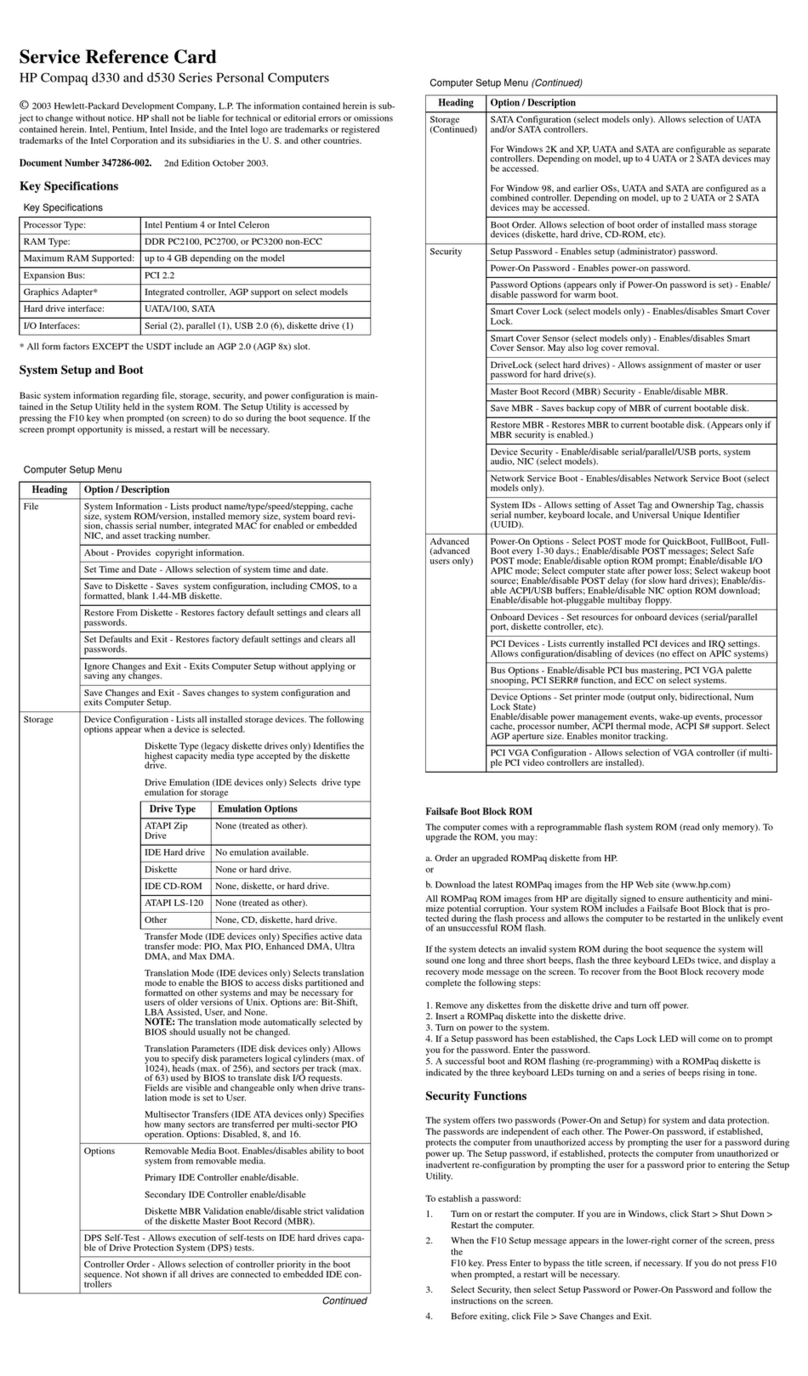
02/04/00 HP VISUALIZE WORKSTATIONS 4
network. This can lead to attempts to fool (e.g. spoofing) a system into believing an
alternate identity for the intruding system. However, HP-UX has added a number of
features that enhance its security capabilities.
HP-UX provides for security level certification to Department of Defense (DOD) C2 on
through B1. HP-UX can, providing that the administrator implements it, include security
processes utilizing Access Control Lists (ACLs) and a Shadow Password File. HP-UX
also fully supports the Distributed Computing Environment (DCE) which includes the
Distributed Security Services (DSS) support for a cross platform security environment.
DSS is a security mechanism to enable privacy and authenticity of client/server
transactions. Authentication, authorization and user account management is included in
this service. Finally, the Kerberos security protocol is also available for HP-UX, and is an
authentication mechanism that utilizes a “shared-secret-key” method of verification.
Windows NT View
of Security There was little thought given to security in the early days of MS/DOS. It was, of course,
a simplified operating system for personal computers where the individual had complete
control of local system resources and very limited access to shared resources (i.e. printers
and directories of files). As PCs began to share resources, a fundamental security process
was implemented. Cooperative file password security was placed on shared resources like
printers and directories. That is, the owners of the resource could share it without a
password. However, when a resource is shared with a password, it is open to anyone that
has (or can guess) the password. It is not tied to user identification or authentication.
Windows NT was planned from the start to have strong security, owning its heritage to
VMS and Windows NT’s chief architect, David Cutler.
In Windows NT, like UNIX, it is up to the administrator to implement security. For
example, the file security with an ACL’s type model is only available with the NTFS file
system. The administrator must explicitly format the hard disk drive with NTFS to
achieve this level of security. The operating system itself imposes a level of security on
all system calls for its services (i.e. system level objects). That is, when a program (a
thread actually) requests a resource, the OS verifies the thread’s security token. The
security token provides information on what resources this thread can have access to. This
token is based upon a previously authenticated and authorized user activation process.
The user logon procedure utilizes encrypted DES (Data Encryption Standard) passwords
over the net. In addition, Windows NT has encryption and challenge/response for system
authentication. Today, Windows NT 4.0 can also participate in DCE security, but only as
it relates to Remote Procedure Calls (RPC).
It is reported that Windows NT 5.0 will incorporate Kerberos as a system wide
authentication mechanism. This should allow Windows NT to have enhanced integration
capability into the UNIX security paradigm.