TANDBERG Gatekeeper User manual
Other TANDBERG Conference System manuals

TANDBERG
TANDBERG Maestro MXP User manual

TANDBERG
TANDBERG D12817-05 User manual

TANDBERG
TANDBERG 880 MXP User manual
TANDBERG
TANDBERG ENTRYPOINT Service manual

TANDBERG
TANDBERG Gatekeeper User manual

TANDBERG
TANDBERG 7000 User manual

TANDBERG
TANDBERG 3000 MXP Profile User manual

TANDBERG
TANDBERG 1500 MXP User manual

TANDBERG
TANDBERG Video Portal Service manual

TANDBERG
TANDBERG Director User manual

TANDBERG
TANDBERG Codec C90 Service manual

TANDBERG
TANDBERG 700 MXP User manual

TANDBERG
TANDBERG 550 MXP User manual
TANDBERG
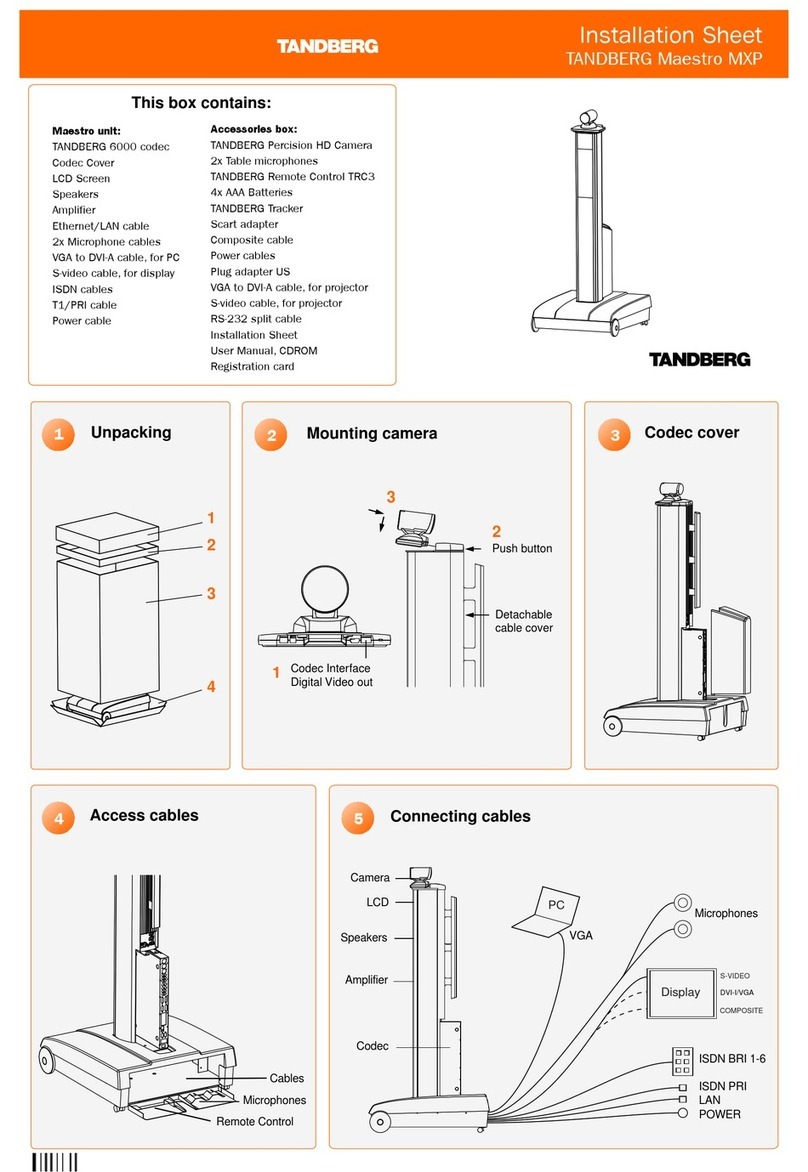
TANDBERG Maestro MXP Assembly instructions

TANDBERG
TANDBERG 7000 MXP User manual

TANDBERG
TANDBERG 3000 MXP Profile User manual

TANDBERG
TANDBERG 8000 MXP Assembly instructions

TANDBERG
TANDBERG 6000 MXP Profile User manual

TANDBERG
TANDBERG 880 MXP Instruction Manual

TANDBERG
TANDBERG Codec C60 Service manual
Popular Conference System manuals by other brands

Kramer
Kramer VIA GO quick start guide

ProSoft Technology
ProSoft Technology AN-X4-AB-DHRIO user manual

Sony
Sony PCS-I150 Operation guide

Middle Atlantic Products
Middle Atlantic Products VTC Series instruction sheet
AVT
AVT MAGIC AC1 Go Configuration guide

Prentke Romich Company
Prentke Romich Company Vanguard Plus Setting up and using