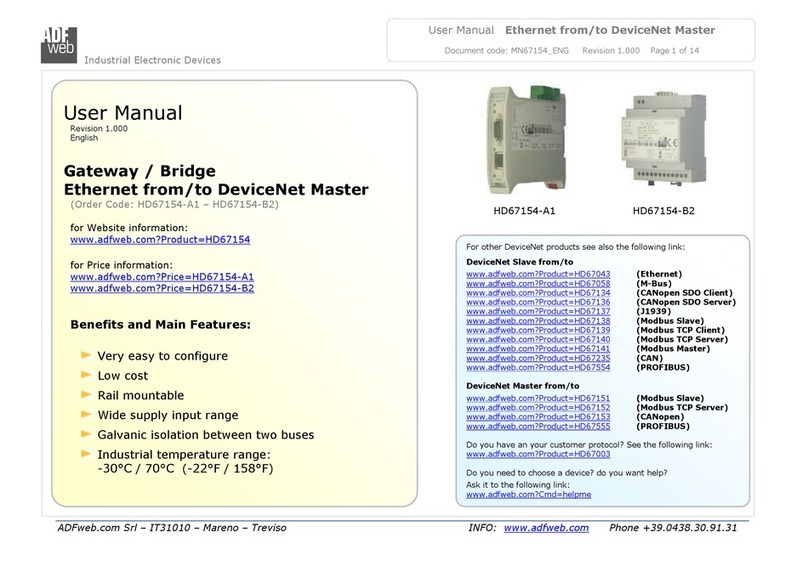
NetSHIELD Branch PRO User manual

Nano25/100
BranchPro
Enterprise10/100/250
USERGUIDE
MAY,2017

i
TABLE OF CONTENTS
February, 2017......................................................................................................................................i
Setup ......................................................................................................................................................2
Connect appliance to the network and determine IP address ............................................................2
Using a Console Connection.............................................................................................................3
LOGIN TO NETSHIELD™IN A WEB BROWSER................................................................................5
Appliance Installation Wizard............................................................................................................6
License not activated......................................................................................................................11
System Management.............................................................................................................................12
Rebooting NetSHIELD....................................................................................................................12
Stopping Audits In-Process.............................................................................................................13
Factory Reset.................................................................................................................................13
Reset Console Password................................................................................................................13
Enable SSH....................................................................................................................................14
Setting Up User Accounts..................................................................................................................15
Understanding Relationships between User Types .........................................................................15
Creating or Editing User Accounts..................................................................................................16
NetSHIELD Access Level ...............................................................................................................17
Deleting User Accounts..................................................................................................................17
Coordinating User Accounts with Asset Tracker User List ...............................................................17
Setting System Date/Time..................................................................................................................18
Background Scans.............................................................................................................................18
Backup and Restore...........................................................................................................................19
Backup Now...................................................................................................................................20
Restore ..........................................................................................................................................21
System Statistics................................................................................................................................23
Manage Server Certificate..................................................................................................................23
Network Configuration ...........................................................................................................................26
Multiple Network Interface Card (NIC) Support...................................................................................27
Configuring NICs............................................................................................................................27
Setting Up Network Access Control .......................................................................................................27
Initial Asset Discovery........................................................................................................................27
How SnoopWall NetSHIELD Generates the List of IP Addresses........................................................29
Adding IP Addresses Manually...........................................................................................................30
System Information Fields ..............................................................................................................31
List Categories ...............................................................................................................................32
Determining Ping Response of Nodes on Subnet...................................................................................32

ii
Ping Latency Chart.............................................................................................................................32
Pinging Individual Assets ...................................................................................................................33
IP Categories.....................................................................................................................................34
Managing Assets...................................................................................................................................35
Manage Assets Overview...................................................................................................................35
Asset Summary Box...........................................................................................................................37
Pop-up Menu.....................................................................................................................................37
Filter Panel.........................................................................................................................................38
Deleting IP Addresses........................................................................................................................39
Managing Asset Categories...................................................................................................................40
Importing and Exporting Asset Lists.......................................................................................................41
Exporting...........................................................................................................................................41
Importing............................................................................................................................................42
Setting Up SmartSwitch Integration........................................................................................................42
Asset Detection and Vulnerability Quarantine™ .....................................................................................43
NetShield Blocking .........................................................................................................................46
Enabling Manual NetSHIELD Blocking............................................................................................46
Enabling Automatic NetSHIELD Blocking........................................................................................46
Excluding Assets From NetSHIELD Blocking......................................................................................47
Viewing Assets Blocked With NetSHIELD Blocking............................................................................47
Viewing NetSHIELD Blocking Logs ....................................................................................................48
Immediately Blocking an Untrusted Asset...........................................................................................48
Enabling NetSHIELD UnBlocking Traffic.............................................................................................49
Enabling MAC Spoof Alerting.............................................................................................................50
Enabling MAC Spoof Blocking............................................................................................................50
Viewing ADS Configuration Settings...................................................................................................50
Preparing Your Network for Asset Detection.......................................................................................50
Queuing Trusted Asset Scans............................................................................................................51
Disable ADS ......................................................................................................................................52
Policy Manager......................................................................................................................................52
Configuring Inventory Alerts...................................................................................................................53
Configuring Asset Tracker .....................................................................................................................54
Viewing Systems List (Asset List) in Asset Tracker.............................................................................54
Viewing/Modifying/Adding Systems In The Asset Tracker...................................................................55
Editing/Adding System Information .................................................................................................55
Viewing Asset Report List...............................................................................................................56
Adding User Information.....................................................................................................................57
Adding Software Information ..............................................................................................................58

iii
Adding Peripheral Information............................................................................................................59
Associating Users, Software, & Peripherals With Systems..................................................................60
Associating Users with Systems.........................................................................................................61
Associating Software with Systems....................................................................................................62
Associating Peripherals with Systems ................................................................................................62
Removing Assets from SnoopWall NetSHIELD ..................................................................................63
Malware detection system .....................................................................................................................64
overview............................................................................................................................................64
configuration malware detection.........................................................................................................64
malware detection system..................................................................................................................64
Managing Whitelist For Detected Malware IP Address(es)..............................................................66
Managing Manual Malware IP Addresses....................................................................................67
Viewing Malware IP Address History...............................................................................................68
Viewing Malware Signature Update Schedule.................................................................................68
Audits....................................................................................................................................................69
Creating and Managing Audits ...........................................................................................................69
Running a One-Click Audit.................................................................................................................69
Defining A New Audit.........................................................................................................................70
Assigning an Audit Name................................................................................................................71
Setting Vulnerability Threshold for Notification ................................................................................71
Modifying Who Receives Reports ...................................................................................................72
Scheduling Audits..............................................................................................................................73
Scheduling Backups and Audits.........................................................................................................73
Setting Audit Frequency and Start Time..........................................................................................73
Choosing IP Addresses From List......................................................................................................74
Selecting/Grouping IP Addresses to Audit..........................................................................................75
Saving the Audit.................................................................................................................................75
Activating & Managing Audits.............................................................................................................76
Scheduling an Audit to Run................................................................................................................76
Starting an Audit.............................................................................................................................76
Deactivating an Audit .........................................................................................................................77
Removing an Audit.............................................................................................................................77
Modifying an Existing Audit’s Definition ..............................................................................................78
Copying an Audit to Create a Variation...............................................................................................78
Removing Systems/IP Addresses from an Audit.................................................................................78
Viewing Lists of CVE Tests by OS and Application.............................................................................79
Managing Known Missing Assets...........................................................................................................79
Viewing SnoopWall NetSHIELD Schedule.............................................................................................80

iv
Viewing the Monthly, Weekly, or Yearly Schedule ..............................................................................81
Viewing The Daily Schedule...............................................................................................................81
Daily Schedule Details....................................................................................................................81
Searching the Calendar......................................................................................................................81
Opening Audit/Scheduling FAQ in the Calendar View.........................................................................82
National Vulnerability Database..........................................................................................................82
Managing In Process Audits...............................................................................................................83
Reviewing Audits............................................................................................................................83
Viewing Partial Reports ..................................................................................................................84
Generating and Viewing Asset Reports..................................................................................................85
Updates.................................................................................................................................................88
Setting Up Automatic Vulnerability Updates........................................................................................88
Retrieving SnoopWall NetSHIELD Service Packs/Version Updates....................................................89
Service Pack Configuration................................................................................................................90
Malware threat feed update................................................................................................................90
License/Subscription updates.........................................................................................................91
Configuring a Proxy for Service Pack and Vulnerability Updates.........................................................91
Command Center..................................................................................................................................92
Managing Appliances.........................................................................................................................93
Adding Managed Appliances..............................................................................................................93
Edit Appliance Information..............................................................................................................94
Removing Appliances.....................................................................................................................94
Adding/Managing Appliance Groups ..................................................................................................94
Remote Operations............................................................................................................................95
Command Center Syslog Messages ..................................................................................................96
Configuring the Syslog Server............................................................................................................98
Clearing Command Center Alerts.......................................................................................................98
Developing Corporate Policies.............................................................................................................101
Understanding Regulations..............................................................................................................101
Using The Basic Policy Builder.........................................................................................................102
Modifying Policy Text.......................................................................................................................104
Revising Policy Document Status and Releasing Policy....................................................................105
Using The ISO 27001/17799 Policy Builder......................................................................................106
Indicating Your Existing Security Status ...........................................................................................107
Generating Draft Text for Your Security Policy..................................................................................108
Reports Guide.....................................................................................................................................110
Overview of Report Types and Content............................................................................................110
Understanding SnoopWall NetSHIELD Report Types.......................................................................110

v
CVE Information in Reports..............................................................................................................110
Selecting Content Presented in Reports...........................................................................................111
Interpreting and Understanding Reports...........................................................................................113
Interpreting Complete Vulnerability Reports......................................................................................113
Interpreting Vulnerability Descriptions...............................................................................................115
Interpreting Summary Reports..........................................................................................................116
Remediation of Vulnerabilities in Reports .........................................................................................117
Custom Comments ..........................................................................................................................117
Adding New Comments................................................................................................................118
Editing/Removing Existing Comments ..........................................................................................119
Viewing Comments in Reports......................................................................................................119
Finding Automatic Reports for Dynamically Detected Devices ..........................................................120
Removing a Report..........................................................................................................................120
Saving a Report to Disk....................................................................................................................121
Creating Custom Reports Using Queries..........................................................................................121
Querying Reports Database..........................................................................................................121
Printing Query Results..................................................................................................................122
Generating Management and Executive Reports .................................................................................123
Requirements for Executive/Management Reports...........................................................................123
Generating Management Reports.....................................................................................................123
Understanding Content of Management Reports..............................................................................124
Generating Executive Reports..........................................................................................................126
Understanding Content of Executive Reports...................................................................................126
Working with Logs...............................................................................................................................129
Viewing Network Events Log............................................................................................................129
Viewing System Events Log.............................................................................................................130
Log Reporting Wizard ......................................................................................................................130
Filtering........................................................................................................................................131
Generating PDFs..........................................................................................................................132
Saving Reports.............................................................................................................................133
Opening Reports..........................................................................................................................134
Sorting..........................................................................................................................................135
Summary......................................................................................................................................135
Workflow /Remediation Requirements.................................................................................................137
Workflow Management System at a Glance .....................................................................................137
Progression of Job Status.............................................................................................................137
Remediation of Vulnerabilities.......................................................................................................137
Flagging False Positives...............................................................................................................137

vi
Workflow Setup/Remediation Steps .................................................................................................138
Who Should Learn about Vulnerability Remediation .........................................................................138
Understanding Workflow and User Responsibilities..........................................................................139
Progression of Job Status.............................................................................................................139
IT Staff: Steps For Remediation of Vulnerabilities.............................................................................139
Managing Remediation—Initial Setup...........................................................................................140
Managing Remediation—Responding to Events as Manager............................................................140
Using Workflow in Vulnerability Remediation....................................................................................141
Remediation Scheduling ..................................................................................................................141
How SnoopWall NetSHIELD Calculates/Sets Due Dates...............................................................142
The Workflow Ticket Log..................................................................................................................143
Selecting and Assigning Jobs...........................................................................................................143
Recognizing a Job Is On Hold..........................................................................................................145
Viewing Logs of Assigned Jobs........................................................................................................145
Viewing Vulnerability Reports...........................................................................................................146
Using Links in Reports.....................................................................................................................146
Researching CVEs and CANs..........................................................................................................147
Updating Job Status.........................................................................................................................147
Updating Multiple IDs in a Single Job Ticket.....................................................................................148
Tagging a Vulnerability as a False Positive.......................................................................................148
Dealing with Escalated Jobs (Managers Only)..................................................................................148
Viewing Escalated Jobs ...................................................................................................................149
Reassigning Jobs (Managers Only)..................................................................................................149
Viewing Job Logs of Specific Individuals (Managers Only)................................................................150
Confirming False Positives (Managers Only)....................................................................................151
Closing a Job (Managers Only)........................................................................................................152
Customer Service................................................................................................................................154

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 1
System Guide

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 2
SETUP
Connect appliance to the network and determine IP address
1. Plug power cord into the power jack in the rear of the NetSHIELD appliance, and into
a 3-prong grounded outlet.
2. Connect your local area network cable to the eth0 port on the NetSHIELD appliance.
Network cable must be Type RJ -45, category 5 cable or higher.
3. Connect a monitor to the VGA port on the NetSHIELD™appliance.
4. Connect a keyboard to the USB ports.
5. Boot the appliance by pushing the red Start button on the left side of the front panel.
6. The green Power light will come on. The yellow Disk Activity indicator will also flash.
7. The front panel lights (from right to left) are:
Power
Hard Drive Activity
Network Activity 1
Network Activity 2
System Overheat
8. The appliance will run through its startup, displaying its progress on the monitor. When
it is finished, a screen like the following will appear.

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 3
9. Make a note of the DHCP assigned IP address (https://XX.X.XX) you are given.
The final number (443) is the port number.
Before you configure NetSHIELD™ software, open port 443 on your Firewall Server. This port
must remain open while NetSHIELD™ is operating so that you can receive service packs,
code updates, and updates to vulnerability tests from SnoopWall.
Using a Console Connection
To manually configure your appliance using a console connection do the following:
1. The default console password is changeme. No characters will be displayed when
entering the password.
2. The following screen appears:
NOTE: If you do not open the port on the Firewall, you cannot receive
automatic vulnerability signature updates, malware updates, or SnoopWall
NetSHIELD™ Service Packs.

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 4
The following functions can be performed from this screen:
<1> Network Configuration –Configure network settings for Eth0. A web browser is
used to configure additional interfaces.
<2> Allowed Access Control - Modify the list of IP addresses that are allowed to
access the user interface via a web browser.
<3> Disable ADS –Disable the Asset Detection engine on the NetSHIELD™.
<4> Disable NetSHIELD™ NAC Blocking - Disable NetSHIELD™ Blocking and stop
blocking any assets currently being blocked.
<5> Reset Network Interfaces - Configuration for all interfaces except ETH0 will be cleared
and the appliance will be rebooted.
<6> Change Console Password - You will be asked to provide the current password and
confirm the new password. Please remember your password for future use.
<7> Reset MainAccount Password –Reset MainAccount password to changeme.
<8> Reboot - Restart the appliance.
<9> Shutdown - Power down the appliance.
<10> Factory settings - Return to factory preset settings.
<11> Enable SSH Login –Enables the ability to login via SSH

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 5
<12> Reset License - Reinstall the NetSHIELD™ license
<13> Generate SSH Key –Create a one-tine key to allow SSH login.
<14> Open Support Channel –Open the SSH connection for remote support.
<15> Close Support Channel –Close the SSH connection for remote support.
<16> Recreate Certificate –Recreate the self-signed certificate of the NetSHIELD™.
<17>Logout
LOGIN TO NETSHIELD™IN AWEB BROWSER
To log in
1. Open a secure browser window using https://<IP address of appliance>
For example;
If the appliance has an IP address 192.168.254.159
https://192.168.254.159
2. If you changed the default port (443) in the installation process, add a colon followed by
the new port number.
For example;
If using port number 10000, Enter the URL as https://192.168.254.159:10000.
If you see a Security Alert or other message from your system, Click Continue to
proceed with the login.
3. The login screen appears:
1. Login the NetSHIELD™appliance with the default credentials.
Username: MainAccount
Password: changeme

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 6
4. Click the Login button.
First time setup
Appliance Installation Wizard
The Appliance Installation Wizard will automatically launch. It consists of 8 tabs designed to
get you up and running as quickly as possible. Note that the new tabs do not appear until the
most recently presented tab is completed.
The 1st tab is the End Users License Agreement.
The 2nd tab is the MainAccount Password.
1. Fill in the default Login ID and Password.
2. Confirm the Password.
3. Click the Save button.

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 7
The 3rd tab is the Subscription Information tab.
1. Fill in all of the required information, indicated by (*).
2. Click the Save button.
The 4th tab is the Ethernet Port Configuration.
1. A picture of the possible Ethernet connections is displayed based on the appliance type.
See the example below.

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 8
The 5th tab is the Network Configuration tab.
1. Make changes as necessary to the Network Configuration Data.
2. Click on Save.
3. Click the Next buttons to go to the next screen.
If you have changed the IP Address for Eth0 or SSL port, the appliance server will be restarted.
The Appliance Installation Wizard will attempt to reload itself. You can need to login again, or
prompt the browser to try the reload again. You will also need to confirm the certificate again.

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 9
The 6th tab is Notification Information.
1. Fill in the Required Information as indicated by the red (*).
2. Click the Verify Mail Settings.
3. If the configuration is correct, a message box will appear, and the email address
specified in the System Admin Email entry will receive a test message.
4. Click Save.

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 10
The 7th tab is Configure Multiple VLANs.
1. Select an Ethernet interface to configure from the NIC dropdown box.
2. Click the ( + ) button to add a VLAN entry for the current interface.
3. Enter the VLAN tag, the VLAN name, the subnet mask, and the IP address.
4. Repeat Steps 2 and 3 for each VLAN the appliance will use on the current interface.
5. Click Save to save the VLAN configuration.
6. Repeat Steps 1 thru 6 for each additional Interface required.
7. To Remove a VLAN entry, click the checkbox to the left side of the item.
8. Now click the ( –) button.

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 11
The 8th tab is Initial Asset Discovery.
1. Click Refresh IPs to perform an initial asset discovery
2. When complete the Manage Assets page opens.
License not activated
If your license has not yet been activated, you will get the following message;
1. Click Continue
2. Go to UpdatesLicense/Subscription.
3. Enter the code sent to you by SnoopWall, or wait for automatic activation (usually
overnight).
4. When the license is activated, you will see a screen similar to this:

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 12
SYSTEM MANAGEMENT
The System Menu gives you access to the NetSHIELD system functions such as utilities,
password change, change the system date and time, etc.
To access system utilities, select System
Utilities from the left menu.
Rebooting NetSHIELD
Restart SnoopWall NetSHIELD without losing any saved information.
Select System
Utilities from the left menu.
Click the Reboot button.
Confirm or cancel the reboot. If you proceed, the browser window displays the message Reboot
in Progress.
Rebooting does not change the Scheduled or Inactive status of an audit profile. Any audits in
process when the reboot occurs are not completed. You will receive a warning informing you
that they are currently in process, will stop, and must be restarted later.
NOTE: Wait at least 2 minutes for the reboot to complete.
To shut down SnoopWall NetSHIELD:
Select System
Utilities from the left menu.
Click the Shutdown button.

Ten Tara Boulevard, Suite 140 Copyright © 2017 SnoopWall, Inc.
Nashua NH 03062 Page | 13
You are asked to confirm or cancel the shutdown. If you proceed, SnoopWall NetSHIELD
operating system will shut down. Manually press the power button to power off.
To restart SnoopWall NetSHIELD, you must manually press the Power button on the appliance.
Shutting down does not change the Scheduled or Inactive status of any audit. Any audits in
process when the shutdown occurs will stop. You must restart them when SnoopWall
NetSHIELD is powered up again.
Stopping Audits In-Process
To terminate audits currently running:
Select System
Utilities from the left menu.
(You can also halt an audit on the Manage Audits page by clicking the Stop button.)
Click the Stop All Audits button.
You are asked to confirm or cancel the action.
Any audits currently in process do not complete. You
receive a warning saying in-process audits will stop and
must be restarted later.
Any reports already generated remain on the system. You may still view them by selecting
Reports
View Audit Results.
A halted audit does not run again until its next scheduled time. Halting all audits does not
change their Scheduled or Inactive status.
To restart an audit sooner than the next scheduled time:
Select Audits
Manage Audits from the left menu.
Select the audit to open it in the Audit Wizard. Click through Audit Wizard pages until you
reach the screen with audit frequency settings. Set the Frequency of Audit to Now.
Click Next until you complete the AuditWizard steps, and Save the audit. When the
Manage Audits page opens, click the Start button to begin the audit.
Factory Reset
To return SnoopWall NetSHIELD to the settings with which it was shipped, select System
Utilities from the left menu, and then click Factory Settings.
Important Note: Alerts should always be cleared from the command center
following a factory reset on the client appliance.
Just as with the console factory reset, you will be given the option of retaining the Company
Information, Notification Information, and the appliance name. All the asset information,
categories, audits, reports, etc. will be deleted.
Reset Console Password
To reset the Console Password back to the original changeme, click the Reset Console
Password button on the System
Utilities page.
Other manuals for Branch PRO
1
This manual suits for next models
6
Table of contents
Popular Gateway manuals by other brands

Rosen Aviation
Rosen Aviation MIP100 Series Technical manual
Honeywell
Honeywell Lyric LCP300-L Installation and reference guide

4IPNET
4IPNET WHG315 user manual

ZyXEL Communications
ZyXEL Communications ZYWALL - CLI reference guide

RTA
RTA 460ECSC-NNA4 Product user guide

Energenie
Energenie MiHome Gateway user manual