Bosslan BOSSW76 User manual

BOSSW76
CPE /AP/ Bridge/Router
High Power Wireless Radio Output power Max 200mW
Built with 18dBi Panel antenna frequency 5725~5850MHz
Add N type for option b/g antenna (radio board 11abg) or high gain antenna
It is innovative for saving cost and convenience on your networking solutio
User’s Manual

2
- Index -
1. Wireless Technology................................................................................................................................5
1.1 Standard..............................................................................................................................................5
1.2 Planning your Wireless Network........................................................................................................5
2. Connecting The BOSSW76 To Your Network................................................6
3. AP/ WDS (Bridge) Mode Configuration..................................................................................................7
3.1 Login Web page .................................................................................................................................9
3.2 Information.........................................................................................................................................9
3.3 Stations.............................................................................................................................................10
3.4 Wireless Basic..................................................................................................................................11
3.4.1 Wireless Model..........................................................................................................................12
3.4.2 Wireless On/Off.......................................................................................................................12
3.4.3 Visibility Status.........................................................................................................................12
3.4.4 SSID ..........................................................................................................................................12
3.4.5 Transmission rate (Mbits/s).......................................................................................................12
3.4.6 802.11 Mode..............................................................................................................................12
3.4.7 Super Mode ...............................................................................................................................13
3.4.8 Adaptive Radio Selection..........................................................................................................13
3.4.9 Auto Channel Select..................................................................................................................13
3.4.10 Channel....................................................................................................................................14
3.5 WDS.................................................................................................................................................13
3.5.1 Enable WDS..............................................................................................................................13
3.5.2 AP MAC address.......................................................................................................................13
3.6 Security Setup...................................................................................................................................14
3.6.1 WPA Setup................................................................................................................................14
3.6.1.1 WPA Enable.......................................................................................................................14
3.6.1.2 WPA Mode.........................................................................................................................15
3.6.1.3 Cipher Type........................................................................................................................15
3.6.1.4 PSK.....................................................................................................................................16
3.6.1.5 WPA Group Key Update Interval.......................................................................................17
3.6.2 802.1X Setup.............................................................................................................................17
3.6.2.1 802.1X enable:....................................................................................................................17
3.6.2.2 Authentication timeout (mins)............................................................................................17
3.6.2.3 RADIUS server IP address.................................................................................................18
3.6.2.4 RADIUS server port number..............................................................................................18
3.6.2.5 RADIUS server shared secret.............................................................................................18
3.6.2.6 MAC Address Authentication ............................................................................................18
3.6.3 Wire Equivalent Privacy (WEP) Setup......................................................................................18
3.6.3.1 Enable WEP........................................................................................................................19
3.6.3.2 Default WEP key to use......................................................................................................19

3
3.6.3.3 Authentication ....................................................................................................................19
3.6.3.4 WEP key lengths ................................................................................................................19
3.6.3.5 Valid Key............................................................................................................................19
3.7 Access Control Setup .......................................................................................................................19
3.7.1 Enable access control.................................................................................................................19
3.7.2 MAC Address............................................................................................................................19
3.8 Administration setup ........................................................................................................................19
3.8.1 Reboot .......................................................................................................................................19
3.8.2 Reset Configuration...................................................................................................................19
3.8.3 Firmware Upgrade.....................................................................................................................19
3.8.4 Device name..............................................................................................................................29
3.8.5 IP setting....................................................................................................................................29
3.8.5.1 IP Address Mode................................................................................................................30
3.8.5.2 Default IP address...............................................................................................................29
3.8.5.3 Default subnet mask ...........................................................................................................30
3.8.5.4 Default gateway..................................................................................................................30
3.8.6 Security......................................................................................................................................30
3.8.6.1 User name...........................................................................................................................30
3.8.6.2 Administrator password......................................................................................................30
3.9 Advanced Setup................................................................................................................................27
3.9.1 Fragmentation threshold............................................................................................................27
3.9.2 RTS threshold............................................................................................................................28
3.9.3 Beacon period............................................................................................................................28
3.9.4 DTIM interval............................................................................................................................28
3.9.5 802.11d......................................................................................................................................28
3.9.6 Transmit Power .........................................................................................................................28
3.9.7 Antenna selection ......................................................................................................................29
3.9.8 Act Timeout...............................................................................................................................29
4. AP Client Mode......................................................................................................................................30
4.1 Information.......................................................................................................................................30
4.2 Access Points....................................................................................................................................30
4.3 Basic Wireless..................................................................................................................................31
4.3.1 Wireless Model..........................................................................................................................31
4.3.2 Wireless On/Off.........................................................................................................................31
4.3.3 Wireless Mode...........................................................................................................................31
4.3.4 Wireless Network Name (SSID) ...............................................................................................31
4.3.5 Transmission rate (Mbits/s).......................................................................................................32
4.3.6 802.11 Mode..............................................................................................................................32
4.3.7 Super Mode ...............................................................................................................................32
4.3.8 Channel......................................................................................................................................33
4.4 Security Setup...................................................................................................................................33

4
4.4.1 WPA Configuration...................................................................................................................34
4.4.1.1 WPA Enable.......................................................................................................................38
4.4.1.2 WPA Mode.........................................................................................................................38
4.4.1.3 Cipher Type........................................................................................................................39
4.4.1.4 PSK.....................................................................................................................................39
4.4.2 Wire Equivalent Privacy (WEP) Configuration ........................................................................35
4.4.2.1 Enable WEP........................................................................................................................41
4.4.2.2 Default WEP Key To Use...................................................................................................42
4.4.2.3 IP Authentication................................................................................................................42
4.4.2.4 WEP Key Lengths..............................................................................................................42
4.4.2.5 Valid Key............................................................................................................................42
4.5 Administration setup ........................................................................................................................38
4.5.1 Reboot .......................................................................................................................................38
4.5.2 Reset Configuration...................................................................................................................38
4.5.3 Firmware Upgrade...................................................................................................................394
4.5.4 Device name..............................................................................................................................39
4.5.5 IP setting....................................................................................................................................40
4.5.5.1 IP Address Mode................................................................................................................46
4.5.5.2 Default IP Address..............................................................................................................46
4.5.5.3 Default Subnet Mask..........................................................................................................46
4.5.5.4 Default Gateway.................................................................................................................46
4.5.6 Security......................................................................................................................................47
4.5.6.1 User Name..........................................................................................................................47
4.5.6.2 Administrator Password .....................................................................................................47
4.6 Advanced Setup................................................................................................................................41
4.6.1 Fragmentation threshold............................................................................................................41
4.6.2 RTS threshold............................................................................................................................42
4.6.3 Beacon period............................................................................................................................42
4.6.4 DTIM interval............................................................................................................................42
4.6.5 802.11d......................................................................................................................................49
4.6.6 Transmit Power .........................................................................................................................49
4.6.7 Antenna selection ......................................................................................................................49
4.6.8 Act Timeout...............................................................................................................................49

5
1. The Wireless Technology
1.1 Standard
The Wireless Access Point utilizes the 802.11b, 802.11g or 802.11a standards. The IEEE 802.11g standard is an
extension of the 802.11b standard. It increases the data rate up to 54 Mbps (108Mbps in Super G mode) within the
2.4GHz band, utilizing OFDM technology. This means that in most environments, within the specified range of this
device, you will be able to transfer large files quickly or even watch a movie in MPEG format you’re your network
without noticeable delays. The IEEE 802.11a standard is based on 5.8 GHz band with data rate up to 54 Mbps (108
Mbps in Turbo mode) to have a better clean wireless band away from interference.
These two standards work by transmitting high-speed digital data over a radio wave utilizing OFDM (Orthogonal
Frequency Division Multiplexing) technology. OFDM works by splitting the radio signal into multiple smaller
sub-signals that are then transmitted simultaneously at different frequencies to the receiver. OFDM reduces the
amount of cross talk (interference) in signal transmissions. The AP will automatically sense the best possible
connection speed to ensure the greatest speed and range possible. The 802.11g and 802.11a offers the most
advanced network security features available today, including: WPA, TKIP, AES and Pre-Shared Key mode.
U11.2 Planning Your Wireless Network
Network Topology
A wireless network is a group of computers, each equipped with one wireless adapter. Computers in a wireless
network must be configured to share the same radio channel. Several PCs equipped with wireless cards or adapters
can communicate with one another to form an ad-hoc network. The wireless adapters also provide users access to a
wired network when using an access point or wireless router. An integrated wireless and wired network is called an
infrastructure network. Each wireless PC in an infrastructure network can talk to any computer in a wired network
infrastructure via the access point or wireless router. An infrastructure configuration extends the accessibility of a
wireless PC to a wired network, and may double the effective wireless transmission range for two wireless adapter
PCs. Since an access point is able to forward data within a network, the effective transmission range in an
infrastructure network may be doubled.
Roaming
Infrastructure mode also supports roaming capabilities for mobile users. Roaming means that you can move your
wireless PC within your network and the access points will pick up the wireless PC's signal, providing that they both
share the same channel and SSID. Before enabling you consider roaming, choose a feasible radio channel and
optimum access point position. Proper access point positioning combined with a clear radio signal will greatly
enhance performance.
Network Layout
The AP Access Point has been designed for use with 802.11a or 802.11g and 802.11b products. With 802.11g
products communicating with the 802.11b standard, products using these standards can communicate with each
6
other. The Access point is compatible with 802.11a or 802.11g and 802.11b adapters, such at the PC Cards for your
laptop computers, PCI Card for your desktop PC, and USB Adapters for when you want to enjoy USB connectivity.
These wireless products can also communicate with a 802.11g or 802.11b wireless Print Server. When you wish to
connect your wired network with your wireless network, the Access Point’s network port can be used to connect to
any of switches or routers.
Installation Considerations
The AP lets you access your network, using a wireless connection, from virtually anywhere within its operating range.
Keep in mind, however, that the number, thickness and location of walls, ceilings, or other objects that the wireless
signals must pass through, may limit the range. Typical ranges vary depending on the types of materials and
background RF (radio frequency) noise in your home or business. The key to maximizing wireless range is to follow
these basic guidelines:
zKeep your product away (at least 3-6 feet or 1-2 meters) from electrical devices or appliances that generate RF
noise.
zKeep the number of walls and ceilings between the AP and other network devices to a minimum - each wall or
ceiling can reduce your AP’s range from 3-90 feet (1-30 meters.) Position your devices so that the number of
walls or ceilings is minimized.
zBe aware of the direct line between network devices. A wall that is 1.5 feet thick(0.5 meters), at a 45-degree
angle appears to be almost 3 feet (1 meter) thick. At a 2-degree angle it looks over 42 feet (14 meters) thick!
Position devices so that the signal will travel straight through a wall or ceiling (instead of at an angle) for better
reception.
zBuilding materials can impede the wireless signal - a solid metal door or aluminum studs may have a negative
effect on range. Try to position wireless devices and computers with wireless adapters so that the signal passes
through drywall or open doorways and not other materials.
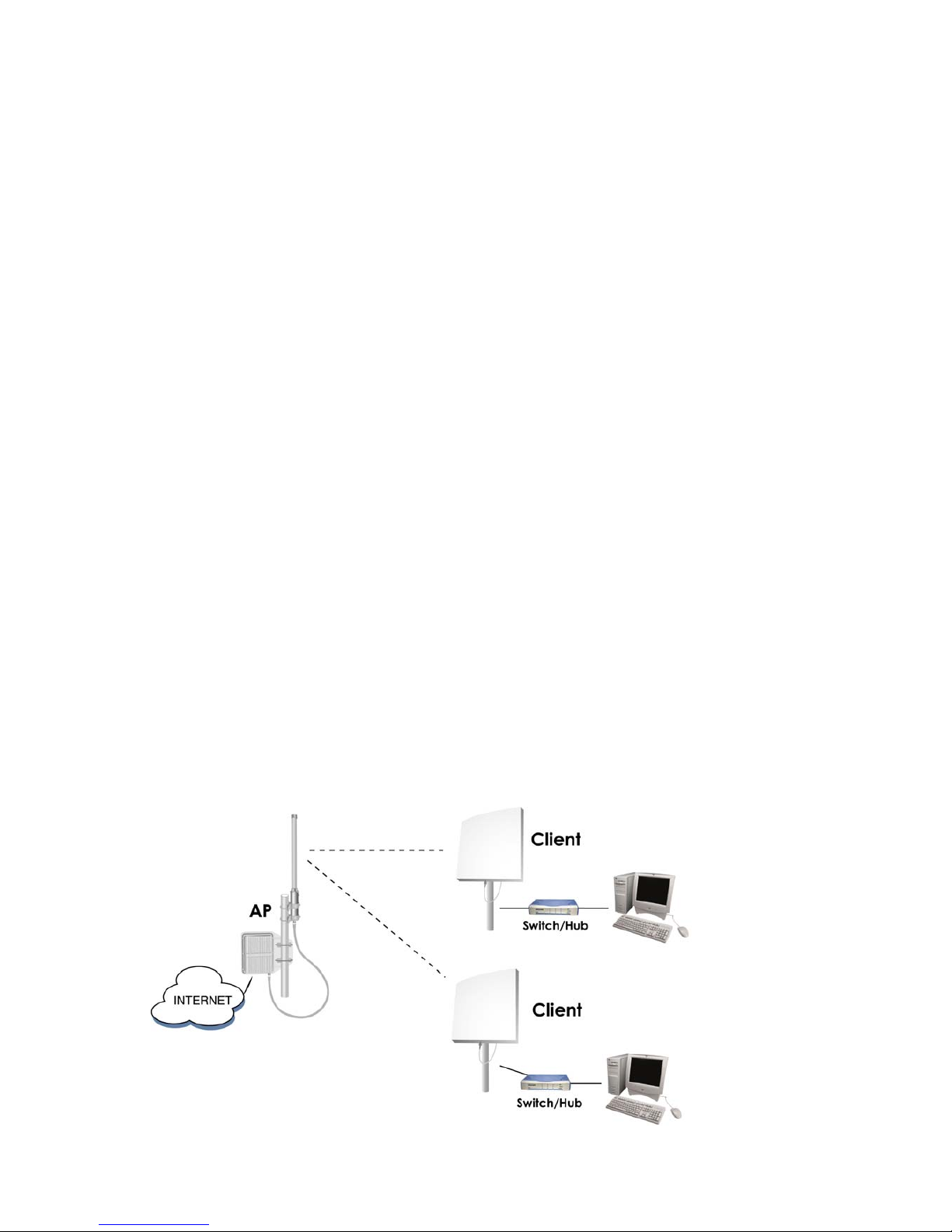
Network Topology – AP Mode and Client Mode
7
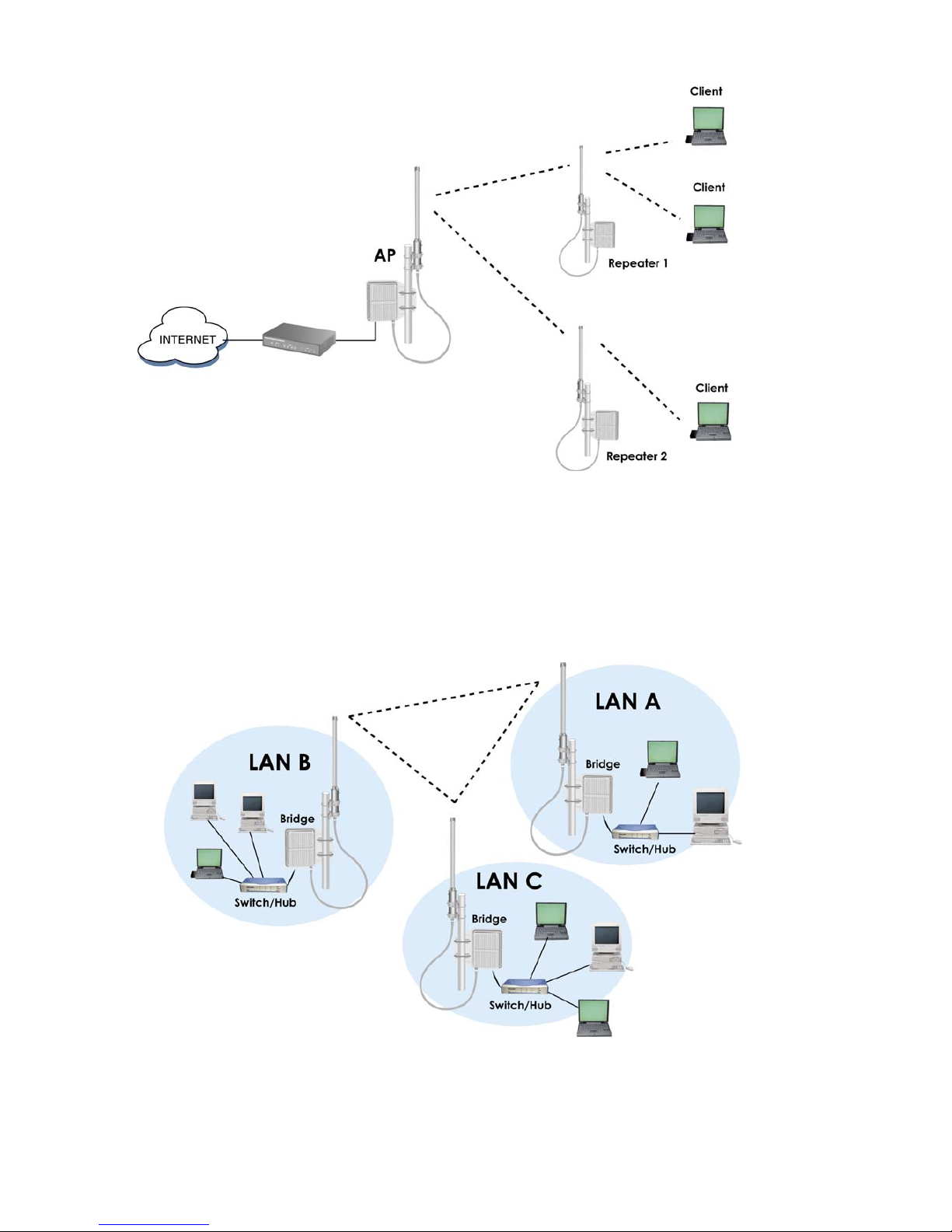
Network Topology – Repeater Mode
Network Topology – Wireless Bridge (WDS) Point to Multi-Point Mode

8
Connecting the BOSSW76 to Your Network
Step 1:
First, connect the POE injector with two Ethernet cable and the power adapter, then plug the other end of the power
adapter to a wall outlet or power strip.
Step 2:
Insert an Ethernet cable (Out) to LAN port of the BOSSW76 and another Ethernet
cable (In) to the network adapter in the computer; you will use it to configure the BOSSW76.
9
AP/ WDS (Bridge) Mode Configuration
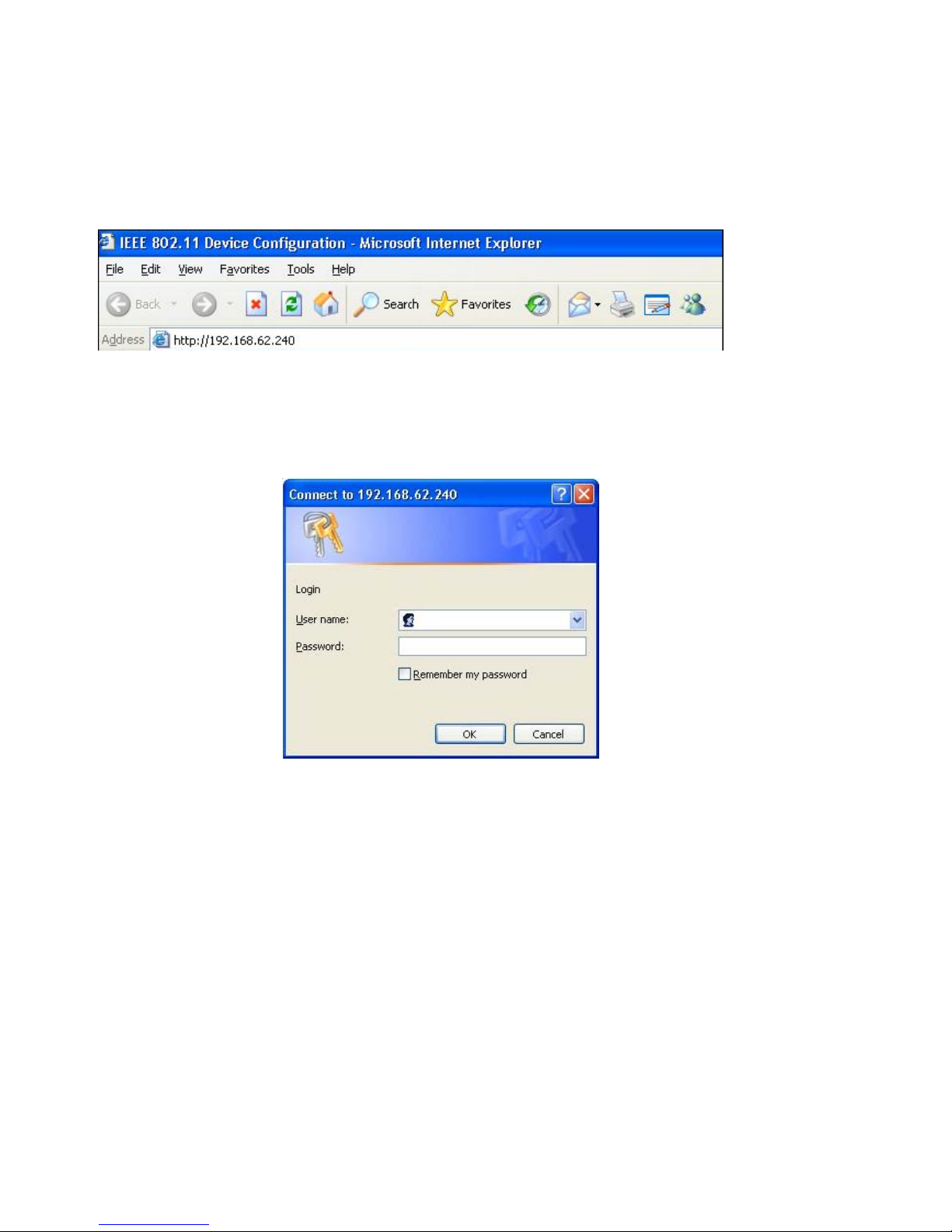
3.1 Login Web Page
To access the web control interface, please open a browser window and type in the factory default IP address in the
URL : 192.168.62.240.
Using the Web-based Management Setup
There are only a few basic steps you need to complete to set up the wireless bridge for your network. The Setup web
page takes you through configuration procedures for the radio channel selection, IP configuration, and wireless
security.
Logging In – Click “OK” (there is NO default user name or password, just leave the field blank).
3.2 Information
Under the main web page you will see the configuration menu pages for :
Information, Stations, Wireless, WDS, Security, Filtering, Admin and Advanced.
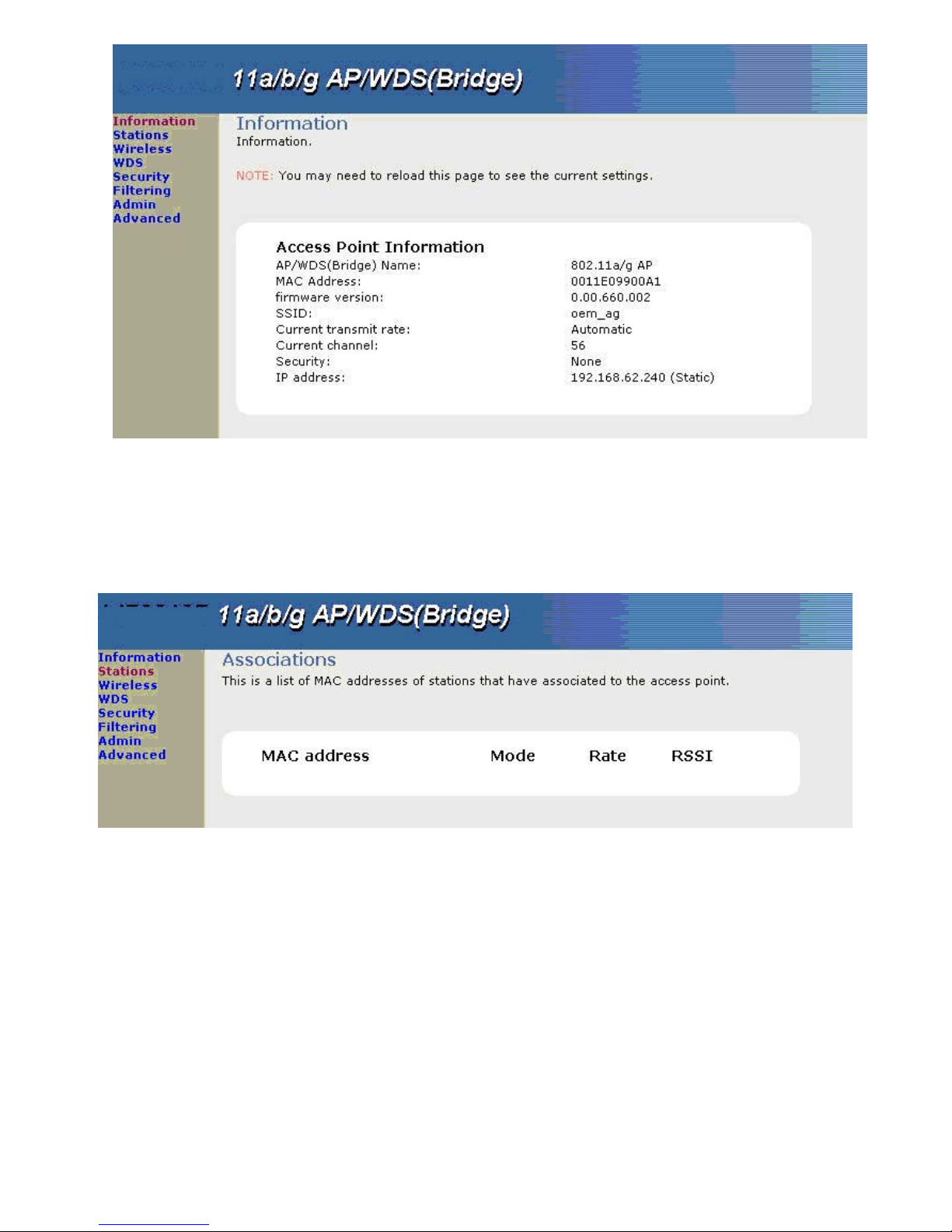
The “Information” windows displays the settings of the BOSSW76 AP/WDS (Bridge), the AP/WDS (Bridge)
Name, MAC Address, firmware version, SSID, Current transmit rate, Current channel, Security and IP address.
10
3.3 Stations
This is to display the list of MAC addresses and some RF related information of available stations that have
associated to theAccess Point in the area.

11
3.4 Wireless Basic
This is to show the wireless basic setting for the user to choose the options for their wireless application:
12
3.4.1 Wireless Model
Change wireless mode for AP/WDS (Bridge) or AP Client. Here please select “AP/WDS (Bridge)”.
3.4.2 Wireless On/Off
This is to Select On or Off switch of the radio card. By selecting OFF all wireless functions of the Access Point will
turn disabled. (Default: ON)
3.4.3 Visibility Status
This is for Visible or Invisible the SSID during broadcasting. When the Invisible is selected, the SSID will not be
broadcasted in the beacons, so the clients has to know the networking name (SSID) to associate with this
Access Point. Enabling this feature the SSID will broadcast the SSID across the network.
3.4.4 SSID
(Access point mode only) SSID (Service Set Identifier) is the name designated for a specific wireless local area
network (WLAN) and provided by Access Point. Clients that want to connect to the WLAN through the access
point must set their SSID to the same as that of Access Point. (Default: oem_ag; Range: 1-32 characters could
be input).
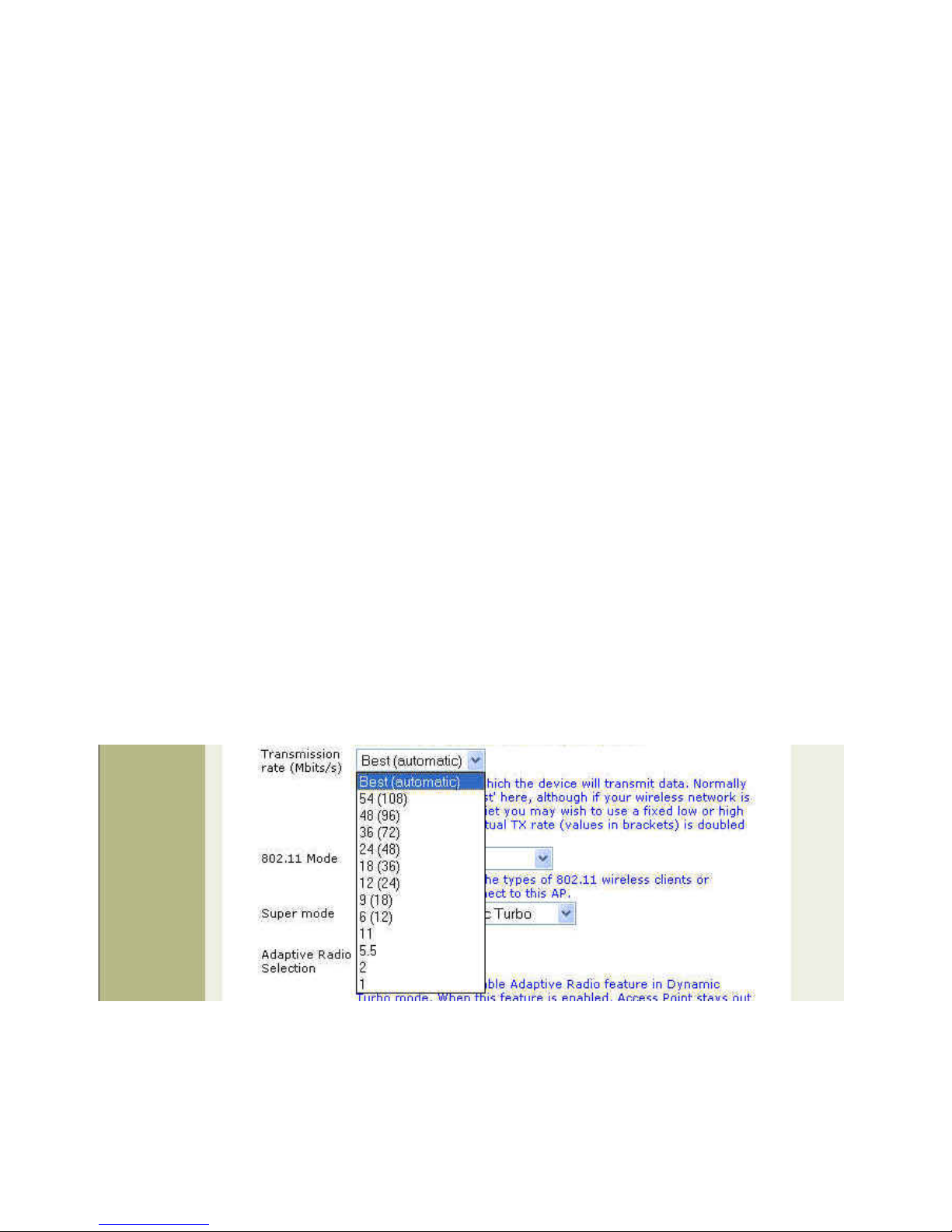
3.4.5 Transmission rate (Mbits/s)
This option indicates the transmission rate of theAP/WDS (Bridge).The Transmission rate is the rate at which the
access point transmits uni-cast packets on the wireless interface. The maximum transmission distance is
affected by the data rate. The lower the data rate, the longer the transmission distance. (Options: Best
(automatic), 54 (108), 48( 96), 36 (72), 24 (48), 18 (36), 12 (24), 9 (18), 6 (12), 11, 5.5, 2, 1 Mbps; Default : Best
(automatic).
3.4.6 802.11 Mode
This setting controls the types of 802.11 wireless clients or stations that can connect to this AP. The wireless
mode allows the user to select whether thisAP will connect to an 802.11b only network, an 820.11g only network,

13
an both 820.11b/g network on an 802.11a only network. The Default setting is 802.11a only.
3.4.7 Super Mode
Super mode is supported when the AP is using Atheros radio card. The normal 802.11a and 802.11g wireless
operation mode provides connections up to 54Mbps. Turbo mode is an enhanced mode (not regulated in IEEE
802.11a and 802.11g) that provides a higher data rate of up to 108Mbps. Enabling Turbo Mode allows the
wireless bridge to provide connections up to 108Mbps. (Default: Super A/G with Dynamic Turbo)
Super Mode Function
Disabled Standard 802.11a/g does NOT support enhanced capabilities.
Super A/G without Turbo Capable of Packet Bursting, Fast Frames, Compression, No Turbo Mode
Super A/G with Static Turbo Capable of Packet Bursting, Fast Frames, Compression, and Static Turbo Mode.
This setting is not backwards compatible with non-Turbo (legacy) devices. Static
turbo mode is always on and is only enabled when all devices on the wireless
network are configured with Super A/G and Static Turbo enabled.
Super A/G with Dynamic Turbo Capable of Packet Bursting, Fast Frames, Compression and Dynamic Turbo
Mode. This setting is backwards compatible with non-Turbo (legacy) devices.
Dynamic Turbo mode is only enabled when all devices on the wireless network
are configured with Super A/G and Dynamic Turbo enabled.
3.4.8 Adaptive Radio Selection
Check this box to enableAdaptive Radio feature in Dynamic Turbo mode. When this feature is enabled, Access
Point stays out of turbo mode whenever it detects any non-turbo traffic on adjacent channels. (Default: Enable)
3.4.9 Auto Channel Select
This is to enable the wireless AP/Bridge to automatically select an unoccupied radio channel or the best channel
at start up. This may take up to 20 seconds and no clients will be able to associate during this period. (Default:
Enable)
14
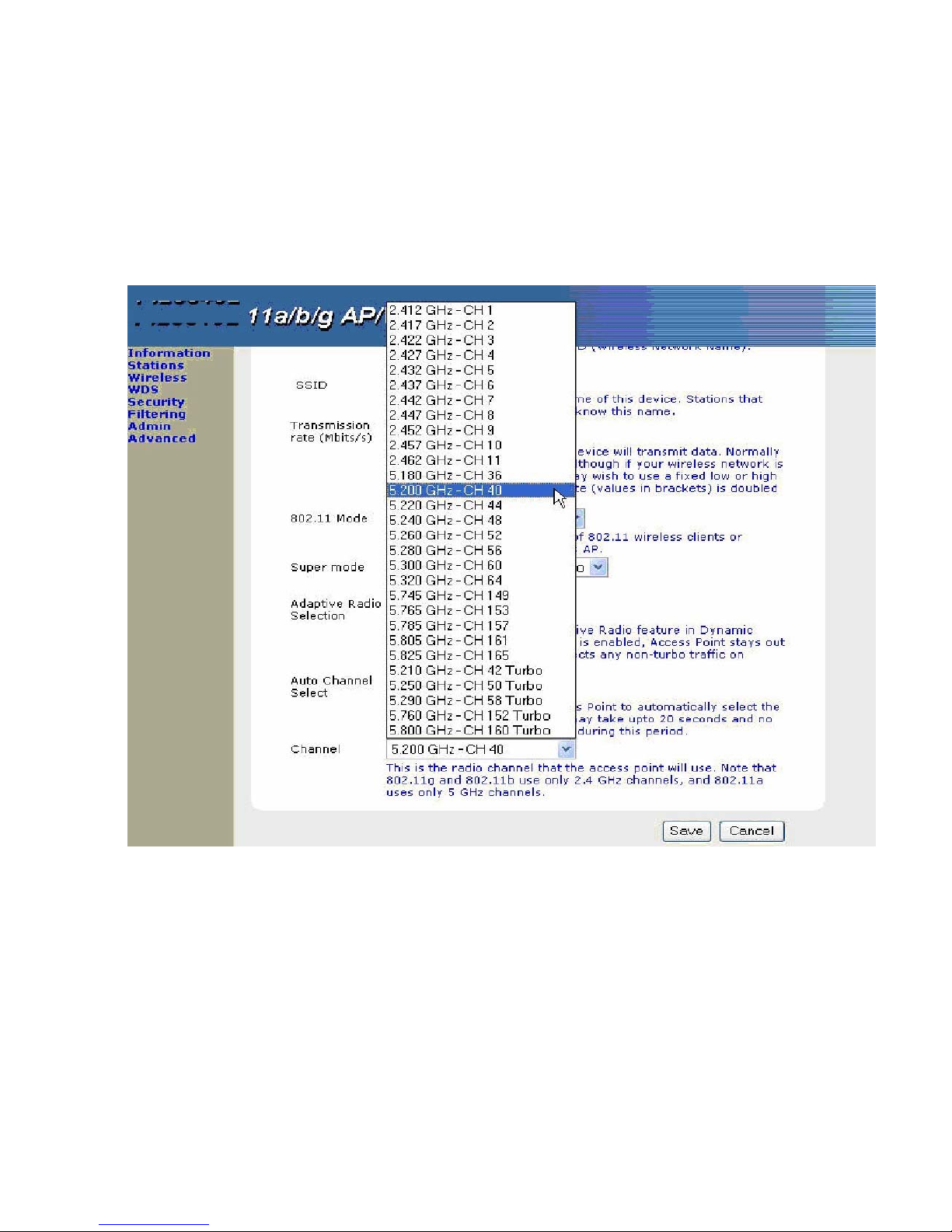
3.4.10 Channel
This is the radio channel that theAccess Point will use which represents a narrow band of radio frequency. It is
important that the frequencies do not overlap to impact the data packets transmission quality. To avoid
interference within the network with multiple APs, set each AP to use one of the 3 channels (e.g. channel 1) and
then the other AP to be one of the other 2 channels (e.g. channel 5 or channel 10). Note that 802.11b and
802.11g use only 2.4 GHz channels and 802.11a only 5.0 GHz channels. All devices on the network must share
the same channel. (Default: 5.200 GHz – CH40 for 802.11a)
15
802.11b/g Channel Frequency Ranges : 2.4 GHz – 2.497 GHz
Americas : Wireless Channels 1-11
Asia : Wireless Channels 1-14
Europe : Wireless Channels 1-13
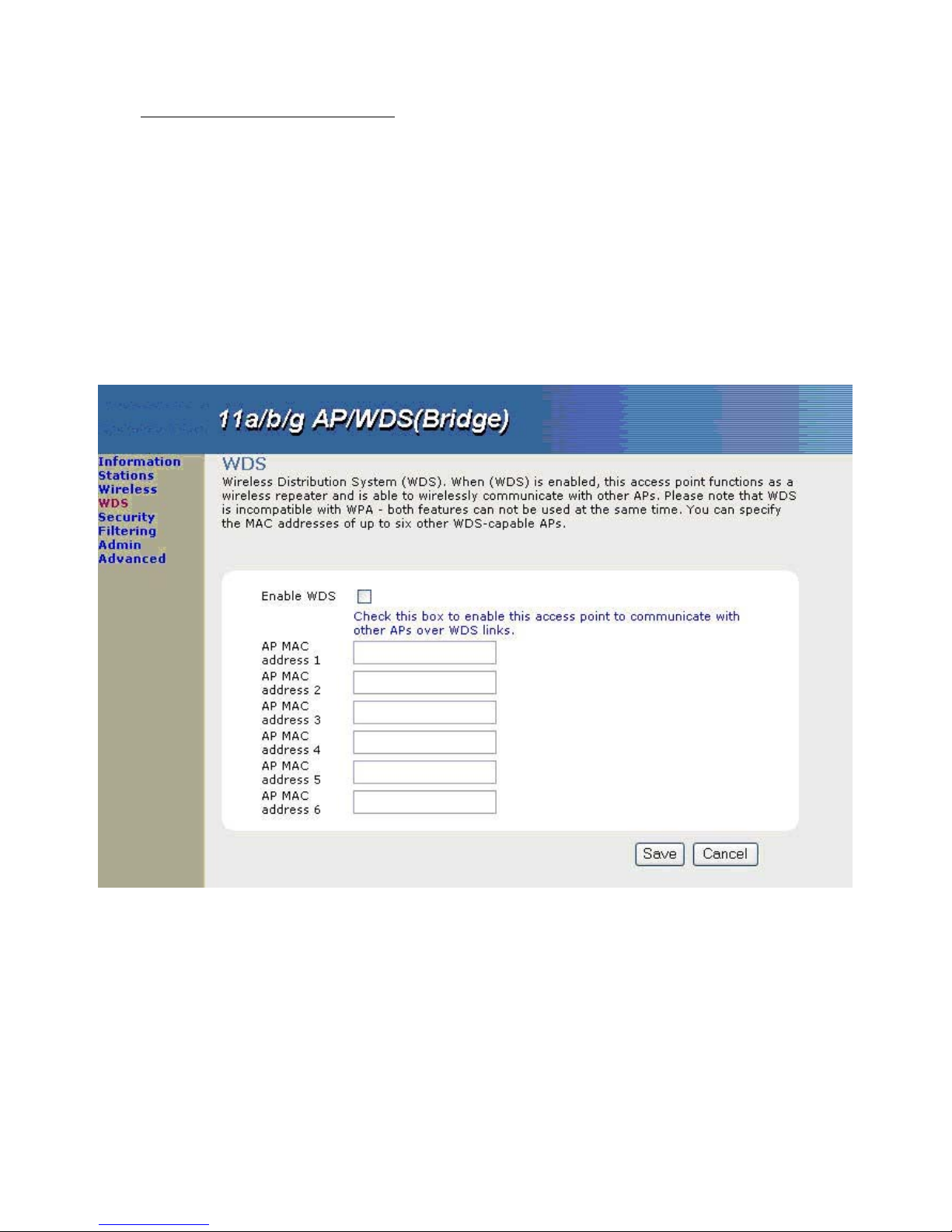
3.5 WDS
Wireless Distribution System (WDS), when (WDS) is enabled, this Access Point functions as a wireless bridge and is
able to wirelessly communicate with other Access Points. Please note that WDS is incompatible with WPA – both
features cannot be used at the same time. After entering all necessary information, please click [Save] for completing
setting.
3.5.1 Enable WDS
Check this box to enable this access point to communicate with other Access Points over WDS links, as a Bridge.
(Default: Disable)
3.5.2 AP MAC Address
Enter the MAC address of theAccess Points in your network that will serve as bridges to wirelessly connect
multiple networks. Your can specify the MAC addresses of up to six other WDS/capableAccess Points.

16
3.6 Security Setup
If you wish to use encryption for your 802.11g and 802.11a network, the BOSSW76 offers WEP and WPA
security. By default the encryption is disabled. You can change the encryption settings for more secure wireless
communication from Security and Encryption settings web page. After entering all figures, please click [Save] to
complete the setting.
3.6.1 WPA Configuration
Over the WEP, WPA improves the data encryption through the temporal key integrity protocol (TKIP). TKIP
scrambled the keys using a hashing algorithm and, by adding an integrity-checking feature, ensures that the keys
haven’t been tampered with.
WEP regulates access to a wireless network based on a computer’s hardware-specific MAC address, which is
relatively simple to be sniffed out and stolen. EAP is built on a more secure public-key encryption system to ensure
that only authorized network users can access the network.
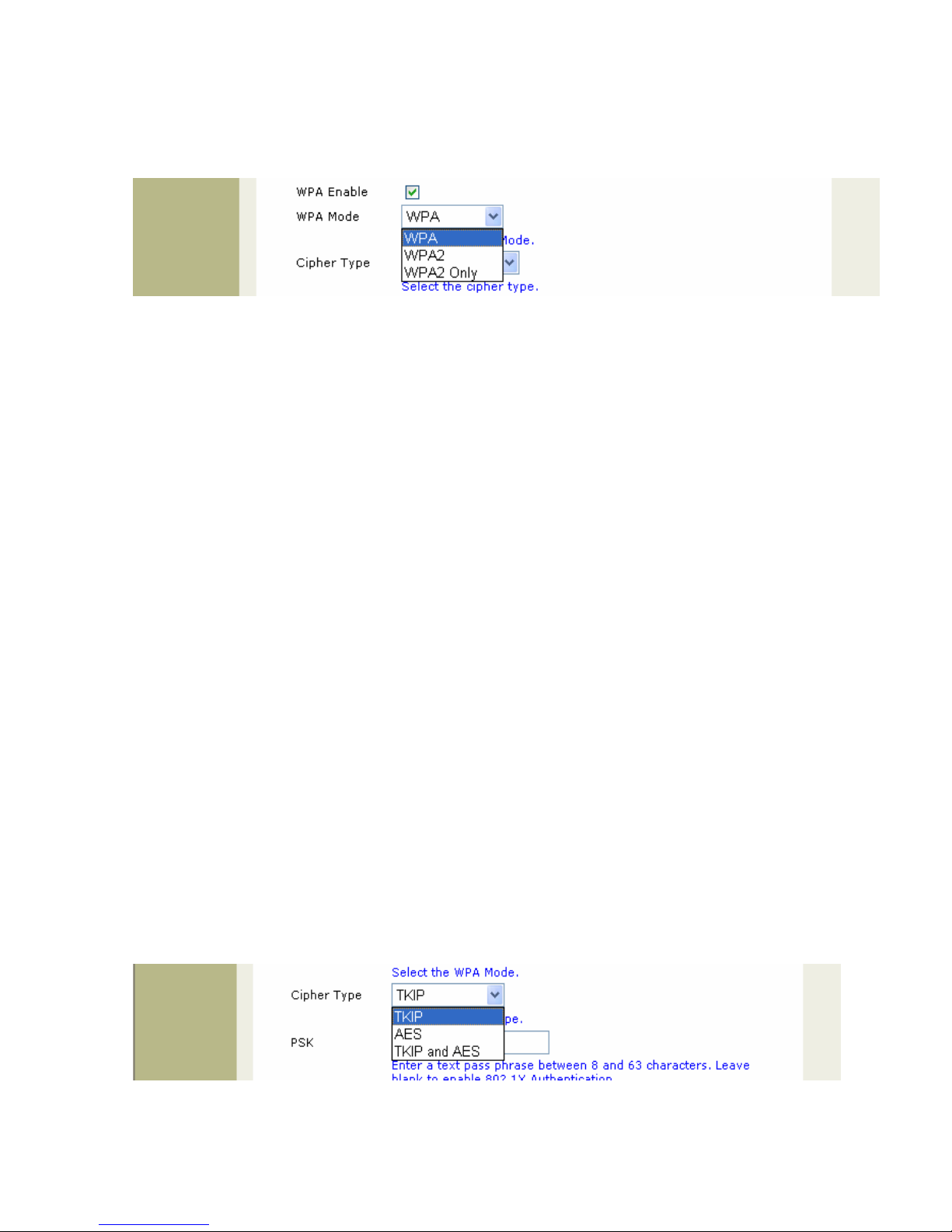
3.6.1.1 WPA Enable
Enable WPAAuthenticator to require stations to use high grade encryption and authentication. (Default: Disable)
Note : any client, that does not support the WPA standard, could not be able to authenticate with WPA enabled.
17
3.6.1.2 WPA Mode
Select the WPA Mode. (Default: WPA)
- WPA :
WPA addresses all known vulnerabilities in WEP, the original, less secure 40 or 104-bit encryption scheme
in the IEEE 802.11 standard. WPA also provides user authentication, since WEP lacks any means of
authentication. Designed to secure present and future version of IEEE 802.11 devices, WPA is subset of the
802.11i specification. WPA replaces WEP with a strong new encryption technology called Temporal Key
Integrity Protocol (TKIP) with Message Integrity Check (MIC). It also provides a scheme of mutual
authentication using either IEEE 802.11x / Extensible Authentication Protocol (EAP) authentication or
pre-shared key (PSK) technology. It can be implemented immediately and inexpensively as a software or
firmware upgrade to most existing Wi-Fi CertifiedAccess points and client Devices with minimal degradation
in network performance. WPA offers standards-based, Wi-Fi Certified security. It assures users that the
Wi-Fi certified devices they buy will be cross-vendor compatible. When properly installed, WPA provides a
high level of assurance to enterprises, small businesses and home users that data will remain protected an
that only authorized users may access their networks.
- WPA2 :
WPA2 is the second generation of WPAsecurity; providing enterprise and consumer WiFi users with a high
level of assurance that only authorized users can access their wireless networks. WPA2 is the certified
interoperable version of the full IEEE 820.11i specification. Like WPA, WPA2 supports IEEE 802.11x / EAP
authentication or PSK technology. It also included a new advanced encryption mechanism using the
Counter-Mode / CBC-MAC Protocol (CCMP) called the Advanced Encryption Standard (AES).
3.6.1.3 Cipher Type
If you selected EAP you will need to select the cipher type for TKIP, AES or Auto. (Default: TKIP)
Note: When you select WPA, WPA2 or WPA2 only, you must select TKIP, AES, or Auto from the pull-down
menu.

18
- TKIP : Temporal Key Integrity Protocol is an upgrade to the WEP known as WEP 1.1 that fixed unknown
security problems in WEP’s implementation of the RC4 stream cipher. TKIP scrambled the keys using a
hashing algorithm and, by adding an integrity-checking feature, ensures that the keys haven’t been tampered
with.
- AES : Advanced Encryption Standard is the U.S. government’s next-generation cryptography algorithm, which
will replace DES and 3DES.AES works at multiple network layers simultaneously and support 128, 192 and
256 bit keys.
- TKIP and AES : If clients support both the TKIP and AES standards, then this would be the strongest cipher
type to use and combine both the TKIP and AES security.
3.6.1.4 PSK
PSK is the pre-shared key mode of WPAwhich does not require the inclusion of a RADIUS server in your
network. The user needs to enter a pass phrase in this field. The pass phrase is an alpha-numeric password
between 8 and 63 characters long. The password can include symbols (!?*&_) and spaces. Make sure you enter
key exactly the same on all other wireless clients. Leave blank to enable 802.1X Authentication. (Default:
password)
3.6.1.5 WPA Group Key Update Interval
Select the interval during which the group key will be valid and user need to enter a figure in this field. The default
value of 3600 is recommended.
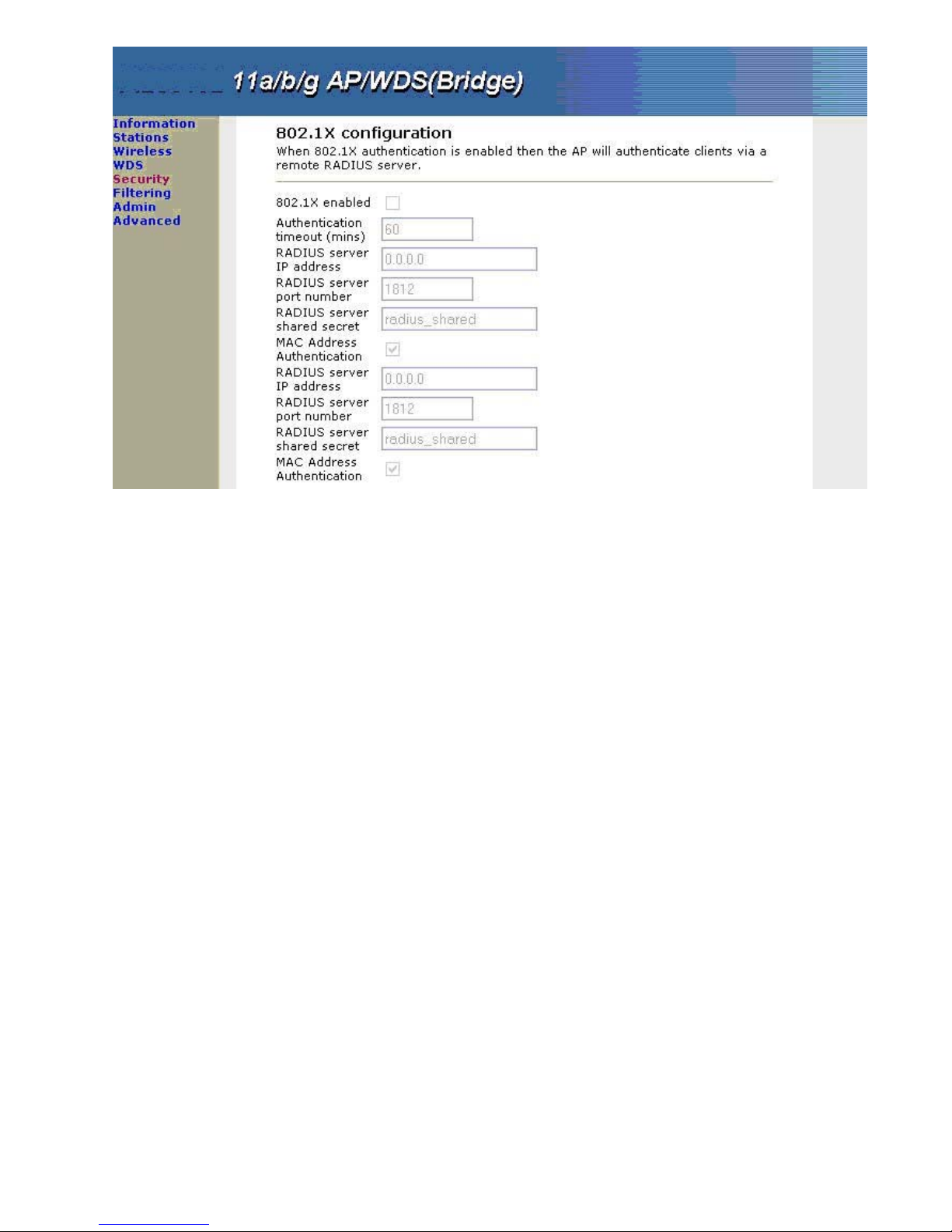
3.6.2 802.1X Configuration
IEEE 802.1x is a standard framework for network access control that uses a central RADIUS server for user
authentication. This control feature prevents unauthorized access to the network by requiring an 802.1x client
application to submit user credentials for authentication. The 802.1x standard uses the ExtensibleAuthentication
Protocol (EAP) to pass user credentials (digital certificates, user names and passwords, or other) from the client to
the RADIUS server. Client authentication is then verified on the RADIUS server before the access point grants
client access to the network. Only the Access Point could work with 802.1x standard with the RADIUS Server.
19
3.6.2.1 802.1X enable:
You can enable 802.1x as optionally supported or as required to enhance the security of the wireless network.
(Default: Disable)
3.6.2.2 Authentication timeout (mins)
Within this time, Default: 60
3.6.2.3 RADIUS server IP address
Enter the IP address of the Radius server. (Default: 0.0.0.0)
3.6.2.4 RADIUS server port number
Enter the Radius port on your AP dedicated to the RADIUS server. (Default: 1812)
3.6.2.5 RADIUS server shared secret
Enter the Radius secret phrase. (Default: radius_shared)
3.6.2.6 MAC Address Authentication
Default: Enable.
20
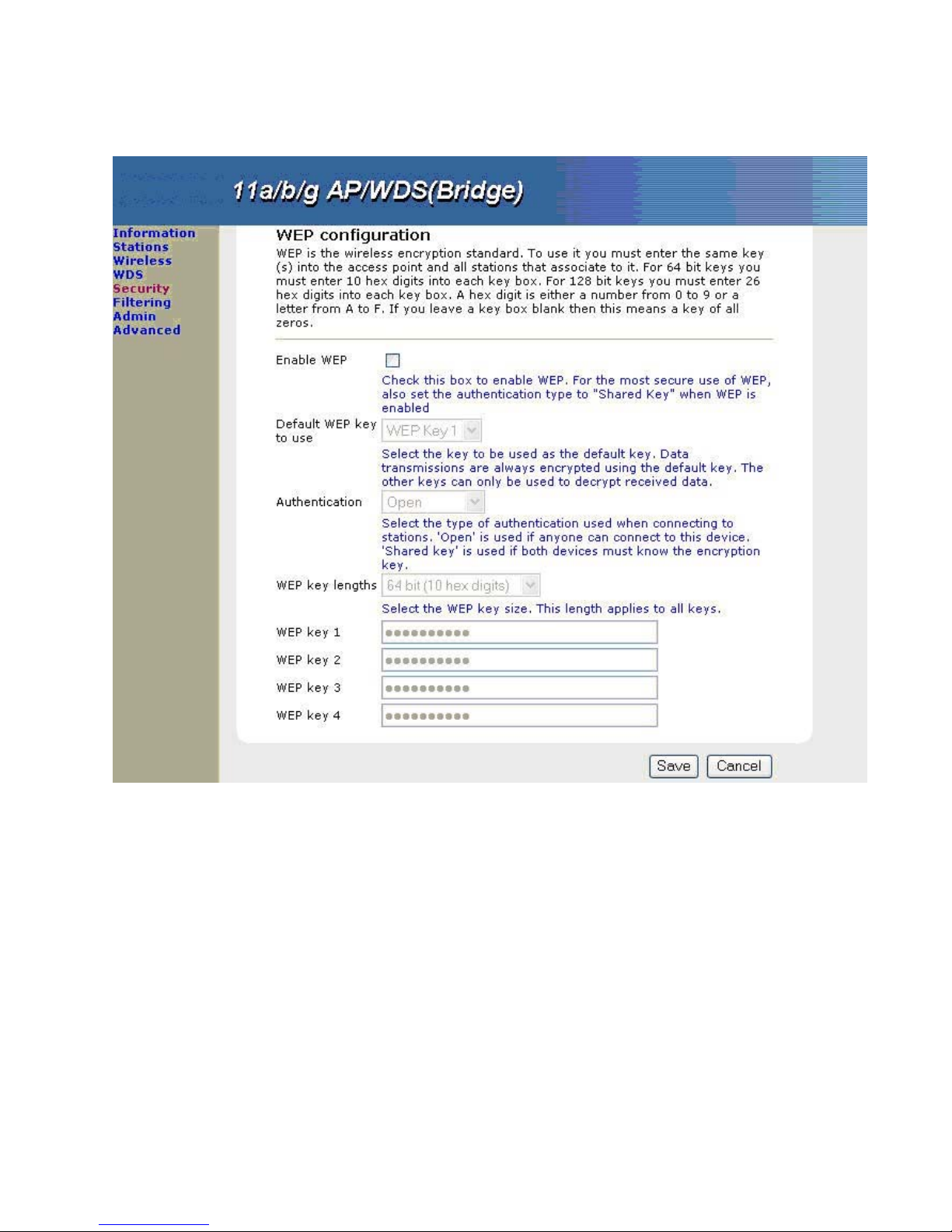
3.6.3 Wire Equivalent Privacy (WEP) Configuration
WEP provides a basic level of security, preventing unauthorized access to the network and encrypting data
transmitted between wireless bridge units. WEP uses static shared keys (fixed-length hexadecimal) that are
manually configured on all units in the wireless bridge network.
3.6.3.1 Enable WEP
Enable or disable the wireless bridge to use either WEP for data encryption. If WEP encryption is selected and
enabled, you must configure at least one encryption key on the wireless bridge. (Default: Disable)
3.6.3.2 Default WEP key to use
Select the key 1-4 to be used as the default key. Data transmissions are always encrypted using the default key.
The other keys can only be used to decrypt received data. (Default: WEP Key 1)
Table of contents
Other Bosslan Network Router manuals
Popular Network Router manuals by other brands

UTT
UTT N518W manual

Imagine communications
Imagine communications Platinum PM-FR-5 Installation and operation manual

Comtech EF Data
Comtech EF Data Vipersat CDD-562L user guide

BinTec
BinTec BinGO Plus Getting started

Teldat
Teldat Regesta Smart PRO installation manual

Juniper
Juniper M-Series Monitoring and troubleshooting guide