Chainway R6 User manual

SHENZHEN CHAINWAY INFORMATION TECHNOLOGY CO.,LTD
UHF Sled Reader
R6 User Manual

1
Content
Content..........................................................................................1
Statement..........................................................................................3
Chapter 1 Product intro.....................................................................4
1.1 Intro.....................................................................................4
1.2 Precaution before using battery...........................................5
1.3 Charger...............................................................................6
1.4 Notes................................................................................... 7
Chapter 2 Installation instructions......................................................8
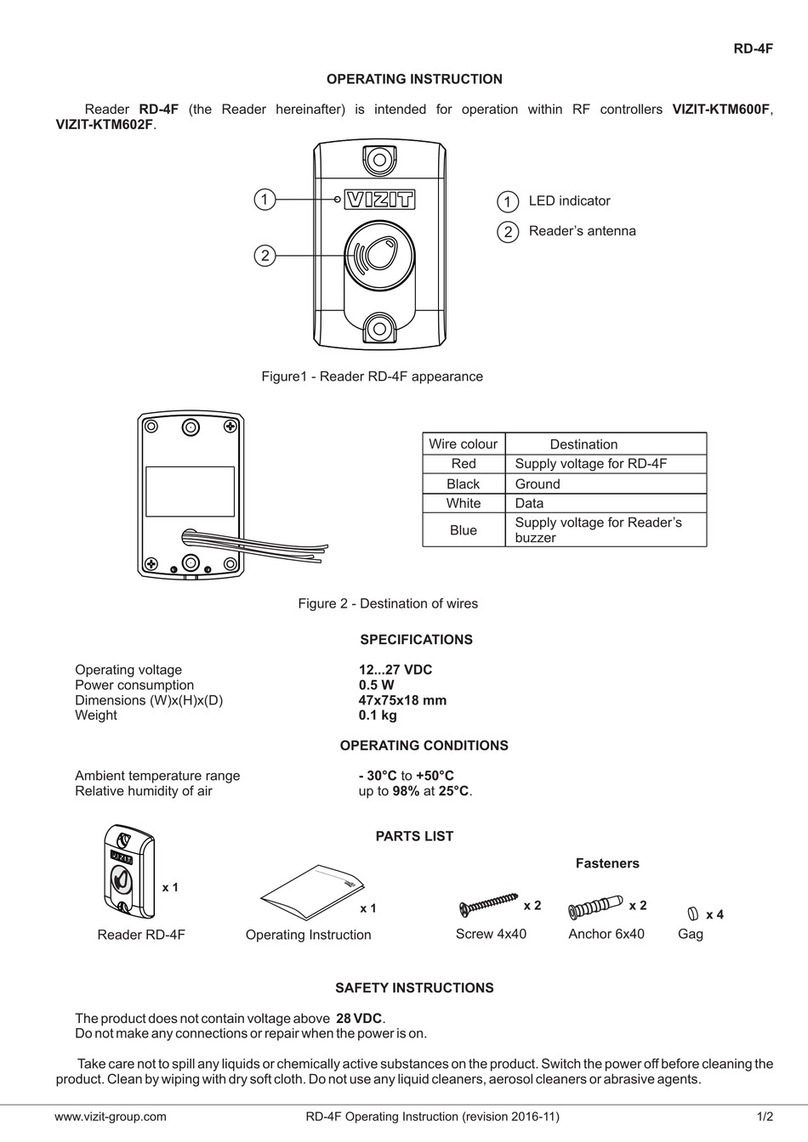
2.1 Appearance.............................................................................8
2.3 Battery charge .........................................................................9
2.4 Buttons and function area display.......................................... 10
Chapter 3 Demo Test...................................................................... 11
3.1 Install demo-uhf-bt (1.0.8)...................................................... 11
3.2 Pairing Device................................................................... 12
3.3 UHF Scan Function........................................................... 14
3.4 UHF Configuration............................................................. 15
3.5 UHF Encryption................................................................. 16
3.6 UHF Tag Reading and Writing........................................... 17
3.7 UHF Tag Lock and Kill....................................................... 18
3.8 Firmware Upgrade............................................................. 20
3.9 Barcode Scan Test............................................................ 21
Chapter 4 Device characteristic....................................................... 22

2

3
Statement
2013 by ShenZhen Chainway Information Technology Co., Ltd. All
rights reserved.
No part of this publication may be reproduced or used in any form, or
by any electrical or mechanical means, without permission written
from Chainway. This includes electronic or mechanical means, such
as photocopying, recording, or information storage and retrieval
systems. The material in this manual is subject to change without
notice.
The software is provided strictly on an “as is” basis. All software,
including firmware, furnished to the user is on a licensed basis.
Chainway grants to the user a non-transferable and non-exclusive
license to use each software or firmware program delivered
hereunder (licensed program). Except as noted below, such license
may not be assigned, sublicensed, or otherwise transferred by the
user without prior written consent of Chainway. No right to copy a
licensed program in whole or in part is granted, except as permitted
under copyright law. The user shall not modify, merge, or incorporate
any form or portion of a licensed program with other program
material, create a derivative work from a licensed program, or use a
licensed program in a network without written permission from
Chainway.
Chainway reserves the right to make changes to any software or
product to improve reliability, function, or design.
Chainway does not assume any product liability arising out of, or in
connection with, the application or use of any product, circuit, or
application described herein.
No license is granted, either expressly or by implication, estoppel, or
otherwise under any Chainway intellectual property rights. An implied
license only exists for equipment, circuits, and subsystems contained
in Chainway products.

4
Chapter 1 Product intro
1.1 Intro
This is a new UHF back clip product, featuring the Cortex-M3 STM32
processor with excellent working performance. The device can be
used with any Android and IOS device as a host. The device
combines powerful UHF (Read and write) functions with 2D scanning
for greater sensitivity. It equipped with a host is widely used in
clothing inventory, warehouse management, vehicle management,
financial management and other fields.

5
1.2 Precaution before using battery
Do not leave battery unused for long time, no matter it is in
device or inventory. If battery has been used for 6 months
already, it should be check for charging function or it should be
disposed correctly.
The lifespan of Li-ion battery is around 2 to 3 years, it can be
circularly charged for 300 to 500 times. (One full battery charge
period means completely charged and completely discharged.)
When Li-ion battery is not in used, it will continue discharge
slowly. Therefore, battery charging status should be checked
frequently and take reference of the related battery charging
information on the manuals.
Observe and record the information of a new unused and non-
fully charged battery. On the basis of operating time of new
battery and compare with a battery that has been used for long
time. According to product configuration and application
program, the operating time of battery would be different.
Check battery charging status at regular intervals.
When battery operating time drops below about 80%, charging
time will be increased remarkably.
If a battery is stored or otherwise unused for an extended
period, be sure to follow the storage instructions in this
document. If you do not follow the instructions, and the battery
has no charge remaining when you check it, consider it to be
damaged. Do not attempt to recharge it or to use it. Replace it
with a new battery.
Store the battery at temperatures between 5 °C and 20 °C
(41 °F and 68 °F).

6
1.3 Charger
The charger type is GME10D-050200FGu, output voltage/current is
5V DC/2A. The plug considered as disconnect device of adapter.

7
1.4 Notes
Note:
Using the incorrect type battery has danger of explosion.
Please dispose the used battery according to instructions.
Note:
Due to the used enclosure material, the product shall only be
connected to a USB Interface of version 2.0 or higher. The
connection to so called power USB is prohibited.
Note:
The adapter shall be installed near the equipment and shall be
easily accessible.
Note:
The suitable temperature for the product and accessories is 0-10℃
to 50℃.
Note:
CAUTION RISK OF EXPLOSION IF BATTERY IS REPLACED BY
AN INCORRECT TYPE. DISPOSE OF USED BATTERIES
ACCORDING TO THE INSTRUCTIONS.

8
Chapter 2 Installation instructions
2.1 Appearance
R6 right and front appearances are showing as follows:
Indicating Lamps instruction
Lamps
Description
Indicating
Lamps
Power
Constant light up (battery available)/Flash (Low battery)
Bluetooth
Constant light up (Bluetooth connected)
Work
Flash when read UHF tags

9
2.2 Battery charge
By using USB contact, the original adaptor should be used for
charging the device. Make sure not to use other adaptors to charge
the device.
Table of contents