Crossmatch D SCAN AUTHENTICATOR CF User manual



Cross Match®Technologies, Inc.
D SCAN® AUTHENTICATOR CF™
Document Authentication Reader
User Manual
Version 2.1

Version 2.1 (April 2010)
Specifications are subject to change without prior notice.
Cross Match Technologies GmbH assumes no liability for maloperation or
improper use of products.
Cross Match® and D SCAN® are registered trademarks, and the CROSS
MATCH TECHNOLOGIES logo is a trademark of Cross Match
Technologies, Inc.
All other trademarks, brands and names are the property of their respective
owners and are protected by US and international copyright and trademark
laws.
No portion of this guide may be reproduced in any form or by any means
without the express written permission of Cross Match® Technologies.
© Copyright 2010, Cross Match Technologies. All rights reserved.

Basic health and safety instructions iii
Basic health and safety instructions
The D SCAN®AUTHENTICATOR CF document reader is designed,
manufactured and tested to meet international safety standards. The document
reader contains an RF transmission device, and is therefore subject to national and
international regulations. The Authenticator transmits at a frequency of 13,56
MHz. However, all electric appliances can emit spurious RF-signals at other than
the specified frequency.
To ensure safe operation of the D SCAN AUTHENTICATOR CF:
• The operator of the D SCAN AUTHENTICATOR CF must observe the
guidelines and particularly the safety precautions outlined in this document
and according to related country regulation requirements.
• You must restrict the use of the device in potentially hazardous
environments. The environments include fuel depots, chemical plants and
areas where the air contains chemicals or particles (such as grain, dust, or
metal powders). The restrictions apply in any other area where you would
normally be asked to turn off your vehicle engine.
• Transmitted radio frequency energy may interfere with some hearing aids,
pacemakers or other medical devices if the person is positioned too close to
the document reader.
• To reduce the RF exposure refer to your related country regulation
requirements. See the specifications table and the section “Magnetic field
strength” on page 4-3 for detailed information.
• Read the User Manual on the CDROM for detailed information to operate
the D SCAN AUTHENTICATOR CF.
• Turn off the document reader when not in use.
• Do not open the device. Repairs must be done by Cross Match Technologies.
Changes or modifications not expressly approved by Cross Match
Technologies could void the user's authority to operate the equipment.
Cross Match Technologies GmbH assumes no liability for the customer's failure
to comply with these requirements.

iv D SCA N ®AUTHENTICATOR CF™ User Manual v2.1

The optional coaxial light feature v
The optional coaxial light feature
The D SCAN® AUTHENTICATOR CF is a high performance device for reading
all kinds of personal identification documents such as passports and national ID
cards. Any document compliant to the specifications of the ICAO can be placed
on the glass plate on top of the device for capturing the image of the personalized
page. The optional RFID feature further provides the functionality for reading out
the contents of the digital data chip contained in the new electronic passports.
How does the optical reading of the device work?
The D SCAN AUTHENTICATOR CF device contains a built-in high resolution
camera and several sources of light. Each light source can be turned on before
taking one image with the camera. Thereby the user can take an image of the
personalized page as it appears under normal visible light or under ultraviolet
(UV) or infrared (IR) light. In the interest of a very uniform intensity level of the
light on the document page being captured the light sources are arranged in a way
to provide a diffuse kind of light rather than a directed light under a specific angle.
This is also helpful to avoid reflections. After the image was taken by the build-in
camera it is being transferred through the USB 2.0 interface cable to the PC. The
software belonging to the D SCAN AUTHENTICATOR CF receives the image
and makes it available through the Application Programming Interface (API).
Thereby the image becomes accessible for the application software of the system
integrator.
Among the available options is the "coaxial light" feature. This is an illumination
which works similar to the other ones but delivers its light under the same angle as
the camera view angle to the document. Thereby camera and illumination are
arranged on the same axis - or coaxially, hence the name.
Which functionality does the coaxial light feature
provide?
This optional feature provides the functionality of turning the coaxial illumination
on while all other illuminations are off, taking one image with the camera, turning
the coaxial illumination off, and making the captured image available as a digital
bitmap via the API to the application software of the system integrator. The
application can then take this image and display it on the screen of the PC so that
the operator can view it.

vi D SC A N ®AUTHENTICATOR CF™ User Manual v2.1
A personalized page of a document covered with a protective laminate may show
certain retro reflective patterns when viewed with the coaxial illumination. When
viewed with one of the diffuse illuminations the same page will not show the retro
reflective pattern. Thereby the existence of such a laminate can be checked
visually.
The coaxial light product feature of the D SCAN AUTHENTICATOR CF does
not provide any kind of image processing or image analysis e.g. intended for the
automatic detection of tampering and alteration of documents having security
laminates such as the 3M™ Confirm™ Laminates.
Cross Match Technologies does not provide any product option or product
extension or separate product for performing such kind of automatic detections.
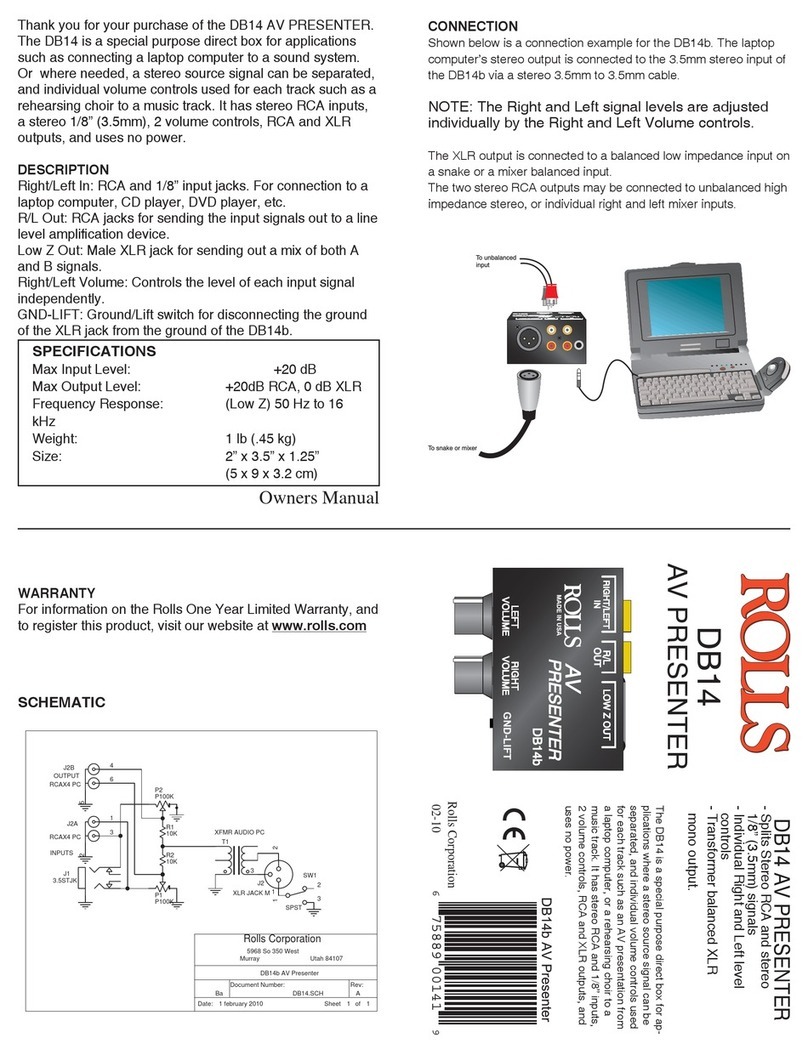
Image captured with an D SCAN AUTHENTICATOR CF under coaxial light
showing a document having a 3M™ Confirm™ Laminate on top of the
personalized page. The retro reflective marks are clearly visible while the
underlying text and pictures are almost invisible.
Notice to system integrators
System integrators shall be aware that an automatic detection of tampering
and alteration of documents having security laminates is the subject of a
technical invention filed by Minnesota Mining and Manufacturing Co. and
published as patent in the following countries: AU 685830, CA 2173230, DE
69418 887 T2, ES 2133583 T3, FR 0722597, GB 0722597, HK 1013873, IT
0722597, JP 09504629 T2, KR 0354883 B, US 6019287, US 6611612, and US
publication 2004-022420 A1.

The optional coaxial light feature vii
Disclaimer
Cross Match Technologies explicitly reminds the integrators of the D SCAN
AUTHENTICATOR CF of the existence of the above mentioned patents. The use
of the D SCAN AUTHENTICATOR CF for reading documents with the coaxial
light is authorized by Cross Match Technologies only for the purpose of taking the
image without any kind of image processing for the automatic detection of
tampering and alteration. Cross Match Technologies shall not be liable for any
violation of the rights and claims of the patents mentioned above. System
integrators and end users interested in performing such automatic detection shall
consider to contact the owner of the above mentioned patents for a potential
licensing.
This document applies to each D SCAN AUTHENTICATOR CF device if it is
equipped with the coaxial lighting feature option (CX2). System integrators and
resellers must provide this document to the end user.
Cross Match Technologies GmbH assumes no liability for the customer's failure
to comply with these requirements.

viii D SCAN®AUTHENTICATOR CF™ User Manual v2.1

Contents ix
Contents
Basic health and safety instructions ....................................................0-iii
The optional coaxial light feature ........................................................ 0-v
How does the optical reading of the device work? ............................. 0-v
Which functionality does the coaxial light feature provide? ................. 0-v
Notice to system integrators ......................................................... 0-vi
Disclaimer ..................................................................................0-vii
Introduction
Appropriate Operation ...................................................................... 1-1
Who should read this book ................................................................1-1
How this book is arranged ................................................................. 1-1
Standards ....................................................................................... 1-2
FCC statement ................................................................................. 1-2
Industry Canada .............................................................................. 1-3
Statement of Compliance ..................................................................1-3
Recycling information ....................................................................... 1-3
WEEE Directive ................................................................................ 1-3
Safety when operating ......................................................................1-4
Glossary ......................................................................................... 1-4
Installation
D SCAN AUTHENTICATOR CF .............................................................2-1
Front view ................................................................................... 2-2
Top of the document reader ...........................................................2-3
Ambient light cover ...................................................................2-4
Back view .................................................................................... 2-5
Product label ............................................................................ 2-6
System requirements ....................................................................... 2-6
Operating system ......................................................................... 2-7
Hardware .................................................................................... 2-7
Installation ...................................................................................... 2-7
Remove the contents ....................................................................2-7
List of contents ............................................................................2-7
Prepare to use ............................................................................. 2-7
Connect the Authenticator CF .........................................................2-8
Attach the Authenticator CF to a surface ............................................. 2-9
Prepare the installation .................................................................2-9

x D SCAN®AUTHENTICATOR CF™ User Manual v2.1
Installation ...................................................................................2-9
How to use the Authenticator CF
Applications and software levels .........................................................3-1
Characteristics of documents ..............................................................3-2
The machine readable zone ............................................................3-3
Align the documents ......................................................................3-3
Read in a document ..........................................................................3-4
The Overview page .......................................................................3-5
The camera pictures page ..............................................................3-8
The images page ..........................................................................3-9
The RFID data groups page ..........................................................3-10
The barcode page .......................................................................3-11
The RFID check results page .........................................................3-12
The options page ........................................................................3-13
Global result settings ...............................................................3-13
Workflow settings ....................................................................3-14
Barcodes to read .....................................................................3-14
Glare reduction mode settings ...................................................3-14
Maintenance
Cleaning ..........................................................................................4-1
Clean the document contact area ....................................................4-1
Clean the case ..............................................................................4-2
Authenticator CF specifications ...........................................................4-2
Magnetic field strength ......................................................................4-3
Problems and Corrections
The Authenticator does not work .....................................................5-1
Authenticator disconnected during operation .....................................5-1
Initialization failed .........................................................................5-2
Dark image sections ......................................................................5-2
Visualization and processing speed too slow .....................................5-2
Creating a problem report ..............................................................5-3
Customer Care and Contact Information
Technical Support .............................................................................6-1
E-mail .........................................................................................6-1
Telephone and facsimile .............................................................6-1
Return and repair of the Authenticator CF ........................................6-2
Delivery costs ..................................................................................6-3
The product is in the warranty period ...........................................6-3
Customers inside the EU .........................................................6-3

Contents xi
The product is not in the warranty period .....................................6-3
Contact information ..........................................................................6-3
Corporate Headquarters .............................................................6-3
Corporate Web Page .............................................................. 6-3
Product Warranty
Limited Warranty .............................................................................7-1
Repair or Replacement ..................................................................7-1
Limitations ..................................................................................7-2
Out-of-Warranty Repairs ...............................................................7-3
Index

xii D SCAN®AUTHENTICATOR CF™ User Manual v2.1

xiii
Figures
Figure 2.1: DSCAN AUTHENTICATOR CF front view .................................... 2-2
Figure 2.2: DSCAN AUTHENTICATOR CF instruction label ............................ 2-2
Figure 2.3: Top view of the DSCAN AUTHENTICATOR CF .............................................2-4
Figure 2.4: Ambient light cover positions ..........................................2-5
Figure 2.5: DSCAN AUTHENTICATOR CF back view .................................... 2-5
Figure 2.6: DSCAN AUTHENTICATOR CF product label ................................ 2-6
Figure 2.7: DSCAN AUTHENTICATOR CF connection box ............................. 2-8
Figure 2.8: Place the drill template .................................................. 2-9
Figure 2.9: Remove rubber feet .................................................... 2-10
Figure 2.10: Mount points ............................................................. 2-10
Figure 2.11: Fasten the Authenticator CF ......................................... 2-11
Figure 3.1: The machine readable zone ............................................3-3
Figure 3.2: Instruction label on the cover .........................................3-3
Figure 3.3: Positioning of a passport ................................................ 3-4
Figure 3.4: Launching application .................................................... 3-5
Figure 3.5: Message about missing background images ...................... 3-5
Figure 3.6: Processing information .................................................. 3-6
Figure 3.7: Overview data page ...................................................... 3-6
Figure 3.8: Failed verification ......................................................... 3-7
Figure 3.9: Camera pictures page ................................................... 3-8
Figure 3.10: Images page ............................................................... 3-9
Figure 3.11: RFID data groups page ............................................... 3-10
Figure 3.12: Barcode page ............................................................. 3-11
Figure 3.13: RFID check results page .............................................. 3-12
Figure 3.14: Options page ............................................................. 3-13
Figure 4.1: Clean the document contact area .................................... 4-1
Figure 4.3: Magnetic field strength lateral ........................................ 4-3
Figure 4.4: Magnetic field strength frontal ........................................ 4-4
Figure 4.5: Magnetic field strength on top ........................................ 4-4

xiv D SCAN®AUTHENTICATOR CF™ User Manual v2.1

xv
Tables
Table 1.1: Glossary of terms ............................................................1-4
Table 2.1: Front features ................................................................. 2-3
Table 2.2: Top features ................................................................... 2-4
Table 2.3: Back features .................................................................. 2-5
Table 2.4: Illumination codes ........................................................... 2-6
Table 4.2: Product specifications ....................................................... 4-2
Table 6.1: The Technical Support department addresses ...................... 6-1
Table 6.2: The Technical Support department numbers ........................ 6-1
Table 6.3: The addresses for product returns ......................................6-2

xvi D SCAN®AUTHENTICATOR CF™ User Manual v2.1

Appropriate Operation 1-1
1
Chapter0Introduction
Appropriate Operation
The D SCAN® AUTHENTICATOR CF captures color images and reads full
pages to capture and transmit personal and document data. The device can capture
an entire data page from any ID document in different types of light. The device
can read RFID data contactless found on the RFID tag.
It is intended for the use in IT-devices area and the operation and installation must
be in connection with suitable computer equipment. When operating, the
electrical installation and cabling must comply with the IEC 60950 standard.
Who should read this book
You should read this book if you are a user and you will operate the D SCAN
AUTHENTICATOR CF document authentication reader device.
How this book is arranged
•Chapter 1 “Introduction” covers standards for the manual and describes the
safety instructions. The chapter also contains a glossary of terms.
•Chapter 2 “Installation” describes the D SCAN AUTHENTICATOR CF and
how to install the document authentication reader.
•Chapter 3 “How to use the Authenticator CF” describes how to use the
indicators on the device to capture the best quality images.
•Chapter 4 “Maintenance” explains how to maintain the
D SCAN AUTHENTICATOR CF.
•Chapter 5 “Problems and Corrections” describes the problems, causes, and
corrections.
•Chapter 6 “Customer Care and Contact Information” explains how to get
the technical support that is available from Cross Match Technologies.

1-2 D SCA N ®AUTHENTICATOR CF™ User Manual v2.1
Introduction
Standards
The following standards are used in this book:
•Bold UPPER/lower case and tilted text identify important information.
• Special information can appear as a Note, Caution, Warning, or Danger.
Note
A Note contains additional information. To ignore a note can cause a delay, but not
mechanical damage or personal injury.
Caution
A Caution contains a method to prevent data loss or damage to equipment. To ignore the
caution can cause damage or data loss.
Warning
A Warning describes an action that can cause injury or loss of life. Mechanical damage can
occur.
DANGER
A Warning describes an action or condition that causes injury or loss of life. Mechanical
damage can occur.
FCC statement
FCC ID: WO8RJ0479V2
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions:
(1) this device may not cause harmful interference, and
(2) this device must accept any interference received, including interference that
may cause undesired operation.
The power source for the AUTHENTICATOR CF must provide an output voltage
of 18 - 24 V DC. The electric current range of the power supply unit must be min.
1 A and max. 7 A. Use only power supply units that comply with the class B limits
of 47 CFR 15, Subpart B.
Note:
This equipment has been tested and found to comply with the limits for a Class B digital
device, pursuant to part 15 of the FCC Rules. These limits are designed to provide
reasonable protection against harmful interference in a residential installation.
This equipment generates, uses and can radiate radio frequency energy and, if not installed
and used in accordance with the instructions, may cause harmful interference to radio
communications. However, there is no guarantee that interference will not occur in a
particular installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off and on, the user
is encouraged to try to correct the interference by one or more of the following measures:
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circuit different from that to which the
receiver is connected.
• Consult the dealer or an experienced radio/TV technician for help.
Table of contents