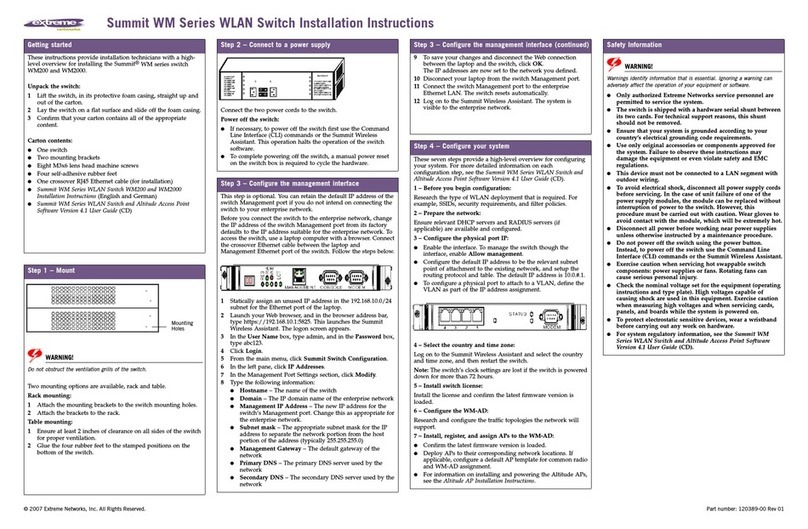
4
Extreme Networks Data Sheet: Summit X250e Series Technical Specifications
Comprehensive Security Management
User Authentication and Host Integrity Checking
Network Login and Dynamic Security Profile
NetworkLogincapabilityenforcesuseradmissionandusagepolicies.
SummitX250eseriesswitchessupportacomprehensiverangeofNetwork
Loginoptionsbyprovidingan802.1xagent-basedapproach,aWeb-based
(agent-less)logincapabilityforguests,andaMAC-basedauthentication
modelfordevices.WiththesemodesofNetworkLogin,onlyauthorized
usersanddevicesarepermittedtoconnecttothenetworkandbeassigned
totheappropriateVLAN.TheUniversalPortscriptingframeworkletsyou
implementDynamicSecurityProleswhichinsyncwithNetworkLogin
allowsyoutoimplementne-grainedandrobustsecuritypolicies.Upon
authentication,theswitchcanloaddynamicACL/QoSprolesforauseror
groupofusers,todeny/allowtheaccesstotheapplicationserversor
segmentswithinthenetwork.
Multiple Supplicant Support
Sharedportsrepresentapotentialvulnerabilityinanetwork.Multiple
supplicantcapabilityonaswitchallowsittouniquelyauthenticateand
applytheappropriatepoliciesandVLANsforeachuserordeviceona
sharedport.
MultiplesupplicantsupporthelpssecureIPTelephonyandwirelessaccess.
Convergednetworkdesignsofteninvolvetheuseofsharedports(see
Figure4).
Media Access Control (MAC) Lockdown
MACsecurityallowsthelockdownofaporttoagivenMACaddressand
limitingthenumberofMACaddressesonaport.Thiscanbeusedto
dedicateportstospecichostsordevicessuchasVoIPphonesorprinters
andavoidabuseoftheport—acapabilitythatcanbeespeciallyusefulin
environmentssuchashotels.Inaddition,anagingtimercanbecongured
fortheMAClockdown,protectingthenetworkfromtheeectsofattacks
using(oftenrapidly)changingMACaddresses.
IP Security
ExtremeXOSIPsecurityframeworkhelpsprotectthenetwork
infrastructure,networkservicessuchasDHCPandDNS,andhost
computersfromspoongandman-in-the-middleattacks.Italsohelps
protectthenetworkfromstaticallyconguredand/orspoofedIPaddresses
andbuildsanexternaltrusteddatabaseofMAC/IP/portbindingsso
youknowwherethetracfromaspecicaddresscomesfromfor
immediatedefense.
Identity Manager
IdentityManagerallowsnetworkmanagerstotrackuserswhoaccesstheir
network.UseridentityiscapturedbasedonNetLoginauthentication,LLDP
discoveryandKerberossnooping.ExtremeXOSusestheinformationto
thenreportontheMAC,VLAN,computerhostname,andportlocationof
theuser.Further,IdentityManagercancreatebothrolesandpolicies,
andthenbindthemtogethertocreaterole-basedprolesbasedon
organizationalstructureorotherlogicalgroupings,andapplythemacross
multipleuserstoallowappropriateaccesstonetworkresources.In
addition,supportforWideKeyACLsfurtherimprovessecuritybygoing
beyondthetypicalsource/destinationandMACaddressasidentication
criteriaaccessmechanismtoprovidelteringcapabilities.
Host Integrity Checking
Hostintegritycheckinghelpskeepinfectedornoncompliantmachineso
thenetwork.SummitX250eseriesswitchessupportahostintegrityor
endpointintegritysolutionthatisbasedonthemodelfromtheTrusted
ComputingGroup.
Network Intrusion Detection and Response
CLEAR-Flow Security Rules Engine
CLEAR-FlowSecurityRulesEngineprovidesrstorderthreatdetection
andmitigation,andmirrorstractoappliancesforfurtheranalysisof
suspicioustracinthenetwork.
Hardware-Based sFlow Sampling
sFlowisasamplingtechnologythatprovidestheabilitytocontinuously
monitorapplication-leveltracowsonallinterfacessimultaneously.
ThesFlowagentisasoftwareprocessthatrunsonSummitX250eand
packagesdataintosFlowdatagramsthataresentoverthenetworktoan
sFlowcollector.Thecollectorgivesanup-to-the-minuteviewoftrac
acrosstheentirenetwork,providingtheabilitytotroubleshootnetwork
problems,controlcongestionanddetectnetworksecuritythreats.
Port Mirroring
Forthreatdetectionandprevention,SummitX250esupportsmany-to-
oneandone-to-manyportmirroring.Thisallowsthemirroringoftracto
anexternalnetworkappliancesuchasanintrusiondetectiondevicefor
trendanalysisorforutilizationbyanetworkadministratorfordiagnostic
purposes.PortMirroringcanalsobeenabledacrossswitchesinastack.
Line-Rate ACLs
ACLsareoneofthemostpowerfulcomponentsusedincontrolling
networkresourceutilizationaswellasprotectingthenetwork.Summit
X250esupports1,024centralizedACLsper24-portblockbasedonLayer2,
3or4-headerinformationsuchastheMAC,IPv4andIPv6addressor
TCP/UDPport.ACLsareusedforlteringthetrac,aswellasclassifying
thetracowtocontrolbandwidth,priority,mirroringandpolicy-based
routing/switching.
Denial of Service Protection
SummitX250ecaneectivelyhandleDoSattacks.Iftheswitchdetectsan
unusuallylargenumberofpacketsintheCPUinputqueue,itwillassemble
ACLsthatautomaticallystopthesepacketsfromreachingtheCPU.Aftera
periodoftime,theseACLsareremoved,andreinstallediftheattack
continues.ASIC-basedLPMroutingeliminatestheneedforcontrolplane
softwaretolearnnewows,allowingmorenetworkresilienceagainst
DoSattacks.
Secure Management
Topreventmanagementdatafrombeinginterceptedoralteredby
unauthorizedaccess,SummitX250esupportsSSH2,SCPandSNMPv3
protocols.TheMD5hashalgorithmusedinauthenticationprevents
attackersfromtamperingwithvaliddataduringroutingsessions.