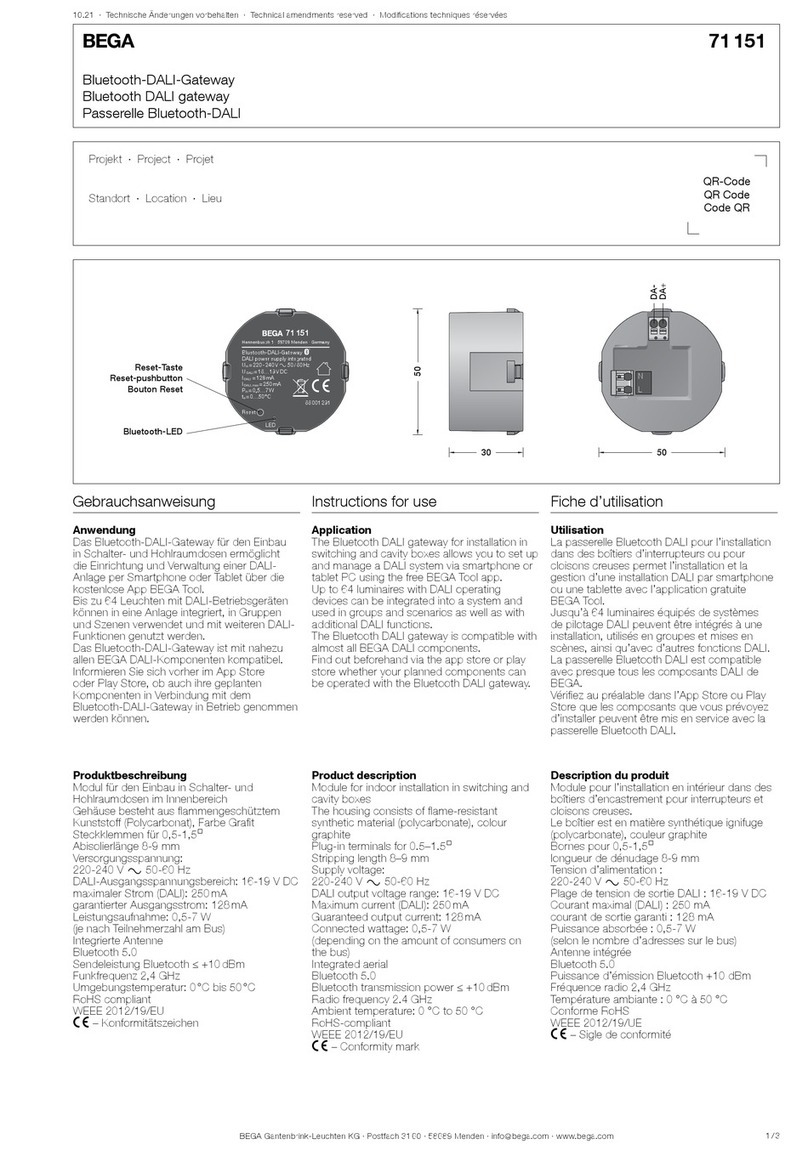
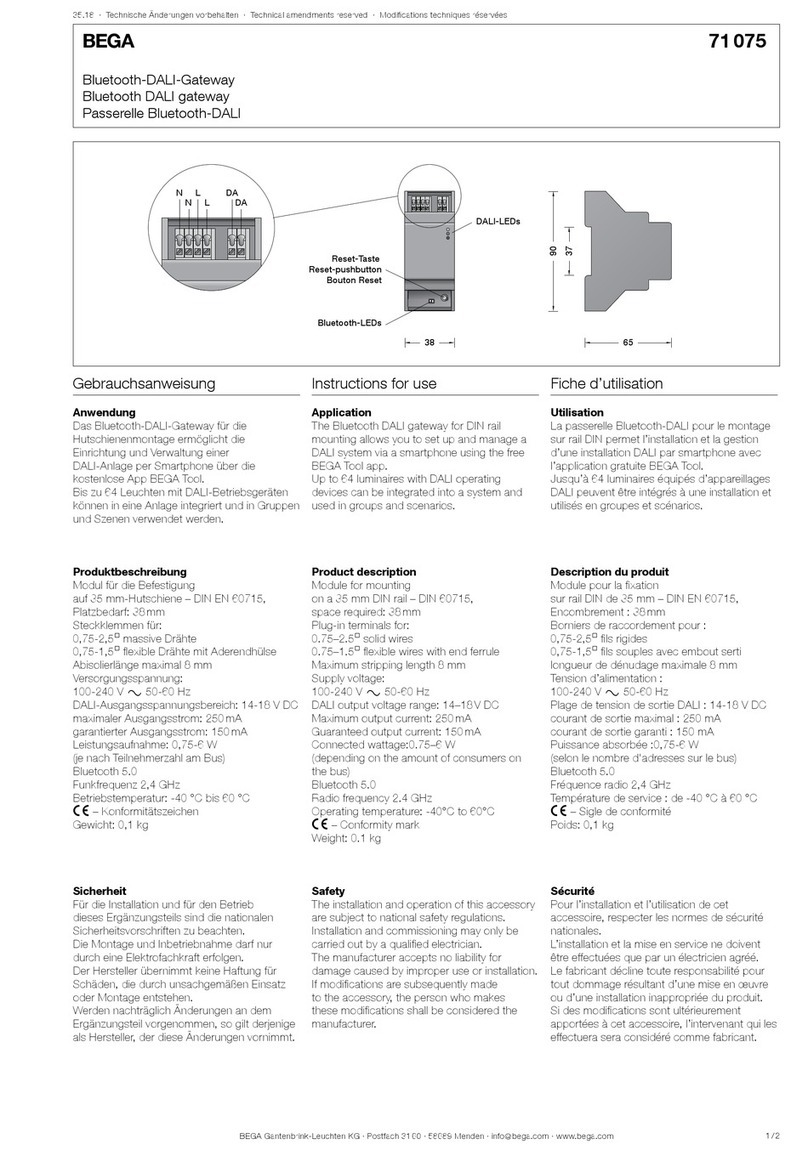
6Gateway 70 588
Chapter 1 | General information
1.2 Security and privacy
From the very beginning our ZigBee Gateway development department focused on developing encryption and
authentication algorithms ensuring that at any time only you can gain access to your system’s components.
However, as the system’s operator you will need to uphold some basic security concepts in order not to
compromise the system’s security.
1.2.1 Safety of radio links
Hacker attacks via radio links are only possible when the attacker is in range of your facility’s radio network.
For this reason, hackers don’t prioritize these objects, but put their focus on devices that can be globally
accessed, such as gateways. Nevertheless, we attached importance to insuring that the radio interface met all
high level safety requirements. As an administrator of a public facility, e.g. a hotel, holiday resort, company or a
government building, you should take the threat of such hacker attacks seriously.
Radio links between the components of your BEGA Control ZigBee network are based on the standard ZigBee
Home Automation System, which is based on the ZigBee PRO core technology. ZigBee PRO includes several
safety features, such as an AES-128 network key to ensure that your data can’t be read by third parties near
your facility. Moreover, it is not possible for attackers to send control commands to your network, or to record
legit control commands for future execution (“replay attack”). Unlike proprietary solutions, the open ZigBee
PRO standard has passed safety tests, allowing it to be used in billing related systems and companies.
1.2.2 Gateway safety
The gateway has several services that are required to gain access to your facility from the outside or for certain
event or time controlled processes. This includes the Smart Facility Service, which establishes the connection
between the facility and the BEGA Gateway app on your mobile device. Naturally, is has to be ensured that this
service is accessible from the outside. Therefore, all connections from your apps to this service are especially
protected and encrypted.
While setting up your facility via app, access authorization will be installed on your smartphone, giving you
access to your facility after the setup. A lost smartphone can be locked out at any time via the gateway’s web
interface.
Make sure that the web interface of your gateway cannot be accessed from the outside. Don’t set up port
forwarding via the TCP port 80, use local accesses or secured connections such as VPN to gain safe access
to the web interface.
1.2.3 Remote maintenance
Remote maintenance is done via a secured connection. This connection is protected by a certificate and has to
be opened explicitly via the gateway’s web interface. The interface will indicate an active remote access.
1.2.4 Updates
Firmware updates for your gateway are signed. Therefore, they cannot be manipulated to install threatening
software. The firmware for ZigBee devices is encrypted and has an integrity test. Every time the gateway firm-
ware is updated, the current firmware version and serial number will be stored for statistic reasons.