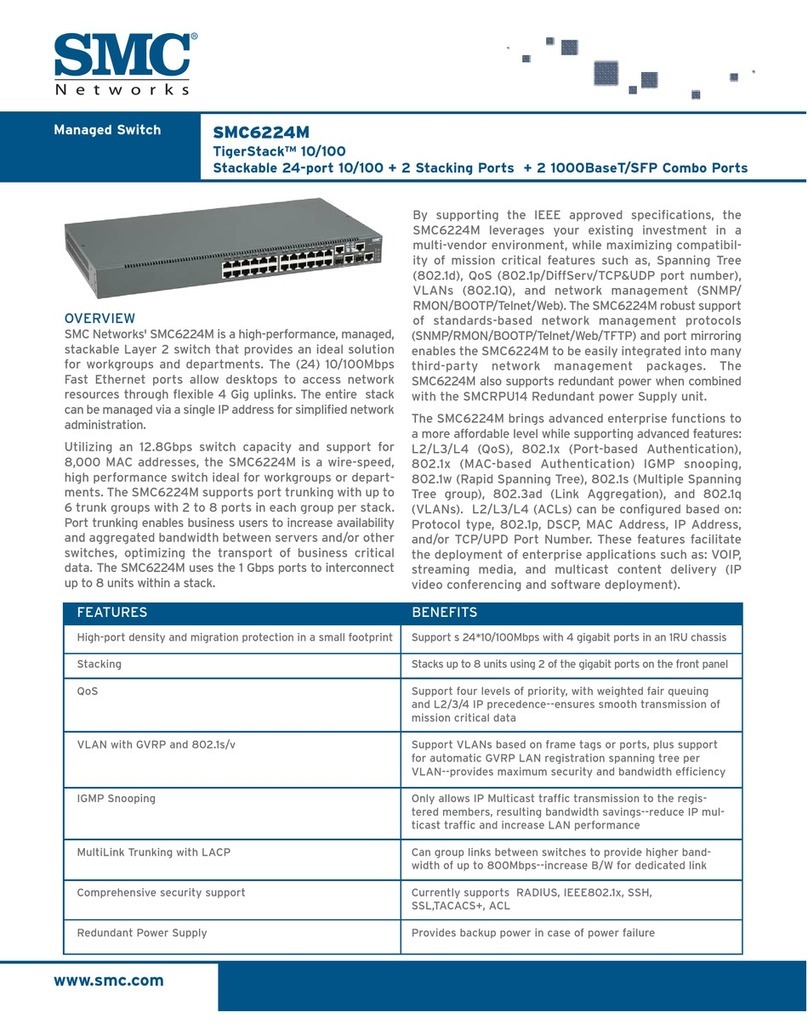
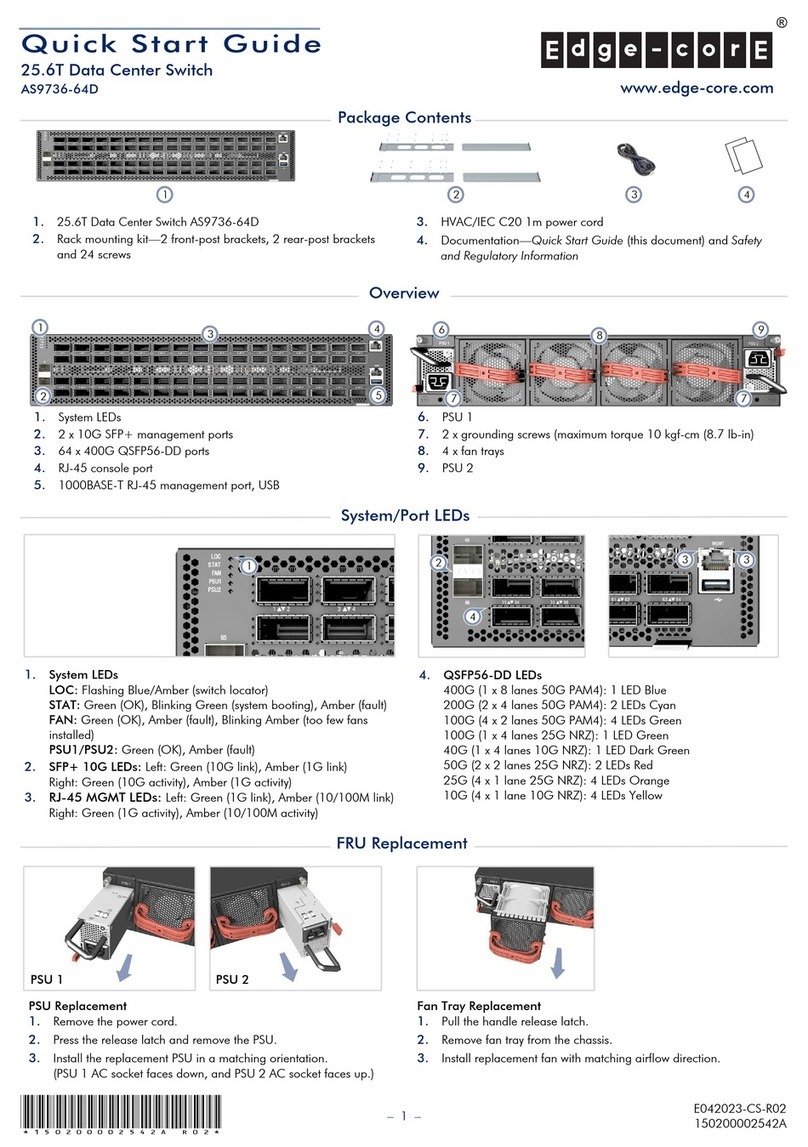
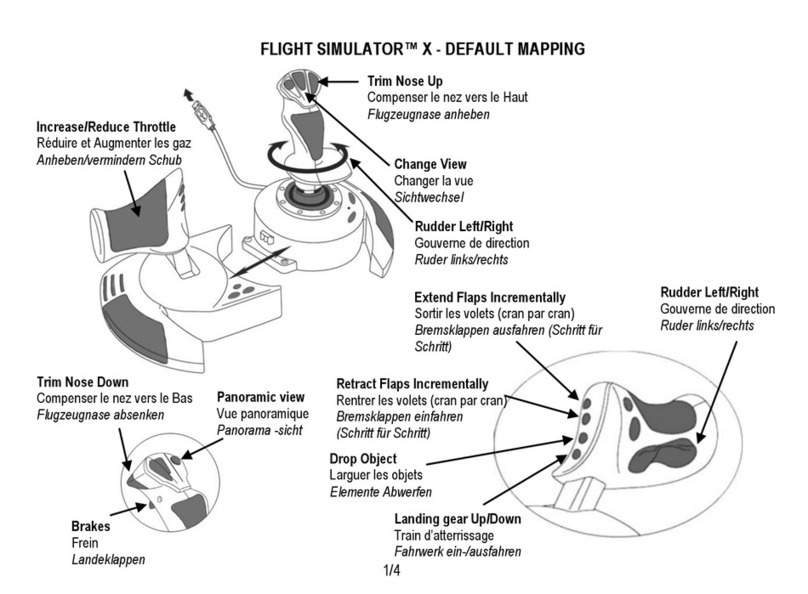
December 2000 ix
FEATURE LIST ......................................................................................................................................8-3
SHOWING SYSTEM DEFAULTS ...............................................................................................................8-6
ACCESS AND MANAGEMENT FEATURES .......................................................................................................8-7
SECURE SHELL (SSH) .........................................................................................................................8-7
MANAGEMENT INTERFACES ..................................................................................................................8-8
MULTIPLE LEVELS OF ACCESS CONTROL ............................................................................................8-10
ACCESS CONTROL LISTS (ACLS) .......................................................................................................8-11
DYNAMIC CONFIGURATION ..................................................................................................................8-11
SOFT REBOOT ...................................................................................................................................8-11
SCHEDULED SYSTEM RELOAD ............................................................................................................8-11
TELNET ..............................................................................................................................................8-11
TRIVIAL FILE TRANSFER PROTOCOL (TFTP) .......................................................................................8-11
SIMPLE NETWORK TIME PROTOCOL (SNTP) .......................................................................................8-12
DOMAIN NAME SERVER (DNS) RESOLVER ..........................................................................................8-12
SNMPV2CSUPPORT .........................................................................................................................8-12
REMOTE MONITORING (RMON) STATISTICS .......................................................................................8-13
SYSLOG LOGGING ..............................................................................................................................8-13
PING AND TRACEROUTE FACILITIES ....................................................................................................8-13
PORT MIRRORING ..............................................................................................................................8-14
IRONCLAD QUALITY OF SERVICE (QOS) ....................................................................................................8-14
IP TYPE OF SERVICE (TOS) MAPPING ................................................................................................8-14
SELECTABLE QUEUING METHOD .........................................................................................................8-14
CONFIGURABLE BANDWIDTH PERCENTAGES ........................................................................................8-14
802.1QPRIORITY MAPPING ................................................................................................................8-15
QUEUE ASSIGNMENT BY TRAFFIC TYPE ..............................................................................................8-15
LAYER 2 SWITCHING FEATURES ................................................................................................................8-15
MAC SWITCHING ...............................................................................................................................8-15
STATIC MAC ENTRIES .......................................................................................................................8-15
STANDARD SPANNING TREE PROTOCOL (STP) ...................................................................................8-16
IRONSPAN STP ENHANCEMENTS ........................................................................................................8-16
TRUNK GROUPS .................................................................................................................................8-16
PORT-BASED VIRTUAL LANS(VLANS) ...............................................................................................8-17
VLAN TAGGING .................................................................................................................................8-17
MAC FILTERS ....................................................................................................................................8-17
ADDRESS-LOCK FILTERS ....................................................................................................................8-17
DYNAMIC HOST CONFIGURATION PROTOCOL (DHCP) ASSIST .............................................................8-18
IP MULTICAST CONTAINMENT .............................................................................................................8-18
LAYER 3 SWITCHING FEATURES ................................................................................................................8-18
PROTOCOL-BASED VIRTUAL LANS(VLANS) .......................................................................................8-18
IP ROUTER ACCELERATION ................................................................................................................8-19
IPX ROUTER ACCELERATION ..............................................................................................................8-20
IP AND IPX ROUTER ACCELERATION POLICIES ....................................................................................8-20
LAYER 3 ROUTING FEATURES ...................................................................................................................8-20
MULTI-NETTING ..................................................................................................................................8-20
MULTIPLE IP SUB-NETS PER INTERFACE .............................................................................................8-21
MULTIPLE IPX FRAME TYPE SUPPORT PER INTERFACE .......................................................................8-21