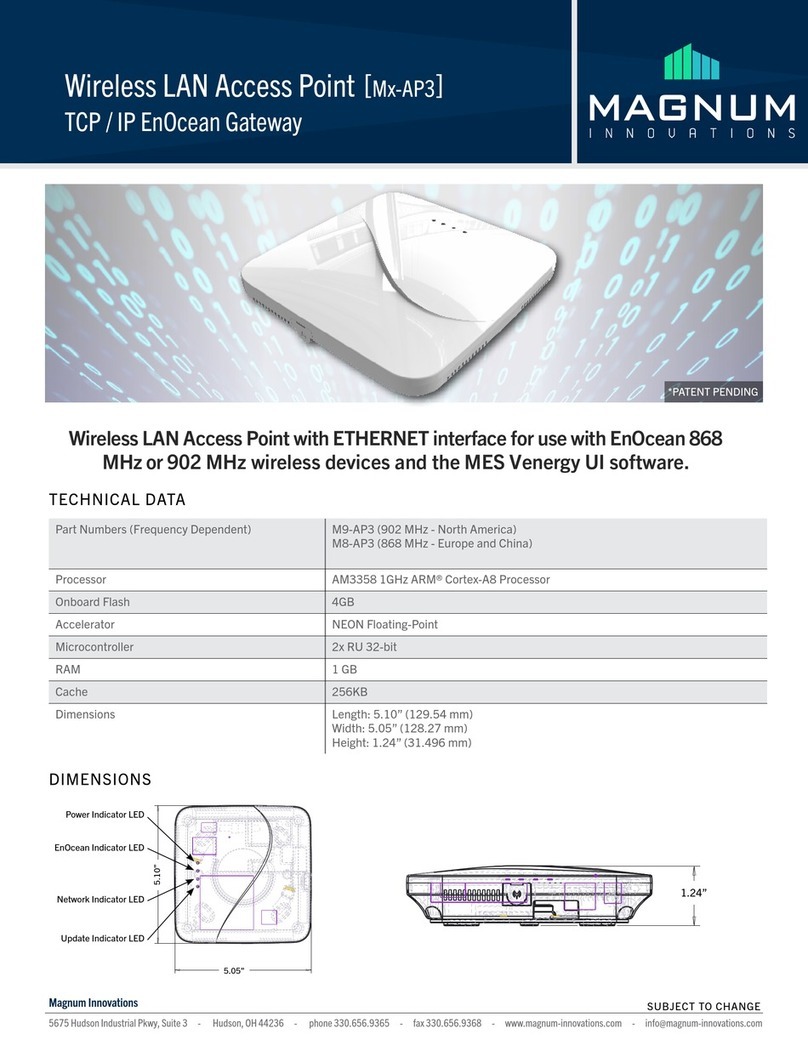
Ferimex FX-551 5Ghz User manual

802.11a/b/gAccessPoint
User’s Guide

-
FCC Certifications
This equipment has been tested and found to comply with the limits for a Class B digital device,
pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection
against harmful interference in a residential installation. This equipment generates, uses and can
radiate radio frequency energy and, if not installed and used in accordance with the instructions, may
cause harmful interference to radio communications. However, there is no guarantee that interference
will not occur in a particular installation. If this equipment does cause harmful interference to radio
or television reception, which can be determined by turning the equipment off and on, the user is
encouraged to try to correct the interference by one or more of the following measures:
Reorient or relocate the receiving antenna.
Increase the separation between the equipment and receiver.
Connect the equipment into an outlet on a circuit different from that to which the receiver is
connected.
Consult the dealer or an experienced radio/TV technician for help.
CAUTION:
Any changes or modifications not expressly approved by the grantee of this device could void the
user’s authority to operate the equipment.
This device complies with Part 15, subpart B, subpart C, and subpart E of the FCC rules. Operation
is subject to the following two conditions: (1) This device may not cause harmful interference, and
(2) This device must accept any interference received, including interference that may cause
undesired operation.
FCC RF Radiation Exposure Statement
This equipment complies with FCC RF radiation exposure limits set forth for an uncontrolled
environment. This equipment should be installed and operated with a minimum distance of 20cm
between the radiator and your body.
CE Mark
CE Approvals:
EN 300 328
EN 301 893
EN 301 489-1/-17
EN 60950-1

Table of Content
TUINTRODUCTIONUT ................................................................................................................................3
TUFeaturesUT .........................................................................................................................................3
TUApplicationUT ....................................................................................................................................3
TUParts Names and FunctionsUT .........................................................................................................4
TUHARDWARE CONNECTIONUT ...........................................................................................................7
TUABOUT THE OPERATION MODESUT ................................................................................................8
TU AP ModeUT ........................................................................................................................................8
TU Client Mode (Infrastructure)UT ......................................................................................................8
TU Client Mode (Ad-hoc)UT ...................................................................................................................8
TUBridge ModeUT ..................................................................................................................................9
TURepeaterUT.........................................................................................................................................9
TUWISP (Client Router) modeUT .........................................................................................................9
TUWISP + Universal modeUT .............................................................................................................10
TUCONFIGURATIONUT ...........................................................................................................................11
TULoginUT ............................................................................................................................................11
TUConfiguration via WebUT ...............................................................................................................11
TUWireless ModeUT .......................................................................................................................11
TUStatusUT ......................................................................................................................................35
TUTCP/IPUT ...................................................................................................................................37
TUOtherUT ......................................................................................................................................40

Introduction
This is an IEEE802.11a/b/g compliant 11 Mbps & 54 Mbps Ethernet wireless Access Point.
The wireless Access Point is equipped with five 10/100 M Auto-sensing Ethernet ports for
connecting to LAN and also for cascading to next wireless Access Point.
This Access Point provides 64/128bit WEP encryption, WPA and IEEE802.1x which ensures
a high level of security to protects users’ data and privacy. The MAC Address filter prevents
the unauthorized MAC Addresses from accessing your Wireless LAN. Your network security
is therefore double assured.
The web-based management utility is provided for easy configuration that your wireless
network connection is ensured to be always solid and hassle free.
Features
• Five LAN ports for Wireless AP cascade
• Support WPA-PSK and WPA2-PSK
• Support AP client mode
• Support data rate automatic fallback
• Automatic channel selection
• Client access control
• Support 802.1x/Radius client with, TKIP, AES and TKIP_AES encryption
• Support IAPP
• Adjustable Tx power, Tx rate, and SSID broadcast
• Allow WEP 64/128 bit
Web interface management
• Support System event log and statistics
• MAC filtering (For wireless only)
• Support wireless 802.11 SNMP management
• WatchDog timer to warm boot system
Application
Example 1

Example 2
Parts Names and Functions
1. Front Panel: (LED Indicators)

Appendix B - Specifications
-
LED Status
Indicator
Color Solid Flashing
1 Power Yellow Turns solid yellow when
the power is applied to
this device.
N/A.
2~6 LAN Yellow Turns solid Yellow when
the corresponding port is
connected to another
network device through
an Ethernet cable.
Receiving/
Sending data
7
WLAN Blue
Turns solid Blue when
the power is applied to
this device.
Receiving/
Sending data
Table 1: LED Indicators
2. Rear Panel: Connection Ports

Port/butto
n Functions
A (Factory)
RESET
Press for over 3 seconds to reboot this device.
Press for over 10 seconds to restore the factory
settings. Performing the Factory Reset will erase all
previously entered device settings.
B~F LAN ports Use standard LAN cables (RJ45 connectors) to connect
your PCs to these ports.
If required, any port can be connected to another
hub. Any LAN port will automatically function as an
"Uplink" port when necessary.
G 12V DC Connects the power adapter plug
Table 2: Connection Ports

Appendix B - Specifications
-
Hardware Connection
Note: Before you start the hardware connection, you are advised to find an appropriate
location to place the Access Point. Usually, the best place for an Access Point is at the center
of your wireless network, with line of sigh to all wireless stations. Also, the higher the antenna
is placed, the better the device can perform.
1. Connect to your local area network: connect a Ethernet cable to one of the Ethernet
port (LAN1~LAN5) of this wireless Access Point, and the other end to a hub, switch,
router, or another wireless access point.
2. Power on the device: connect the included AC power adapter to the wireless Access
Point’s power port and the other end to a wall outlet.
3. Configure your PC: Make sure your local PC(s) has wireless network adapter(s)
installed.

About the Operation Modes
This device provides four operational applications with AP, Bridge, Client (Ad-hoc), Client
(Infrastructure) and Repeater modes, which are mutually exclusive.
This device is shipped with configuration that is functional right out of the box. If you want to
change the settings in order to perform more advanced configuration or even change the mode
of operation, you can use the web-based utility provided by the manufacturer as described in
the following sections.
AP Mode
When acting as an access point, this device connects all the stations (PC/notebook with
wireless network adapter) to a wired network. All stations can have the Internet access if only
the Access Point has the Internet connection.
Client Mode (Infrastructure)
If set to Client (Infrastructure) mode, this device can work like a wireless station when it’s
connected to a computer so that the computer can send packets from wired end to wireless
interface.
Client Mode (Ad-hoc)
If set to the Client (Ad-hoc) mode, this device can work like a wireless station when it is
connected to a computer so that the computer can send packets from wired end to wireless
interface. You can share files and printers between wireless stations (PC and laptop with
wireless network adapter installed).

Appendix B - Specifications
-
Bridge Mode
You will be able to connect two wireless LANs together under the Bridge mode. This only
works with another wireless a/b/g Access Point. If enabled you must enter the MAC address of
that wireless a/b/g Access Point.
Repeater
You will be able to repeat the wireless signal of the root access point. When enabled you must
enter the MAC address of the root access point.
WISP (Client Router) mode
In WISP mode, the AP will behave just the same as the Client mode for wireless function.
However, router functions are added between the wireless WAN side and the Ethernet LAN
side. Therefore, the WISP subscriber can share the WISP connection without the need for
extra router.

WISP + Universal mode
In WISP + Universal mode, the AP can also send wireless signal to LAN side, i.e. the AP can
connect with the remote WISP AP and the indoor wireless device, and then provide IP sharing
capability all at the same time. However, the output power will be cut down while it is being
distributed to two wireless sides.

Appendix B - Specifications
-
Configuration
Login
1. Start your computer. Connect an Ethernet cable between your computer and the wireless
Access Point.
2. Make sure your wired station is set to the same subnet as the wireless Access Point, i.e.
192.168.1.254
3. Start your WEB browser. In the Address box, enter the following:
HTTP://192.168.1.254
4. Enter admin in the Username column when you are prompted the login screen. No
password is required for the default setting.
Configuration via Web
Wireless Mode
Select a wireless mode and then click the Setup button to enter its configuration page.

Wireless Mode
AP When acting as an access point, this device connects all the stations
(PC/notebook with wireless network adapter) to a wired network.
All stations can have the Internet access if only the Access Point
has the Internet connection.
Client If set to Client (Infrastructure) mode, this device can work like a
wireless station when it’s connected to a computer so that the
computer can send packets from wired end to wireless interface.
If set to the Client (Ad-hoc) mode, this device can work like a
wireless station when it is connected to a computer so that the
computer can send packets from wired end to wireless interface.
You can share files and printers between wireless stations (PC and
laptop with wireless network adapter installed).
Bridge The WDS (Wireless Distributed System) function lets this access
point act as a wireless LAN access point and repeater at the same
time. Users can use this feature to build up a large wireless network
in a large space like airports, hotels and schools …etc. This feature
is also useful when users want to bridge networks between
buildings where it is impossible to deploy network cable
connections between these buildings.
Repeater When set to Wireless Repeater mode, the Wireless Repeater is able
to talk to one remote access point within its range and retransmit its
signal.
WISP In WISP mode, the wireless AP function is basically the same as in
the client mode. Only the router function is added between the
wireless WAN side and the Ethernet LAN side. Therefore the
WISP subscriber can share the WISP connection without the need
of an extra router.

Appendix B - Specifications
-
UAP Mode
AP Mode Settings
Alias Name Display the name of this device.
Disable Wireless LAN
Interface Check the box to disable the Wireless LAN Interface, by so doing,
you won’t be able to make wireless connection with this Access
Point in the network you are located. In other words, this device
will not be visible by any wireless station.
Band You can choose one mode of the following you need.
2.4GHz (B): 802.11b supported rate only.
2.4GHz (G): 802.11g supported rate only.
2.4GHz (B+G): 802.11b supported rate and 802.11g supported
rate.
The default is 2.4GHz (B+G) mode.
SSID The SSID differentiates one WLAN from another, therefore, all
access points and all devices attempting to connect to a specific
WLAN must use the same SSID. It is case-sensitive and must not
exceed 32 characters. A device will not be permitted to join the
BSS unless it can provide the unique SSID. An SSID is also
referred to as a network name because essentially it is a name that
identifies a wireless network.
Channel Number Allow user to set the channel manually or automatically.
If set channel manually, just select the channel you want to
specify.
If “Auto” is selected, user can set the channel range to have
Wireless Access Point automatically survey and choose the
channel with best situation for communication.

The number of channels supported depends on the region of this
Access Point. All stations communicating with the Access Point
must use the same channel.
Advanced Settings
Fragment Threshold: Fragmentation mechanism is used for
improving the efficiency when high traffic flows along in the
wireless network. If your 802.11g Wireless LAN PC Card often
transmit large files in wireless network, you can enter new
Fragment Threshold value to split the packet. The value can be set
from 256 to 2346. The default value is 2346.
RTS Threshold: RTS Threshold is a mechanism implemented to
prevent the “Hidden Node” problem. “Hidden Node” is a
situation in which two stations are within range of the same
Access Point, but are not within range of each other. Therefore,
they are hidden nodes for each other. When a station starts data
transmission with the Access Point, it might not notice that the
other station is already using the wireless medium. When these
two stations send data at the same time, they might collide when
arriving simultaneously at the Access Point. The collision will
most certainly result in a loss of messages for both stations.
Thus, the RTS Threshold mechanism provides a solution to
prevent data collisions. When you enable RTS Threshold on a
suspect “hidden station”, this station and its Access Point will use
a Request to Send (RTS). The station will send an RTS to the
Access Point, informing that it is going to transmit the data. Upon
receipt, the Access Point will respond with a CTS message to all
station within its range to notify all other stations to defer
transmission. It will also confirm the requestor station that the
Access Point has reserved it for the time-frame of the requested
transmission.
If the “Hidden Node” problem is an issue, please specify the
packet size. UThe RTS mechanism will be activated if the data size
exceeds the value you set.U. The default value is 2347.
Warnin
g
:Enablin
g
RTS Threshold will cause redundant

Appendix B - Specifications
-
network overhead that could negatively affect the throughput
performance instead of providing a remedy.
This value should remain at its default setting of 2347. Should you
encounter inconsistent data flow, only minor modifications of this value
are recommended.
Beacon Interval: Beacon Interval is the amount of time between
beacon transmissions. Before a station enters power save mode,
the station needs the beacon interval to know when to wake up to
receive the beacon (and learn whether there are buffered frames at
the access point).
Inactivity Time:
Data Rate: By default, the unit adaptively selects the highest
possible rate for transmission. Select the basic rates to be used
among the following options: Auto, 1, 2, 5.5, 11or 54 Mbps. For
most networks the default setting is Auto which is the best choice.
When Auto is enabled the transmission rate will select the optimal
rate. If obstacles or interference are present, the system will
automatically fall back to a lower rate.
Preamble Type: A preamble is a signal used in wireless
environment to synchronize the transmitting timing including
Synchronization and Start frame delimiter. (Note: If you want to
change the Preamble type into Long or Short, please check the
setting of AP)
Broadcast SSID: Enable: This wireless AP will broadcast its SSID to
stations.
Disable: This wireless AP will not broadcast its SSID to stations. If stations want
to connect to this wireless AP, this AP’s SSID should be known in advance to
make a connection.
IAPP: IAPP (Inter Access Point Protocol) is designed for the
enforcement of unique association throughout a ESS (Extended
Service Set) and a secure exchange of station’s security context
between current access point (AP) and new AP during handoff
period.
802.11g Protection: The 802.11g standard includes a protection
mechanism to ensure mixed 802.11b and 802.11g operations. If
there is no such kind of mechanism exists, the two kinds of
standards may mutually interfere and decrease network’s
performance.
Tx Power level: Select the Tx Power Level from the pull-down
men including Highest (~16dBm), High (~15dBm), Middle
(~13dBm),Low (~10dBm) and Lowest (~3dBm).
Enable WatchDog: Check to enable the WatchDog function.
Watch Interval: Set the Watch Interval in from 1to 60 minutes.
Watch Host: Set the Watch Host in this column.
Ack Timeout: When a packet is sent out from one wireless station
to the other, it will wait for an Acknowledgement frame from the
remote station. If the ACK is NOT received within that timeout

period then the packet will be re-transmitted resulting in reduced
throughput. If the ACK setting is too high then throughput will be
lost due to waiting for the ACK Window to timeout on lost
packets. By having the ability to adjust the ACK setting we can
effectively optimize the throughput over long distance links. This
is especially true for 802.11a and 802.11g networks.
Set Default: Click to restore the current settings to the default
ones.
Apply Changes: Click to save and apply the current setting.
Reset: Click to clear and reset the current settings.
Security Click the Setup button to enter the Security setup page.
Authentication: Select an Authentication from the pull-down list
including Open system or Shared Key,Open System, Open
System with 802.1x,Shared Key,WPA-RADIUS,WPA-PSK,
WPA2-RADIUS and WPA2-PSK.
Encryption: Select the type of encryption from the pull-down list
either non or WEP.
Use 802.1x Authentication: Select 64bit or 128bit Encryption.
Select HEX if you are using hexadecimal numbers (0-9, or A-F).
Select ASCII if you are using ASCII characters (case-sensitive).
Ten hexadecimal digits or five ASCII characters are needed if
64-bit WEP is used; 26 hexadecimal digits or 13 ASCII
characters are needed if 128-bit WEP is used.
Pre-Shared Key Format: Select Passphrase or Hex (64
characters)
Pre-Shared Key: Pre-Shared-Key serves as a password. Users
may key in a 8 to 63 characters string to set the password or leave
it blank, in which the 802.1x Authentication will be activated.
Make sure the same password is used on client’s end.
There are two formats for choice to set the Pre-shared key, i.e.
Passphrase and Hex. If Hex is selected, users will have to enter a
64 characters string. For easier configuration, the Passphrase (at
least 8 characters) format is recommended.
Group Key Life Time: Enter the number of seconds that will
ela
p
se before the
g
rou
p
ke
y
chan
g
e automaticall
y
. The default is

Appendix B - Specifications
-
86400 seconds.
Enable Pre-Authentication: The two most important features
beyond WPA to become standardized through 802.11i/WPA2 are:
pre-authentication, which enables secure fast roaming without
noticeable signal latency.
Preauthentication provides a way to establish a PMK security
association before a client associates. The advantage is that the
client reduces the time that it’s disconnected to the network.
Authentication RADIUS Server: RADIUS is an authentication,
authorization and accounting client-server protocol. The client is a
Network Access Server that desires to authenticate its links. The
server is a server that has access to a user database with
authentication information.
Port: Enter the RADIUS Server’s port number provided by your
ISP. The default is 1812.
IP Address: Enter the RADIUS Server’s IP Address provided by
your ISP.
Password: Enter the password that the AP shares with the
RADIUS Server.
Enable Accounting: Check to enable this function.
Accounting RADIUS Server: Port: Enter the RADIUS Server’s
port number provided by your ISP. The default is 1812.
IP Address: Enter the RADIUS Server’s IP Address provided by
your ISP.
Password: Enter the password that the AP shares with the
RADIUS Server.
Apply Changes: Click to save and apply the current settings.
Reset: Click to clear and reset the current settings.
Access Control Click to enter the Access Control screen.
Wireless Access Control Mode: Select the Access Control Mode

from the pull-down menu.
• Disable: Select to disable Wireless Access Control Mode.
• Allow Listed: Only the stations shown in the table can
associate with the AP.
Deny Listed: Stations shown in the table won’t be able to
associate with the AP.
MAC Address: Enter the MAC Address of a station that is
allowed to access this Access Point.
Comment: You may enter up to 20 characters as a remark to the
previous MAC Address.
Apply Changes: Press to save the new settings on the screen.
Reset: Press to discard the data you have entered since last time
you press Apply Change.
Delete Selected: To delete clients from access to this Access
Point, you may firstly check the Select checkbox next to the MAC
address and Comments, and press Delete Selected.
Delete All: To delete all the clients from access to this Access
Point, just press Delete All without selecting the checkbox.
Reset: If you have made any selection, press Reset will clear all
the select mark.
Apply Changes Click to save the current settings.
Reset Click to reset this page.
UClient Mode

Appendix B - Specifications
-
Client Mode Settings
Alias Name Display the name of this device.
Disable Wireless LAN
Interface Check the box to disable the Wireless LAN Interface, by so doing,
you won’t be able to make wireless connection with this Access
Point in the network you are located. In other words, this device
will not be visible by any wireless station.
Band You can choose one mode of the following you need.
2.4GHz (B): 802.11b supported rate only.
2.4GHz (G): 802.11g supported rate only.
2.4GHz (B+G): 802.11b supported rate and 802.11g supported
rate.
The default is 2.4GHz (B+G) mode.
Network type Select a network type from the pull-down menu.
SSID The SSID differentiates one WLAN from another, therefore, all
access points and all devices attempting to connect to a specific
WLAN must use the same SSID. It is case-sensitive and must not
exceed 32 characters. A device will not be permitted to join the
BSS unless it can provide the unique SSID. An SSID is also
referred to as a network name because essentially it is a name that
identifies a wireless network.
Channel Number Allow user to set the channel manually or automatically.
If set channel manually, just select the channel you want to
specify.
If “Auto” is selected, user can set the channel range to have
Wireless Access Point automatically survey and choose the
channel with best situation for communication.
The number of channels supported depends on the region of this
Access Point. All stations communicating with the Access Point
must use the same channel.
Enable MAC Clone
(Single Ethernet
Client)
If your ISP restricts service to PCs only, use the MAC Clone
feature to copy a PC Media
Access Control (MAC) address to your router. This procedure will
cause the router to appear as a single PC, while allowing online
access to multiple computers on your network.
Security Click the Setup button to enter the Security configuration page.
Table of contents
Other Ferimex Wireless Access Point manuals
Popular Wireless Access Point manuals by other brands
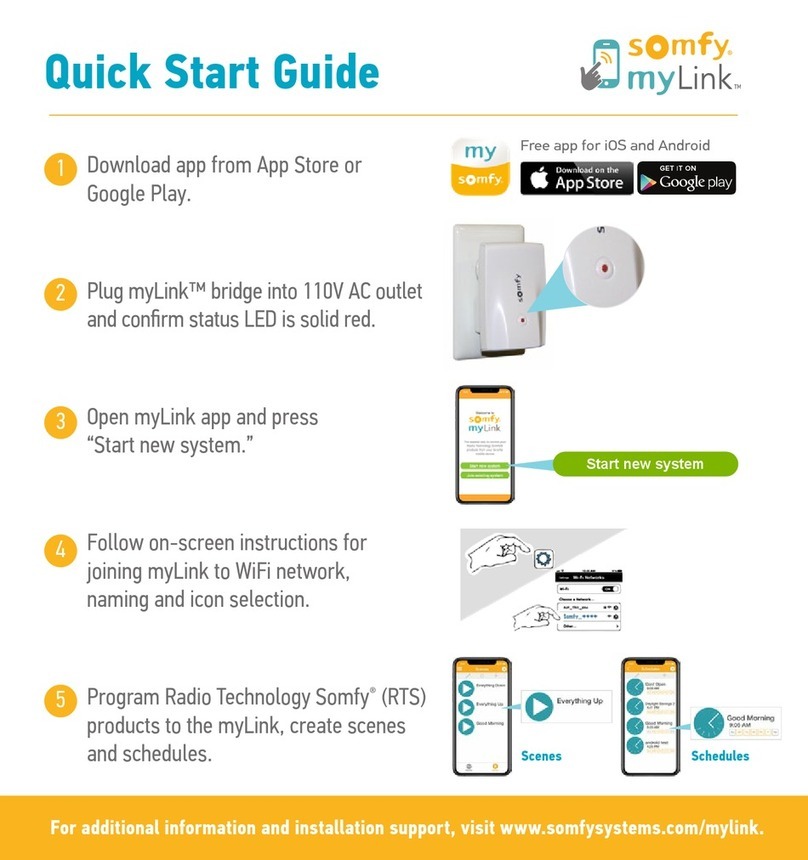
SOMFY
SOMFY myLink quick start guide

Edge-Core
Edge-Core ECWO5211-L Quick installation guide

LG-Ericsson
LG-Ericsson EARU 1211 user manual

ZyXEL Communications
ZyXEL Communications NWA-3160 user guide

ZyXEL Communications
ZyXEL Communications ZyXEL ZyAIR B-1000 Specifications

araknis
araknis AN-100-AP-I-N product manual