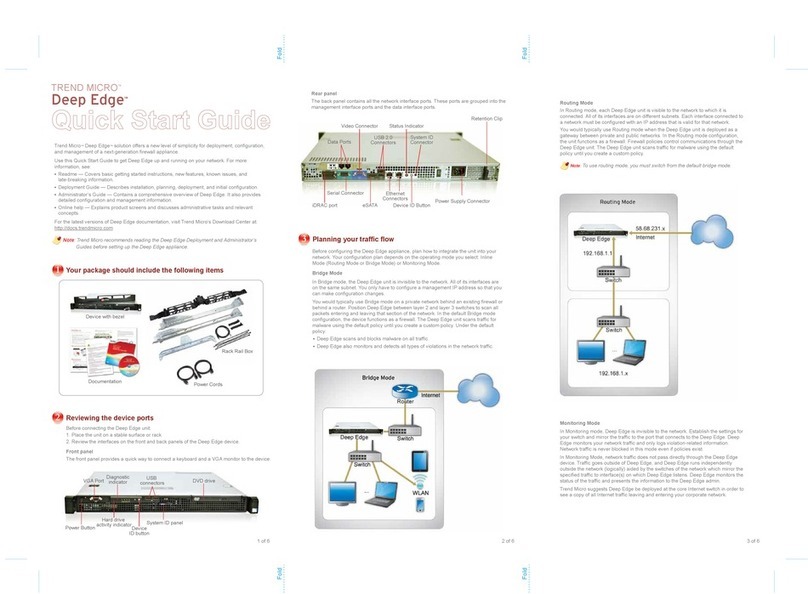
TREND MICROTM
Network VirusWall™ Enforcer 1200 Quick Start GuideQuick Start Guide
After preparing the terminal application, you are ready to access the Preconfiguration console.
To log on to the Preconfiguration console:
1. Power on the device and wait for a welcome message to appear on the LCM panel
(approximately 1-2 minutes).
To power-on a device:
a. Connect the power cord to the AC power receptacle.
b. Connect the power cord to an electrical outlet.
Tip: See Power Requirements and Environmental Specifications in the Getting
Started Guide for power requirements and environmental specifications.
c. Push the power switch to the On position. The Welcome message appears
when the system is successfully powered on.
2. Press Enter. The User name logon prompt displays. If the screen does not display,
type Ctrl + ’r’ or Ctrl + ’l’.
3. Type the default administrator user name and its corresponding password:
User name: admin
Password: admin
Use this login for full access to all preconfiguration features.
4. After logging on, the Main Menu appears.
Log on to the Preconfiguration console
6
6
10
10
11
11
12
12
3. Hardware configuration is now complete. To test the hardware setup and complete
the configuration, relocate to a computer with access to the device and open a Web
browser. Type the IP address of the device to access the Web console.
You can quickly assign Network VirusWall Enforcer 1200 a fixed IP address using the
Preconfiguration console. You will need the information you prepared in step 3.
To configure device settings:
1. On the Main Menu of the Preconfiguration console, type 2 to select Device Settings.
The Device Setting Summary appears.
Note: When configuring the device for the first time, the factory default
settings appear.
2. Type or select the Management IP setting details under Management IP settings.
3. Type a host name that properly represents the device in the network. Trend Micro
recommends a unique descriptive host name to represent and identify the device locally
(through the front panel LCD module) or remotely (through the management console).
Host names may be up to 30 alphanumeric characters ("A-Z, a-z, 0-9 and hyphens "-" can
be used. Spaces are not allowed).
WARNING!
If there is a NAT device in your environment, Trend Micro recommends assigning
a static IP address to the device. Because different port settings are assigned from
your NAT, your device may not work properly if dynamic IP addresses are used.
4. After specifying the device settings, select Return to main menu and press Enter.
5. Select Save and log off. A confirmation message displays.
6. Click OK.
You can register Network VirusWall Enforcer 1200 to Trend Micro Control Manager from
the Device Settings screen. Refer to the Administrator’s Guide for more information.
Configure device settings
7
7
Management/
Mirror port
Port 1 Port 2
Network VirusWall Enforcer 1200 ships with two default accounts - admin and poweruser.
Both accounts use admin and poweruser, respectively, as their default password. Change
the default passwords of these accounts to prevent unauthorized access.
Open the Web console from a desktop or laptop on the network that can access the
device (and is running Internet Explorer version 6.0 or later).
To change default passwords:
1. Type the Network VirusWall Enforcer 1200 IP address in your Web browser’s address field:
http://[IP Address]
where [IP Address] is the IP you just assigned.
2. Type the default administrator user name and its corresponding password:
User name: admin
Password: admin
Log on to the Web console and change the default passwords
9
9
5
5
TREND MICROTMTM
Network VirusWallTMTM Enforcer 1200
Upgrading Network VirusWall Enforcer 1200
To perform the following procedure you will need the Trend Micro Network VirusWall
Enforcer 1200 Solutions CD. To roll back the device after upgrading, perform this process using
the NVW_image_downgrade_2.0.1000.en.us.b file in place of the boot image file (.B file)
and the previous version of the program image in place of the program image (.R file).
To upgrade Network VirusWall Enforcer 1200:
1. Connect to the device using the Console port and Port 1.
2. Specify the IP address of your computer to the same segment as the Network VirusWall
Enforcer 1200 device:
a. Click Start > Control Panel > Network and Internet Connections > Network
Connections. The Network Connections window appears.
b. Right-click the network connection you will use to connect to the Network VirusWall 1200
device. A pop up menu appears.
c. Select Properties. The Connection Properties dialog box appears.
d. Select Internet Protocol (TCP/IP) from the This connection uses the following items
list. Internet Protocol (TCP/IP) highlights in the list.
e. Click Properties. The Internet Protocol (TCP/IP) Properties dialog box appears.
f. Select Use the following IP address and match the first three octets of the IP address in
the IP address field to the IP address of the Network VirusWall Enforcer 1200 device.
For example: If the device IP address is 192.168.252.1, set the IP address for your
computer to 192.168.252.XX (where XX represents a number you specify).
g. Specify the following in the Subnet mask field: 255.255.255.0.
h. Click OK to close the Internet Protocol (TCP/IP) Properties dialog box.
i. Click Close to close the Connection Properties dialog box.
3. Perform Prepare the Preconfiguration console to prepare the Hyper Terminal console
to connect to the Network VirusWall Enforcer device
4. Reset the device by pressing the Reset button on the front panel of the device.
5. After the device reboots, type rin the HyperTerminal console before the Rescue Mode
countdown completes.
6. Insert the Trend Micro Network VirusWall Enforcer 1200 Solutions CD.
7. Locate and execute the nvwrescue.exe file on the Solutions CD. The Trend Micro Network
VirusWall Rescue Utility dialog box appears.
8. Click Browse and import the device boot image (.B file) from the Solutions CD.
9. Click Update in the Trend Micro Network VirusWall Rescue Utility dialog box. The device
uploads the boot image and reboots automatically.
10. Click Finish. When the device reboots a message appears in the HyperTerminal console
prompting you to enter rescue mode.
11. Type rin the HyperTerminal console before the Rescue Mode countdown completes.
12. Locate and execute the nvwrescue.exe file on the Solutions CD. The Trend Micro Network
VirusWall Rescue Utility dialog box appears.
13. Click Browse and import the device program image (.R file) from the Solutions CD.
14. Click Update in the Trend Micro Network VirusWall Rescue Utility dialog box. The device
uploads the program image and reboots automatically.
15. Click Finish. When the device reboots a message appears in the HyperTerminal console
prompting you to enter rescue mode. The device has successfully been upgraded.
16. Do not enter rescue mode. Wait until the rescue mode countdown elapses. The
Preconfiguration console Login screen appears.
3. From the main menu, click Administration > Administrative Accounts.
4. Click a User ID. The Edit Administrative Account screen displays.
5. Type a new password for the account next to Password. Repeat this step next to Password confirm.
6. Click Save.
Change the passwords for each of the two default accounts.
Default Policy
Network VirusWall Enforcer 1200 allows you to create multiple policies directed at different
types of endpoints and traffic. Network VirusWall Enforcer 1200 follows a first-match rule. This
means that once Network VirusWall Enforcer 1200 matches a policy to an endpoint, the
device will no longer search for further matches to the endpoint down the policy list. So,
the device only applies the first policy that matches the endpoint.
Once you have set up Network VirusWall Enforcer 1200, there is one active default sample
policy that matches any source and any destination. Adding new policies pushes older policies
to a lower priority. So to use the broad settings available in the default sample policy, you must
move the default policy to a higher priority. Refer to the Administrator’s Guide for more
information about policy enforcement.
Test and finish setting up Network VirusWall Enforcer 1200
Trend Micro recommends that you update the pattern files and test your installation to confirm
that it works. Instructions for these and other important tasks are described in the Getting
Started Guide and Administrator’s Guide.
After preconfiguration, you must switch off the device before connecting it to the network.
To connect Network VirusWall Enforcer 1200 to your network:
1. Connect one end of a 10/100Mbps Ethernet cable to Port 1 or Port 2 and the other
to a segment of your network.
2. Power on the device.
Note: Network VirusWall Enforcer 1200 can handle various interface speed
(up to 100Mbps) and duplex mode network traffic. See the Getting Started Guide
for more information.
Connect Network VirusWall Enforcer 1200 to your test network
8
8
Item Code: NVEQ02920/61109
© 2006 by Trend Micro Incorporated. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval
system, or transmitted without the prior written consent of Trend Micro Incorporated. Trend Micro, Network VirusWall, and the t-ball logo are
trademarks or registered trademarks of Trend Micro Incorporated. All other company and/or product names may be trademarks or registered
trademarks of their owners. Information contained in this document is subject to change without notice.