NETGEAR FVX538v1 - ProSafe VPN Firewall Dual WAN User manual
Other NETGEAR Network Router manuals
NETGEAR
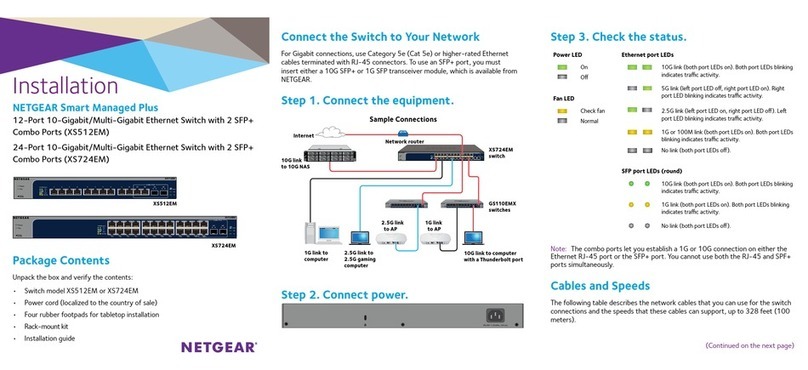
NETGEAR XS512EM User manual

NETGEAR
NETGEAR FS102 User manual
NETGEAR
NETGEAR FS518T FS518T FS518T User manual

NETGEAR
NETGEAR Orbi User manual

NETGEAR
NETGEAR Orbi RBW30 User manual

NETGEAR
NETGEAR WGE101 User manual
NETGEAR
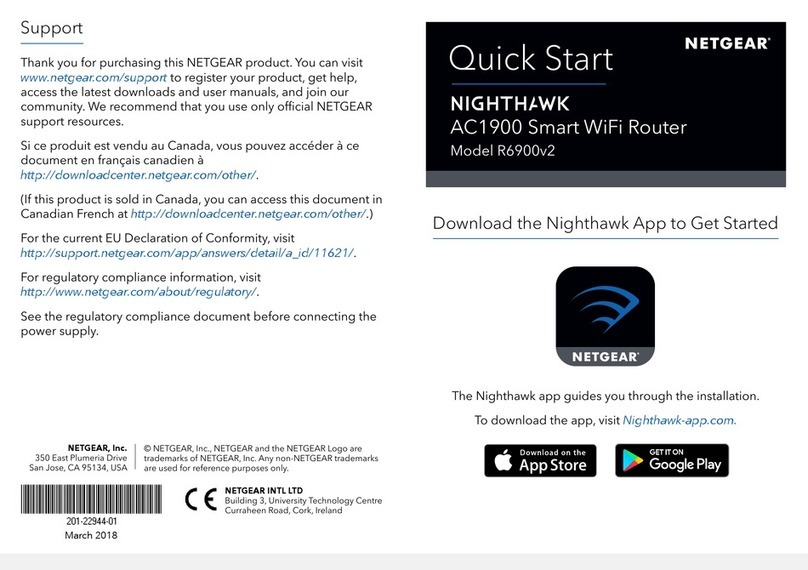
NETGEAR R6900v2 User manual

NETGEAR
NETGEAR RT338 User manual

NETGEAR
NETGEAR C3000v2 User manual

NETGEAR
NETGEAR AC1000 User manual

NETGEAR
NETGEAR C6250 User manual

NETGEAR
NETGEAR RH348 User manual
NETGEAR
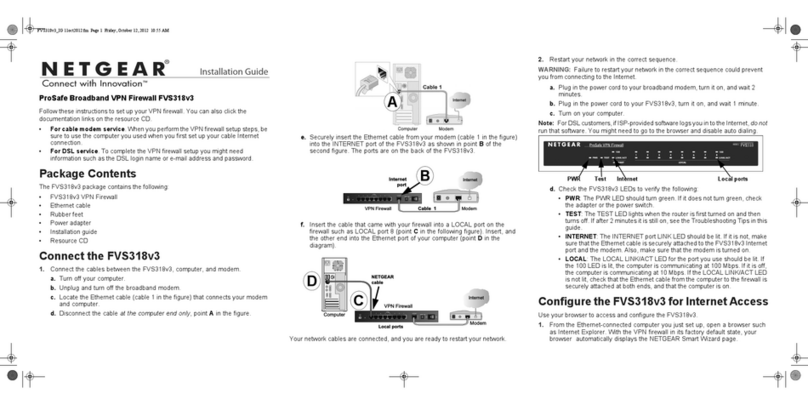
NETGEAR ProSafe FVS318v3 User manual

NETGEAR
NETGEAR Nighthawk R7000P User manual

NETGEAR
NETGEAR Orbi RBR20 User manual

NETGEAR
NETGEAR D8500 User manual

NETGEAR
NETGEAR MBR1515 User manual

NETGEAR
NETGEAR R6200v2 User manual
NETGEAR
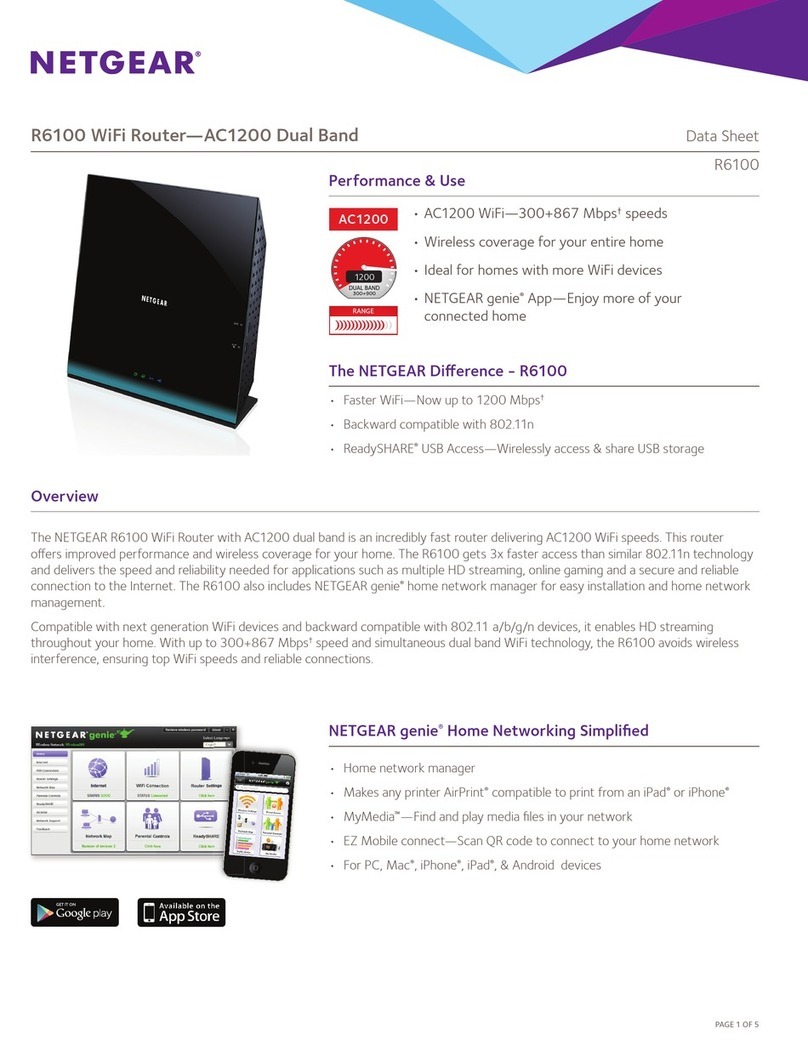
NETGEAR R6100 User manual

NETGEAR
NETGEAR WNR2000v2 - Wireless- N 300 Router User manual