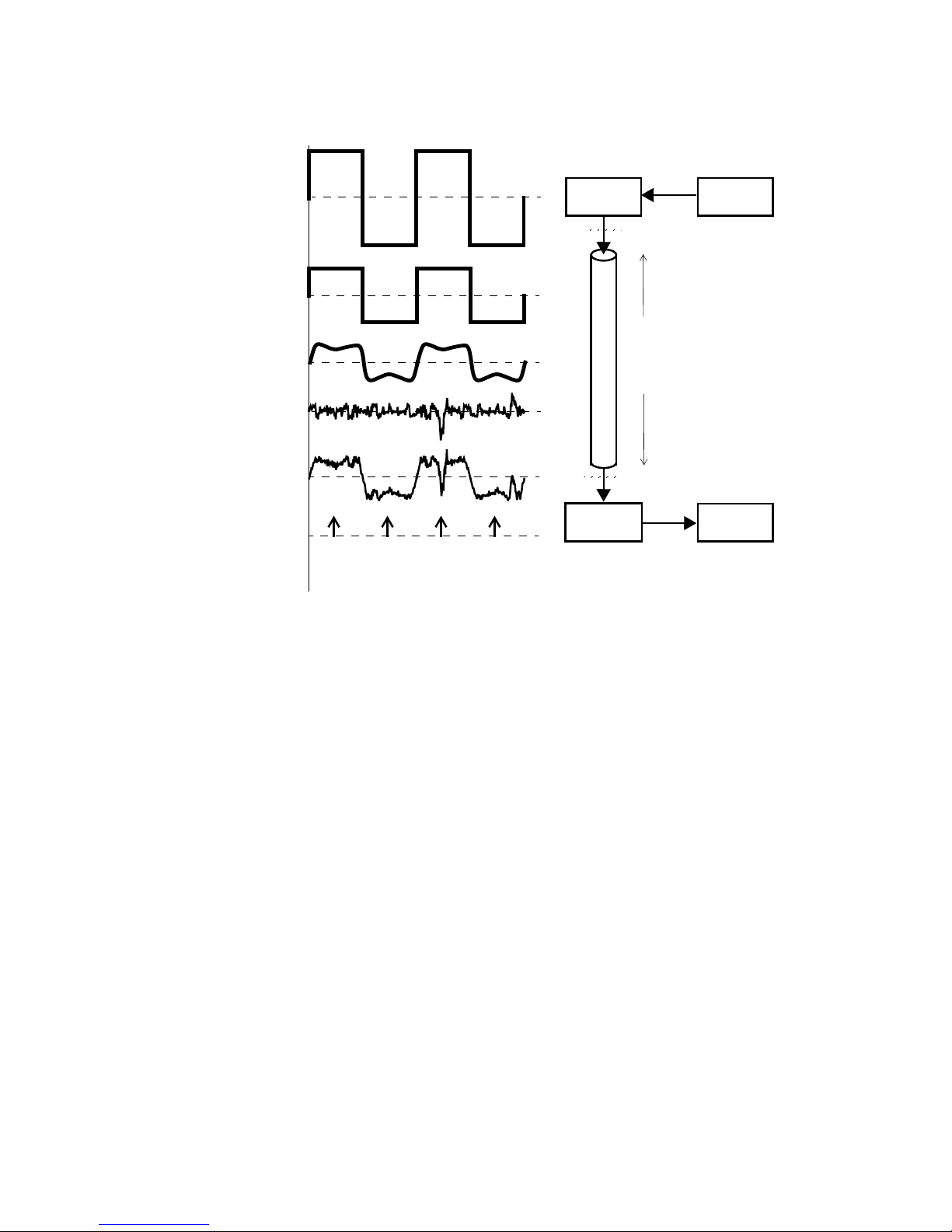
ALBEDO AT.2048
8
Example: A typical value of S/N for a voice grade line is 30 dB (equivalent to a
power ratio of 1,000:1). Thus for a bandwidth of 3,100 Hz the maximum data trans-
fer rate (C) should be 30,894 bit/s.
If we pay attention only to the Nyquist formula (see Section 1.2.2) we could in-
accurately conclude that for a given bandwidth (B) the data rate can be increased
endlessly, by increasing the number of signal elements. However in reality, the sig-
nal-to-noise ratio sets up the theoretical limit of the channel capacity.
The Shannon theorem makes no statement as to how the channel capacity is
achieved. In fact, channels only approach this limit. The task of providing high chan-
nel efficiency is the goal of coding techniques.
1.2.4 The transmission channel
A digital channel is a communication subsystem with capacity to send and receive
information between two points: a source and a sink. Related concepts are:
•Bandwidth, expressed in hertz (Hz). This is the difference between the highest
and the lowest frequency that can be transmitted across a line or a network.
•Data rate, expressed in bits per second (bit/s). This is a measure of the speed
with which information is transferred. It depends on the bandwidth, transmis-
sion medium impairments, and the technological capacity to efficiently use the
available bandwidth.
•Performance, expressed in bit error rate (BER). This is the probability of a sin-
gle bit being corrupted in a defined interval. Performance is on indication of
the quality of the channel.
Channel capacity is the data rate that can be transmitted over a communication path
under specific conditions.When two channels define a two-way communication, it
is more usual to talk about a circuit.
1.3 Channel Coding
Channel coding is the process that transforms binary data bits into signal elements
that can cross the transmission medium. In the simplest case, in a metallic wire a bi-
nary 0 is represented by a lower voltage, and a binary 1 by a higher voltage. How-
ever, before selecting a coding scheme it is necessary to identify some of the
strengths and weaknesses of line codes:
•High-frequency components are not desirable because they require more chan-
nel bandwidth, suffer more attenuation, and generate crosstalk in electrical
links.