TAPKO MECip-Sec Technical specifications

MECip
SECURE
MECip-Sec
KNX IP Secure Router
Technical & Application Description

MECip
SECURE
- 2 -
This document is property of the company named at the last page.
Without written approval, it may not be reproduced or commercialized,
distributed or presented to other individuals for commercial purpose.
Details and information contained within may be subject to change
without notice. For the accuracy of the document no warranty is given.
All rights reserved.

MECip
SECURE
- 3 -
Content
1Product Description 5
1.1 Front Panel 6
1.2 LED Indication 7
1.3 LED Indication of Special Functions 8
1.4 Commissioning 9
1.5 Secure Commissioning 10
1.6 Important Notes 11
1.6.1 Installation and Commissioning 11
1.6.2 Mounting and Safety 11
1.6.3 Maintenance 11
1.7 Safekeeping of Device Certificate 12
1.8 Feature Summary 13
2KNXnet/IP 14
2.1 IP Secure Tunneling 14
2.2 IP Secure Routing 14
2.3 IP Firmware Update 14
3KNX Secure 15
4Operational Description 16
4.1 IP Secure Router Application 16
4.2 IP Network 17
4.3 KNX Network Installation 18
4.4 Adding Device Certificate 19
4.5 Programming 21
4.5.1 Programming of Individual Address (and Application) 21
4.5.2 IP Configuration 22
4.6 Special Functions 24
4.6.1 Manual Function 24
4.6.2 Factory Reset 24
4.6.3 IP Firmware Update Request 25

MECip
SECURE
- 4 -
5ETS Database 26
5.1 General 26
5.2 Main Line (IP) 27
5.3 Subline (KNX TP) 28
5.4 IP (Secure) Tunneling Address Assignment 30
6Web Front-end 31
6.1 Protection of the MECip-Sec Web Front-end 31
6.2 Accessing the MECip-Sec Web Front-end 32
6.2.1 via Windows Explorer 32
6.2.2 via IP Address 33
6.2.3 via MAC Address 34
6.3 Device Info 35
6.4 KNX 36
6.5 IP Firmware Update 38
7Glossary 40
8Technical 43
8.1 State of Delivery 43
8.2 Datasheet 44
8.3 Drawings 45
9Legal Notice 46
10 FAQ 47

Product Description
MECip
SECURE
- 5 -
1Product Description
MECip-Sec, the secured version of MECip, is a KNX IP Secure Router supporting both KNX
Secure mechanisms, KNX IP Secure and KNX Data Secure. It provides a bi-directional data
connection between KNXnet/IP main line and KNX TP subline, to interconnect TP lines or
areas via an IP (Secure) Backbone. The Device Certificate utilization enables the usage of
Security functions “Secure Commissioning”, “Secure Tunneling” and “IP Backbone Security”.
MECip-Sec can also work as a KNX IP Secure Interface for connecting KNX IP devices, a PC, or
an Ethernet network to KNX TP. It establishes access to bus devices for commissioning,
address assignment, setting parameters, visualization, protocolling, and diagnostics. With the
ETS (or compatible commissioning tool) MECip-Sec works as the KNX programming interface.
Connecting a personal computer to KNX TP can be done directly and via Ethernet. Four
tunneling channels are available for IP (Secure) Tunneling. For every channel, an Individual
Address (plus Security password) can be set.
MECip-Sec also features a comfortable web front-end for watching the busload history, to
remotely control functions of MECip-Sec and to update its firmware via IP. With using this
web front-end, it´s easy to identify MECip-Sec in an installation by remotely switching on the
Programming LED. For reasons of protection, the web-frontend can be deactivated
completely or be set to only allow showing actual settings and operational data.
MECip-Sec is suitable for the Extended Frame format and has no KNX communication objects
for itself. Long telegrams are supported with up to 240 bytes APDU length. Filtering of
telegrams can be configured for both Physical Telegrams and Group Telegrams. Operational
modes, line states, telegram traffic, and filter states are shown at the duo-LED display.
Telegram repetition (on TP side) is also configurable. For bus traffic reduction, special
repetition/confirmation settings are provided.
It is possible to set programming of MECip-Sec and main line devices via the subline to
inactive. To be more exact, the sub-to-main transmission of telegrams for configuring
purpose can be switched off. This function can avoid unwanted access to devices (and their
configurations) from a subline (that may be located outside of a building).
The configurable Manual Function for short-time filter switch-off can ease commissioning
and troubleshooting. For example, “transmit all group telegrams” can be activated by a single
on-device button press. After the pre-set time period, MECip-Sec then switches automatically
back to normal operation.
Product Description
MECip
SECURE
- 6 -
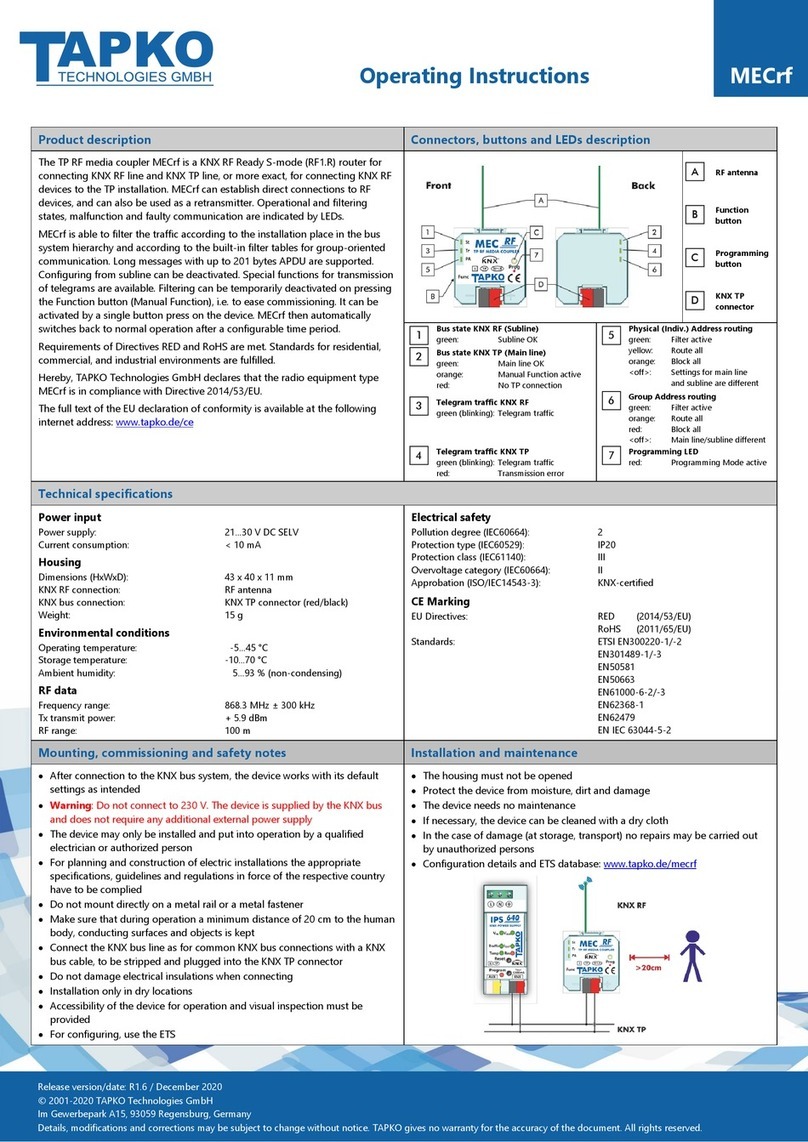
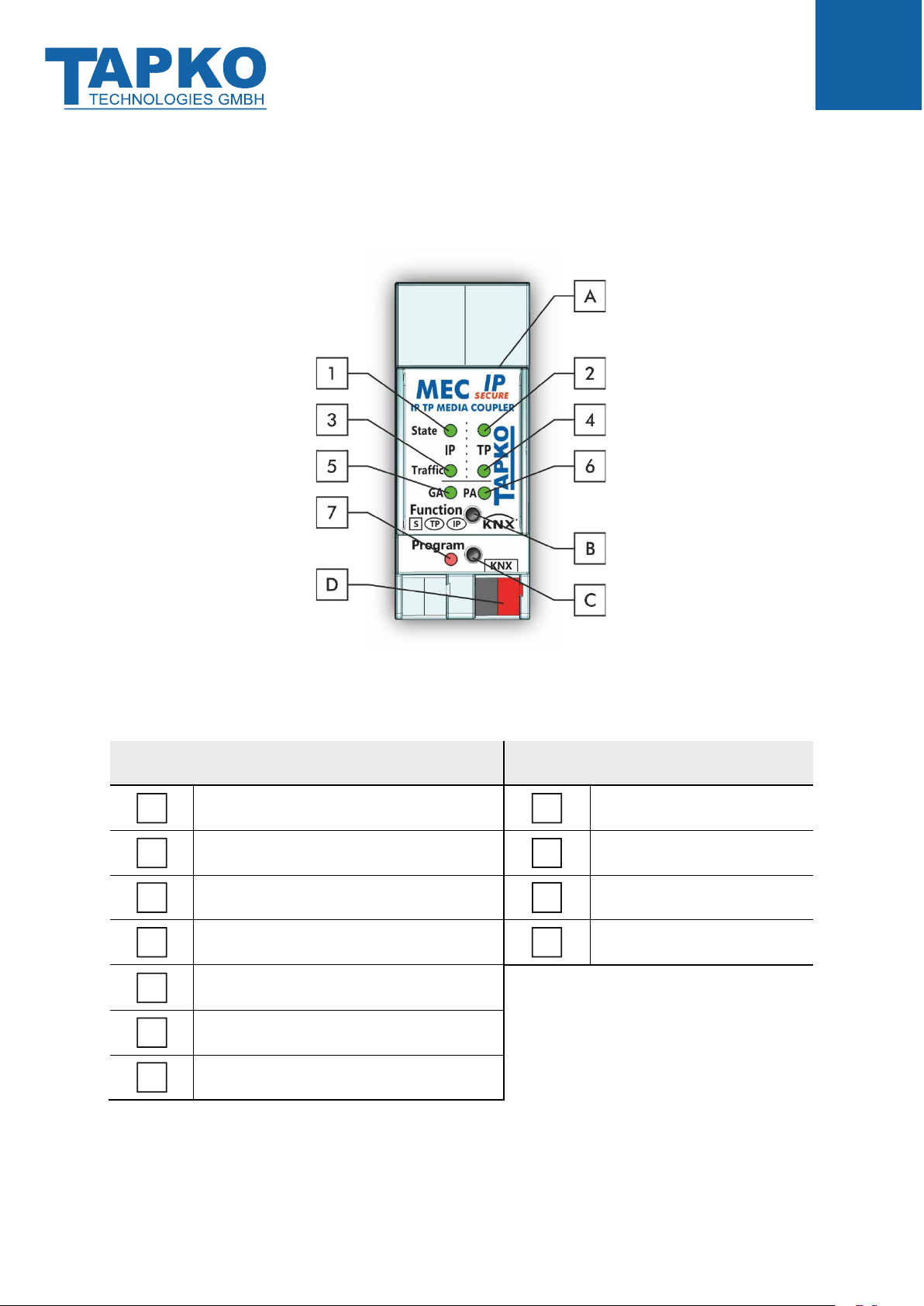
1.1 Front Panel
Figure 1: Front View
Table 1: Front Panel Elements
LEDs
Buttons / Connectors
State IP (Main line)
Ethernet Connector
Bus State KNX TP (Subline)
Function Button
Telegram Traffic IP (Main line)
Programming Button
Telegram Traffic KNX TP (Subline)
KNX TP Connector
Group Address Routing*
Individual (Physical) Address Routing
Programming LED
*only group telegrams with main groups 0…13
1
A
2
B
3
C
4
D
5
6
7

Product Description
MECip
SECURE
- 7 -
1.2 LED Indication
Following table gives a general description of the LED display indication intended for normal
operation. Constellations of LED lighting during active special functions are further described
in next chapter.
Table 2: Normal LED Display
Number
LED
Color
Explanation / Range
State IP
(Main line)
green
IP line OK (connection established)
orange
Manual Function active
< off >
No IP connection
Bus State KNX TP
(Subline)
green
Subline OK
< off >
Subline not connected
Telegram Traffic IP
(Main line)
blinking green
Telegram traffic extent indicated by blinking
< off >
No telegram traffic
Telegram Traffic
KNX TP (Subline)
blinking green
Telegram traffic extent indicated by blinking
blinking red
Transmission error (BUSY, NACK, missing
IACK)
< off >
No telegram traffic
Group Address
Routing
green
Filter table active
orange
Route all
red
Block all
< off >
Routing of Group Telegrams is different
on main line and subline
Individual
(Physical) Address
Routing
green
Filtering active
orange
Route all
red
Block all
< off >
Routing of Physical telegrams is different
on main line and subline
Programming LED
red
Programming Mode active
blinking red
No IP connection
< off >
Programming Mode not active
1
2
3
4
5
6
7
Product Description
MECip
SECURE
- 8 -
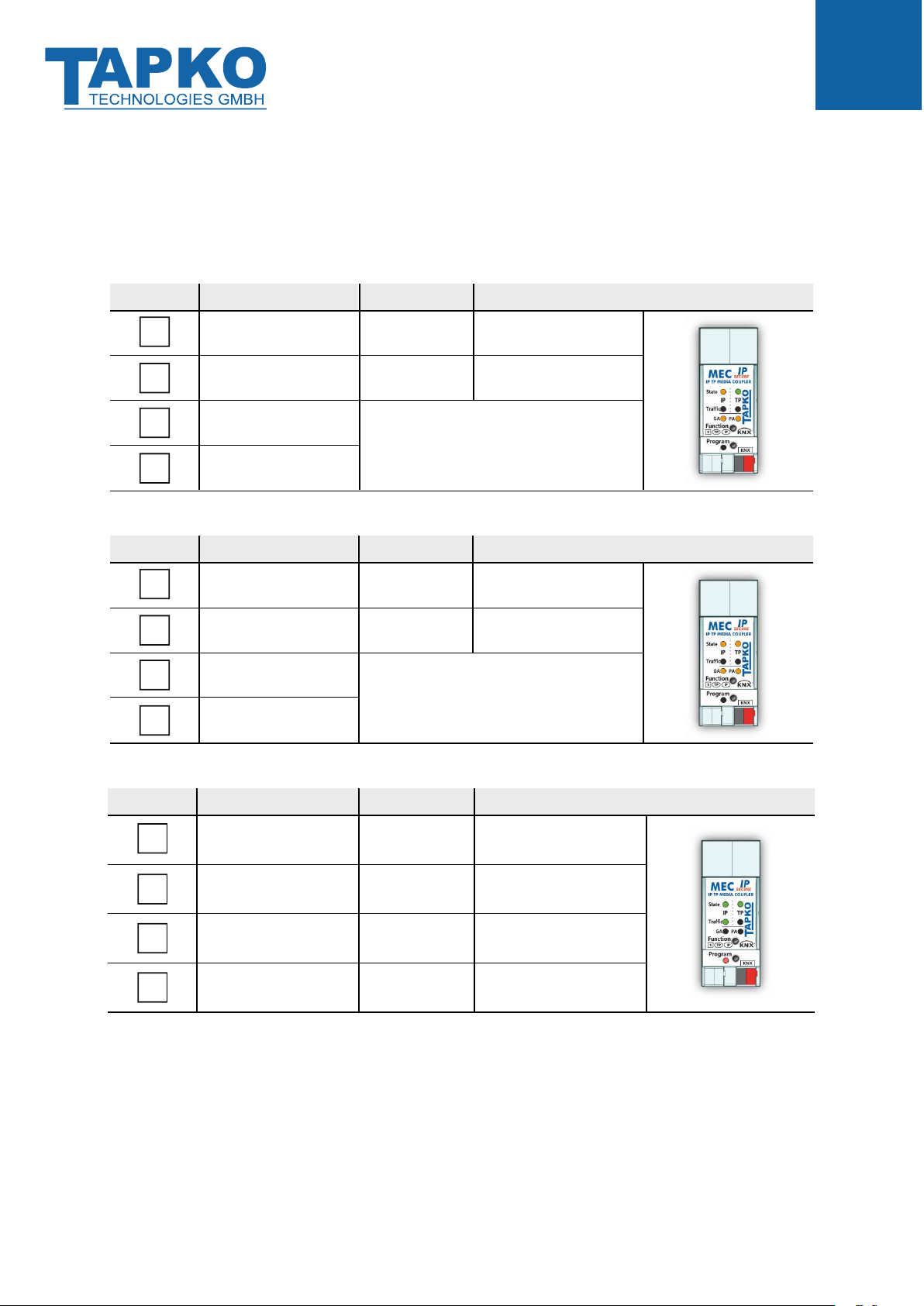
1.3 LED Indication of Special Functions
During an active special function, only LEDs described here are lighting. Other LEDs are off.
Table 3: LED Status Display for Manual Function
Number
LED
Color
Comment
State IP
orange
lights red if not
connected
Bus State KNX TP
green
Group Address
Routing
green:
orange:
red:
filter
route all
block all
Individual Address
Routing
Table 4: LED Status Display for Factory Reset after first Function Button Press
Number
LED
Color
Comment
State IP
orange
lights red if not
connected
Bus State KNX TP
orange
Group Address
Routing
green:
orange:
red:
filter
route all
block all
Individual Address
Routing
Table 5: LED Status Display for Firmware Update
Number
LED
Color
Comment
State IP
green
blinking, then lighting
Bus State KNX TP
blinking green
Telegram Traffic IP
green
Programming LED
red
1
2
5
6
1
2
5
6
1
2
3
7
Product Description
MECip
SECURE
- 9 -
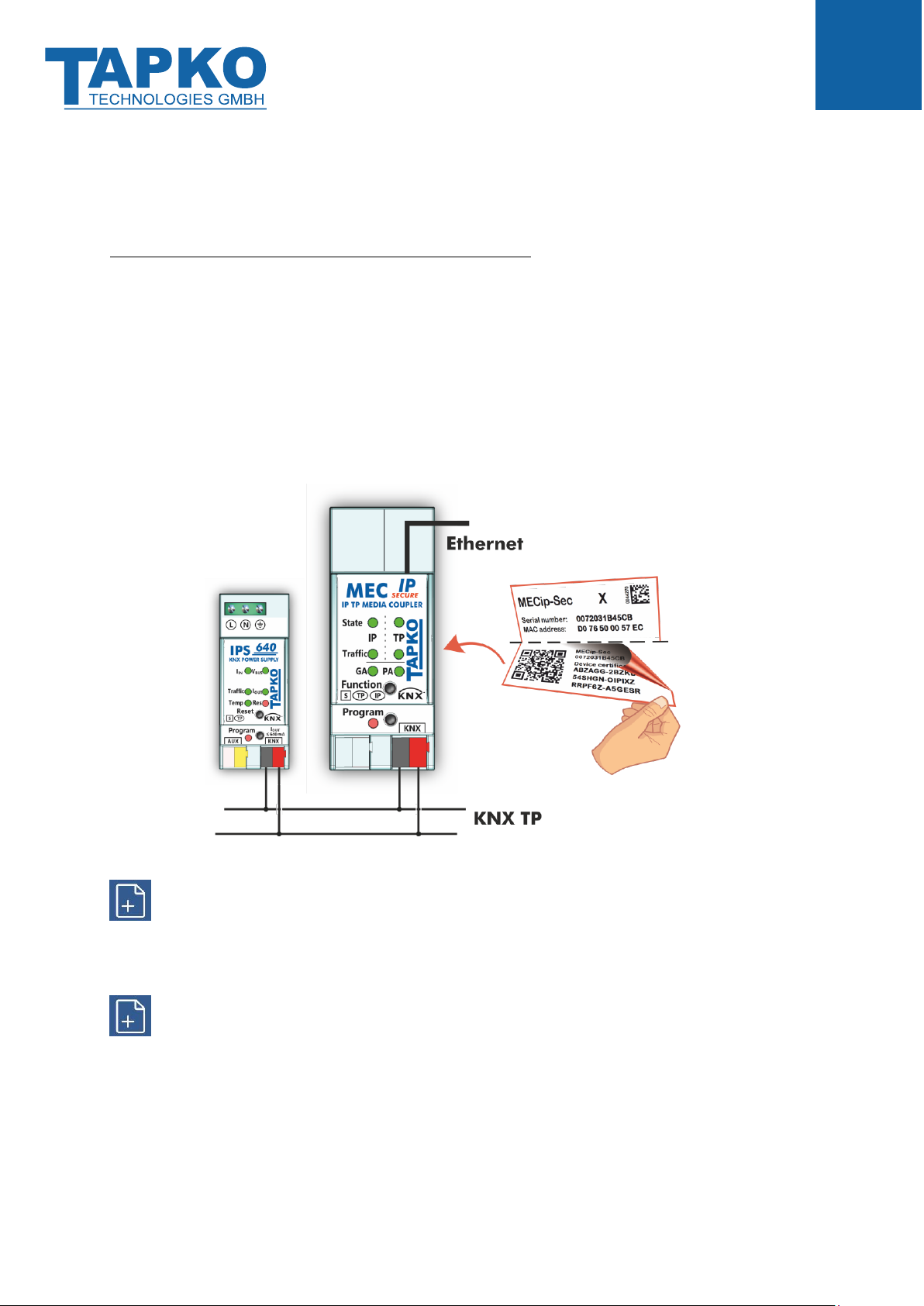
1.4 Commissioning
Please note for commissioning with default settings:
•All telegrams are blocked because the filter table is not defined
•The Manual Function switch-off time is 120 min
•Individual Address is 15.15.0
•Activation of Secure Commissioning requires the Device Certificate
•Activation of Secure Commissioning requires a minimum ETS version
(see also Security functions)
Figure 2: Connection Scheme
To start a secured configuration download, Secure Commissioning must be activated in
the ETS project before. Without activation, MECip-Sec is working as plain device and
will behave like MECip (without supporting KNX Secure).
Please also read chapter 1.6 Important Notes before putting the device into operation.

Product Description
MECip
SECURE
- 10 -
1.5 Secure Commissioning
Before the secured download of a configuration setting and/or the Individual Address can
start, the individual Device Certificate of MECip-Sec must have been added to the ETS
project. To be able to add it, the ETS project must be password-protected.
A secured download is only possible after activation of Secure Commissioning.
Activation of Secure Commissioning demands the individual Device Certificate.
Device Certificates can only be added to a password-protected ETS project.
When no project password is set, Secure Commissioning cannot be activated. ETS projects
with having Secure Commissioning and/or IP Security set to active always require pre-setting
a project password. Having no project password set on activation, the ETS then asks to type it
in.
Figure 3: Set Project Password
The individual Device Certificate always is enclosed with a KNX Secure product. To keep
the product fully configurable by the user, it is important to make sure the Device
Certificate cannot be lost (please note chapter 1.7 Safekeeping of Device Certificate).

Product Description
MECip
SECURE
- 11 -
1.6 Important Notes
It is recommended to participate the standardized courses of a KNX-certified training center
before installing, programming, and commissioning a KNX system. Here, the participant gains
the necessary knowledge and skills, also required for troubleshooting, by practical exercises.
Please read this chapter carefully before first use and installation:
1.6.1 Installation and Commissioning
•In the case of damage (at storage, transport) no repairs may be carried out by
unauthorized persons
•After connection to the KNX bus system, the device works with its default settings
•Warning: Do not connect to 230 V. The device is supplied by the KNX bus and does not
require any additional external power supply
•The device may only be installed and put into operation by a qualified electrician or
authorized person
•For planning and construction of electric installations the appropriate specifications,
guidelines and regulations in force of the respective country have to be complied
•For configuring, use the ETS (or ETS Inside)
1.6.2 Mounting and Safety
•For mounting use an appropriate equipment according to IEC60715
•Installation on a 35 mm DIN rail (TH35)
•Connect the KNX bus line as for common KNX bus connections with a KNX bus cable, to be
stripped and plugged into a KNX TP connector
•Do not damage electrical insulations during connecting
•Installation only in dry locations
1.6.3 Maintenance
•Accessibility of the device for operation and visual inspection must be provided
•The housing must not be opened
•Protect the device from moisture, dirt and damage
•The device needs no maintenance
•If necessary, the device can be cleaned with a dry cloth

Product Description
MECip
SECURE
- 12 -
1.7 Safekeeping of Device Certificate
The Device Certificate can be found on a label that is adhered on side of the housing. To
avoid unwanted access, the label consists of two parts. The upper part must remain on the
housing, for identifying the device. The lower one is the tear-off part. This part contains the
Device Certificate and should be removed from the device for keeping the information at a
safe place after commissioning.
Figure 4: Device Certificate Label
After adding the Device Certificate to the Device Certificate list in ETS, the tear-off part of the
Device Certificate label can be archived at a safe place. The Device Certificate list only needs
to contain the certificates of the KNX Secure devices that are used within the ETS project. ETS
then automatically uses the correct certificates for programming the relevant devices.
For clear identification of the device after removing the tear-off part, the serial number is
printed on both label parts, on the one that was removed and on the fixed one that stays on
the housing.
When the tear-off part that contains the Device Certificate is lost, only the password-
protected ETS project contains the Device Certificate.
Be aware, when the Device Certificate is completely lost, meaning the tear-off part is
unavailable and the project password (that contained the certificate) is lost, too, a
Secure device cannot be set to active secure mode anymore! Consequently, Security
cannot be activated within a new ETS project. In this case, to reprogram a Secure device
with active secure mode, a Reset has to be carried out and the Secure device can only
be used unsecured, as “plain” device, from then.
tear-off part

Product Description
MECip
SECURE
- 13 -
1.8 Feature Summary
•Device Certificates guarantee only authorized persons can have access to MECip-Sec.
•When the ETS “Secure Commissioning” function is active, configuration data is
downloaded only in encrypted KNX Data Secure format.
•Activation of “IP Backbone Security” for protection of IP routing.
•Configuring MECip-Sec plus devices on the main line from the subline can be switched off.
(This is very useful, when there are sublines that bear a high risk of being misused.)
•MECip-Sec supports long telegrams with up to 240 bytes APDU length. (Both product
series, the MEC couplers and UIM interfaces, can process long messages e.g. for energy
metering applications and visualization purposes, and support Extended Frames.)
•The great advantage, when MECip-Sec replaces a common TP line/area coupler is using a
KNX IP line as a fast KNX backbone instead of a TP backbone.
•MECip-Sec works without external power supply.
•For IP (Secure) Tunneling, four tunneling connections can be realized in parallel. On
activation of Secure Tunneling, the password protection becomes available.
•Settings to increase data throughput and decrease high bus traffic are featured.
•IACK sending on sent out messages is configurable.
•Repetition is configurable for both Physical Telegrams and Group Telegrams.
•To ease commissioning, troubleshooting and fast on-site diagnostics, normal run-time
filtering can temporarily be suspended by a single Function button press. Other lines can
be fully accessed without having to carry out additional ETS downloads. Switching back to
normal run-time filter settings after suspension period expiry is automatic (see Manual
Function). This avoids forgetting to reactivate the settings for normal filtering.
•UPnP Discovery enables discovering MECip-Sec within the IP network.
•ETS recognizes MECip-Sec as bus connection interface by KNXnet/IP Search Request.
•Updating the firmware can easily be accomplished by a web browser.
•The available web front-end provides informative settings and enables to remotely switch
the device into Programming Mode without using the Programming Button.
•With the web front-end, a 60 min busload history diagram can be watched.
•For Security, the web front-end can fully be disabled or be set to display only status info.
•MECip-Sec supports KNXnet/IP, ARP, ICMP, IGMP, HTTP, UPnP discovery, UDP/IP, TCP/IP,
DHCP and AutoIP.

KNXnet/IP
MECip
SECURE
- 14 -
2KNXnet/IP
The presence of the Internet Protocol (IP) has led to the definition of the KNXnet/IP protocol.
As documented in the KNXnet/IP specifications, KNX telegrams are transmitted encapsulated
in IP packets, and Ethernet networks can be used to route and tunnel KNX telegrams.
IP routers and IP interfaces are an excellent alternative to TP line/area couplers and USB data
interfaces. KNX IP routers are similar to TP line couplers, but make use of the KNXnet/IP
communication protocol. They connect the IP communication medium to TP, instead of
connecting two TP lines. According to this, a TP backbone can completely be replaced by an
Ethernet based IP backbone. It is even possible to integrate end devices directly via IP.
2.1 IP Secure Tunneling
KNXnet/IP provides KNX connection via IP Tunneling. Such point-to-point IP Tunneling
connections usually are used to connect clients like the ETS or supervisory systems to the
KNX installation. On activation of “Secure Tunneling”, these then called IP Secure Tunneling
connections become secured. This means the data communication of every channel is
encrypted and the possibility is offered to protect the single channels by passwords.
2.2 IP Secure Routing
Regarding KNX topology, KNX TP lines and areas can be connected by an Ethernet/IP
network, what then is called a KNX IP (backbone) line. KNX IP media couplers hereby transfer
the KNX data from TP to IP and vice versa, and are often called KNX IP routers for this reason.
For the data communication on KNX IP, or to be more exact, for the communication between
KNX IP devices, KNXnet/IP is the fundamental protocol for IP Routing. When IP Security is
active, the IP Routing specification is replaced by the IP Secure Routing specification and
KNX IP communication becomes entirely encrypted according to the security concept KNX
Secure. The KNX Secure part, that is relevant for IP, is called KNX IP Secure.
2.3 IP Firmware Update
To provide updating the firmware remotely via IP, MECip-Sec has a bootloader functionality
integrated. This function is called IP Firmware Update and can be executed in the web front-
end. The download process for rewriting the program memory content is independent from
ETS and replaces both communication stack and application software.

KNX Secure
MECip
SECURE
- 15 -
3KNX Secure
KNX devices that support KNX Secure are able to use a special protection basing on telegram
encryption. Also, access to the device for configuring is protected and limited to the user that
knows its Device Certificate. The Device Certificate is a device-specific protection code that is
enclosed with the device on delivery.
To make use of the KNX Secure protection, every KNX Secure device supports a secure mode.
When its secure mode is on, commissioning, configuring and runtime communication run in
an encrypted manner so that the device is shielded against intruder attack and unwanted
manipulation. For activation, the Device Certificate is necessary (see chapter 1.5 Secure
Commissioning). Only when secure mode is active, the KNX Secure device is able to read and
send encrypted telegrams. When secure mode is off, the Secure device behaves like a
common KNX device without KNX Secure support (also called plain KNX device). KNX Secure
devices in secure mode and plain devices can´t be combined by the same group object, but it
is possible to have a mixed installation consisting of secured devices and plain devices.
Mixing unsecure and secure communication on the same group address is impossible.
Also, a mix of KNX IP Secure couplers in secure mode and plain KNX IP Secure couplers
cannot be configured when IP Backbone Security is on.
Encrypted KNX telegrams that are processed by secured devices can be distinguished
between telegrams for KNX IP Secure and telegrams for KNX Data Secure:
•KNX IP Secure can only be applied upon the KNX IP medium. KNX Secure telegrams
are sent as encrypted IP Secure frames (no matter if KNX Data Secure is used or not).
•KNX Data Secure can be applied on any KNX communication medium. End-to-end
communication, better say group communication for one or more certain group
objects is encrypted. Due to an individual security key, only end devices having
identical Group Addresses can encrypt/decrypt the telegrams of their secured group.
For programming a KNX Secure device, ETS must know its FDSK (Factory Default Setup Key)
and its serial number. But it is not necessary entering FDSK or serial number. ETS retrieves
this information from the Device Certificate, a device-specific 36-character code containing
both serial number and FDSK. Serial number and FDSK cannot be modified. After adding a
KNX Secure device plus Device Certificate to the ETS project, ETS automatically sets the
project-specific Tool Key that is used for programming from then. This Tool Key cannot be
modified and only be deleted by a device reset (see chapter 4.6.2 Factory Reset). After the
reset, ETS uses the registered FDSK to get access to the device to program a new Tool Key.

Operational Description
MECip
SECURE
- 16 -
4Operational Description
In KNX network installations, MECip-Sec is used as KNX IP line/area coupler to connect
KNX IP and KNX TP (see also chapter 2.2 IP Secure Routing). It can be used in plain mode,
without activation of Security, and in ETS projects where Security is set to active. After
connecting to KNX TP, MECip-Sec operates with its default settings. For KNX IP routers, only
Individual Addresses x.y.0 can be set. Setting the correct Individual Address is necessary for
proper telegram transmission and functioning within the installation.
4.1 IP Secure Router Application
During normal operation, MECip-Sec reacts in accordance with its filter settings. When
MECip-Sec receives telegrams that use Individual Addresses as destination (for example
during commissioning), it compares the Individual Address of the receiver with its own
Individual Address and decides on that whether it has to route the telegrams or not. When
MECip-Sec receives telegrams that use group addresses as destination, only the telegrams
whose group addresses are entered in the filter table are routed.
If a telegram is routed by MECip-Sec to TP without receiving the corresponding
acknowledgement, i.e. due to a missing receiver or to a transmission error, the telegram will
be repeated up to three times (depending on the ETS setting). With the parameter
„Repetitions if errors ...“, this function can be configured for the KNX TP line and both kinds
of telegrams. It is recommended to use the default parameter setting.
The IP Secure Router application is designed for usage in 10/100 BaseT networks compliant
to IEEE802.3. The AutoSensing function sets the baud rate (10 Mbit or 100 Mbit)
automatically. The IP address can be received from a DHCP server. For this, the automatic
assignment of the IP address can be set in ETS (“obtain an IP address automatically”). If set so
and no DHCP server was found, MECip-Sec starts an AutoIP procedure and autonomously
assigns the IP address. For MECip-Sec having a fixed IP configuration (IP address as well as
subnet mask and standard gateway), this can also be set by ETS.

Operational Description
MECip
SECURE
- 17 -
4.2 IP Network
In the IP network, MECip-Sec sends and receives telegrams in accordance with the KNXnet/IP
protocol specification. According to the default setting, IP telegrams are sent as IP Multicast to
the IP address 224.0.23.12. Multicast IP address 224.0.23.12 and port 3671 are the defined
values for KNXnet/IP by KNX Association in conjunction with IANA.
Important notes:
•All KNX IP devices that are intended to communicate with each other via IP must have
the same IP multicast address.
•Multicast IP address 224.0.23.12 may need to be changed in respect of the network
type and of the network components´ settings. It is recommended to change this
address only when it becomes necessary due to the environment.
•IGMP (Internet Group Management Protocol) is used for IP Routing and Discovery.
•If problems occur for IP address assignment, please ask your network administrator.
•According to the topology, Individual Addresses that are used for Tunneling channels
always have to be assigned in the range of subline addresses. Detailed information
about these additional Individual Addresses can be found in chapter 5.4 IP (Secure)
Tunneling Address Assignment.
Operational Description
MECip
SECURE
- 18 -
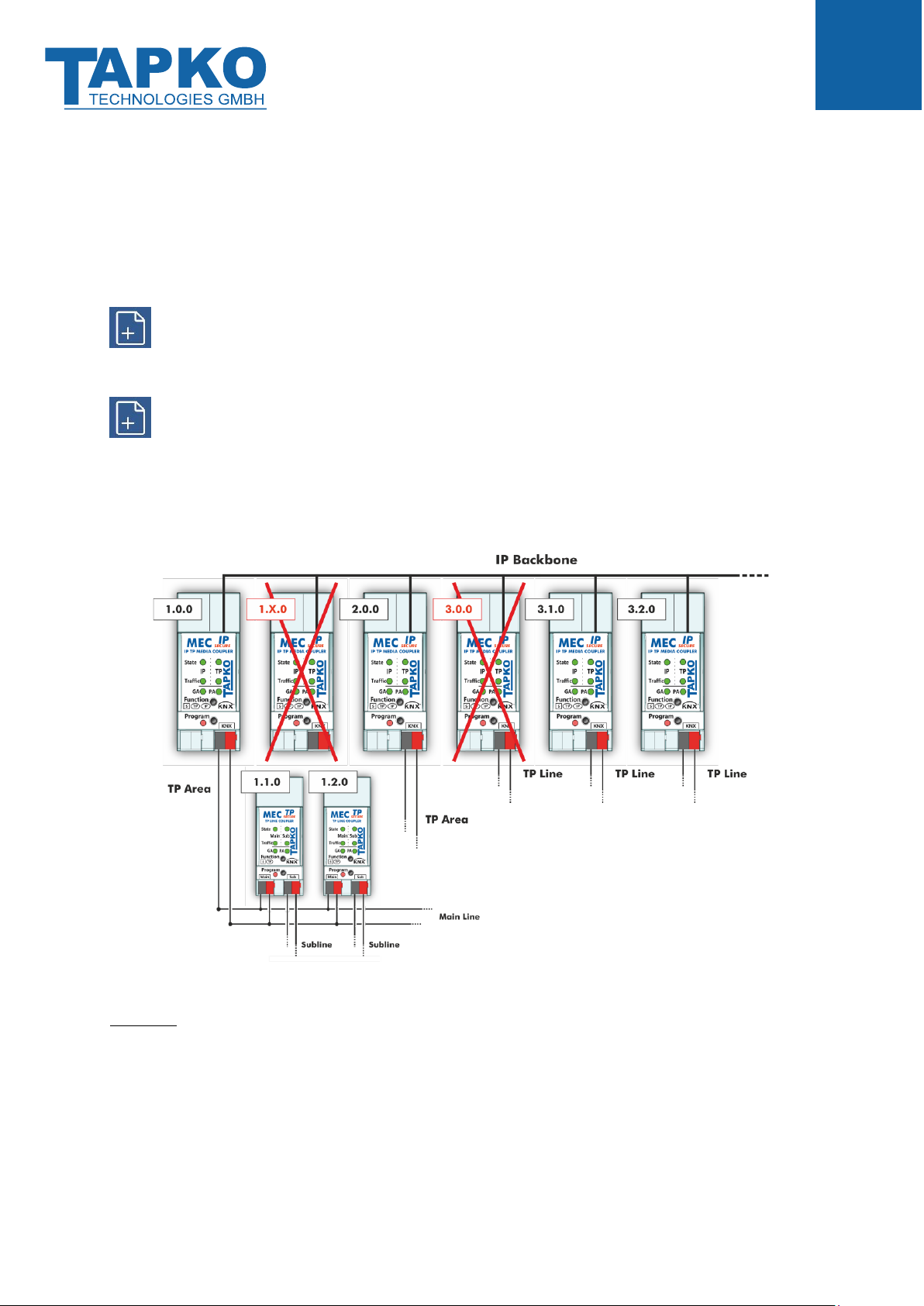
4.3 KNX Network Installation
For MECip-Sec´s usage in a KNX installation, one of the available Individual Addresses must
be chosen. Having set an Individual Address (x.y.0), a TP Line is connected to KNX IP. To
connect a TP Area to the IP Backbone, an area coupler address (x.0.0) must be set.
It is recommended to make sure the factory default Individual Address 15.15.0 is not
used in the installation network.
Defining a correct topology is absolutely mandatory to guarantee proper functioning.
In a KNX system with MECip-Sec backbone couplers and MECtp-Sec line couplers, it is
necessary to ensure that every MECip-Sec has an address assigned from a free addressing
area. Following figure illustrates a possible topology scenario.
Figure 5: MECip-Sec Network Topology
Example: If a KNX IP router with address 1.0.0 already exists on the backbone no KNX IP
router with address 1.x.0 can be added here. Even if no line coupler with address 1.1.0 exists
on the subline of the 1.0.0 router. Vice versa, when line couplers with addresses 3.x.0 already
exist in an installation, an IP router with address 3.0.0 cannot be added.
Operational Description
MECip
SECURE
- 19 -
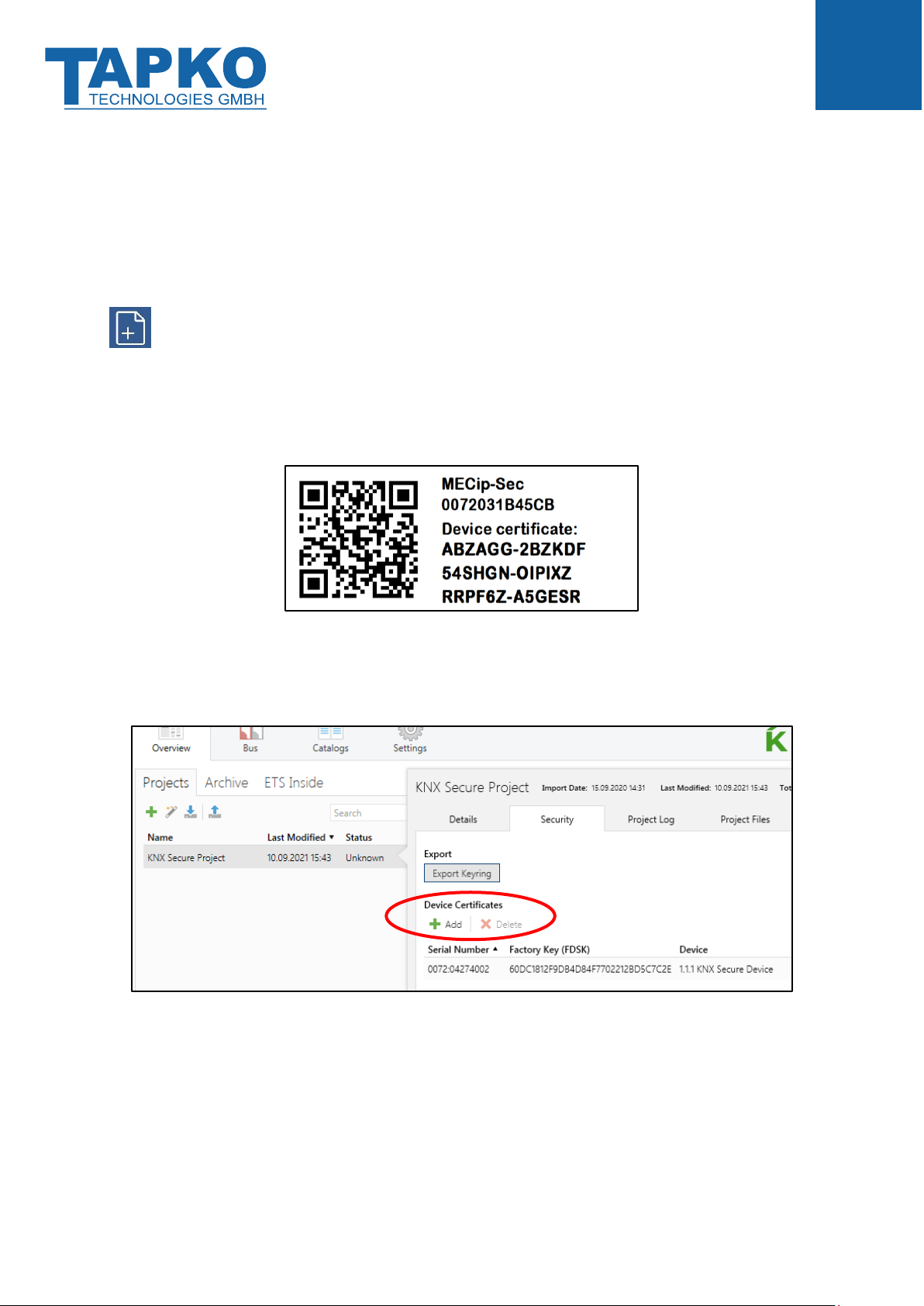
4.4 Adding Device Certificate
The Device Certificate can be found printed on a side label on the housing. Every KNX Secure
device uses its own Device Certificate. Entering this Device Certificate in ETS is mandatory
before activating or using KNX Security functions.
Please also follow the advice on handling the tear-off part of the side label in chapter
1.7 Safekeeping of Device Certificate.
The Device Certificate can be entered manually and by taking a webcam picture of the QR
code that is additionally contained on the tear-off part of the Device Certificate side label.
Figure 6: Tear-off Part of the Device Certificate Side Label
After opening the project, the Device Certificate list can be edited. In the Security tab under
Project Overview Device Certificates can be added and deleted.
Figure 7: Device Certificate List
When the Device Certificate list doesn´t contain the Device Certificate of a certain Secure
device, on starting the Secure download into this device following window appears. Then, the
QR code must be scanned, or alternatively, the 36-character code of the Device Certificate
must be entered manually to continue.

Operational Description
MECip
SECURE
- 20 -
Figure 8: Adding Device Certificate
Table of contents
Other TAPKO Cables And Connectors manuals