Table of Contents
1 Introduction ..........................................................................................................1
2 Network Connection.............................................................................................2
2.1LAN ……………………………………………………………………………..........2
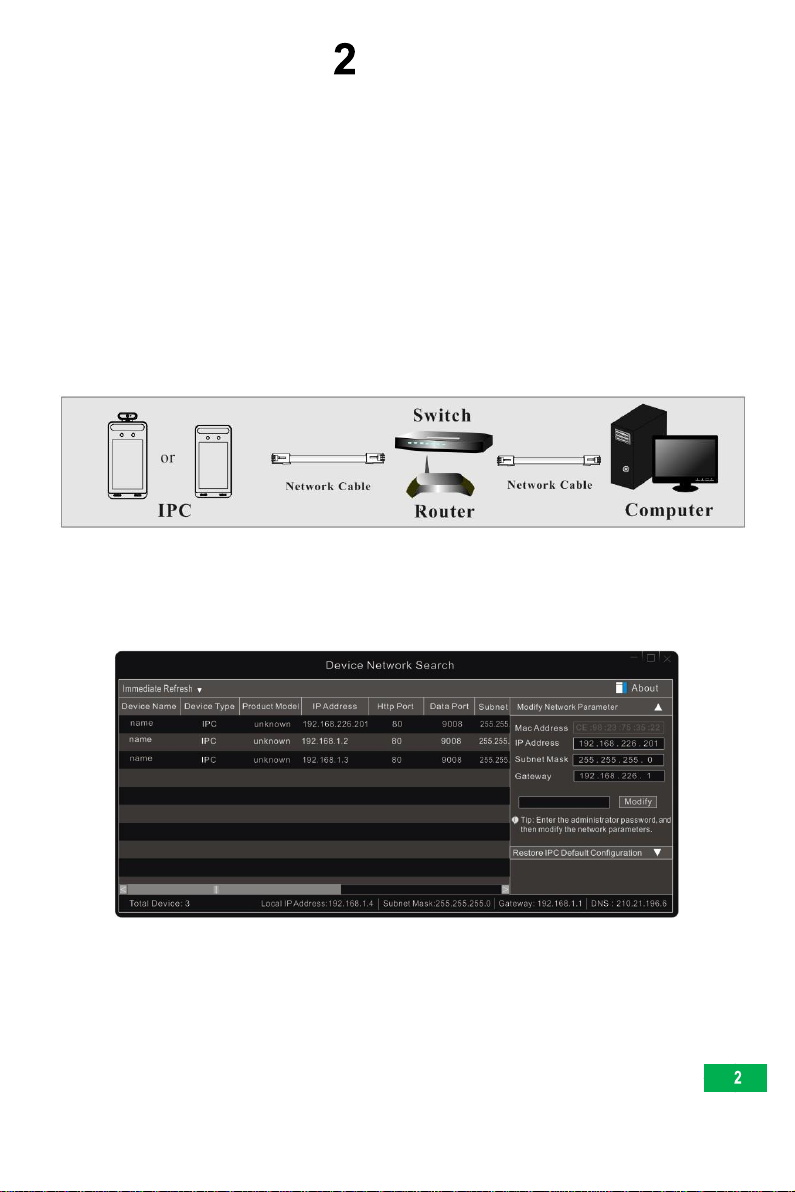
2.1.1Access through IP-Tool................................................................................2
2.1.2Directly Access through IE...........................................................................4
2.2WAN ……………………………………………………………………….. .............5
3 Temperature Measurement & Face Recognition Configuration ............................9
3.1Temperature Measurement Settings................................................................9
3.2Face Match Configuration ..............................................................................10
3.3Face Database Management.........................................................................11
3.4Mask Detection...............................................................................................12
4 Live View.................................................................................................................14
4.1Temperature Measurement & Face Recognition View.....................................14
4.1.1Temperature Measurement Requirements.................................................14
4.1.2Temperature Measurement & Face Recognition View.................................15
4.2Live Viewvia Web..........................................................................................................16
5 Access Control Settings.....................................................................................19
5.1Door Lock Settings.........................................................................................19
5.2Wiegand Settings...........................................................................................19
5.3Tampering Alarm Settings...............................................................................20
6 Other Configurations..........................................................................................21
6.1System Settings .............................................................................................21
6.1.1Basic Information .......................................................................................21
6.1.2Date and Time ...........................................................................................21
6.1.3Local Config...............................................................................................22
6.1.4Storage ......................................................................................................22
6.2Image Configuration.......................................................................................25
6.2.1Display Configuration.................................................................................25
6.2.2Video / Audio Configuration .......................................................................27
6.2.3OSD Configuration.....................................................................................28
6.2.4Screen Brightness......................................................................................29
6.2.5White Light Control.....................................................................................29
6.2.6Face Exposure...........................................................................................30
6.3Alarm Configuration........................................................................................30
6.3.1Exception...................................................................................................30
6.3.2Micro-SD card Full .....................................................................................32
6.3.3Micro-SD card Error...................................................................................32
6.3.4IPAddress Conflict.....................................................................................33