Version 0.90 Page
3
of 15 06.Sep.04
1. Scenario 1: Client-to-gateway with pre-shared secrets
1.1 Scenario Setup
The following is a typical client-to-gateway VPN that uses a preshared secret for authentication.
172.23.9.0/24
|
|--
+-----------+ /-^-^-^-^--\ +-----------+ |
| Client A |=====| Internet |=====| Gateway B |-----|
+-----------+AW \--v-v-v-v-/ BW+-----------+BL |
Dynamically assigned 22.23.24.25 172.23.9.1 |--
|
Figure 1.1.1: cenario
Client A's WAN interface (AW) has the address dyna ically assigned to it by the ISP. Client A will access
Gateway B's internal LAN, by eans of a secure tunnel.
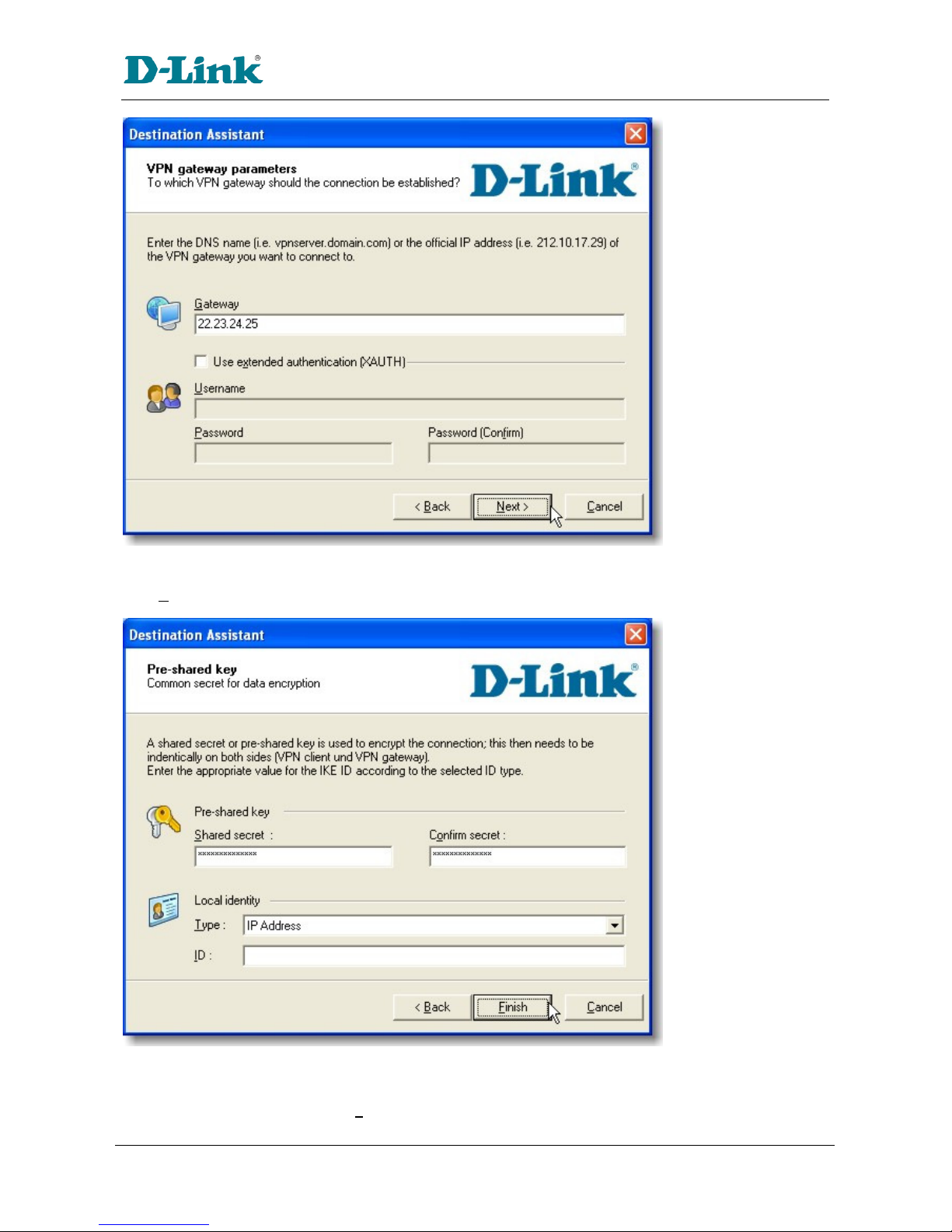
Gateway B connects the internal LAN 172.23.9.0/24 to the Internet. Gateway B's WAN (Internet)
interface has the address 22.23.24.25. Gateway B's LAN interface address, 172.23.9.1, can be used for
testing IPsec but is not needed for configuring Client A.
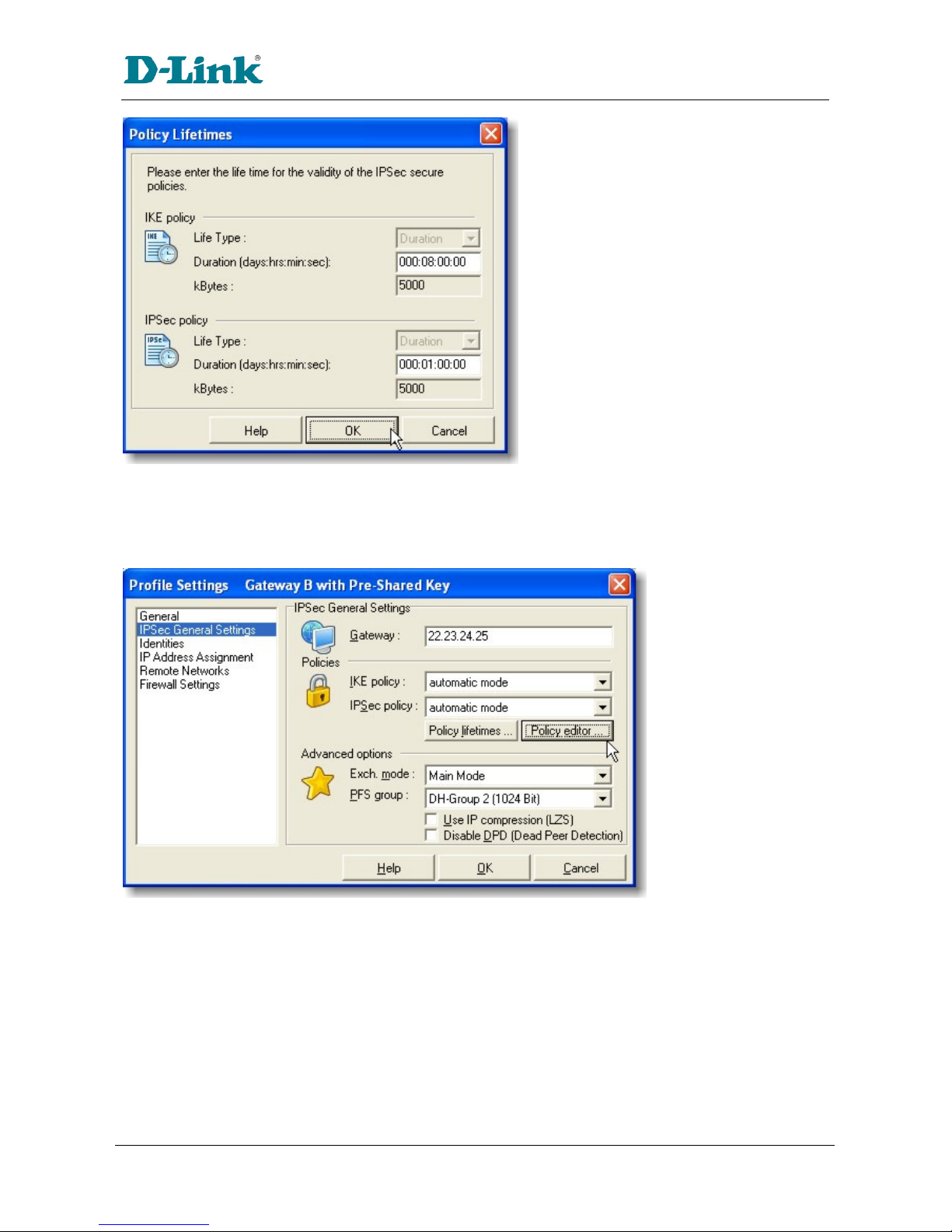
The IK Phase 1 parameters used in Scenario 1 are:
Main ode
TripleDES
SHA-1
MODP group 2 (1024 bits)
pre-shared secret of "hr5xb84l6aa9r6"
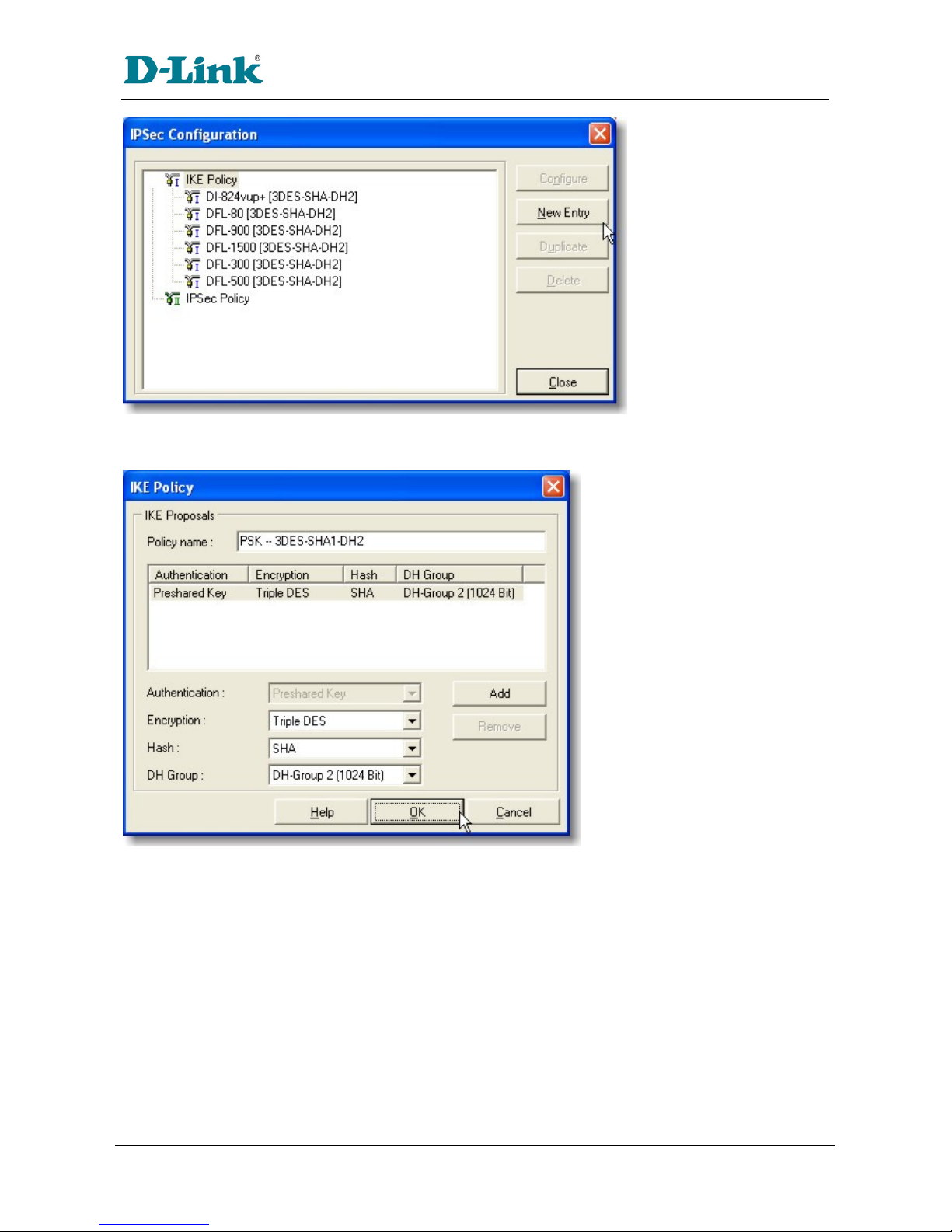
SA lifeti e of 28800 seconds (eight hours) with no kbytes rekeying
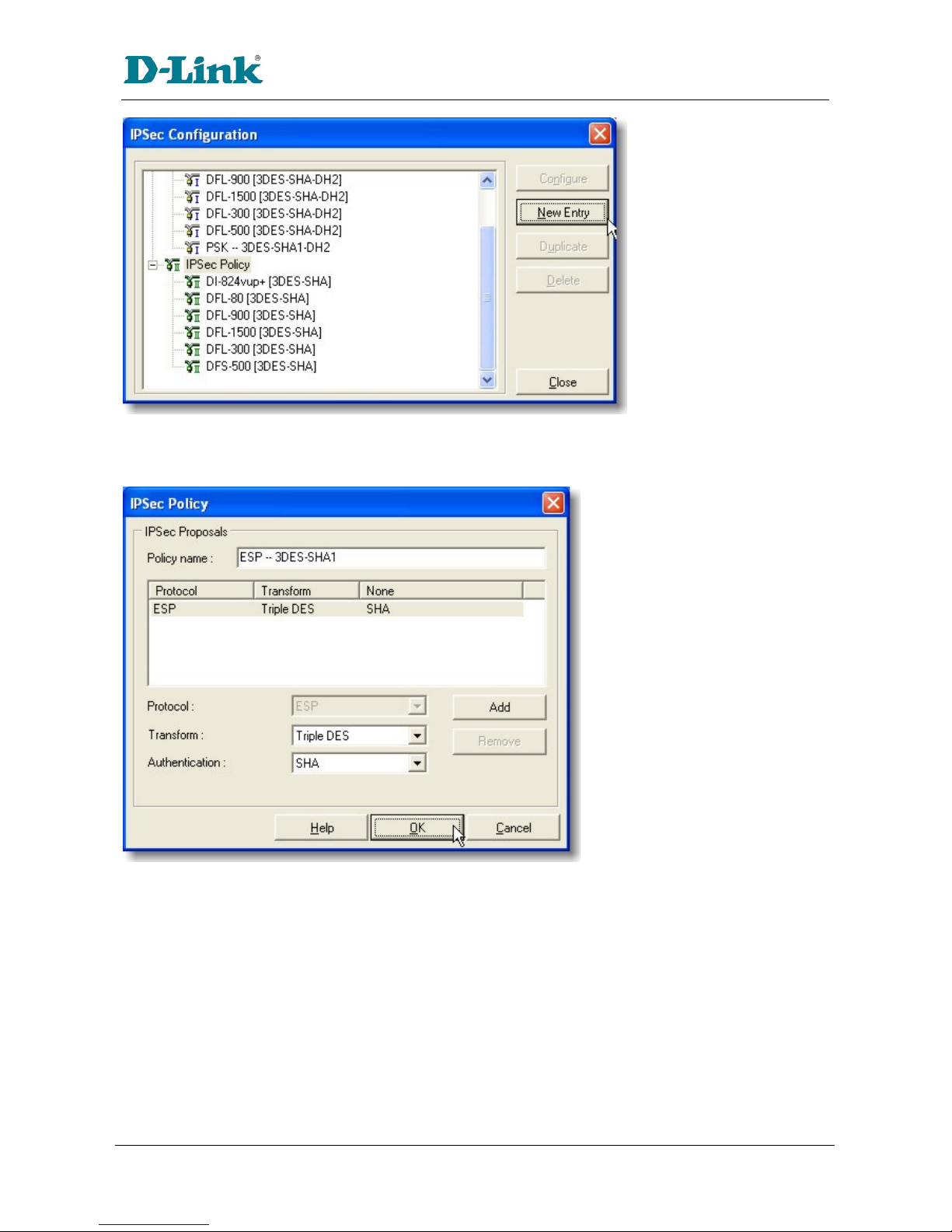
The IK Phase 2 parameters used in Scenario 1 are:
TripleDES
SHA-1
ESP tunnel ode
MODP group 2 (1024 bits)
Perfect forward secrecy for rekeying
SA lifeti e of 3600 seconds (one hour) with no kbytes rekeying
Selectors for all IP protocols, all ports, between the client and 172.23.9.0/24, using IPv4 subnets
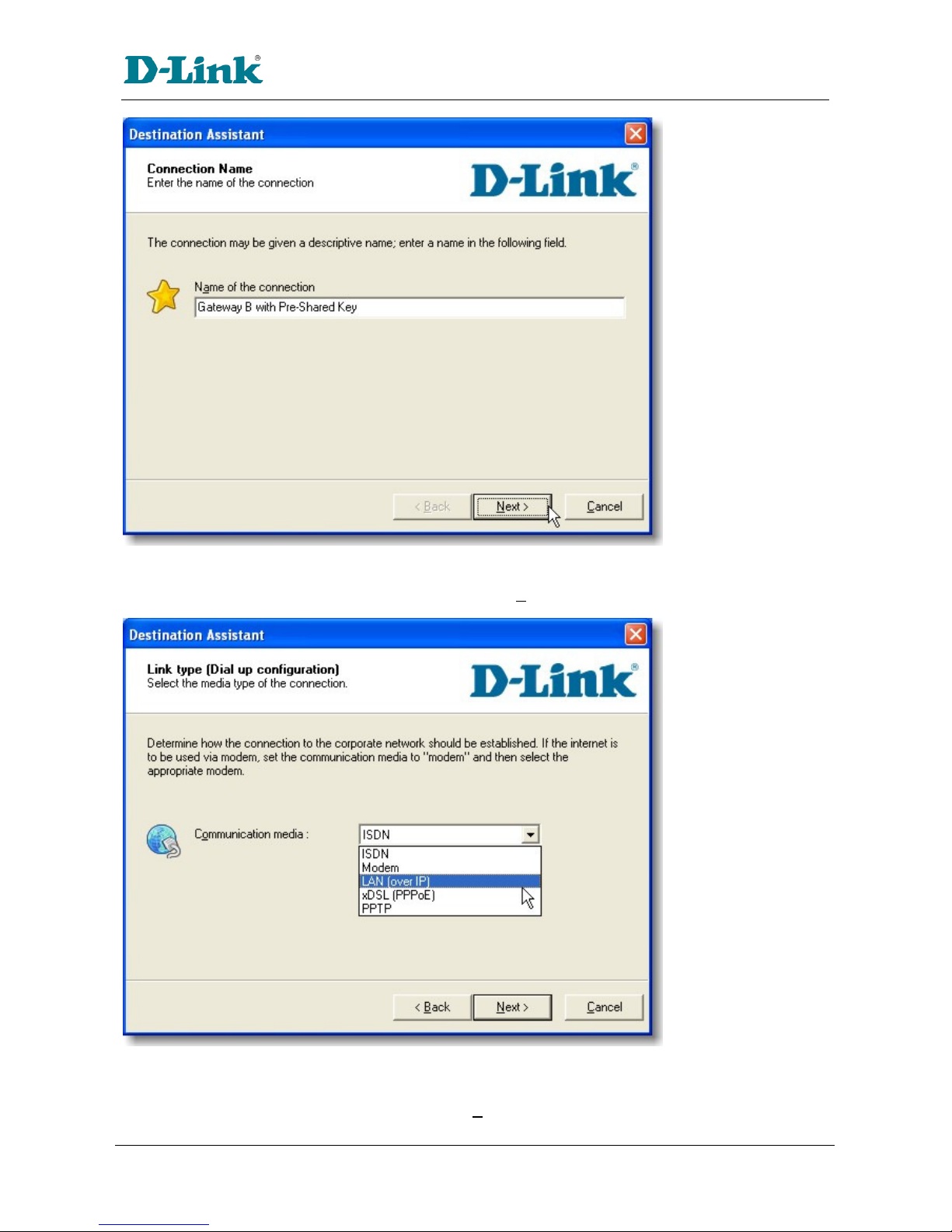
1.2 Using the Configuration Assistant
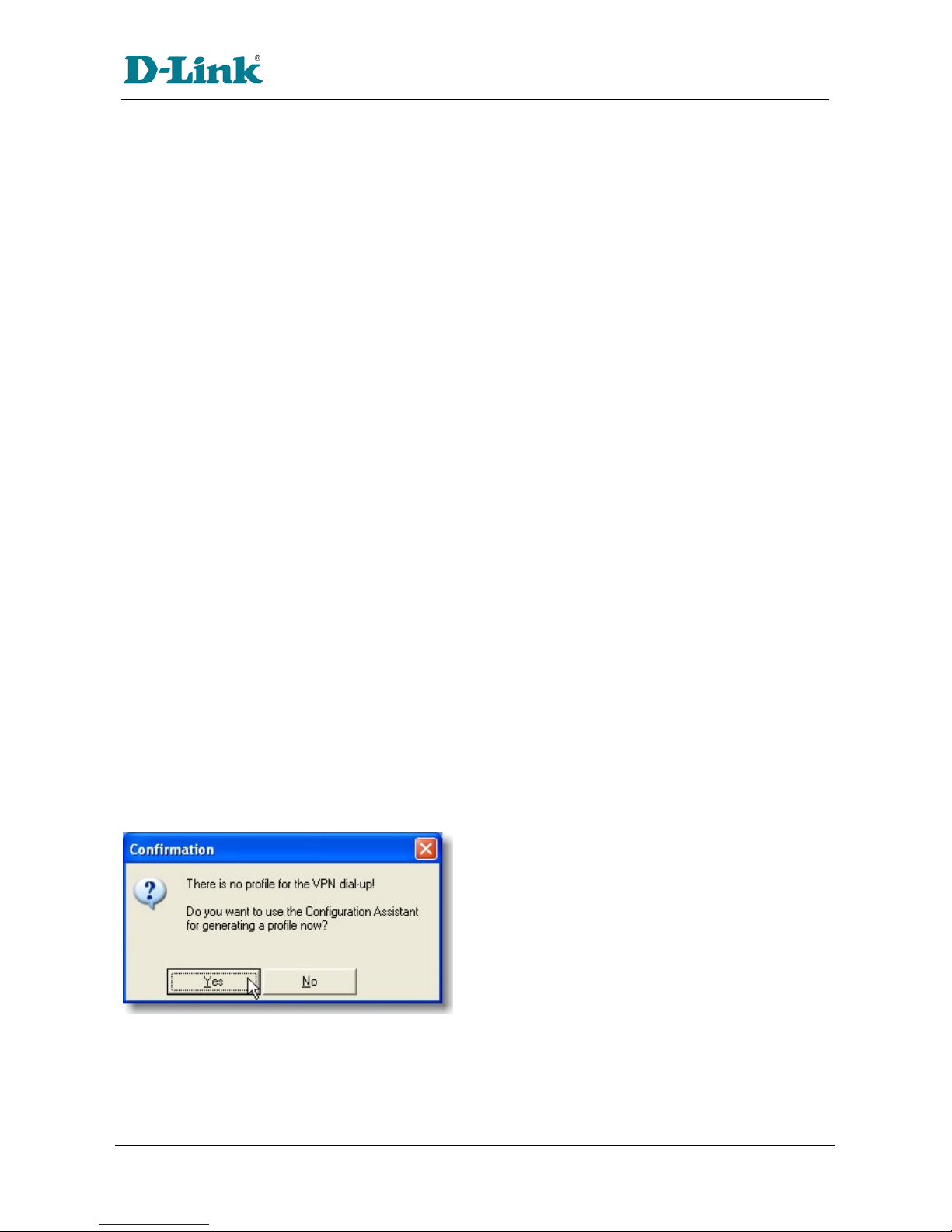
Figure 1.2.1: Configuration Assistant
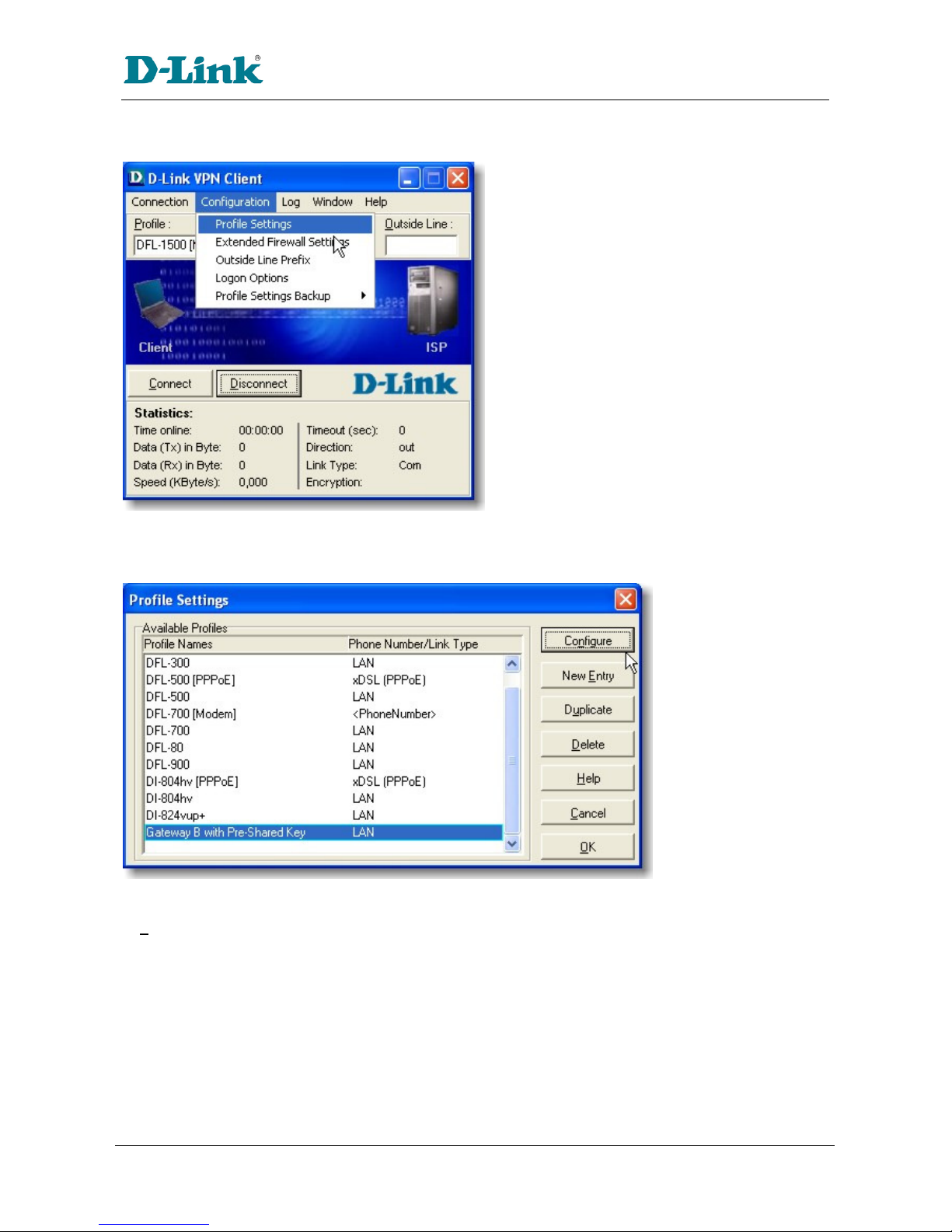
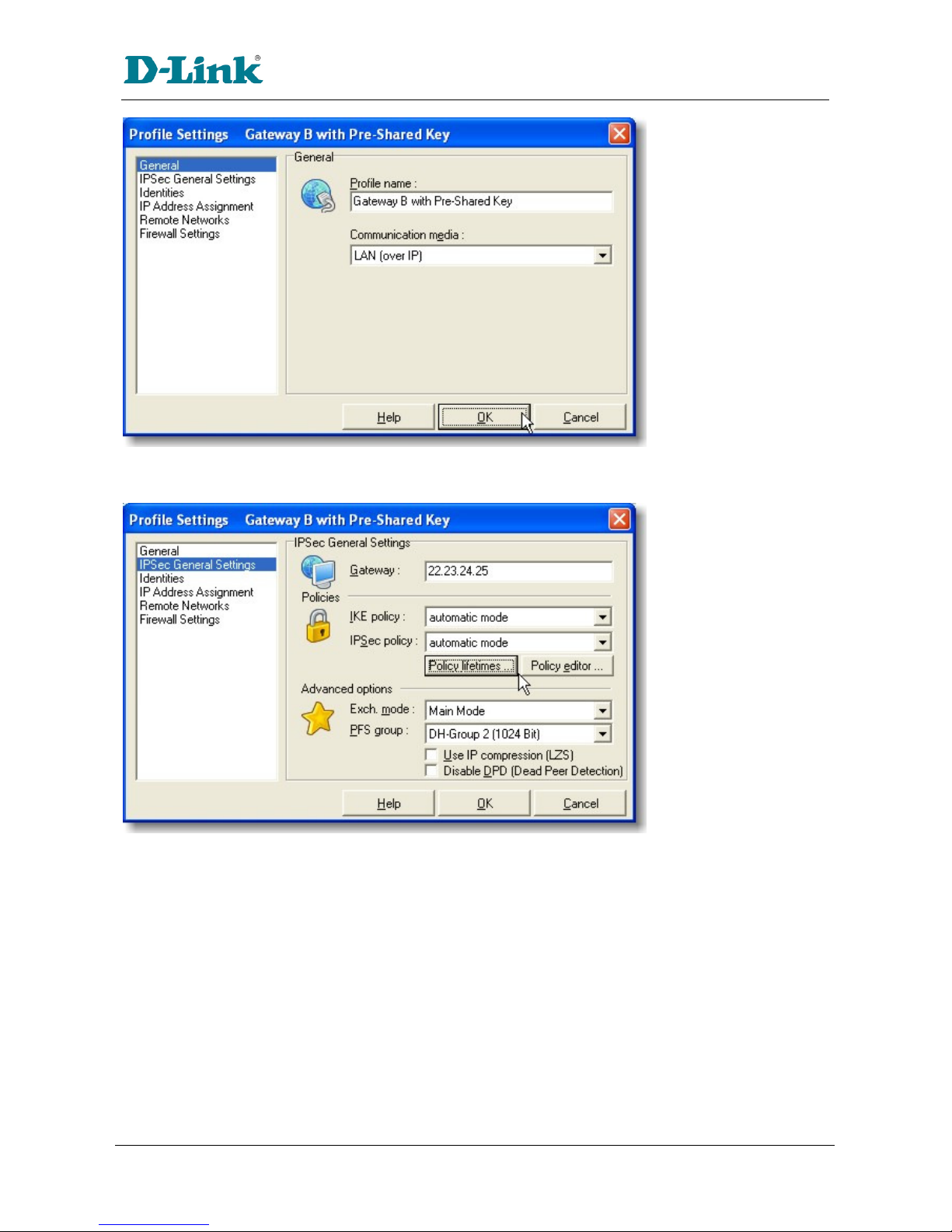
The first ti e you start up the D-Link VPN Client you ay be pro pted to create a profile if one doesn't
already exist. You can either use the assistant as outlined in section 1.2, or odify an existing profile as
in section 1.3.