2
Setting-up SecureComm...........................................................................................3
Commissioning the GSM-WiFi U - Standalone Mode................................................3
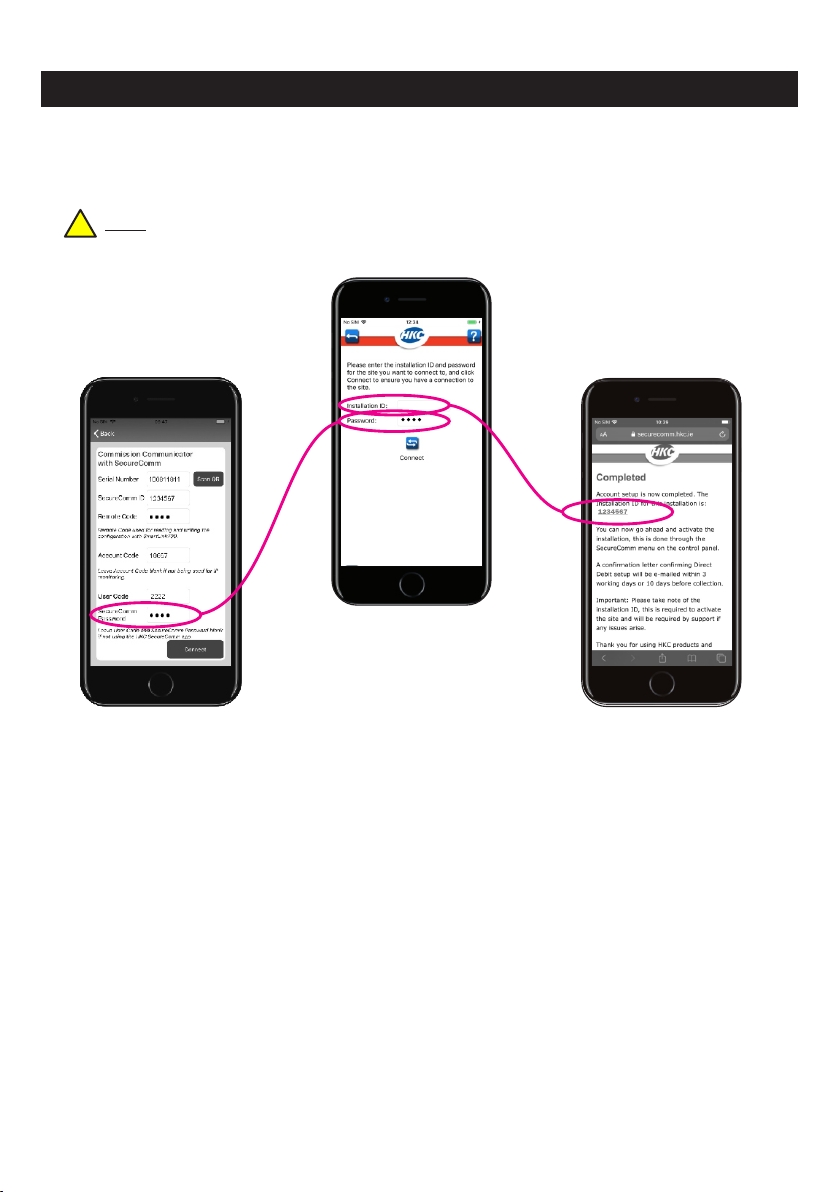
How to commission u
...........................................................10
......11
Technical Specifications...........................................................................................26
sing the
he HKC APP...........................
......................................................
SmartLink700 app...........................................4
Downloading t ................................................8
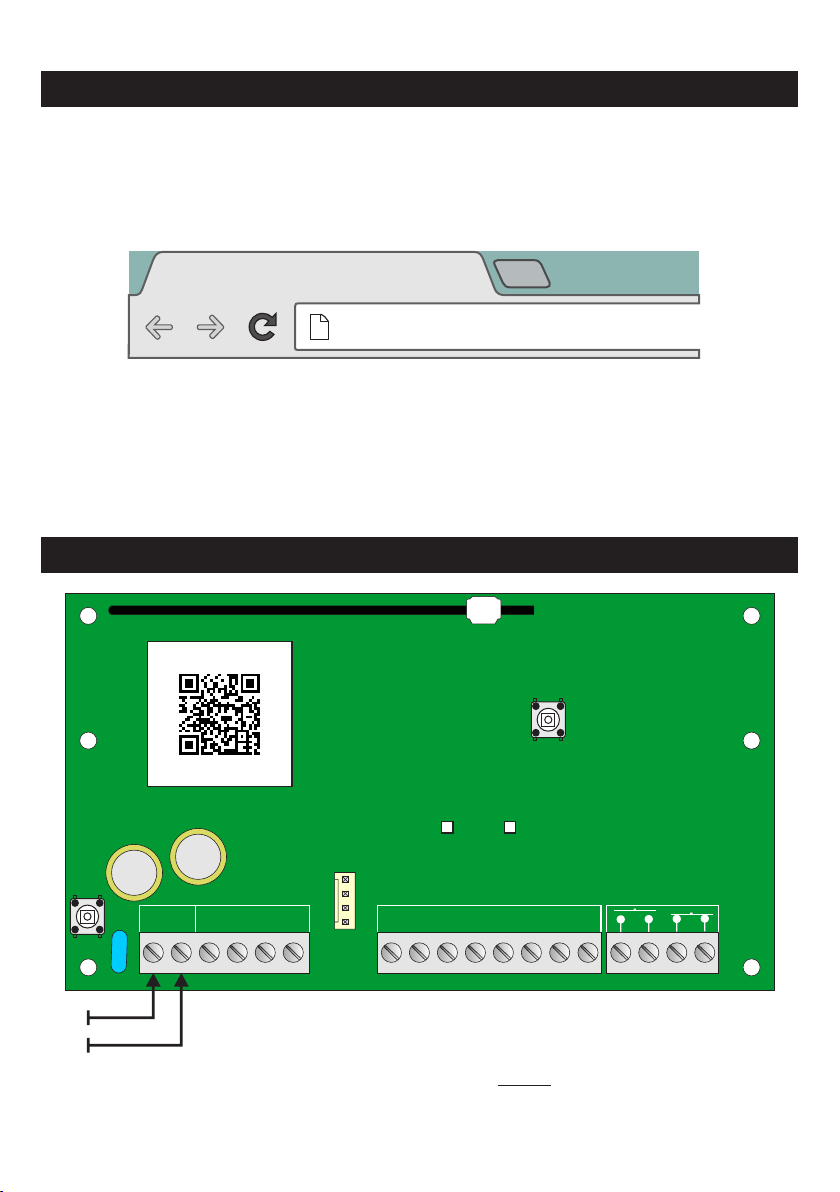
GSM-WiFiU Inputs & Outputs......... ........9
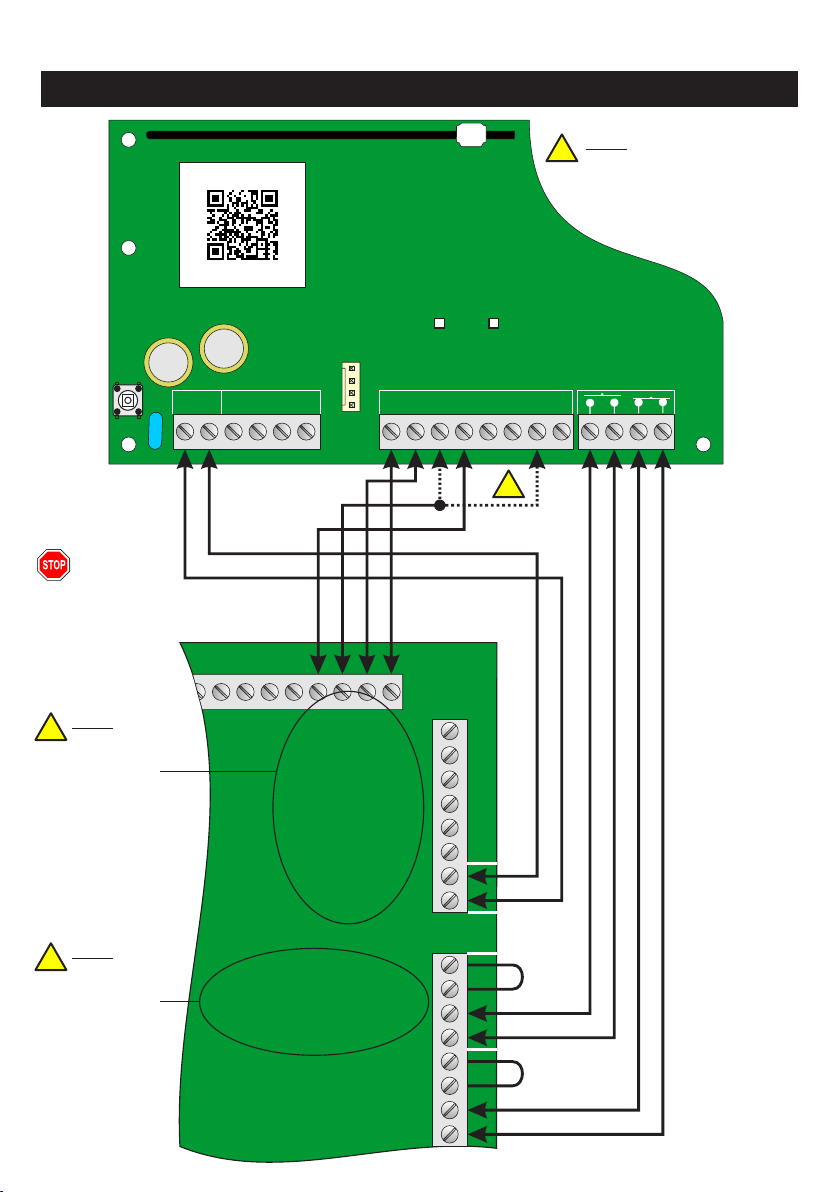
Example of Standalone Wiring........
Commissioning GSM-WiFi U - SecureWatch Mode.............................................
Wiring to SecureWatch Panel.....................................................................12
Menu Map for SecureWatch Panels.............................................................13
Communicators Menu - SecureWatch Panels.............................................14
SecureComm Menu - SecureWatch Panels................................................16
Commissioning GSM-WiFi U - SecureWave Mode....................................................18
Wiring to SecureWave Panel.......................................................................19
Menu Map for SecureWave Panels..............................................................20
Communicators Menu - SecureWave Panels...............................................21
SecureComm Menu - SecureWave Panels..................................................23
GSM & WiFi Status LEDs.............................................................................26
Contents
WARNING
While this system has been designed to the highest standards it does not offer guaranteed protection against burglary, fire or carbon
monoxide. Any alarm system is subject to compromise or failure to activate for a variety of reasons. Therefore, good installation practices and
regular maintenance are essential to ensure continuous satisfactory operation of the system. The transmission of messages is dependent on
the telecom service provider. HKC Security Ltd. cannot guarantee successful messaging. Messages which remain undelivered when the
validity period expires are discarded. The validity period is the time the message is submitted plus 12 hours.
COPYRIGHT
© HKC Security Ltd. All Rights reserved. No part of this publication may be reproduced, transmitted, stored in a retrieval system or translated
in another language in any form or by any means - electronic, mechanical or otherwise without the prior written permission of HKC Security
Ltd.
DISCLAIMER
HKC Security Ltd. makes no representations or warranties with respect to the contents hereof and specifically disclaim any implied warranties
of merchantability or fitness for any particular purpose. Further, HKC Security Ltd. reserve the right to revise this publication and to make
changes from time to time in the contents hereof without obligation of HKC Security Ltd. to notify any person of such revision.
This marking certifies that this product has been tested in a representative system complying with the requirements laid down in EMC
directive 2014/30/EU, RE Directive 2014/53/EU, RoHS directive 2011/65/EU and their amendments.
GSM-WiFiU Installation Manual Rev 2. 11th of November, 2020