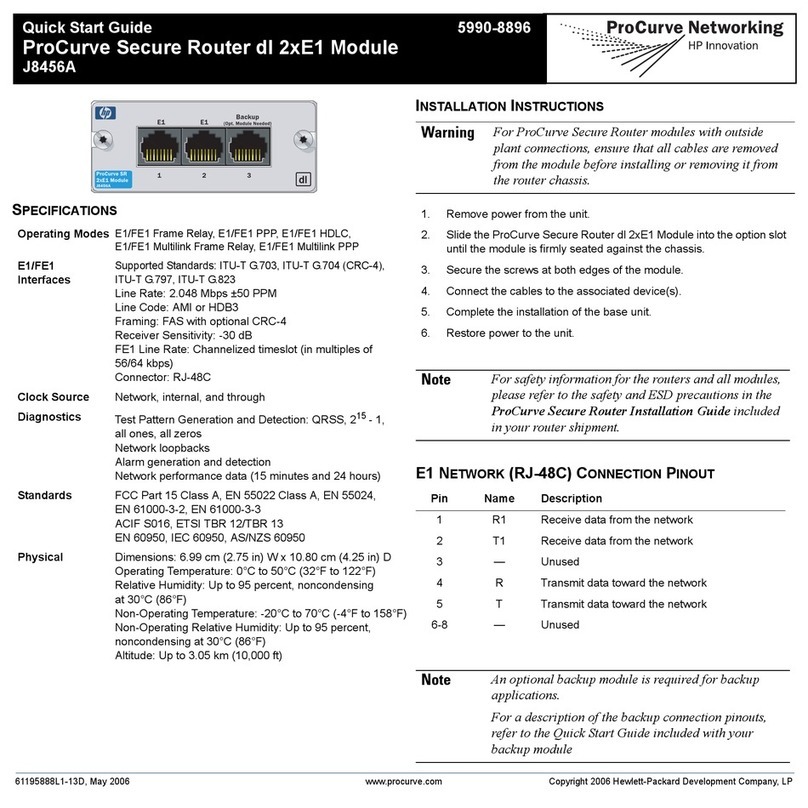
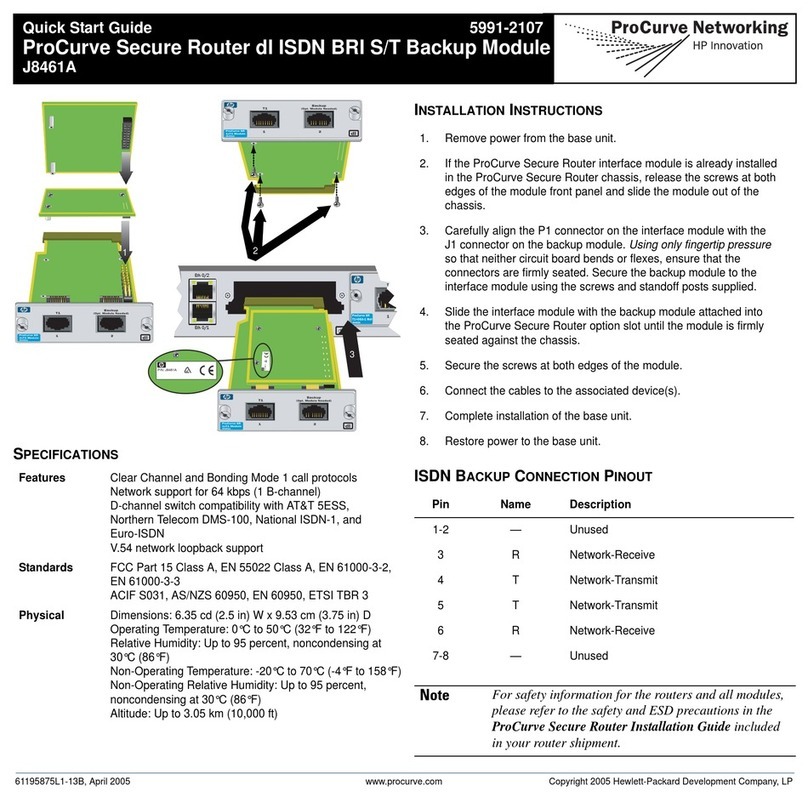
ProCurve 800 User manual

Configuration Guide
www.procurve.com
ProCurve Network Access Controller 800


ProCurve Network Access
Controller 800
Configuration Guide
April 2008
1.0-30398

Hewlett-Packard Company
8000 Foothills Boulevard
Roseville, California 95747
http://www.procurve.com/
© Copyright 2008 Hewlett-Packard Development Company, L.P.
The information contained herein is subject to change without
notice. All Rights Reserved.
This document contains proprietary information, which is
protected by copyright. No part of this document may be
photocopied, reproduced, or translated into another
language without the prior written consent of Hewlett-
Packard.
Publication Number
5991-8618
April 2008
Applicable Products
Network Access Controller 800 (J9065A)
Trademark Credits
Microsoft, Windows, Windows NT, and Windows XP are U.S.
registered trademarks of Microsoft Corporation.
Disclaimer
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY
OF ANY KIND WITH REGARD TO THIS MATERIAL,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS
FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not
be liable for errors contained herein or for incidental or
consequential damages in connection with the furnishing,
performance, or use of this material.
The only warranties for HP products and services are set
forth in the express warranty statements accompanying
such products and services. Nothing herein should be
construed as constituting an additional warranty. HP shall
not be liable for technical or editorial errors or omissions
contained herein.
Hewlett-Packard assumes no responsibility for the use or
reliability of its software on equipment that is not furnished
by Hewlett-Packard.
Warranty
See the Customer Support/Warranty booklet included with
the product.
A copy of the specific warranty terms applicable to your
Hewlett-Packard products and replacement parts can be
obtained from your HP Sales and Service Office or
authorized dealer.
Open Source Software Acknowledgment
Statement
This software incorporates open source components that
are governed by the GNU General Public License (GPL),
version 2. In accordance with this license, ProCurve
Networking will make available a complete, machine-
readable copy of the source code components covered by
the GNU GPL upon receipt of a written request. Send a
request to:
Hewlett-Packard Company, L.P.
Wireless Edge Services xl Module Program
GNU GPL Source Code
Attn: ProCurve Networking Support
MS: 5550
Roseville, CA 95747 USA

i
Contents
1 Overview of the ProCurve NAC 800
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
Hardware Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
LEDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
Console Ethernet Port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Panel LCD and Buttons . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Serial Number and MAC Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Ethernet Ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7
Port 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7
Port 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7
Server Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8
Choosing the Server Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8
Deployment of One MS and Multiple ESs . . . . . . . . . . . . . . . . . . . . 1-8
CS Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-11
Management Server (MS) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-12
Enforcement Server (ES) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-14
Combination Server (CS) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-14
Changing the Server Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-15
Enforcement Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Enforcement Clusters for an MS and ESs . . . . . . . . . . . . . . . . . . . . . . 1-16
Enforcement Clusters for a CS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Endpoint Integrity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-17
Endpoint Integrity Capabilities of the NAC 800 . . . . . . . . . . . . . . . . . 1-18
NAC Tests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-18
NAC Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-20
NAC Policy Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-23

ii
Testing Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-24
NAC EI Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-25
ActiveX . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-26
Agentless . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-27
Endpoint Integrity Posture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-28
Accessible Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-28
Performance Implications of Endpoint Integrity Checks . . . . . . . . . 1-29
Post-Connect Testing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-29
RADIUS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-30
ProCurve NAC 800 RADIUS Capabilities . . . . . . . . . . . . . . . . . . . . . . . 1-31
RADIUS Capabilities of the NAC 800 Integrated with IDM . . . . . . . . 1-32
Deployment Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-33
802.1X Deployment Method . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-34
802.1X Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-34
Types of Access Control Provided by the NAC 800 . . . . . . . . . . . 1-35
802.1X Deployment Method—Endpoint Integrity With
or Without RADIUS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-36
How the NAC 800 Quarantines Endpoints . . . . . . . . . . . . . . . . . . 1-36
How and Where to Deploy the NAC 800 . . . . . . . . . . . . . . . . . . . . 1-38
802.1X Deployment Method—RADIUS Server Only . . . . . . . . . . . . . . 1-43
How and Where to Deploy the NAC 800 . . . . . . . . . . . . . . . . . . . . 1-43
DHCP Deployment Method . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-44
Types of Access Control Provided By the NAC 800 . . . . . . . . . . 1-45
Two Options for a DHCP Deployment . . . . . . . . . . . . . . . . . . . . . 1-45
How and Where to Deploy the NAC 800 for a DHCP Inline
Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-45
How and Where to Deploy the NAC 800 for a DHCP Plug-in
Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-47
How the NAC 800 Quarantines Endpoints for a DHCP
Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-48
Enforcement Methods for DHCP Quarantining . . . . . . . . . . . . . . 1-51
Designing the Quarantine Subnet . . . . . . . . . . . . . . . . . . . . . . . . . 1-52
Inline Deployment Method . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-56
Types of Access Control Provided by the NAC 800 . . . . . . . . . . . 1-57
How the NAC 800 Quarantines Endpoints . . . . . . . . . . . . . . . . . . 1-57
Configuring Accessible Services for Inline Method . . . . . . . . . . . 1-57
How and Where to Deploy the NAC 800 . . . . . . . . . . . . . . . . . . . . 1-58

iii
2 Management Options for the ProCurve NAC 800
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-3
Menu Interface and Panel LCD . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-5
Access the Menu Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-5
Console Session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-5
SSH Session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
Navigate the Menu Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-8
Configure Initial Settings with the Menu Interface . . . . . . . . . . . . . . . . 2-9
Set the Server Type with the Menu Interface . . . . . . . . . . . . . . . . 2-10
Set the IP Address with the Menu Interface . . . . . . . . . . . . . . . . . 2-12
Test IP Settings (Ping) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-13
Change the Password to the Menu Interface . . . . . . . . . . . . . . . . . . . . 2-15
Complete Other Tasks in the Menu Interface . . . . . . . . . . . . . . . . . . . 2-17
Reboot the NAC 800 in the Menu Interface . . . . . . . . . . . . . . . . . 2-18
Shut Down the NAC 800 in the Menu Interface . . . . . . . . . . . . . . 2-19
Turn the Locator LED On and Off . . . . . . . . . . . . . . . . . . . . . . . . . 2-20
View System Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-21
Access the Panel LCD Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-22
Navigate the Panel LCD Menu . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-23
Configure Initial Settings with the Panel LCD Menu . . . . . . . . . . . . . 2-24
Set the Server Type with the Panel LCD Menu . . . . . . . . . . . . . . 2-24
Set the IP Address with the Panel LCD Menu . . . . . . . . . . . . . . . 2-26
Test IP Settings (Ping) with the Panel LCD Menu . . . . . . . . . . . . 2-28
Complete Other Tasks Using the Panel LCD Menu . . . . . . . . . . . . . . 2-29
Reboot the NAC 800 Using the Panel LCD Menu . . . . . . . . . . . . . 2-30
Shut Down the NAC 800 Using the Panel LCD . . . . . . . . . . . . . . . 2-31
Set the Ports Speed and Duplex Settings . . . . . . . . . . . . . . . . . . . 2-32
Root Access to the NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-35
Web Browser Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-37
Access the Web Browser Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-37
Requirements on the NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-37
Requirements on the Management Station . . . . . . . . . . . . . . . . . . 2-38
Steps for Accessing the Web Browser Interface . . . . . . . . . . . . . 2-39

iv
Navigate the Web Browser Interface . . . . . . . . . . . . . . . . . . . . . . . . . . 2-39
Home Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-39
Common Features in Web Browser Interface Windows . . . . . . . 2-44
Following Instructions to Navigate the Web Browser Interface 2-46
ProCurve Manager (PCM) Plus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-48
Enable PCM Plus to Detect the NAC 800 . . . . . . . . . . . . . . . . . . . . . . . 2-48
Capabilities of PCM Plus for Managing the NAC 800 . . . . . . . . . . . . . 2-49
IDM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-50
Enable IDM to Detect the NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-50
Capabilities of IDM for Managing the NAC 800 . . . . . . . . . . . . . . . . . . 2-53
3 Initial Setup of the ProCurve NAC 800
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-1
System Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-3
System Settings—Initial Configuration . . . . . . . . . . . . . . . . . . . . . . . . . 3-4
Initial Configuration of CS or MS Settings . . . . . . . . . . . . . . . . . . . 3-4
Initial Configuration of ES Settings . . . . . . . . . . . . . . . . . . . . . . . . . 3-9
Edit System Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-16
Edit System Settings on an MS or a CS . . . . . . . . . . . . . . . . . . . . . 3-16
Edit System Settings on an ES . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-33
Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-41
Management and Maintenance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-41
Upgrade the Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-41
Create Management Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-43
Create User Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-44
Configure User Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-47
Digital Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-54
Install a CA-Signed Certificate for HTTPS . . . . . . . . . . . . . . . . . . . . . . 3-55
Generate a Key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-56
Install the Root CA Certificate . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-57
Create a Certificate Request and Transfer It off the NAC 800 . . 3-58
Download and Install the Signed Certificate . . . . . . . . . . . . . . . . 3-60
Restart the HTTPS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-61

v
Install a New Self-Signed Certificate for HTTPS . . . . . . . . . . . . . . . . . 3-61
Generate the Self-Certificate and Key . . . . . . . . . . . . . . . . . . . . . . 3-62
Export the Self-signed Certificate to a File . . . . . . . . . . . . . . . . . 3-63
Install the Self-signed Certificate as a Trusted Root
Certificate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-63
Restart the HTTPS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-64
Install the Self-signed Certificate as a Trusted Root
Certificate on Endpoints . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-64
4 Configuring the RADIUS Server—Integrated with
ProCurve Identity Driven Manager
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-3
RADIUS Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-3
Authentication Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-4
Dynamic or User-Based Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-4
IDM Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-5
Data Store Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-6
Local Database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-7
AD (Windows Domain) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-7
LDAP Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-8
Proxy RADIUS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-9
Configure the NAC 800 as a RADIUS Server . . . . . . . . . . . . . . . . . . . 4-11
Specify the Quarantine Method (802.1X) . . . . . . . . . . . . . . . . . . . . . . . 4-12
Configure Authentication Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-14
Configure Authentication to the NAC 800’s Local Database . . . 4-14
Configure Authentication to a Windows Domain . . . . . . . . . . . . 4-16
Configure Authentication to an LDAP Server . . . . . . . . . . . . . . . 4-20
Configure Authentication to a Proxy RADIUS Server . . . . . . . . . 4-30
Test Authentication Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-35
Add NASs as 802.1X Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-40
Apply Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-44
Restart the RADIUS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-44

vi
Manage Digital Certificates for RADIUS . . . . . . . . . . . . . . . . . . . . . . . 4-48
Install the CA Root Certificate on the NAC 800 . . . . . . . . . . . . . . . . . 4-49
Install a Server Certificate for RADIUS . . . . . . . . . . . . . . . . . . . . . . . . 4-50
Create a Self-Signed Certificate . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-51
Install a CA-Signed Certificate Using a Request Generated
on the NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-53
Install a CA-Signed Certificate Using a Request Generated
on Behalf of the NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-58
Manage Certificates on Endpoints . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-62
Disable Server Validation on Endpoints . . . . . . . . . . . . . . . . . . . . . . . . 4-62
5 Configuring the RADIUS Server—Without Identity Driven
Manager
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-3
RADIUS Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-3
Authentication Protocols . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-4
Dynamic or User-Based Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-4
Data Store Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-5
AD (Windows Domain) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-5
LDAP Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-6
Proxy RADIUS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-6
Configure the NAC 800 as a RADIUS Server . . . . . . . . . . . . . . . . . . . . 5-8
Specify the Quarantine Method (802.1X) . . . . . . . . . . . . . . . . . . . . . . . . 5-8
Configure Authentication Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-10
Configure Authentication to a Windows Domain . . . . . . . . . . . . 5-10
Configure Authentication to an LDAP Server . . . . . . . . . . . . . . . 5-14
Configure Authentication to a Proxy RADIUS Server . . . . . . . . . 5-23
Test Authentication Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-28
Add NASs as 802.1X Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-34
Apply Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-38
Restart the RADIUS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-38

vii
Manage Digital Certificates for RADIUS . . . . . . . . . . . . . . . . . . . . . . . 5-42
Install the CA Root Certificate on the NAC 800 . . . . . . . . . . . . . . . . . 5-43
Install a Server Certificate for RADIUS . . . . . . . . . . . . . . . . . . . . . . . . 5-45
Create a Self-Signed Certificate . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-45
Install a CA-Signed Certificate Using a Request Generated
on the NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-47
Install a CA-Signed Certificate Using a Request Generated
on Behalf of the NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-52
Manage Certificates on Endpoints . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-56
Disable Server Validation on Endpoints . . . . . . . . . . . . . . . . . . . . . . . . 5-56
6 Disabling Endpoint Integrity Testing
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-2
Configure Exceptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-2
Configure Exceptions for the Cluster Default Settings . . . . . . . . . 6-3
Configure Exceptions for a Particular Cluster . . . . . . . . . . . . . . . . 6-5
7 Redundancy and Backup for RADIUS Services
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-1
Redundancy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-2
Planning Redundancy for RADIUS-Only Deployments . . . . . . . . . . . . 7-2
Place the RADIUS Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-3
Provide Duplicate Network Pathways . . . . . . . . . . . . . . . . . . . . . . 7-4
Configuring Network Devices for Redundant RADIUS Servers . . . . . 7-4
Configure the NASs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-5
Configure Multiple LDAP Servers on the NAC 800 . . . . . . . . . . . . 7-6
Use IDM to Configure the Usernames and Passwords . . . . . . . . 7-11
Test Your Redundant Configurations . . . . . . . . . . . . . . . . . . . . . . . . . . 7-11
Back Up Your NAC 800 Configuration . . . . . . . . . . . . . . . . . . . . . . . . . 7-12
Configure the Web Browser So That It Allows You to
Save Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-14
Restore the System from the Backup File . . . . . . . . . . . . . . . . . . . . . . 7-15

viii
A Appendix A: Glossary
B Appendix B: Linux Commands
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-1
Common Linux Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-2
vi Editor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-4
Command Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-4
Insert Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-5
keytool . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-6
openssl . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-9
Service Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-12

1-1
Overview of the ProCurve NAC 800
Contents
1
Overview of the ProCurve NAC 800
Contents
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
Hardware Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
LEDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
Console Ethernet Port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Panel LCD and Buttons . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Serial Number and MAC Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Ethernet Ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7
Port 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7
Port 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7
Server Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8
Choosing the Server Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8
Deployment of One MS and Multiple ESs . . . . . . . . . . . . . . . . . . . . 1-8
CS Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-11
Management Server (MS) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-12
Enforcement Server (ES) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-14
Combination Server (CS) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-14
Changing the Server Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-15
Enforcement Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Enforcement Clusters for an MS and ESs . . . . . . . . . . . . . . . . . . . . . . 1-16
Enforcement Clusters for a CS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16

1-2
Overview of the ProCurve NAC 800
Contents
Endpoint Integrity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-17
Endpoint Integrity Capabilities of the NAC 800 . . . . . . . . . . . . . . . . . 1-18
NAC Tests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-18
NAC Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-20
NAC Policy Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-23
Testing Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-24
NAC EI Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-25
ActiveX . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-26
Agentless . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-27
Endpoint Integrity Posture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-28
Accessible Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-28
Performance Implications of Endpoint Integrity Checks . . . . . . . . . 1-29
Post-Connect Testing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-29
RADIUS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-30
ProCurve NAC 800 RADIUS Capabilities . . . . . . . . . . . . . . . . . . . . . . . 1-31
RADIUS Capabilities of the NAC 800 Integrated with IDM . . . . . . . . 1-32
Deployment Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-33
802.1X Deployment Method . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-34
802.1X Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-34
Types of Access Control Provided by the NAC 800 . . . . . . . . . . . 1-35
802.1X Deployment Method—Endpoint Integrity With or
Without RADIUS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-36
How the NAC 800 Quarantines Endpoints . . . . . . . . . . . . . . . . . . 1-36
How and Where to Deploy the NAC 800 . . . . . . . . . . . . . . . . . . . . 1-38
802.1X Deployment Method—RADIUS Server Only . . . . . . . . . . . . . . 1-43
How and Where to Deploy the NAC 800 . . . . . . . . . . . . . . . . . . . . 1-43
DHCP Deployment Method . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-44
Types of Access Control Provided By the NAC 800 . . . . . . . . . . 1-45
Two Options for a DHCP Deployment . . . . . . . . . . . . . . . . . . . . . 1-45
How and Where to Deploy the NAC 800 for a DHCP Inline
Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-45
How and Where to Deploy the NAC 800 for a DHCP
Plug-in Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-47
How the NAC 800 Quarantines Endpoints for a DHCP
Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-48
Enforcement Methods for DHCP Quarantining . . . . . . . . . . . . . . 1-51
Designing the Quarantine Subnet . . . . . . . . . . . . . . . . . . . . . . . . . 1-52

1-3
Overview of the ProCurve NAC 800
Contents
Inline Deployment Method . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-56
Types of Access Control Provided by the NAC 800 . . . . . . . . . . . 1-57
How the NAC 800 Quarantines Endpoints . . . . . . . . . . . . . . . . . . 1-57
Configuring Accessible Services for Inline Method . . . . . . . . . . . 1-57
How and Where to Deploy the NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-58

1-4
Overview of the ProCurve NAC 800
Introduction
Introduction
The ProCurve Network Access Controller (NAC) 800 is a hardware appliance
that controls endpoints’ access to your network.
It provides these capabilities:
■Endpoint integrity testing—tests endpoints for compliance with a
network’s security policies
■Quarantining—isolates non-compliant endpoints, preventing them from
compromising the network
■Remediation—allows quarantinedendpoints access to services that help
them become compliant
■Reporting—documents endpoints’ status and test results
■Authentication—acts as a RADIUS server and checks users’ credentials
■Post-connect NAC testing—supports additional testing by other secu-
rity software such as an Intrusion Detection System (IDS)/Intrusion Pre-
vention System (IPS)
You will learn about all of these capabilities in this overview chapter.
The remainder of this management and configuration guide will focus on the
final capability: the NAC 800 as a RADIUS server, either integrated with
ProCurve Identity Driven Manager (IDM) or acting on its own.
To learn more about setting up other capabilities, see the ProCurve Network
Access Controller 800 Users’ Guide.

1-5
Overview of the ProCurve NAC 800
Hardware Overview
Hardware Overview
The ProCurve NAC 800 is a hardware appliance that comes in a single model
(J9065A). The device is 1U and mounts on a 19”rack.
You plug the power source into the back panel’s AC power connector.
See the ProCurve Network Access Controller 800 Hardware Installation
Guide for more information on mounting and powering the NAC 800.
All other ports, controls, and information displays are on the front panel for
easy access. These include:
■LEDs
■Console port
■Panel LCD
■Panel buttons
■USB port, which will be supported in future software releases
■Serial number and MAC address
■Two Ethernet ports
Figure 1-1. NAC 800 Front Panel
LEDs
The NAC 800 has three LEDs on its left front panel:
■Power LED—glows green when the device is powered on.
■Fault LED—blinks orange to indicate a problem with the device
■Locator LED—glows blue when you turn the LED on through the menu
interface, identifying which device you are configuring
See “Turn the Locator LED On and Off” on page 2-20 of Chapter 2:
“Management Options for the ProCurve NAC 800.”
■Ethernet Link and Mode LEDs—indicate an open connection, as well
the connection speed

1-6
Overview of the ProCurve NAC 800
Hardware Overview
For more information on LEDs, see the ProCurve Network Access Controller
800 Hardware Installation Guide.
Console Ethernet Port
The console Ethernet port is located beneath the front panel LEDs and enables
out-of-band management. The port accepts an RJ45 connector; use the RJ45
Connector/Console Cable (5188-6699) that ships with your NAC 800. The other
end of this cable connects to a standard console port. Plug it in to your
workstation and open a console terminal session to access the NAC 800’s
menu interface.
Panel LCD and Buttons
The NAC 800’s front panel features an LCD, which initially displays this
information:
■Server type (for example, Combination Server)
■IP address
In addition, the panel has six buttons which you use to interact with the LCD:
■Four arrow buttons (left, right, up, and down)
■An accept button (a checkmark)
■A cancel button (an X)
You can press the accept button to access the panel LCD menu interface and
complete tasks such as:
■Set the server type
■Configure IP settings
■Reboot and shutdown the device
For more information, see “Menu Interface and Panel LCD” on page 2-5 of
Chapter 2: “Management Options for the ProCurve NAC 800.”
Serial Number and MAC Address
The front panel of your NAC 800 displays the device’s serial number, necessary
for generating licenses, and its MAC address.

1-7
Overview of the ProCurve NAC 800
Hardware Overview
Ethernet Ports
The ProCurve NAC 800 contains two 10/100/1000 Base-T ports labelled:
• 1 (left port)
• 2 (right port)
Pay careful attention to which port you connect to a segment of the network:
the NAC 800 handles traffic differently depending on the port on which it
arrives.
To the right of the ports, the NAC 800’s panel features text reminding you of
the purpose of each port, which differs according to the device’s deployment
method. (See “Deployment Methods” on page 1-33.)
Port 1
Port 1 is the port with the NAC 800’s IP address; generally, this port connects
to the network to which the NAC 800 controls access.
The following communications are transmitted and received on port 1:
■Management traffic:
• HTTPS traffic to the NAC 800’s Web browser interface
• SSH traffic
■RADIUS authentication traffic
■Endpoint integrity checking traffic
Port 2
Port 2’s function depends on the selected quarantine method. You will learn
more about the three methods in “Deployment Methods” on page 1-33.

1-8
Overview of the ProCurve NAC 800
Server Types
Server Types
The ProCurve NAC 800 can function as one of three types of server:
■Management server (MS)
■Enforcement server (ES)
■Combination server (CS)
Choosing the Server Type
A NAC 800 deployment can consist of either:
■One MS and multiple ESs
■One CS
Deployment of One MS and Multiple ESs
Set your NAC 800s to the MS and EStypes when you requiremultiple NAC 800s
for your endpoint integrity solution.
To ensure adequate performance, ProCurve Networking recommends that a
single NAC 800 provide integrity testing for no more than 3000 endpoints. An
enforcement cluster of multiple NAC 800s answers the needs of a network
with more users. A enforcement cluster consists of a single MS and multiple
ESs (recommended, between two and five). (See “Enforcement Clusters” on
page 1-16 for a more detailed definition of a cluster.)
Neither an MS nor an ES can function on its own. The MS co-ordinates settings
for allclusters ina system while the ESs test endpoint integrity, or authenticate
users, or both.
The ESs load balance endpoints among themselves; a cluster with five ESs
can provide timely testing for up to 15,000 endpoints (80 percent of the
endpoints in under 30 seconds). A cluster of ESs also provides high availabil-
ity; if one fails, the others continue providing services.
Figure 1-2 illustrates, at a high level, a deployment of multiple NAC 800s.
Table of contents
Other ProCurve Network Hardware manuals
Popular Network Hardware manuals by other brands

TP-Link
TP-Link VIGI NVR1008 installation guide

ATTO Technology
ATTO Technology FastStream VT 5700 Installation and operation manual

TeleEye
TeleEye RX806 User guide lite

National Instruments
National Instruments NI 9203 USER GUIDE AND SPECIFICATIONS

Sensys Networks
Sensys Networks VDS240 installation guide

Fortinet
Fortinet FortiAnalyzer 3700G quick start guide