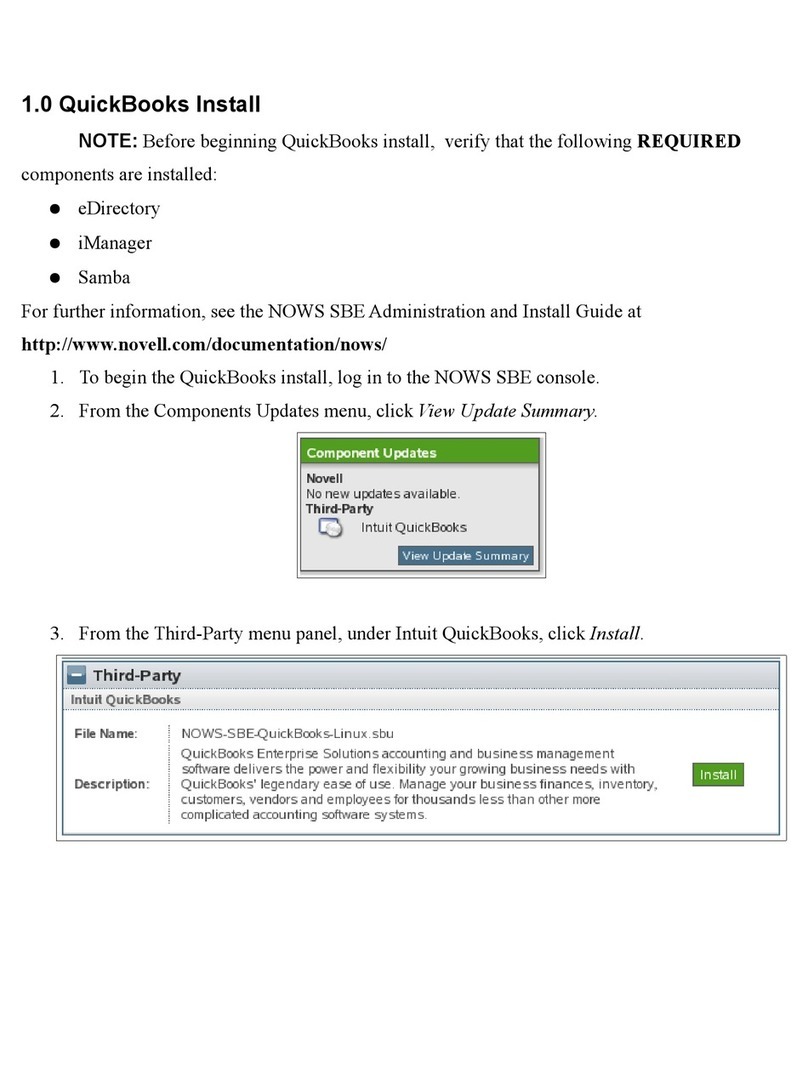
Hats
An AppArmor prole represents a security policy for an
individual program instance or process. It applies to an ex-
ecutable program, but if a portion of the program needs
different access permissions than other portions, the pro-
gram can “change hats” to use a different security context,
distinctive from the access of the main program. This is
known as a hat or subprole.
A prole can have an arbitrary number of hats, but there
are only two levels: a hat cannot have further hats.
The AppArmor ChangeHat feature can be used by applica-
tions to access hats during execution. Currently the packages
apache2-mod_apparmor and tomcat_apparmor utilize
ChangeHat to provide sub-process connement for the
Apache Web server and the Tomcat servlet container.
Conning Users with pam_apparmor
The pam_apparmor PAM module allows applications to
conne authenticated users into subproles based on group
names, user names, or a default prole. To accomplish this,
pam_apparmor needs to be registered as a PAM session
module.
Details about how to set up and congure pam_apparmor
can be found in /usr/share/doc/packages/pam
_apparmor/README. A HOWTO on setting up role-based
access control (RBAC) with pam_apparmor is available at
http://developer.novell.com/wiki/index.php/
Apparmor_RBAC_in_version_2.3.
Logging and Auditing
All AppArmor events are logged using the system's audit
interface (the auditd logging to /var/log/audit/audit
.log). On top of this infrastructure, event notication can
be congured. Congure this feature using YaST. It is based
on severity levels according to /etc/apparmor/
severity.db. Notication frequency and type of noti-
cation (such as e-mail) can be congured.
If auditd is not running, AppArmor logs to the system log
located under /var/log/messages using the LOG_KERN
facility.
Use YaST for generating reports in CSV or HTML format.
The Linux audit framework contains a dispatcher that can
send AppArmor events to any consumer application via
dbus. The GNOME AppArmor Desktop Monitor applet is
one example of an application that gathers AppArmor
events via dbus. To congure audit to use the dbus dispatch-
er, just set the dispatcher in your audit conguration in
/etc/audit/auditd.conf to apparmor-dbus and
restart auditd:
dispatcher=/usr/bin/apparmor-dbus
Once the dbus dispatcher is congured correctly, add the
AppArmor Desktop Monitor to the GNOME panel. As soon
as a REJECT event is logged, the applet's panel icon
changes appearance and you can click the applet to see the
number of reject events per conned application. To view
the exact log messages, refer to the audit log under /var/
log/audit/audit.log. Use the YaST Update Prole
Wizard to adjust the respective prole.
Directories and Files
/sys/kernel/security/apparmor/profiles
Virtualized le representing the currently loaded set of
proles.
/etc/apparmor/
Location of AppArmor conguration les.
/etc/apparmor/profiles/extras/
A local repository of proles shipped with AppArmor,
but not enabled by default.
/etc/apparmor.d/
Location of proles, named with the convention of re-
placing the /in pathnames with .(not for the root /)
so proles are easier to manage. For example, the prole
for the program /usr/sbin/ntpd is named usr.sbin
.ntpd.
/etc/apparmor.d/abstractions/
Location of abstractions.
/etc/apparmor.d/program-chunks/
Location of program chunks.
/proc/*/attr/current
Review the connement status of a process and the
prole that is used to conne the process. The ps auxZ
command retrieves this information automatically.
For More Information
To learn more about the AppArmor project, check out the
project's home page under http://en.opensuse.org/
AppArmor. Find more information on the concept and the
conguration of AppArmor in Part “Conning Privileges
with Novell AppArmor” (↑Security Guide).
Legal Notice
All content is copyright © 2006- 2009 Novell, Inc.
This manual is protected under Novell intellectual property
rights. By reproducing, duplicating or distributing this
manual you explicitly agree to conform to the terms and
conditions of this license agreement.
This manual may be freely reproduced, duplicated and dis-
tributed either as such or as part of a bundled package in
electronic and/or printed format, provided however that
the following conditions are fullled:
5