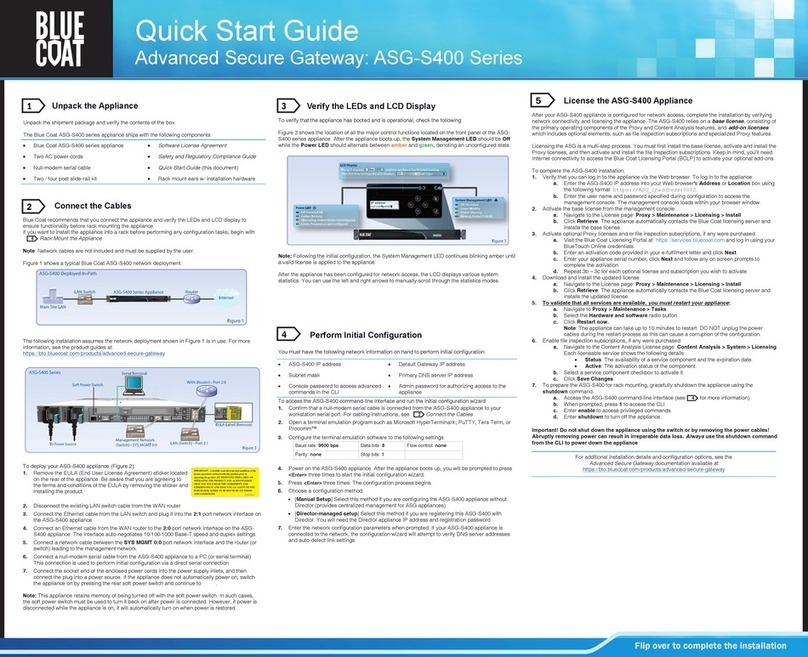
BELL LABS INNOVATIONS Lucent Technologies Access Security Gateway... User manual

Access Security Gateway
Guard and
Access Security Gateway
Guard Plus
User’s Guide
585-212-011
Comcode 108366030
Issue 1
March 1999

Copyright 1999 Lucent Technologies 585-212-011
All Rights Reserved Comcode 108366030
Printed in U.S.A. Issue 1
March 1999
Notice
While reasonable efforts were made to ensure that the information in this document was complete and accurate at the time of printing, Lucent
Technologies can assume no responsibility for any errors or liability for any direct or consequential damages resulting from use of the information.
Changes and/or corrections to the information contained in this document may be incorporated into future issues.
Responsibility for Your System’s Security
Toll fraud is the unauthorized use of your telecommunications system by an unauthorized party, for example, persons other than your company’s
employees, agents, subcontractors, or persons working on your company’s behalf. Note that there may be a risk of toll fraud associated with your
telecommunications system, and if toll fraud occurs, it can result in substantial additional charges for your telecommunications services.
You and your System Manager are responsible for the security of your system, such as programming and configuring your equipment to prevent
unauthorized use. The System Manager is also responsible for reading all installation, instruction, and system administration documents provided
with this product in order to fully understand the features that can introduce risk of toll fraud and the steps that can be taken to reduce that risk.
Lucent Technologies does not warrant that this product is immune from or will prevent unauthorized use of common carrier telecommunication
services or facilities accessed through or connected to it. Lucent Technologies will not be responsible for any charges that result from such
unauthorized use.
Trademark Notice
DEFINITY and INTUITY are registered trademarks of Lucent Technologies.
Disclaimer
Intellectual property related to this product (including trademarks) and registered to AT&T Corporation has been transferred to Lucent Technologies
Incorporated.
Any references within this text to American Telephone and Telegraph Corporation or AT&T should be interpreted as references to Lucent
Technologies Incorporated. The exception is cross references to books published prior to
December 31, 1996, which retain their original AT&T titles.
Heritage Statement
Lucent Technologies — formed as a result of AT&T’s planned restructuring — designs, builds, and delivers a wide range of public and private
networks, communication systems and software, consumer and business telephone systems, and microelectronics components. The world-
renowned Bell Laboratories is the research and development arm for the company.
Ordering Information
You can download a copy of this Guide and the ASG Guard/ASG Guard Plus Getting Started Guide from the Lucent website at
http://www.lucentdocs.com
.
Fraud Intervention
If you suspect you are being victimized by toll fraud and you need technical support or assistance, call the Lucent Technologies National Customer
Care Center at
1 800 643-2353
. For international customers, contact your local Center of Excellence.
To Get Help
If you need assistance with administration and configuration of the ASG Guard, call Ion Networks, Inc. at
1 732 494-4440
. Their technical support staff is available 9:00 a.m. to 5:00 p.m. EST Monday through Friday. This call may be billable. If you
believe you have a repair problem, call Lucent Technologies at
1 800 242-2121
or your local Authorized Dealer. For international customers,
contact your local Center of Excellence.
To resolve the problem as quickly as possible, describe the problem and note the steps that you have taken to resolve it. Also note the status of the
LEDs on the front panel.
Home Page
The home page for Lucent Technologies is
http://www.lucent.com
.

Table of Contents
1. About This Guide...............................................................................................................1
2. ASG Guard/ASG Guard Plus Overview....................................................................3
2.1 What This Chapter Contains..............................................................................................3
2.2 Terms.................................................................................................................................3
2.3 Notation Used in this Guide...............................................................................................3
2.4 ASG Guard/ASG Guard Plus Physical Overview..............................................................3
2.4.1 ASG Guard Configuration..........................................................................................4
2.4.2 ASG Guard Plus Configuration..................................................................................4
2.4.3 ASG Guard Front Panel ............................................................................................4
2.4.4 ASG Guard Rear Panel.............................................................................................5
2.4.5 ASG Guard Plus Front Panel ....................................................................................5
2.4.6 ASG Guard Plus Rear Panel.....................................................................................6
2.5 ASG Guard/ASG Guard Plus Functional Overview...........................................................7
2.6 Security Management........................................................................................................8
2.6.1 Access Classes .........................................................................................................8
2.6.2 User Database...........................................................................................................8
2.7 Alarm Management ...........................................................................................................9
2.8 Logs.................................................................................................................................10
2.9 Network Capabilities........................................................................................................10
2.10 Editing Modes..................................................................................................................12
2.10.1 TTY Mode................................................................................................................12
2.10.2 VT-100 Mode...........................................................................................................12
2.11 Using the Editing Keys.....................................................................................................13
2.12 Entering Commands........................................................................................................14
2.12.1 Entering/Selecting Parameters................................................................................15
3. Physical Connections and Installation...................................................................17
3.1 What This Chapter Contains............................................................................................17
3.2 LED Displays and Physical Connections.........................................................................17
3.2.1 LED Meanings.........................................................................................................17
3.2.2 Connecting a DCE device to a Host Port ................................................................19
3.3 Installation of the ASG Guard/ASG Guard Plus..............................................................20
3.3.1 Cables and Equipment Required.............................................................................20
3.3.2 Requirements for Network Applications ..................................................................20
3.3.3 Install the Unit..........................................................................................................20

ii
3.3.4 Power up the ASG Guard/ASG Guard Plus............................................................22
3.3.5 Verify PSTN Access ................................................................................................23
4. Basic Configuration........................................................................................................25
4.1 What This Chapter Contains............................................................................................25
4.2 Add the First User Profile................................................................................................25
4.2.1 Password/Callback Authentication Method.............................................................28
4.2.2 ASG Key Authentication Method.............................................................................30
4.3 Specify Network Parameters...........................................................................................32
4.4 Configure the AUX Port...................................................................................................33
4.5 Initiate Security on the AUX Port.....................................................................................35
4.6 Configure a Host Port......................................................................................................36
4.7 Re-Initialize the ASG Guard/ASG Guard Plus via the AUX Port.....................................40
5. Modem Port Setup...........................................................................................................41
5.1 What This Chapter Contains............................................................................................41
5.2 Overview..........................................................................................................................41
5.3 Modem Port Parameters..................................................................................................41
5.3.1 Display Modem Port Parameters – DM Command.................................................41
5.3.2 Set Modem Port Parameters – SM Command........................................................43
5.4 Verify the Settings............................................................................................................47
6. Modifying the User Database.....................................................................................49
6.1 What This Chapter Contains............................................................................................49
6.2 Overview..........................................................................................................................49
6.3 Display the User Maintenance Functions Menu..............................................................50
6.4 Command Summary........................................................................................................51
6.5 Add a User – AU Command............................................................................................52
6.5.1 ASG Key Authentication Method.............................................................................54
6.5.1.1 Encryption Key Source.......................................................................................55
6.5.1.2 Encryption Key Source: Randomly Generated...................................................55
6.5.1.3 Encryption Key Source: Device ID/User Code...................................................56
6.5.1.4 Encryption Key Source: Fixed ............................................................................56
6.5.2 Password/Callback Authentication Method.............................................................57
6.5.2.1 Access Option: Regular Callback.......................................................................57
6.5.2.2 Access Option: Passthru ....................................................................................58
6.5.2.3 Access Option: Variable Callback ......................................................................58
6.5.3 Page Authentication Method ...................................................................................58

iii
6.6 List Users – LU Command...............................................................................................60
6.7 Delete a User Profile – XU Command.............................................................................62
6.8 Display a User Record – DU Command.........................................................................63
6.9 Changing User Information – CU Command...................................................................64
6.10 Set Customer Key – SCK Command ..............................................................................67
6.11 List Lucent Users – LLU Command.................................................................................68
6.12 Block/Unblock Lucent User – BLU Command.................................................................68
6.13 Display Lucent User – DLU Command............................................................................68
6.14 Block/Unblock Lucent Administration – BLA Command..................................................69
7. File Buffering.....................................................................................................................71
7.1 What This Chapter Contains............................................................................................71
7.2 Overview..........................................................................................................................71
7.3 File Management Menu...................................................................................................72
7.4 RAM Disk Organization ...................................................................................................73
7.4.1 Host Port Buffer Naming..........................................................................................73
7.4.2 Buffer File Naming Conventions..............................................................................73
7.5 Set the RAM disk Protection Parameters........................................................................75
7.6 Buffering Data Received by a Host Port..........................................................................77
7.6.1 Automatic Buffering .................................................................................................77
7.6.2 Manual Buffering......................................................................................................79
7.6.3 Displaying the Status of a Buffer.............................................................................79
7.6.4 Sending Buffer Files to the Administration PC........................................................80
7.6.5 Using a Direct or Dial-up Connection......................................................................80
7.6.6 Using FTP to Send Files to Another Device............................................................81
7.6.6.1 Specify the FTP Parameters ..............................................................................81
7.6.6.2 Sending the File(s) via FTP................................................................................83
7.7 Receiving Files ................................................................................................................84
7.8 Managing Files ................................................................................................................85
7.9 File Command Summary.................................................................................................86
7.10 RAM Drive Events ...........................................................................................................88
7.11 Utility Programs ...............................................................................................................88
7.11.1 CSUM.EXE..............................................................................................................88
7.11.2 ZPAD.EXE...............................................................................................................88

iv
8. The Action and Event Tables......................................................................................89
8.1 What this Chapter Contains.............................................................................................89
8.2 Overview..........................................................................................................................89
8.3 Working with Action Tables .............................................................................................89
8.4 Structure of an Action Table............................................................................................90
8.4.1 Alarm Matching Criteria...........................................................................................91
8.4.2 Multiple Actions on a Single Alarm..........................................................................92
8.5 Planning the Action Table................................................................................................92
8.6 Action Table Commands .................................................................................................95
8.6.1 Adding an item to the Action Table – AA Command...............................................95
8.6.2 List Action Items – LA Command............................................................................97
8.6.3 Change Action Item – CA Command......................................................................98
8.6.4 Schedule Action Item – SAI Command...................................................................98
8.6.5 Delete Action Item – XA Command.........................................................................99
8.7 Alarm/Event Functions Commands...............................................................................101
8.7.1 List Alarms/Events – LE Command.......................................................................101
8.7.2 Generate Alarm/Event – GE Command................................................................101
8.7.3 Delete Alarm/Event – XE Command.....................................................................103
8.8 Internal Alarms and Events............................................................................................104
8.9 Action Routines..............................................................................................................107
9. System Functions..........................................................................................................109
9.1 What This Chapter Contains..........................................................................................109
9.2 Overview........................................................................................................................109
9.3 Systems Functions Menu ..............................................................................................109
9.4 System Parameter Functions ........................................................................................111
9.4.1 Set System Parameters – SSP Command............................................................111
9.4.1.1 Site information.................................................................................................111
9.4.1.2 Scheduling Parameters ....................................................................................113
9.4.1.3 Modem Action Routine Parameters..................................................................114
9.4.2 Display System Parameters – DSP Command.....................................................115
9.4.3 Set Host Processor Flag – SHP Command ..........................................................116
9.4.4 Set Date and Time – SDT Command....................................................................117
9.5 Device Management Functions.....................................................................................118
9.5.1 Check the Software Version – VER Command.....................................................118
9.5.2 Upgrade the Software – UPG Command..............................................................119
9.5.3 Restart the ASG Guard/ASG Guard Plus – BOOT Command..............................119
9.5.4 View or Save Configuration Data on Remote Device - DUMP Command............120

v
9.5.5 Save Configuration Data on RAM Disk File - DUMPF Command.........................120
9.5.6 Put Customer User Table on Remote Device – CDUMP Command....................120
9.5.7 Put Customer User Table on RAM Disk File – CDUMPF Command....................120
9.5.8 Load a Configuration File – CONFIG Command...................................................120
9.5.9 Load a Customer User Table – CCONFIG Command..........................................120
10. Environmental Manager...........................................................................................121
10.1 What This Chapter Contains..........................................................................................121
10.2 Overview........................................................................................................................121
10.3 ASG Guard/ASG Guard Plus Series Environmental Manager Options ........................121
10.4 Environmental Manager Functions and Commands .....................................................122
10.4.1 Set Sensor Alarms – SSA Command....................................................................122
10.4.2 Display Sensor Alarms – DSA Command.............................................................122
10.4.3 Display Sensor Inputs – DSI Command................................................................122
10.4.4 Display Contact Inputs – DCC Commands...........................................................122
10.4.5 Set Relays – SRLY Command..............................................................................123
10.4.6 Reset Relays – RRLY Command..........................................................................123
10.5 The Environmental Manager .........................................................................................124
10.5.1 The Environmental Interface of the ASG Guard Plus............................................124
10.5.2 The Environmental Interface of the ASG Guard....................................................126
10.6 Relays on the ASG Guard.............................................................................................128
10.7 Defining Threshold Limits – SSA Command.................................................................128
10.8 Analog Sensors .............................................................................................................130
10.8.1 48-Volt Battery.......................................................................................................130
10.8.2 Temperature..........................................................................................................130
10.8.3 Voltage Inputs........................................................................................................130
10.9 Contact Closure Inputs..................................................................................................131
10.10 Displaying Analog Sensor Inputs – DSI Command.......................................................131
10.11 Displaying the Status of Contact Inputs.........................................................................132
11. User Connectivity.......................................................................................................133
11.1 What This Chapter Contains..........................................................................................133
11.2 Overview........................................................................................................................133
11.3 Dial-up Preparations......................................................................................................133
11.4 Initiate a Dial-up Session...............................................................................................134
11.4.1 Password/Callback................................................................................................134
11.4.2 Regular Callback ...................................................................................................135
11.4.3 Using Variable Callback ........................................................................................137

vi
11.4.4 Using ASG Key......................................................................................................138
11.4.5 Using Pager Authentication Method......................................................................140
11.5 Session Control Functions and Commands..................................................................141
11.5.1 Join Lucent Host – JSL Command........................................................................141
11.5.2 Join Host Session – JS Command........................................................................141
11.5.3 View Session – VS Command...............................................................................142
11.5.4 Connect to Lucent Host – CONL Command.........................................................142
11.5.5 Connect to Host – CON Command.......................................................................142
11.5.6 Disconnect – DIS Command.................................................................................142
11.5.7 Terminal Mode – VT Command ............................................................................143
11.6 Port Control Commands................................................................................................143
11.6.1 Port Status – PST Command................................................................................143
11.6.2 Display Port Signals – DPS Command .................................................................144
11.6.3 Reset Port – RES Command.................................................................................144
12. Network Functions.....................................................................................................147
12.1 What This Chapter Contains..........................................................................................147
12.2 Overview of Supported Network Functions ...................................................................147
12.3 Overview of Telnet Support by ASG Guard/ASG Guard Plus.......................................148
12.4 Overview of SNMP Support by ASG Guard/ASG Guard Plus ......................................148
12.4.1 MIBs.......................................................................................................................148
12.4.2 ASG Guard/ASG Guard Plus MIB.........................................................................149
12.4.3 Delivery of SNMP Traps........................................................................................150
12.4.3.1 SNMP Traps Via Ethernet (Network)................................................................150
12.4.3.2 SNMP Traps Via PPP.......................................................................................150
12.5 Overview of FTP Support by ASG Guard/ASG Guard Plus..........................................150
12.6 Overview of PPP Support by ASG Guard/ASG Guard Plus..........................................151
12.7 Network Parameters......................................................................................................151
12.7.1 Set Network Parameters – SNP Command..........................................................152
12.7.1.1 Network Initialization Parameters.....................................................................152
12.7.1.2 SNMP Manager Parameters ............................................................................154
12.7.1.3 FTP Parameters ...............................................................................................155
12.7.2 Display Network Parameters – DNP Command....................................................157
12.8 Network Startup and Status...........................................................................................158
12.8.1 Startup Network – STARTNET Command............................................................158
12.8.2 Display Network Status – DNS Command............................................................158
12.9 Querying Remote Nodes – PING Command.................................................................159

vii
12.10 Telnet Port Parameters..................................................................................................159
12.10.1 Setting Telnet Port Parameters – ST Command...................................................159
12.10.2 Display Telnet Port Parameters – DT Command..................................................161
12.11 Initiate a PPP Link – PPP Command ............................................................................162
12.11.1 Designate a Port as a PPP Port............................................................................162
12.11.2 Initiate a PPP Connection On-Demand.................................................................162
12.11.2.1 ASG Guard/ASG Guard Plus Setup.................................................................163
12.11.2.2 Setup for PPP Client using "Dial-Up Networking" – New Connection..............163
12.11.2.3 Setup for PPP Client using "Dial-Up Networking" – Remote Connection ........164
12.11.2.4 Establishing a PPP Connection........................................................................164
12.12 Initiating a Telnet Session..............................................................................................165
12.12.1 Initiating a Telnet Session: Direct Connect ...........................................................165
12.12.2 Telnet Session via PPP through a ASG Guard/ASG Guard Plus.........................166
13. Log Functions..............................................................................................................167
13.1 What This Chapter Contains..........................................................................................167
13.2 Overview........................................................................................................................167
13.3 The Log Functions Menu...............................................................................................168
13.3.1 Access History – AH Command............................................................................168
13.3.2 Log History – LH Command..................................................................................170
13.3.3 Failure History – FH Command.............................................................................172
13.3.4 Display Error Log – DER Command .....................................................................174
13.3.5 Clear Log History – CLH Command......................................................................175
13.3.6 Clear Error Log – CER Command.........................................................................175
14. Events and Action Routines..................................................................................177
14.1 What This Chapter Contains..........................................................................................177
14.2 Overview........................................................................................................................177
14.3 Internal Events...............................................................................................................177
14.3.1 .AUTHFAIL Internal Event.....................................................................................177
14.3.2 .BAT48HIGH Internal Event ..................................................................................178
14.3.3 .BAT48LOW Internal Event ...................................................................................178
14.3.4 .BAT48OK Internal Event ......................................................................................179
14.3.5 .BUFREADY Internal Event...................................................................................179
14.3.6 .C#CLOSED Internal Event...................................................................................179
14.3.7 .C#OPEN Internal Event........................................................................................179
14.3.8 .CCLERROR Internal Event ..................................................................................180
14.3.9 .CLKCHANGE Internal Event................................................................................180
14.3.10 .DAILY Internal Event............................................................................................180

viii
14.3.11 .DISKCRIT Internal Event......................................................................................181
14.3.12 .DISKFULL Internal Event.....................................................................................181
14.3.13 .DTRHIGH, .DTRLOW, .DTRHIGH.n, and .DTRLOW.n Internal Events..............181
14.3.14 .HOURLY Internal Event .......................................................................................182
14.3.15 .INTBATLOW Internal Event .................................................................................182
14.3.16 .INTBATOK Internal Event ....................................................................................182
14.3.17 .LOGFULL Internal Event......................................................................................183
14.3.18 .MAXRETRY Internal Event ..................................................................................183
14.3.19 .MDMINITERR Internal Event ...............................................................................183
14.3.20 .MEMLOW Internal Event......................................................................................183
14.3.21 .MONTHLY Internal Event.....................................................................................184
14.3.22 .NETDOWN and .NETUP Internal Event ..............................................................184
14.3.23 .POWERLOW Internal Event.................................................................................184
14.3.24 .POWEROK Internal Event....................................................................................185
14.3.25 .POWERUP Internal Event....................................................................................185
14.3.26 .PPPREQ Internal Event .......................................................................................185
14.3.27 .RTSLOW.n and .RTSHIGH.n Internal Events......................................................186
14.3.28 .S#HIGH, .S#LOW, or .S#OK Internal Event ........................................................186
14.3.29 .TEMPHIGH...........................................................................................................187
14.3.30 .TEMPLOW Internal Events ..................................................................................187
14.3.31 .TEMPOK Internal Events .....................................................................................187
14.3.32 .WEEKLY Internal Event .......................................................................................188
14.4 ACTION ROUTINES......................................................................................................189
14.4.1 AUXCC Action Routine..........................................................................................189
14.4.2 CANCEL Action Routine........................................................................................189
14.4.3 CLKAHEAD and CLKBACK Action Routines........................................................190
14.4.4 CLKCHECK Action Routine...................................................................................190
14.4.5 DOLIST Action Routine.........................................................................................191
14.4.6 LOG Action Routine...............................................................................................191
14.4.7 LOGCHECK Action Routine..................................................................................192
14.4.8 NOACTION Action Routine...................................................................................192
14.4.9 PAGE Action Routine............................................................................................193
14.4.10 PHIRIS Action Routine..........................................................................................194
14.4.11 PHONHOME Action Routine.................................................................................195
14.4.12 PHPPP Action Routine..........................................................................................196
14.4.13 PHSYSOP Action Routine.....................................................................................196
14.4.14 REMINIT Action Routine .......................................................................................197

ix
14.4.15 RESRELAY Action Routine...................................................................................198
14.4.16 SCHEDULE Action Routine...................................................................................199
14.4.17 SETHP Action Routine ..........................................................................................200
14.4.18 SETRELAY Action Routine ...................................................................................201
14.4.19 SNMPTRAP...........................................................................................................202
Appendix A. ASG Key User’s Guide...........................................................................203
Appendix B. Port Default Settings...............................................................................207
Appendix C. Configuration Files..................................................................................211
Appendix D. Troubleshooting........................................................................................223
Appendix E. Internal Battery Replacement..............................................................225
Appendix F. Glossary of Command References...................................................241
Index..........................................................................................................................................247

x
Page intentionally left blank.

1
1. About This Guide
This manual describes the ASG Guard and the ASG Guard Plus. The following is an overview of
each chapter.
Chapter 1 About This Guide Briefly describes the contents of each
chapter.
Chapter 2 ASG Guard/ASG Guard Plus
Overview Contains an overview of the ASG
Guard/ASG Guard Plus operation. We
recommend that all Users read this
chapter.
Chapter 3 Physical Connections and
Installation Describes the required cable
connections and the power-up
procedure.
Chapter 4 Basic Configuration Describes the steps to get the ASG
Guard/ASG Guard Plus “up and
running.”
Chapter 5 Modem Port Setup Explains how to configure an ASG
Guard/ASG Guard Plus modem port.
All parameters to set-up modem ports
are described. These include baud
rate and parity, modem control
strings, and other port settings.
Chapter 6 Modifying the User Database Explains how to add, delete, and
change information in the user
database.
Chapter 7 File Buffering Describes how the ASG Guard/ASG
Guard Plus buffers data from host
ports and how to manage these files.
Chapter 8 The Action and Event Tables Explains how the ASG Guard/ASG
Guard Plus manages alarms. This
chapter also explains how to create,
modify and test Action Tables.
Chapter 9 System Functions Explains how to set the System
Parameters and Environmental
Control Functions. These parameters
include site name and phone
numbers, scheduling, and modem
action routines.
Chapter 10 Environmental Manager Contains information on how to use
the Environmental Manager to monitor
real-world events such as temperature
and voltage.

About This Guide
2
Chapter 11 User Connectivity Explains how to dial into the ASG
Guard/ASG Guard Plus and
authenticate. Also includes
information about joining sessions
that are in progress and secure port
management.
Chapter 12 Network Functions Includes instructions on how to set up
the network parameters, such as the
IP and Ethernet addresses.
Chapter 13 Log Functions Describes the Access, Failure and
System Error Logs maintained
automatically by the ASG Guard/ASG
Guard Plus. Also lists the commands
to display and clear the logs.
Chapter 14 Events and Action Routines Describes each Internal Event and
standard Action Routine. Examples
are also included.
Appendix A ASG Key User’s Guide Describes how to use the ASG Key.
Appendix B Port Default Settings Describes the default Port settings for
the ASG Guard/ASG Guard Plus.
Appendix C Configuration Files Describes the configuration file of the
ASG Guard/ASG Guard Plus.
Appendix D Troubleshooting Provides a table of symptoms,
causes, and possible solutions that
can be used for troubleshooting
problems when installing the ASG
Guard/ASG Guard Plus.
Appendix E Internal Battery Replacement Describes how to replace the battery
in the ASG Guard/ASG Guard Plus.
Appendix F Glossary of Command
References Provides a list of the commands for
the ASG Guard/ASG Guard Plus.

3
2. ASG Guard/ASG Guard Plus
Overview
2.1 What This Chapter Contains
•Figures and descriptions of the front panel connectors for the ASG Guard and ASG Guard
Plus
•Figures of the rear panel connectors for the ASG Guard and ASG Guard Plus
•ASG Guard/ASG Guard Plus Functions-Security Management, Alarm Handling, Data
Buffering, SNMP Management/Reporting
•Command Organization
•How to Display Menus and Issue Commands
2.2 Terms
Authentication method - Method of verifying that the person attempting to access the ASG
Guard/ASG Guard Plus or any protected resource, is an authorized user. Authentication
methods supported by the ASG Guard/ASG Guard Plus include Password/Callback, ASG Key,
and Pager.
Master user - A user with highest level of privileges. A master user may add and delete other
users, including other users with master level privileges.
System prompt - The system prompt is the "greater than" symbol ( > ) and includes the site
name. ASG Guard/ASG Guard Plus commands are typed at this prompt.
2.3 Notation Used in this Guide
Prompts appearing on the screen are typed in italics. Data entered at prompts are typed in bold.
2.4 ASG Guard/ASG Guard Plus Physical Overview
NOTE:
If your ASG Guard/ASG Guard Plus does not have a feature described in this manual,
contact Lucent Technologies or your distributor for upgrade information.

ASG Guard Overview
4
2.4.1 ASG Guard Configuration
The ASG Guard has the following components:
•four Host Ports (Asynchronous DCE Ports – DB9)
•two 33.3 Mhz Internal PCMCIA Modems
•one 10Base-T Ethernet Port
•five Contact Closure Inputs
•one 0-5 VDC Analog Input
•two Temperature Sensors; Temperature Probes required
•two Solid-State Relays (Relay #1 latching, Relay #2 non-latching)
•one 48 Volt Battery Monitoring Input
•one 32 MB Ram Disk
2.4.2 ASG Guard Plus Configuration
The ASG Guard Plus has the following components:
•16 or 28 Host Ports (Asynchronous DCE Ports – DB9)
•two 33.3 Mhz Internal PCMCIA Modems
•one 10Base-T Ethernet Port
•eight Contact Closure Inputs
•three 0-5 VDC Analog Inputs
•one Temperature Sensor; Temperature Probe required
•one 48 Volt Battery Monitoring Input
•one 32 MB Ram Disk
2.4.3 ASG Guard Front Panel
The LEDs, Aux port connector, and Key Switch are located on the front panel of the ASG Guard.
Figure 2-1 shows the front panel connectors of the ASG Guard.
0
1
AC
48VDC
BATTERY
PWR FAIL
PULSE
CLR
PEND
ALARM
EVENT
FILE
RX / TX
DTR
RX / TX
CD
RX
TX
AUX HOST
1234
MODEM
12
ETHERNET
AUX PORTPORTSSYSTEMPOWER
B
ASG Guard
Access Security Gateway Guard
Figure 2-1. ASG Guard Front Panel Connectors

ASG Guard Overview
5
The function of each connector is explained below.
Aux Port connector
You may administer the ASG Guard via a PC or terminal
connected to the front Aux connector.
Key switch
The key switch is used to turn the ASG Guard on and off. The
key can be removed in either the on or off position. The ASG
Guard cannot be turned on or off without a key.
LEDs
The LEDs display status messages. When the unit is operating
properly, the pulse LED will flash. The meaning of each LED is
explained in "LED Meanings," later in this chapter.
2.4.4 ASG Guard Rear Panel
Figure 2-2 shows the rear panel connectors of the ASG Guard.
Figure 2-2. ASG Guard Rear Panel Connectors
2.4.5 ASG Guard Plus Front Panel
The LEDs, Aux port connector, System Initialization Tag (SIT), and Key Switch are located on the
front panel of the ASG Guard Plus. Figure 2-3 shows the front panel connectors of the ASG
Guard Plus.
AC
48VDC
BATTERY
PWR FAIL
PULSE
CLR
PEND
ALARM
EVENT
FILE
RX / TX
DTR
RX / TX
CD
RX
TX
AUX HOST
1234
MODEM
12
ETHERNET
5 6 7 8 9 10 11 12 13 14 15 16
17 18 19 20 21 22 23 24 25 26 27 28
HOST EXPANSION
HOST EXPANSION
RX / TX
RX / TX
DTR
DTR
ASG Guard Plus
Access Security Gateway Guard Plus
ENTINEL
S
Figure 2-3. ASG Guard Plus Front Panel Connectors

ASG Guard Overview
6
The function of each connector is explained below.
Aux Port connector
You may administer the ASG Guard Plus via a PC or terminal
connected to either the front- or back-panel Aux connector.
SIT
The SIT (System Initialization Tag) contains information, unique
to your ASG Guard Plus, that can be transferred to the ASG
Guard Plus by inserting the SIT connector.
Key switch
The key switch is used to turn the ASG Guard/ASG
Guard Plus on and off. The key can be removed in either
the on or off position. The ASG Guard Plus cannot be
turned on or off without a key.
LEDs
The LEDs display status messages. When the unit is operating
properly, the pulse LED will flash. The meaning of each LED is
explained in "LED Meanings," later in this chapter.
2.4.6 ASG Guard Plus Rear Panel
Figure 2-4 shows the rear panel connectors of a 16-port ASG Guard Plus, and Figure 2-5 shows
the rear panel connectors of a 28-port ASG Guard Plus.
Figure 2-4. 16-Port ASG Guard Plus Rear Panel Connectors
Figure 2-5. 28-Port ASG Guard Plus Rear Panel Connectors

ASG Guard Overview
7
2.5 ASG Guard/ASG Guard Plus Functional Overview
The ASG Guard/ASG Guard Plus provides the following basic functions:
•secure access to host device
•site connectivity
•alarm processing
•data buffering
Area Function
Secure Access As a front end to host devices, the ASG Guard/ASG Guard Plus
provides secured access. All users connecting to the ASG
Guard/ASG Guard Plus via network, modem or directly (AUX Port)
need to authenticate themselves before being passed through to a
host device or permitted to administer the ASG Guard/ASG Guard
Plus. Several authentication mechanisms are available in the unit.
The ASG Guard/ASG Guard Plus also provides a logical switching
function, which allows an authorized user to connect to any host
device listed in the user’s profile.
Site Connectivity Acts as a central point for connection to all equipment at the site.
Allows connection via a local terminal, dial-up modem, and
Ethernet. A dial-up modem can also be used for PPP connections
allowing remote access to network-connected devices.
Alarm Processing When attached to a maintenance port of a host device, the ASG
Guard/ASG Guard Plus can process alarm messages and other
ASCII based data streams. Alarm messages can be delivered via
modem or network connectivity. Using either PPP or network
connectivity, the ASG Guard/ASG Guard Plus can deliver SNMP
traps to network managers. The ASG Guard/ASG Guard Plus can
convert ASCII based alarms received on its host ports to standard
SNMP traps. Acting as a SNMP trap proxy agent, the ASG
Guard/ASG Guard Plus allows legacy equipment to be managed
and provides alarm-reporting functions.
Data Buffering The ASG Guard/ASG Guard Plus can buffer all data transmitted to
a host port by the attached device. Data is collected on a
RAMdisk. Error messages, CDR, traffic data and other information
can be subsequently delivered to a central location via dial-up or
network.

ASG Guard Overview
8
2.6 Security Management
The ASG Guard/ASG Guard Plus maintains a database of authorized users (that is, User
Database). Only users listed in the database and who successfully authenticate are allowed
access. Authentication methods include password-oriented methods (Password, Callback, and
Variable Callback) and token methods (ASG Key and Pager).
A Master level user assigns each user when the user’s profile is added to the database. The
access class determines which ports can be addressed and what information can be viewed or
modified within the ASG Guard/ASG Guard Plus.
2.6.1 Access Classes
Master - Master access permits the user to change all information in ASG Guard/ASG Guard
Plus. The Master user can therefore control when and how alarms are reported, add and delete
users from the user database, change user profiles, modify Action and Event tables, manage
data buffering and access all hosts. The Master level is the highest level of access.
Sysop 2 - A Sysop 2 level user can perform all functions listed above except modifying the user
database. The Sysop 2 level user can access all hosts ports and has access to the file
commands used to manage data buffering, can make changes in how ASG Guard/ASG Guard
Plus responds to alarms, and change the port configuration of the unit.
Sysop 1 - The Sysop 1 level user can view pending alarms, but cannot change it. Data buffering
commands are not available to the Sysop 1 user. The Sysop 1 user can access all hosts.
Host 1 to Host n - The host user only has access to a single host device. The host user cannot
access any of the ASG Guard/ASG Guard Plus functions. n= number of the host user. ASG
Guard can have up to four host users. ASG Guard Plus can have 16 or 28 host users. (To have
28 host users, the ASG Guard Plus must have an expansion board.)
2.6.2 User Database
Each ASG Guard/ASG Guard Plus maintains a User Database, as stated above. The database
consists of a Customer User Table and a Lucent User Table. The Customer User Table contains
users added by a Customer Master User (Cmaster). The Lucent User Table contains users
added by a Lucent Master User (Lmaster). Lucent users provide remote maintenance support for
the ASG Guard/ASG Guard Plus for warranty issues and under Service Agreements. See
Chapter 6 for commands and capabilities associated with the Customer User Table and Lucent
User Table.
This manual suits for next models
3
Table of contents
Popular Gateway manuals by other brands

ICP DAS USA
ICP DAS USA tGW-718 quick start

RTA
RTA 460BCAWS-NNA4 Product user guide

Moxa Technologies
Moxa Technologies OnCell G3111-HSPA series user manual

Raritan
Raritan Command Center CC-SG Administrator's guide

Moxa Technologies
Moxa Technologies MGate 5217 Series user manual

Juniper
Juniper SSG 500M Series Hardware installation and configuration guide