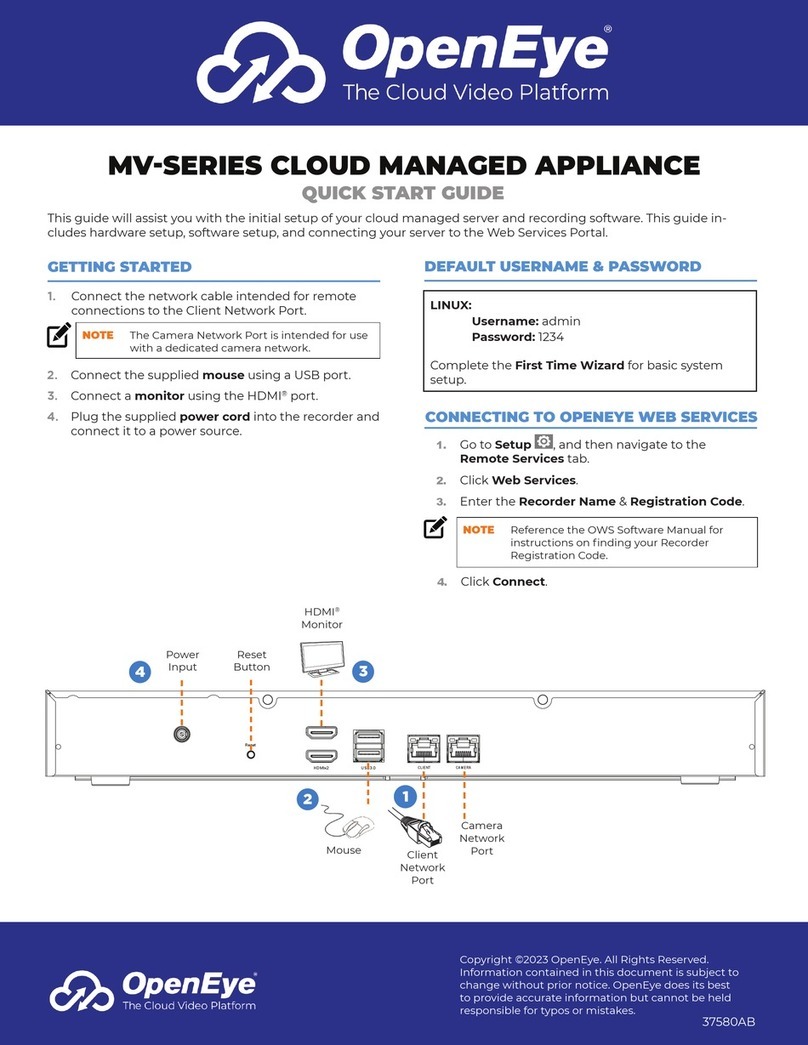
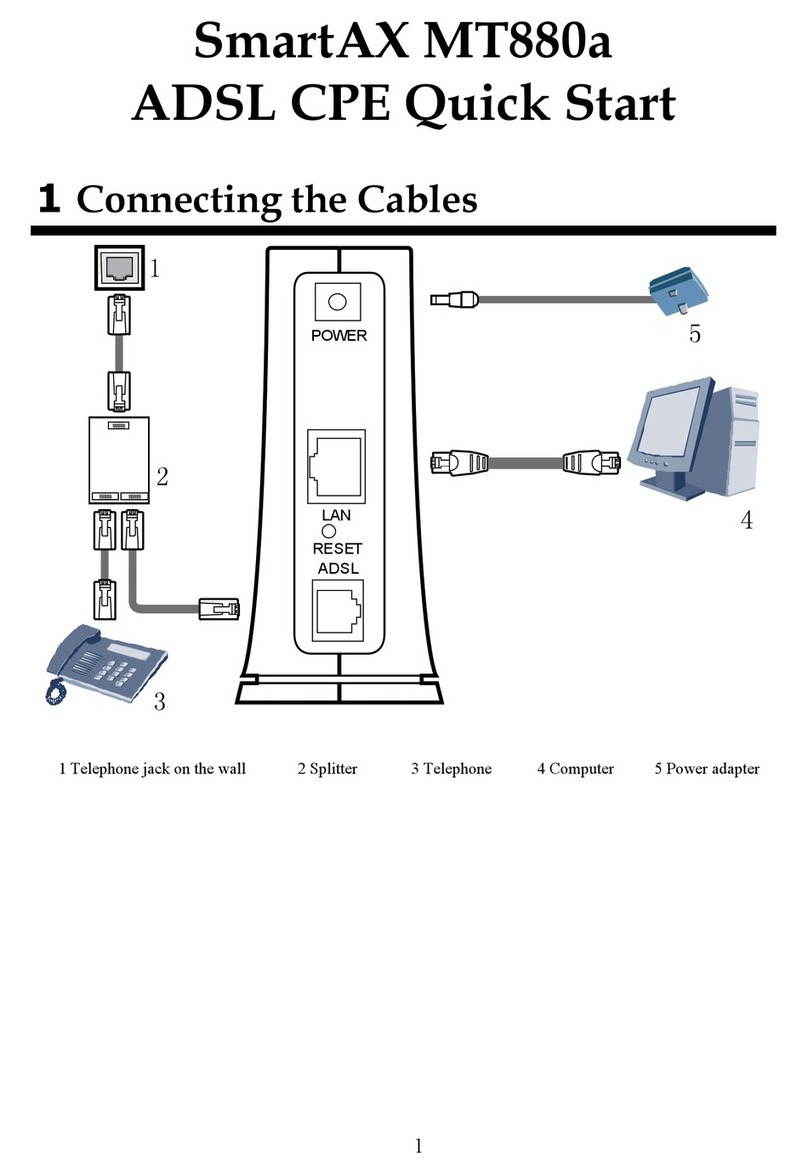
iii
Other Terms and Conditions
This product includes software developed by Cavium Networks. Copyright © 2003-2005 Cavium Networks
This product includes software developed by Tarari, Inc. Copyright © 2003-2007 Tarari, Inc. All rights reserved.
This product includes software and algorithms developed by RSA Data Security Inc., including the RSA Data Security, Inc.
MD5 Message Digest Algorithm.
**********************************************************************************************************************************
This product includes software developed by the University of California, Berkeley and its contributors.
Copyright © 1983, 1990, 1991, 1992, 1993, 1994, 1995, 1996 The Regents of the University of California.
This product contains software developed by the Net-SNMP project. Copyright © 1989, 1991, 1992 by Carnegie Mellon
University. Copyright © 2001-2003, Networks Associates Technology, Inc. All rights reserved. Portions of this code are
copyright © 2001-2003, Cambridge Broadband Ltd. All rights reserved. Portions Copyright © Sun Microsystems, Inc., 4150
Network Circle, Santa Clara, California 95054, USA, All rights reserved. Portions Copyright © 2003-2006 Sparta, Inc, All rights
reserved. Portions Copyright © 2004 Cisco, Inc and Information Network Center of Beijing University of Posts and
Telecommunications, All rights reserved. Portions Code are copyright © 2003 Fabasoft R&D Software GmbH & Co KG.
This product contains software developed through the Internet Software Consortium (http://www.isc.org). Copyright © 1996-
2003 Internet Software Consortium. Portions Copyright © 1996-2001 Nominum, Inc. Portions Copyright © 2004, 2005 Internet
Software Consortium, Inc. ("ISC")
This product contains software developed by Sendmail, Inc. Copyright © 1998-2006 Sendmail, Inc. All rights reserved.
This product includes software developed by the Python Software Foundation. All rights reserved.
This product includes cryptographic software written by Eric Young (eay@cryptsoft.com).
This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http:// www.openssl.org)
Copyright © 1998-2005 The OpenSSL Project. All rights reserved.
This product utilizes MySQL (http://www.mysql.com/). Copyright © 1995, 1996, 2000 TcX AB & Monty Program KB & Detron
Stockholm SWEDEN, Helsingfors FINLAND and Uppsala SWEDEN. All rights reserved.
This product incorporates compression code from the Info-ZIP group. There are no extra charges or costs due to the use of
this code, and the original compression sources are freely available from http://www.info-zip.org or ftp://ftp.info-zip.org on the
Internet.
This product includes software developed at the Information Technology Division, US Naval Research Laboratory. Copyright ©
1995 US Naval Research Laboratory (NRL). All Rights Reserved.
This product includes software developed by Computing Services at Carnegie Mellon University
(http://www.cmu.edu/computing/). Copyright © 1998-2003 Carnegie Mellon University. All rights reserved.
This product incorporates the Mailshell Anti-Spam SDK, which is Copyright © 1999-2007 Mailshell.
This product incorporates the PCRE library package, which is open source software, written by Philip Hazel, and copyrighted
by the University of Cambridge, England.
This product also uses libspf, an implemention of the Sender Policy Framework, which is Copyright © 2004 James Couzens &
Sean Comeau All rights reserved.
This product includes the OpenSSH package. Portions Copyright © 1998 CORE SDI S.A., Buenos Aires, Argentina. Portions
Copyright © 1995, 1996 by David Mazieres. Portions Copyright © 1995 Patrick Powell. Portions Copyright Markus Friedl,
Theo de Raadt, Niels Provos, Dug Song, Aaron Campbell, Damien Miller, Kevin Steves, Daniel Kouril, Wesley Griffin, Per
Allansson, Nils Nordman, Simon Wilkinson, Ben Lindstrom, Tim Rice, Andre Lucas, Chris Adams, Corinna Vinschen, Cray
Inc., Denis Parker, Gert Doering, Jakob Schlyter, Jason Downs, Juha Yrjl, Michael Stone, Networks Associates Technology,
Inc., Solar Designer, Todd C. Miller, Wayne Schroeder, William Jones, Darren Tucker, Eric P. Allman.
Redistribution and use in source and binary forms of the above listed software, with or without modification, are permitted
provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer
in the documentation and/or other materials provided with the distribution.
3. Neither the name of the University nor the names of its contributors may be used to endorse or promote products derived
from this software without specific prior written permission.