Cisco MX60 User manual
Other Cisco Network Hardware manuals

Cisco
Cisco Firepower 2100 Series User manual

Cisco
Cisco SCE 2000 4/8xFE Operator's manual

Cisco
Cisco RSP4+ Bootflash Memory Upgrade to 16MB... Operator's manual

Cisco
Cisco DS-X9530-SF1-K9 - Supervisor-1 Module - Control... User manual

Cisco
Cisco Firepower 9300 Manual

Cisco
Cisco ASR 5000 User manual

Cisco
Cisco Gigabit Switch Router Cisco 12012 User manual

Cisco
Cisco UCS X10c Installation and maintenance instructions

Cisco
Cisco ATA 191 User manual

Cisco
Cisco Cisco ASA Series User manual

Cisco
Cisco Content Engine 510 User manual
Cisco
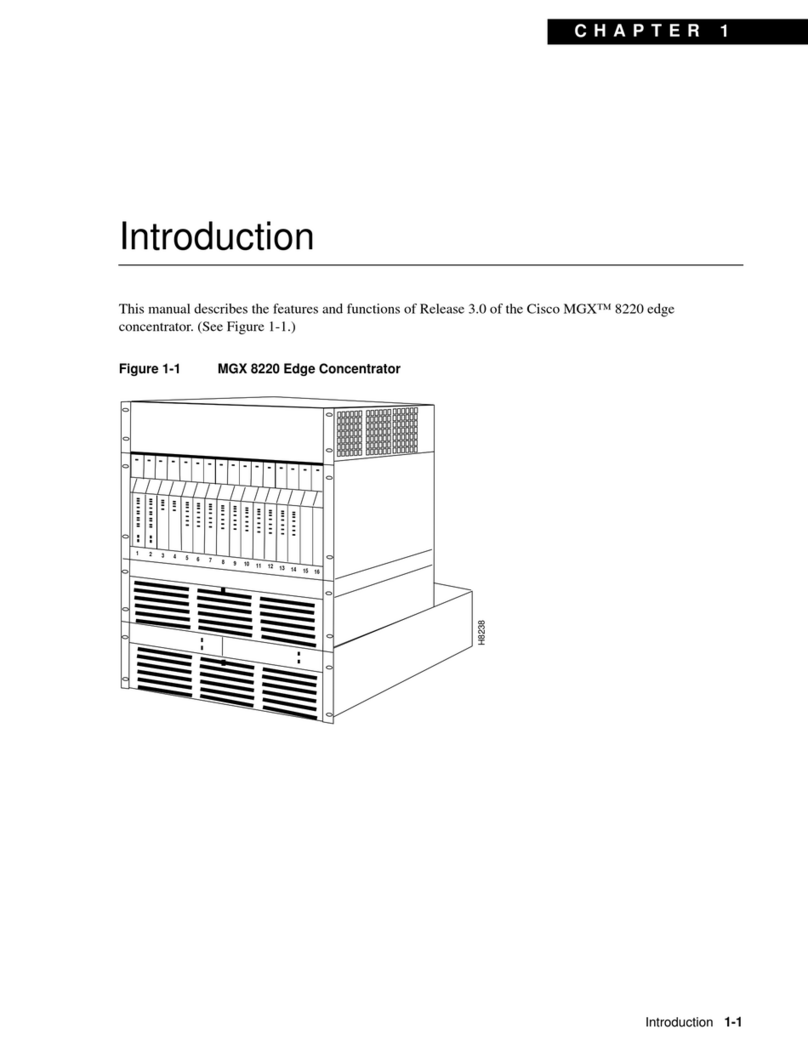
Cisco Edge Concentrator MGX 8220 Reference manual

Cisco
Cisco Linksys Business Series Network Storage System... User manual

Cisco
Cisco GS7000 Operating instructions

Cisco
Cisco GS7000 User manual

Cisco
Cisco GS7000 Operating instructions

Cisco
Cisco 2610 - Router - EN User manual
Cisco
Cisco ONS 15454 SDH E1-75 User manual

Cisco
Cisco 8011-2X2XP4L Manual

Cisco
Cisco ON100 Network Agent User manual
Popular Network Hardware manuals by other brands

Matrix Switch Corporation
Matrix Switch Corporation MSC-HD161DEL product manual

B&B Electronics
B&B Electronics ZXT9-IO-222R2 product manual

Yudor
Yudor YDS-16 user manual

D-Link
D-Link ShareCenter DNS-320L datasheet

Samsung
Samsung ES1642dc Hardware user manual

Honeywell Home
Honeywell Home LTEM-PV Installation and setup guide