ZyXEL Communications ZyAir G-2000 PlusV2 User manual
Other ZyXEL Communications Wireless Router manuals

ZyXEL Communications
ZyXEL Communications Prestige 652 Series User manual

ZyXEL Communications
ZyXEL Communications P-660HW-61 Instruction Manual

ZyXEL Communications
ZyXEL Communications P-336M User manual

ZyXEL Communications
ZyXEL Communications MAX-200M1 Series User manual

ZyXEL Communications
ZyXEL Communications PRESTIGE 334W User manual

ZyXEL Communications
ZyXEL Communications NBG-416N User manual
ZyXEL Communications
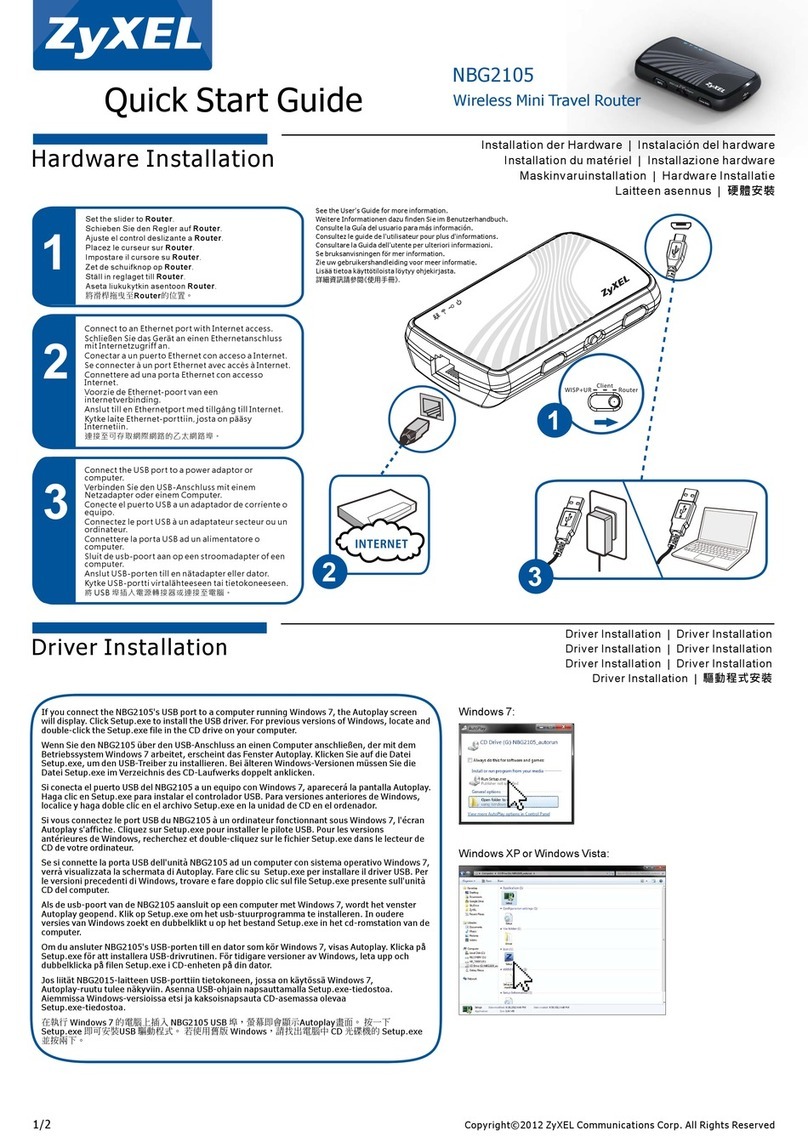
ZyXEL Communications NBG2105 User manual

ZyXEL Communications
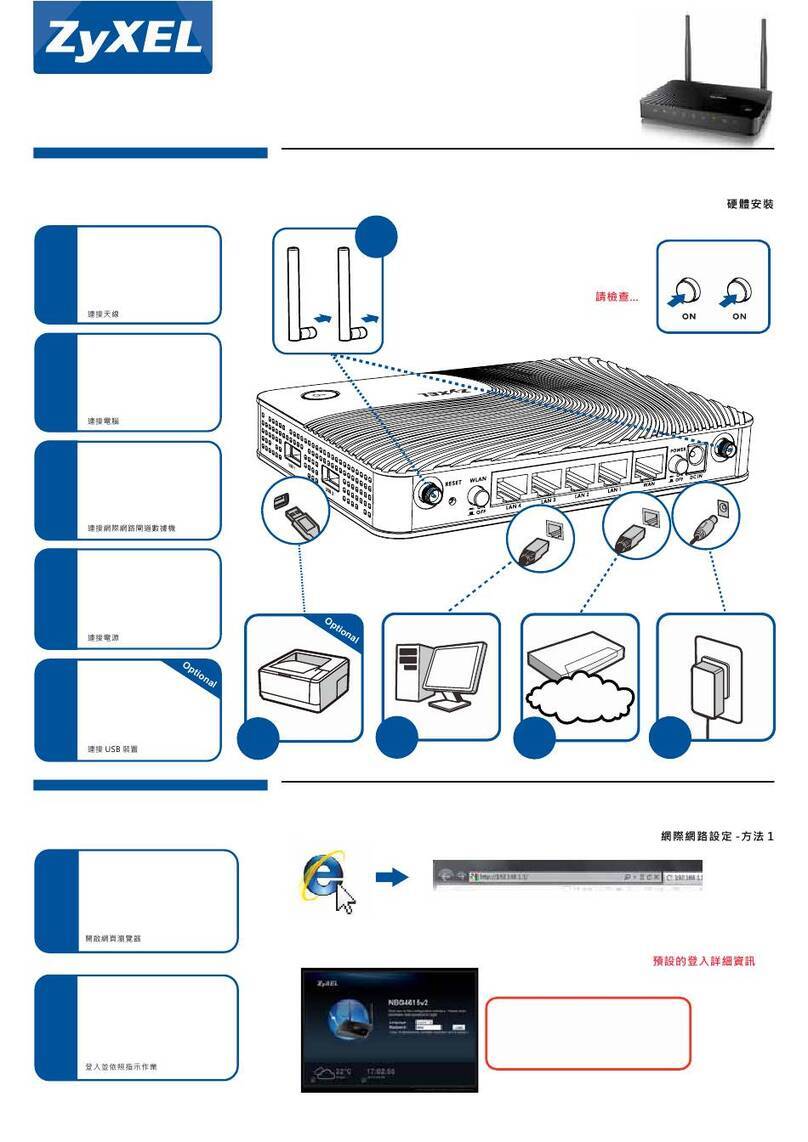
ZyXEL Communications NBG-4615 User manual
ZyXEL Communications
ZyXEL Communications P-2602HWUDL-D User manual

ZyXEL Communications
ZyXEL Communications P-334U User manual

ZyXEL Communications
ZyXEL Communications ZyAir G-2000 PlusV2 Reference guide

ZyXEL Communications
ZyXEL Communications nbg334s User manual

ZyXEL Communications
ZyXEL Communications NR2101 User manual

ZyXEL Communications
ZyXEL Communications Prestige 100IH User manual

ZyXEL Communications
ZyXEL Communications WAH7706 User manual

ZyXEL Communications
ZyXEL Communications NBG2105 User manual
ZyXEL Communications
ZyXEL Communications NBG-4615 User manual

ZyXEL Communications
ZyXEL Communications VSG1432-B101 START V1.10 User manual

ZyXEL Communications
ZyXEL Communications P-320W User manual

ZyXEL Communications
ZyXEL Communications NBG6616 User manual