Entrust nShield 5s User manual

nShield® 5s
Installation Guide
13.3
04 May 2023

Contents
1. Introduction. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê4
1.1. About this guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê4
2. Hardware security modules. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê5
2.1. Electrical power requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê5
2.2. Handling modules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê5
2.3. Module operational temperature and humidity specifications. . . . . . . . . . . . . . . . . . Ê5
2.4. Cooling requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê6
2.5. Physical location considerations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê7
3. Regulatory notices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê8
3.1. FCCÊclass AÊnotice . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê8
3.2. Canadian certification - CAN ICES-3 (A)/NMB- 3(A) . . . . . . . . . . . . . . . . . . . . . . . . . Ê8
3.3. Battery cautions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê8
3.4. Hazardous substance caution. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê8
3.5. Recycling and disposal information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê8
4. Before installing the module. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê9
4.1. Back panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê9
4.2. Module pre-installation steps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê9
4.3. Fitting a module bracket . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê10
4.4. User Replaceable items . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê10
5. Installing the module. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê12
5.1. Fitting a smart card reader . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê12
5.2. After installing the module. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê12
6. Before you install the software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê14
6.1. Preparatory tasks before installing software. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê14
6.2. Firewall settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê18
7. Installing the software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê20
7.1. Installing the Security World Software on Windows. . . . . . . . . . . . . . . . . . . . . . . . . . Ê20
7.2. Installing the Security World Software on Linux . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê22
8. Setting the system clock . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê25
8.1. Setting the HSM system clock . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê25
9. Checking the installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê26
9.1. Checking operational status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê26
9.2. Log message types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê27
10. Status indicators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê30
10.1. Normal operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê30
10.2. Error indication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê30
Appendix A: Uninstalling existing software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê31
A.1. Uninstalling the Security World Software on Windows . . . . . . . . . . . . . . . . . . . . . . . Ê32
nShield® 5s Installation Guide 2 of 37

A.2. Uninstalling the Security World Software on Linux . . . . . . . . . . . . . . . . . . . . . . . . . . Ê32
Appendix B: Software packages on the Security World installation media . . . . . . . . . . . . Ê34
B.1. Security World installation media. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê34
B.2. Components required for particular functionality . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê35
B.3. nCipherKM JCA/JCE cryptographic service provider . . . . . . . . . . . . . . . . . . . . . . . . Ê36
B.4. SNMP monitoring agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Ê37
nShield® 5s Installation Guide 3 of 37

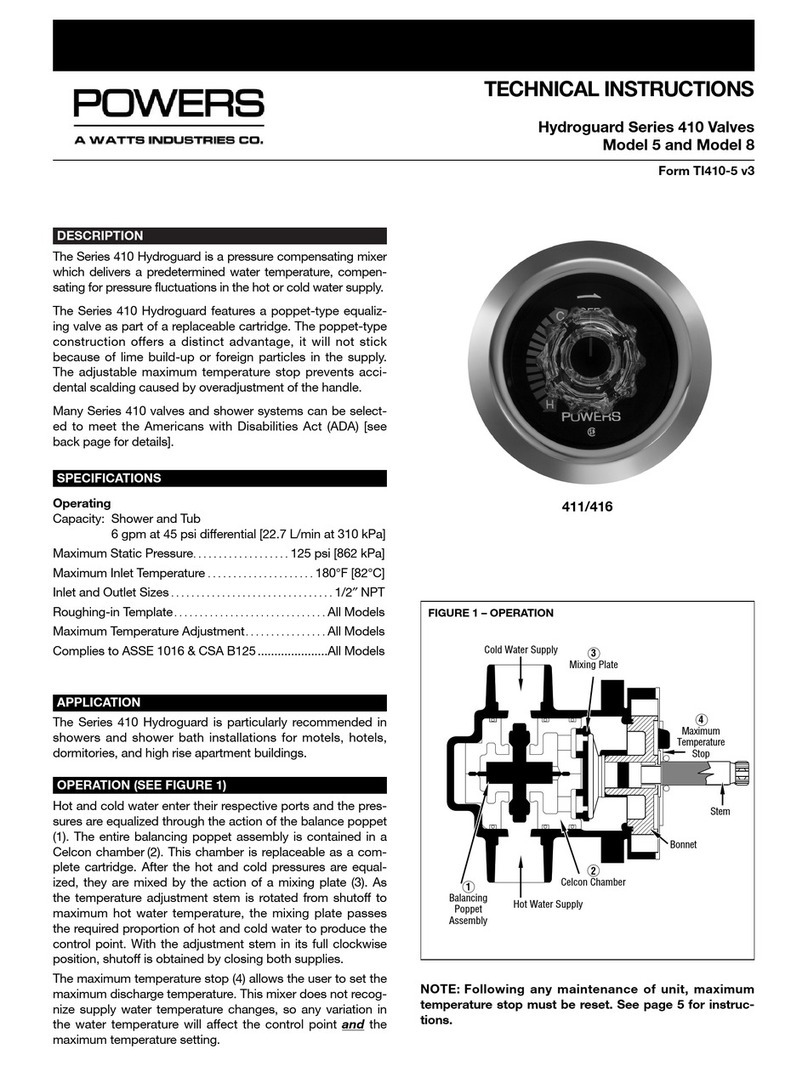
1. Introduction
The Entrust nShield nShield 5s is a Hardware Security Module (HSM) for servers and
appliances.
1.1. About this guide
This guide includes:
•Installing the nShield nShield 5s. See Installing the module.
•Installing the Security World Software. See Installing the software.
•Steps to check the installation. See Checking the installation.
•A description of the module status indicators. See Status indicators
•Instructions about removing existing software. See Uninstalling existing software.
See the User Guide for your module and operating system for more about, for example:
•Creating and managing a Security World
•Creating and using keys
•Card sets
•The advanced features of the nShield nShield 5s.
For information on integrating Entrust nShield products with third-party enterprise
applications, see https://www.entrust.com/digital-security/hsm.
1.1.1. Model numbers
Model numbering conventions are used to distinguish different nShield hardware security
devices.
Model number Used for
NC5536E-B nShield 5s Base
NC5536E-M nShield 5s Medium
NC5536E-H nShield 5s High
1.1.2. Terminology
The nShield nShield 5s is referred to as the nShield nShield 5s, the Hardware Security
Module, or the HSM in this guide.
nShield® 5s Installation Guide 4 of 37

2. Hardware security modules
2.1. Electrical power requirements
Module Maximum power
nShield 5s 25W
Make sure that the power supply in your computer is rated to supply
the required electric power.
The PCIe card, nShield 5s, is intended for installation into a certified personal computer,
server, or similar equipment.
If your computer can supply the required electric power and sufficient cooling, you can
install multiple modules in your computer.
2.2. Handling modules
The module contains solid-state devices that can withstand normal handling. However,
do not drop the module or expose it to excessive vibration.
Before installing hardware, you must disconnect your computer from
the power supply. Ensure that a grounded (earthed) contact remains.
Perform the installation with care, and follow all safety instructions in
this guide and from your computer manufacturer.
Static discharge can damage modules. Do not touch the module
connector pins, or the exposed area of the module.
Leave the module in its anti-static bag until you are ready to install it. Always wear an
anti-static wrist strap that is connected to a grounded metal object. You must also
ensure that the computer frame is grounded while you are installing or removing an
internal module.
2.3. Module operational temperature and humidity
specifications
The nShield 5s module operates within the following environmental conditions.
nShield® 5s Installation Guide 5 of 37

nShield 5s environmental
conditions
Operating range Comments
Min. Max.
Operating temperature* 5°C (41°F) 55°C (131°F) Subject to sufficient
airflow
Storage temperature -5°C (-23°F) 60°C (140°F) -
Transportation
temperature
-40°C (-40°F) 70°C (158°F) -
Operating humidity 5% 85% Relative. Non-condensing
at 30°C (86°F)
Storage humidity 5% 93% Relative. Non-condensing
at 30°C (86°F)
Transportation humidity 5% 93% Relative. Non-condensing
at 30°C (86°F)
Altitude -100m (-328ft) 2000m (6561ft) Above Mean Sea Level
*Air temperature at PCIe card inlet surface. For more information, see Cooling
requirements.
The module is designed to operate in moderate climates only. Never
operate the module in dusty, damp, or excessively hot conditions.
Never install, store, or operate the module at locations where it may be
subject to dripping or splashing liquids.
2.4. Cooling requirements
An air velocity of 1.9 m/s (373 LFM) is recommended for a module in
operation.
During installation, ensure there is adequate airflow around the module. Airflow from fans
must be directed to the inlet surface of the module such that air is flowing through and
across the length of the module. To maximize airflow, use a PCIe slot with no neighboring
modules if possible. If airflow is limited, consider fitting extra cooling fans.
The nShield 5s module is a passively cooled PCIe card that requires the
host to provide sufficient airflow for cooling. Passive cards should not
be powered without cooling airflow in place.
nShield® 5s Installation Guide 6 of 37

Ensure the module has adequate cooling. Failure to do so can result in
damage to the module or computer.
To check the actual and maximum temperature of the module during operation, see the
Maintenance of nShield Hardware section of the User Guide for your module and
operating system. It is advised to do this directly after installing the module in its normal
working environment. Monitor the temperature of the module over its first few days of
operation.
2.4.1. Cooling recommendations for a desktop installation
For a desktop installation running in operating environmental conditions, dedicated
airflow is required across the module. If the system cannot provide the necessary airflow,
Entrust recommends you add a sufficiently powerful dedicated fan to directly cool the
module. For details regarding the cooling requirements see Cooling requirements.
2.4.2. Cooling recommendations for a server installation
The desktop cooling recommendations further apply to a server installation. In addition,
power and airflow control software is sometimes available in a server installation. If this is
the case, Entrust recommends you:
•Configure the target air velocity in the software to ensure it does not fall below the
airflow recommendations of the module. For details regarding the cooling
requirements, see Cooling requirements.
•Ensure that the PCIe slot has been configured to fulfil the module power
requirements.
2.5. Physical location considerations
For the certification of Entrust nShield HSM, refer to the Security Manual. In addition to
the intrinsic protection provided by an nShield HSM, customers must exercise due
diligence to ensure that the environment within which the nShield HSMs are deployed is
configured properly and is regularly examined as part of a comprehensive risk mitigation
program to assess both logical and physical threats. Applications running in the
environment shall be authenticated to ensure their legitimacy and to thwart possible
proliferation of malware that could infiltrate these as they access the HSMs’
cryptographic services. The deployed environment must adopt 'defense in depth'
measures and carefully consider the physical location to prevent detection of
electromagnetic emanations that might otherwise inadvertently disclose cryptographic
material.
nShield® 5s Installation Guide 7 of 37

3. Regulatory notices
3.1. FCCÊclass AÊnotice
The nShield nShield 5s HSMs comply with Part 15 of the FCC rules. Operation is subject
to the following two conditions:
1. The device may not cause harmful interference, and
2. The device must accept any interference received, including interference that may
cause undesired operation.
This equipment has been tested and found to comply with the limits for a Class A digital
device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide
reasonable protection against harmful interference when the equipment is operated in a
commercial environment. This equipment generates, uses, and can radiate radio
frequency energy and, if not installed and used in accordance with the instruction
manual, may cause harmful interference to radio communications. Operation of this
equipment in a residential area is likely to cause harmful interference in which case the
users will be required to correct the interference at their own expense.
3.2. Canadian certification - CAN ICES-3 (A)/NMB- 3(A)
3.3. Battery cautions
Danger of explosion if the battery is incorrectly replaced. The battery may only be
replaced with the same or equivalent type. Dispose of the used battery in accordance
with your local disposal instructions.
3.4. Hazardous substance caution
This product contains a lithium battery and other electronic components and materials
which may contain hazardous substances. However, this product is not hazardous
providing it is used in the manner in which it is intended to be used.
3.5. Recycling and disposal information
For recycling and disposal guidance, see the nShield product’s Warnings and Cautions
documentation.
nShield® 5s Installation Guide 8 of 37

4. Before installing the module
4.1. Back panel
Label Description
A Status LED
B Recovery mode button
C A mini-DIN connector for connecting a smart card reader.
4.2. Module pre-installation steps
Check the module to ensure that there is no sign of damage or tampering:
•Check the epoxy resin security coating for obvious signs of damage.
•If you intend to install the module with an external smart card reader, check the
cable for signs of tampering. If evidence of tampering is present, do not use and
request a new cable.
nShield® 5s Installation Guide 9 of 37

4.3. Fitting a module bracket
Before installing a module in a PCI Express card slot, you may have to replace the
bracket if it is not the same height as the slot. Both full height and low profile brackets
are supplied with the module.
Do not touch the connector pins, or the exposed area of the module without taking
electrostatic discharge (ESD) precautions.
To fit the bracket to the module:
1. Remove the two screws from the solder side of the module.
2. Remove the incorrect bracket.
3. Fit the correct bracket to the component side of the module.
4. Insert the two screws into the solder side of the module to secure the bracket. Do
not over tighten the screws.
4.4. User Replaceable items
If the module has been removed so that a part can be replaced, follow these procedures
before installing the module. If no parts need replacing, proceed to Installing the module.
nShield® 5s Installation Guide 10 of 37

4.4.1. Replace the battery
Please follow battery disposal guidelines in the installation manual.
Required tools
•Small non-conductive tweezers
Required part
•Orderable part number: SOLOXC-REP-BATT (Replacement battery)
To remove and replace the battery:
1. Power off the system and while taking ESD precautions, remove the module.
2. Place the module on a flat surface.
3. Using the tweezers, gently remove the battery from the BT1 connector.
4. Observing the polarity, install the replacement battery in the BT1 connector.
5. Re-install the module into the PCIe slot.
nShield® 5s Installation Guide 11 of 37

5. Installing the module
1. Power off the system and while taking electrostatic discharge precautions, remove
the module from its packaging.
2. Open the computer case and locate an empty PCIe slot. If necessary, follow the
instructions that your computer manufacturer supplied.
You must only install your nShield nShield 5s module into a PCIe
slot. See the instructions that your computer manufacturer
supplied to correctly identify the slots on your computer.
Minimum requirement: 1 PCIe x4 slot
3. If there is a blanking plate across the opening to the outside of the computer, remove
it. Check that the opening is large enough to enable you to access the module back
panel.
4. Insert the contact edge of the module into the empty slot. Press the card firmly into
the connector to ensure that:
◦The contacts are fully inserted in the connector
◦The back panel is correctly aligned with the access slot in the chassis
5. Use the bracket screw or fixing clip to secure the module to the computer chassis.
6. Replace the computer case.
5.1. Fitting a smart card reader
Connect the smart card reader to the connector on the back panel of the module. A D-
type to mini-DIN adapter cable is supplied with the module.
5.2. After installing the module
If the Security World software has not already been installed, you must install the
Security World Software by following the instructions at Installing the software.
Although methods of installation vary from platform to platform, the Security World
Software should automatically detect the module on your computer and install the
drivers. You do not have to restart the system.
If this is not the first HSM installed in this host, the Security World software is already
installed and you can skip the instructions at Installing the software. However, you still
need to set up communication between the host and the newly installed module. The
module must either be in factory state or have been previously prepared for use on this
host. For more information, see Set up communication between host and module in the
nShield® 5s Installation Guide 12 of 37

User Guide for your module and operating system.
If the new module has been supplied from the factory it will already be
in factory state.
nShield® 5s Installation Guide 13 of 37

6. Before you install the software
Before you install the software, you should:
•Install the module. See Installing the module.
•Uninstall any older versions of Security World Software. See Uninstalling existing
software.
•If the nShield Remote Administration Client is installed on the machine, remove it.
You will also have to re-install it after you installed the new Security World software
version. See the nShield Remote Administration User Guide.
•Complete any other necessary preparatory tasks, as described in Preparatory tasks
before installing software.
6.1. Preparatory tasks before installing software
Perform any of the necessary preparatory tasks described in this section before installing
the Security World Software.
6.1.1. Windows
6.1.1.1. Power saving options
Adjust your computers power saving setting to prevent sleep mode.
You may also need to set power management properties of the HSM, once the Security
World Software is installed. See Installing the Security World Software on Windows for
more information.
6.1.1.2. Install Microsoft security updates
Make sure that you have installed the latest Microsoft security updates. Information
about Microsoft security updates is available from http://www.microsoft.com/security/.
6.1.1.3. Add %NFAST_HOME%\bin\ to the PATH environment variable
The default location for %NFAST_HOME%\bin\ is C:\Program Files\nCipher\nfast. Because of
the space in Program Files, nShield commands could fail if NFAST_HOME\bin\ is not in PATH.
If you cannot change PATH, you will have to enclose all file names and paths that use
variable between double quotation marks (" "). For example:
"%NFAST_HOME%\toolkits\pkcs11\cknfast.dll"
nShield® 5s Installation Guide 14 of 37

6.1.2. Linux
6.1.2.1. Install operating environment patches
Make sure that you have installed:
•kernel packages like gcc, kernel-headers, kernel-devel
•the latest recommended patches for your environment in general
See the documentation supplied with your operating environment for information.
6.1.2.2. Users and groups
The installer automatically creates the following group and users if they do not exist. If
you wish to create them manually, you should do so before running the installer. Create
the following, as required:
•The nfast user in the nfast group, using /opt/nfast as the home directory.
•If you are installing SNMP, the ncsnmpd user in the ncsnmpd group, using /opt/nfast as
the home directory.
•If you are installing the Remote Administration Service, the raserv user in the raserv
group, using /opt/nfast as the home directory.
6.1.2.3. Network configuration
The nShield nShield 5s appears to the host operating system as a network interface.
Communication with the HSM is performed over this interface using IPv6. The install
process automatically configures the nShield nShield 5s and any relevant operating
system network settings, with the HSM and host-software using link-local
communication.
After the installation process has been completed, the nShield nShield 5s network
interfaces should have a link-local IPv6 address. On Windows and Linux, this is assigned
automatically. On Linux, the installation process will also detect the following network
management services and create appropriate configuration files:
Network management
service
Configuration file path
NetworkManager /etc/network/interfaces.d/nshield
systemd.networkd /etc/systemd/network/nshield.network
These files instruct the network management service not to configure the the nShield
nShield® 5s Installation Guide 15 of 37

nShield 5s interfaces. They will be configured by the nShield host software. This covers all
of our supported distributions, and more. If your distribution is not using one of these
network management services, you will need to configure the interfaces to have a link-
local IPv6 address manually.
The following network configuration must be present for the host software and HSM to
function:
•The HSM’s network interface must be assigned a link-local IPv6 address
(https://tools.ietf.org/html/rfc4862).
•Multicast DNS must be possible for the host software to discover the services
running on the HSM (https://tools.ietf.org/html/rfc6762).
This requires inbound UDP packets on port 5353, to receive service advertisement
responses from the HSM.
•The following ports must be accessible on the HSM from the host to access
management and crypto services.
Outbound SSH traffic on TCP ports:
◦2201
◦2202
◦2203
◦2204
◦2206
6.1.3. All environments
6.1.3.1. Install Java with any necessary patches
The following versions of Java have been tested to work with, and are supported by, your
nShield Security World Software:
•Java7 (or Java 1.7x)
•Java8 (or Java 1.8x)
•Java11.
Entrust recommends that you ensure Java is installed before you install the Security
World Software. The Java executable must be on your system path.
If you can do so, please use the latest Java version currently supported by Entrust that is
compatible with your requirements. Java versions before those shown are no longer
supported. If you are maintaining older Java versions for legacy reasons, and need
nShield® 5s Installation Guide 16 of 37

compatibility with current nShield software, please contact Entrust nShield Support,
https://nshieldsupport.entrust.com.
To install Java, you may need installation packages specific to your operating system,
which may depend on other pre-installed packages to be able to work.
Suggested links from which you may download Java software as appropriate for your
operating system:
•http://www.oracle.com/technetwork/java/index.html
•http://www.oracle.com/technetwork/java/all-142825.html
You must have Java installed to use KeySafe.
6.1.3.2. Identify software components to be installed
Entrust supply standard component bundles that contain many of the necessary
components for your installation and, in addition, individual components for use with
supported applications. To be sure that all component dependencies are satisfied, you
can install either:
•All the software components supplied
•Only the software components you require
During the installation process, you are asked to choose which bundles and components
to install. Your choice depends on a number of considerations, including:
•The types of application that are to use the module
•The amount of disc space available for the installation
•Your company’s policy on installing software. For example, although it may be
simpler to choose all software components, your company may have a policy of not
installing any software that is not required.
On Windows, the nShield Hardware Support bundle and the nShield CoreÊTools bundle
are mandatory, and are always installed.
On Windows, the Windows device drivers component is installed as part of the
Hardware Support bundle. On Linux, the Kernel device drivers component is installed.
On Linux, you must install the hwsp component and the nshield5_net component.
The Core Tools bundle contains all the Security World Software command-line utilities,
including:
•generatekey
•Low level utilities
nShield® 5s Installation Guide 17 of 37

•Test programs
The Core Tools bundle includes the Tcl run time component that installs a run-time Tcl
installation within the nCipher directories. This is used by the tools for creating the
Security World and by KeySafe. This does not affect any other installation of Tcl on your
computer.
You need to install the Remote Administration Service component if you require remote
administration functionality. See Preparatory tasks before installing software and the
User Guide for your module and operating system for more about the Remote
Administration Service.
Always install all the nShield components you need in a single installation process to
avoid subsequent issues should you wish to uninstall. You should not, for example, install
the Remote Administration Service from the Security World installation media, then later
install the Remote Administration Client from the client installation media.
Ensure that you have identified any optional components that you require before you
install the Security World Software. See Software packages on the Security World
installation media for more about optional components.
6.2. Firewall settings
When setting up your firewall, you should ensure that the port settings are compatible
with the HSMs and allow access to the system components you are using. The following
table identifies the ports used by the nShield system components. All listed ports are the
default setting. Other ports may be defined during system configuration, according to
the requirements of your organization.
Component Default
Port
Protocol Use
Hardserver 9000 TCP Internal non-privileged connections
from Java applications including
KeySafe
Hardserver 9001 TCP Internal privileged connections from
Java applications including KeySafe
nShield® 5s Installation Guide 18 of 37

Component Default
Port
Protocol Use
Hardserver 9004 TCP Incoming impath connections from
other hardservers, for example:
* From a cooperating client to the
remote file system it is configured to
access * From a non-attended host
machine to an attended host
machine when using Remote
Operator
Remote Administration
Service
9005 TCP Incoming connections from Remote
Administration Clients
Audit Logging syslog 514 UDP If you plan to use the Audit Logging
facility with remote syslog or SIEM
applications, you need to allow
outgoing connections to the
configured UDP port
mDNS 5353 UDP Send out mDNS Service Discovery
requests and receive responses
If you are using an nShield Edge as a Remote Operator slot for an HSM located
elsewhere, you need to open port 9004. You may restrict the IP addresses to those you
expect to use this port. You can also restrict the IP addresses accepted by the hardserver
in the configuration file. See the User Guide for your module and operating system for
more about configuration files. Similarly, if you are setting up the Remote Administration
Service you need to open port 9005.
nShield® 5s Installation Guide 19 of 37

7. Installing the software
This chapter describes how to install the Security World Software on the host computer.
After you have installed the software, you must complete further Security World creation,
configuration and setup tasks before you can use your nShield environment to protect
and manage your keys. See the User Guide for your module and operating system for
more about creating a Security World and the appropriate card sets, and further
configuration or setup tasks.
If you are planning to use an nToken with a client, this should be physically installed in
the client before installing the Security World software, see nToken Installation Guide.
7.1. Installing the Security World Software on Windows
For information about configuring silent installations and uninstallations on Windows, see
the User Guide.
For a regular installation:
Installing Security World software on Windows via Remote Desktop
Connection can result in a brief loss of RDP connection. If this happens,
it will happen during the Status: part of the installation, towards the
end. When the session reconnects, the installation carries on until
completion.
1. Sign in as an Administrator or as a user with local administrator rights.
If the Found New Hardware Wizard appears and prompts you to
install drivers, cancel this notification, and continue to install the
Security World Software as normal. Drivers are installed during the
installation of the Security World Software.
2. Place the Security World Software installation media in the optical disc drive.
3. Launch setup.msi manually when prompted.
4. Follow the onscreen instructions.
5. Accept the license terms and select Next to continue.
6. Specify the installation directory and select Next to continue.
7. Select all the components required for installation.
By default, all components are selected. Use the drop-down menu to deselect the
components that you do not want to install. nShield Hardware Support and Core
Tools are necessary to install the Security World Software.
nShield® 5s Installation Guide 20 of 37
Table of contents
Other Entrust Control Unit manuals