Technical Information Brochure Universal DECT Secury System 10.05.2012
Table of Contents 3
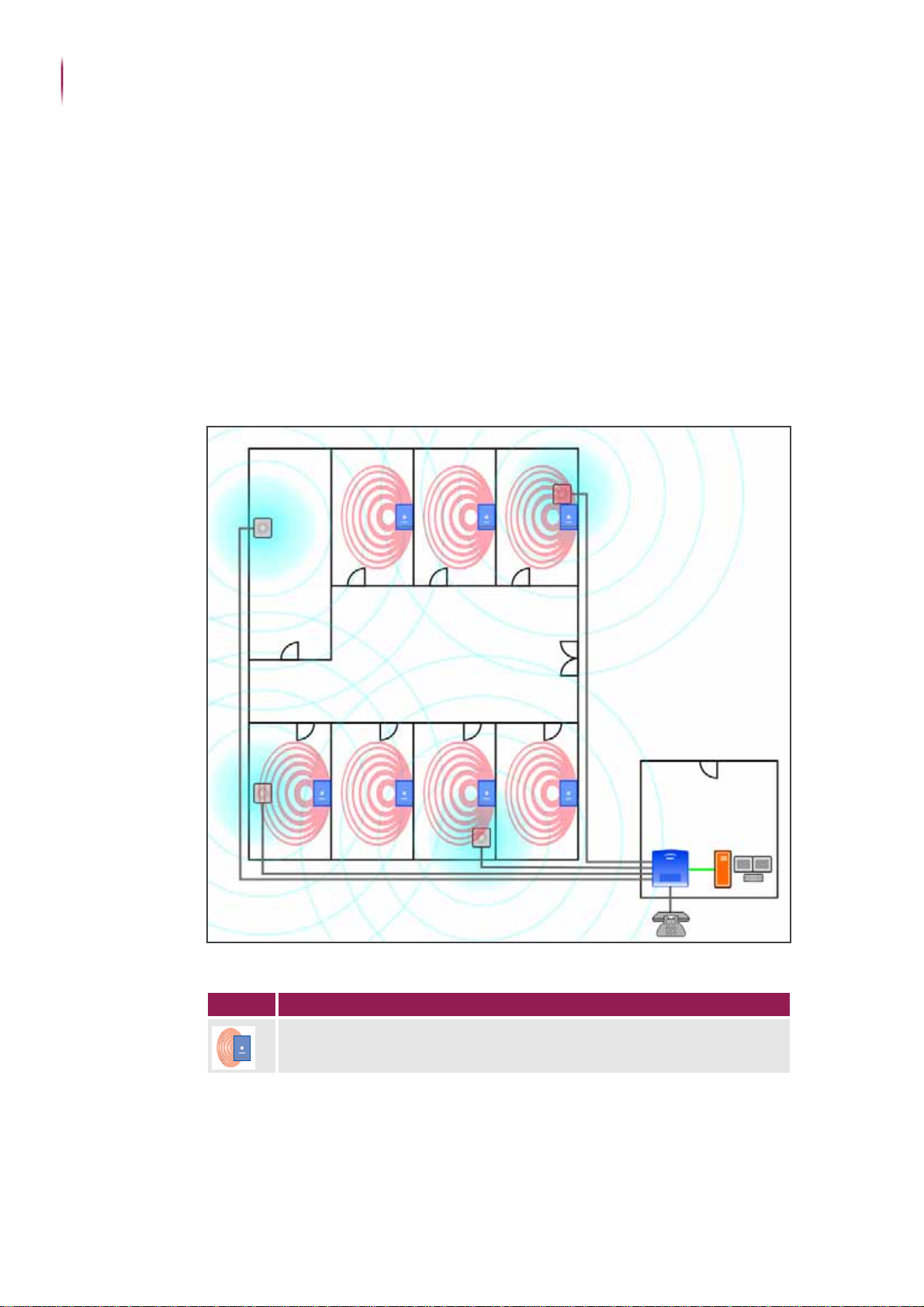
Table of Contents
1 Functional Description of UDSS .......................................................................................................... 4
1.1 What is UDSS? ..................................................................................................................... 4
1.2 Personal Emergency Signal Functionality ............................................................................ 6
1.3 Messaging ............................................................................................................................ 7
1.4 Operational requirements .....................................................................................................8
1.5 Operation of the UDSS ......................................................................................................... 9
1.6 UDSS supported by Inductive Localisation Beacons .......................................................... 10
1.7 Alarms ................................................................................................................................. 11
1.7.1 Alarm types............................................................................................................. 11
1.7.2 Alarm parameters ................................................................................................... 13
1.7.3 Login and log-off in the secure Secury mode ......................................................... 14
1.8 Localisation of personnel ....................................................................................................15
1.9 Alarm Activation .................................................................................................................. 16
1.9.1 Schematic representation ....................................................................................... 17
1.9.2 Processing an alarm ............................................................................................... 18
1.9.3 Expanded alarm procedures .................................................................................. 19
1.10 Application limits ................................................................................................................ 19
1.11 Scope of supply ................................................................................................................. 19
1.12 Commissioning .................................................................................................................. 20
2 UDSS Server ........................................................................................................................................ 21
2.1 Overview ............................................................................................................................. 21
2.2 Function .............................................................................................................................. 21
2.3 Connection type .................................................................................................................. 21
2.4 Secury Software ................................................................................................................. 22
2.4.1 Overview ................................................................................................................. 22
2.4.2 Configuration and Operation .................................................................................. 22
2.4.3 Warden’s Rounds Command and Control System (optional) ................................. 23
2.5 Guard module versions ....................................................................................................... 24
3 Handsets .............................................................................................................................................. 25
3.1 Technical data .................................................................................................................... 25
3.2 Handsets | Messaging-only Function .................................................................................. 26
3.3 Handsets | Alarm Function.................................................................................................. 27
3.4 MemCard ............................................................................................................................ 27
3.5 Accessories and enhancements ......................................................................................... 27
4 Inductive Localisation Beacon........................................................................................................... 28
4.1 Overview ............................................................................................................................. 28
4.2 Function .............................................................................................................................. 28
4.3 Properties ........................................................................................................................... 29
4.4 Technical data .................................................................................................................... 29
4.5 Accessories and Spares ..................................................................................................... 30
5 Application examples.......................................................................................................................... 31
5.1 Mid-sized retail business ....................................................................................................31
5.1.1 Technical Service ................................................................................................... 31
5.1.2 Security Personnel and House Detectives ............................................................. 31
5.2 Mid-sized business in the recycling industry ....................................................................... 33
5.2.1 Machine operators and assistants .......................................................................... 33
5.2.2 Electrician and mechanic ........................................................................................ 33
6 Abbreviations....................................................................................................................................... 35