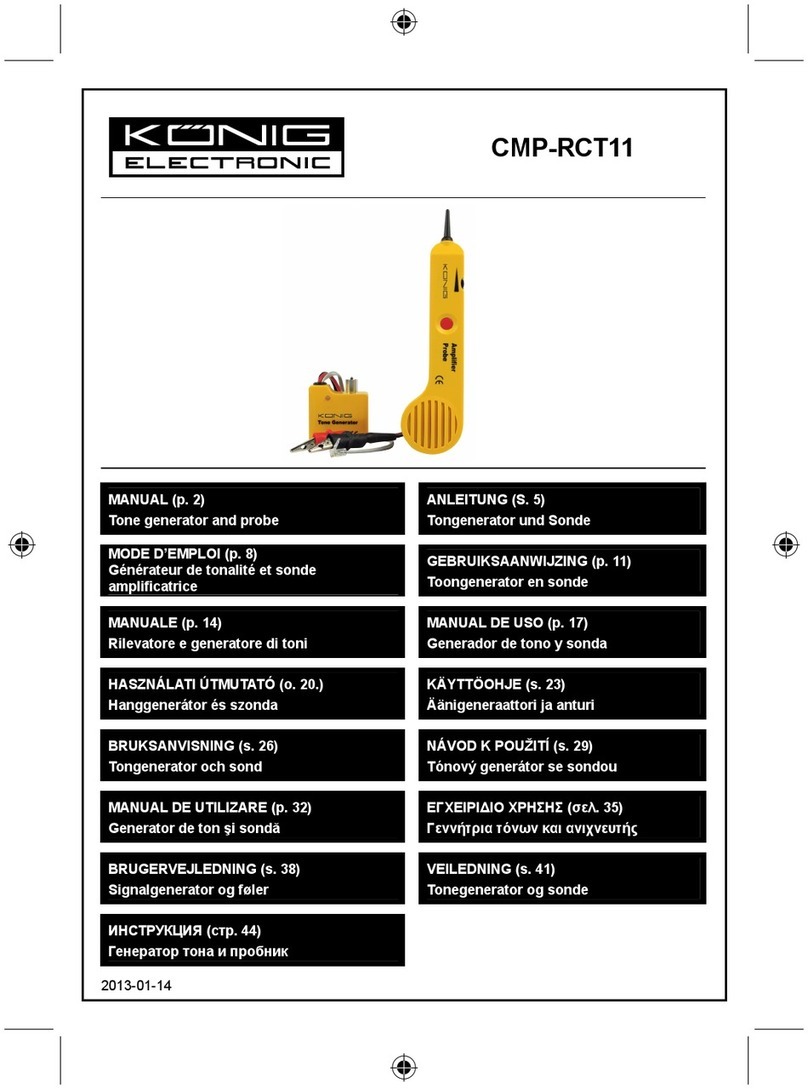
Berkeley Varitronics Systems Mantis User manual

Mantis
manual version 1.4

Page 1
Contents
GETTING STARTED...................................................................................................... 2
MAIN SCREEN........................................................................................................... 2
PRODUCT INFORMATION.............................................................................................. 3
SEARCHING.............................................................................................................. 3
ACQUIRING NAMES..................................................................................................... 3
AVAILABLE DEVICES.................................................................................................... 3
SELECTED DEVICE...................................................................................................... 4
SERVICE.................................................................................................................. 4
MEASUREMENT SELECTION........................................................................................... 4
SIGNAL STRENGTH..................................................................................................... 5
PER........................................................................................................................ 5
OPTIONS.................................................................................................................. 5
USING A DIRECTION FINDING ANTENNA............................................................................ 6
BATTERY TIPS........................................................................................................... 7
NETWORKING BASICS.................................................................................................. 8
GLOSSARY OF ACRONYMS............................................................................................ 10
BLUETOOTH GLOSSARY................................................................................................ 11
GENERAL SAFETY....................................................................................................... 24
ANTENNA RADIATION PATTERNS
MANTIS DATA SHEET

Page 2
Mantis™ is a handheld, wireless transceiver designed
specifically for installing, sweeping and verifying
Bluetooth devices and parameters. The instrument
identifies all nearby Bluetooth devices and their status
in dBm.
Mantis uses common AA battery cells found in any con-
veinence store. Ni-Cad, Alkalines, Ni-MH and Li-Ion
cells may all be used. Mantis does require 4 AA cells
with at least 1500 mAh per cell. BVS supplies 8 Ni-MH
battery cells and a Ni-MH charger to get users working
right out of the box. Ni-MH cells are recommended for
best performance from your Mantis. See the charger’s
instructions and battery tips in this manual.
Mantis also includes a simple 2.4 GHz threaded anten-
na that screws right into the top of the unit. Additional
antennas may be ordered from BVS through BVS.
At the top of the Mantis rest the power switch and
antenna connector. The power switch is a simple two
way toggle switch. The antenna connector (middle) is
an SMA Female 50 ohm. The provided antenna easily
screws and unscrews from this connector. Be sure to
unscrew antenna when transporting the Mantis.
GETTING STARTED
Operation of the Mantis is straightforward. Insert 4
fresh battery cells into removable pack. Close back up
and power on the Mantis. The Mantis will display the
startup screen followed by the Main Screen.
Mantis Main Screen
Use the UP/DOWN arrows to scroll through menu
selections. Push the RIGHT arrow button to make a
selection and push the LEFT button to move back one
previous screen.

Page 3
Product Information
This screen displays the current version of Mantis that
you are using. Visit www.bvsystems.com to find out if
you have the latest Mantis version.
Searching...
From the Main Screen, select Search for Devices and
press the RIGHT arrow key. This screen will appear.
Mantis takes approximately 10 seconds for a complete
scan of nearby Bluetooth devices. The devices found
will be listed by their ID numbers first.
Acquiring Names...
After acquiring the ID of each device, Mantis will go
back and list the name given to each device (up to 20
characters).
Available Devices
After the 10 second scan, Mantis will list all Bluetooth
devices found that are currently powered and opera-
tional. Use the UP and DOWN arrow keys to scroll
through the list of devices. Mantis creates a list of
up to 16 devices at once. Once you have selected the
device you wish to verify, press the RIGHT arrow key to
select that device. Press the LEFT arrow key at anytime
to return to the previous menu.

Page 4
Selected Device
This screen provides basic information about the
device including the ID number, the name and the
class. Class is an attribute assigned by the Bluetooth
standard. Here are some common classes:
Use the DOWN arrow key to see Service information for
the selected Bluetooth device.
Service
This screen provides basic Service information regard-
ing the nature and capabilities of the selected Bluetooth
device. An x to the left of any category identifies it as a
known Service. Use the DOWN arrow key to see more
Service information for the selected Bluetooth device.
Service (continued)
You may use the UP arrow key to scroll back up to
the top of the Service list. Use the LEFT arrow key to
return back to the Main Screen. Use the RIGHT arrow
key to see the Signal Strength of the selected Bluetooth
device.
Measurement Selection
Select the type of measurement you wish to make using
the UP or DOWN arrow key. After you select either RSSI
or PER, use the RIGHT arrow key to continue to the
desired measurement screen.

Signal Strength
This screen indicates the current received signal
strength of the selected Bluetooth device in dB on a
scale from -20 to 20 dB. The orange receive LED on
the front of the Mantis will blink whenever any data
is received. Use the arrow keys to return to the Main
Screen or perform another Search.
Note: A transceiver that wishes to support power-con-
trolled links must be able to measure the strength of
the received signal and determine if the transmitter on
the other side of the link should increase or decrease
its output power level. A Receiver Signal Strength
Indicator (RSSI) makes this possible.
The RSSI measurement compares the received signal
power with two threshold levels, which define the
Golden Receive Power Range. The lower threshold
level corresponds to a received power between -56
dBm and 6 dB above the actual sensitivity of the
receiver. The upper threshold level is 20 dB above the
lower threshold level to an accuracy of + 6 dB.
(BLUETOOTH SPECIFICATION Version 1.1)
PER
This screen indicates the PER (Packet Error Rate) of
the selected Bluetooth device from 0 to 100 percent. A
PER of 0% indicates optimal transmission of Bluetooth
data packets.
OPTIONS
Mantis provides two privacy options. To enable or
disable an option, use the UP or DOWN arrow keys to
select the option and the RIGHT arrow key to toggle the
enabled “X” on or off. The LEFT arrow key returns to
Main screen.
Page Scan Enabled
When enabled, Mantis answers page scans from other
Bluetooth devices. Page scans provide the Bluetooth
Page 5

Page 6
MAC address and information about features the device has. Disabling this option prevents the Mantis from
being seen by other Bluetooth devices. The default is enabled.
Send Friendly Name
When enabled, Mantis responds to requests for a user friendly name with “BVS Mantis Bluetooth Tester”.
When disabled, it responds with a blank string.
USING A DIRECTION FINDING ANTENNA
Mantis ships with an optional Directon Finding Antenna for locating
and pinpointing local Bluetooth devices. This antenna may be removed
at anytime and replaced with the standard omni-directional antenna.
See antenna specifications and guidelines below.
2.4 GHz Direction Finding
Corner Reflector Screw SMA cable
into connector
here.
Secure these screws to
the top of Mantis case.

BATTERY TIPS
The Mantis™, Grasshopper™, Locust™, Yellow Jacket™ and Yellow Jacket Plus (fomally called Scorpion), Beetle™,
Cricket™, and Cicada W-LAN receivers use 4 or 5 Ni-MH long-lasting “AA Cells”.
1. Ni-MH batteries do not charge to full capacity the first time they are charged.
2. Ni-MH batteries do not charge to full capacity the first time they are charged after a long period of inactivity. or after a long
period of non-use.
Cause:
When charging Ni-MH batteries for the first time after long-term storage, deactivation of reactants may lead to increased
battery voltage and decreased capacity, (which causes premature termination of charging). Because batteries are chemical
products involving internal chemical reactions, performance deteriorates with prolonged storage. This is normal in Ni-MH bat-
teries.
Resolution:
Ni-MH batteries may not charge to full capacity the first time they are charged, or after a long period of inactivity.
The first-time charge of the Ni-MH Rechargeable Battery Pack should take approximately 2 hours. If the Receiver Dock light
turns green, indicating a full charge, in less than 2 hours, repeat the charge cycle as follows:
First-time Charge:
1. To begin charging, place the instrument on the Charge Dock. Refer to your instrument’s User Guide for details.
2. When the charge light turns green, remove the W-LAN Receiver from the dock and place back on the dock after several
seconds.
3. Repeat steps 1 and 2 three or four times or until the combined charge time is 2 hours.
Subsequent charges of the W-LAN Ni-MH Battery Pack will not require multiple charging cycles unless left uncharged for a
long period of time (greater than 2 months).
Networking Basics
Packets and traffic
Information travels across a network in chunks called “packets.” Each packet has a header that tells where
the packet is from and where it’s going, similar to what you write on the envelope when you send a letter.
The flow of all these packets on the network is called “traffic.”
Hardware addresses
Your PC “listens” to all of the traffic on its local network and selects the packets that belong to it by check-
ing for its hardware address in the packet header or MAC (Media Access Control). Every hardware product
used for networking is required to have a unique hardware address permanently embedded in it.
IP addresses
Since the Internet is a network of networks (connecting millions of computers), hardware addresses alone
are not enough to deliver information on the Internet. It would be impossible for your computer to find its
packets in all the world’s network traffic, and impossible for the Internet to move all traffic to every net-
work, your PC also has an IP (Internet Protocol) address that defines exactly where and in what network
it’s located. IP addresses ensure that your local Ethernet network only
receives the traffic intended for it. Like the hierarchical system used to define zip codes, street names,
and street numbers, IP addresses are created according to a set of rules, and their assignment is carefully
administered.
Page 7

Put another way, the hardware address is like your name; it uniquely and permanently identifies you. But it
doesn’t offer any clues about your location, so it’s only helpful in a local setting. An IP address is like your
street address, which contains the information that helps letters and packages find your house.
Rules for Sending Information (Protocols)
A protocol is a set of rules that define how communication takes place. For instance, a networking proto-
col may define how information is formatted and addressed, just as there’s a standard way to address an
envelope when you send a letter.
Networking Devices:
Bridges
A bridge joins two networks at the hardware level. This means that as far as other protocols are concerned,
the two networks are the same.
Routers
A router connects two IP networks. In contrast to a bridge, which joins networks at the hardware level, a
router directs network IP traffic based on information stored in its routing tables. A routing table matches
IP addresses with hardware addresses. The router stamps each incoming IP packet with the hardware
address that corresponds to that IP address. As a result, the packet can be picked up by the right computer
on the hardware network.
DNS (Domain Name Server)
Networks (domains) on the Internet have names that correspond to their IP addresses. A Domain Name
Server maintains a list of domain names and their corresponding addresses. This is why you can go to
Berkeley’s Web site by entering www.bvsystems.com, instead of the IP address.
Networking Terms:
TCP/IP (Transport Control Protocol/Internet Protocol)
TCP/IP is a collection of protocols that underlies almost every form of communication on the Internet.
DHCP (Dynamic Host Control Protocol)
DHCP is a method of automatically assigning IP addresses. Instead of assigning addresses to individual
users, addresses are assigned by the DHCP server when clients need them. This means that instead of
entering several fields of long addresses, users need only to select DHCP as their configuration method
for IP networking.
PPP (Point-to-Point Protocol)
PPP is the most common protocol for providing IP services over a modem.
NAT (Network Address Translation)
NAT is used to share one IP address among several computers. A device set up as a NAT router uses a col-
lection of “private” IP addresses (in the range 10.0.1.2 to 10.0.1.254 for example) to allow several com-
puters to access the Internet using one “public” IP address. When a computer using a private IP address
requests information from the Internet, the NAT router keeps a record of the computer making the request,
and sends the information to the Internet using its own IP address. When the response comes back from
the Internet, the NAT router forwards the packet to the appropriate computer.
Page 8

Glossary of Acronyms
AC Alternating Current
A/D Analog to Digital converter
AGC Automatic Gain Control
AP Access Point
Applet a small Application
BER Bit Error Rate
BPSK Binary Phase Shift Keying
BSS Basic Service Set
BW Band Width
CDMA Code Division Multiple Access (spread spectrum modulation)
DC Direct Current
D/A Digital to Analog
dB decibel
dBm decibels referenced to 1 milliwatt
DOS Digital Operating System
DSP Digital Signal Processing
DSSS Direct Sequence Spread Spectrum
ESS Extended Service Set
FIR Finite Impulse Response
GHz GigaHertz
IF Intermediate Frequency
I and Q In phase and Quadrature
IBBS Independent Basic Service Set
kHz kiloHertz
LCD Liquid Crystal Display
LO Local Oscillator
MAC Medium Access Control
Mbits Megabits
MHz MegaHertz
NIC Network Interface Card
OFDM Orthogonal Frequency Domain Multiplexing (802.11a)
PC Personal Computer
PCS Personal Communications Service (1.8 to 2.1 GHz frequency band)
PER Packet Error Rate
PN Pseudo Noise
QPSK Quaternary Phase Shift Keying, 4-level PSK
RF Radio Frequency
RSSI Receiver Signal Strength Indicator
SSID Service Set IDentification
UCT Universal Coordinated Time
VAC Volts Alternating Current
VGA Video graphic
WLAN Wireless Local Area Network
Page 9

Bluetooth Glossary
ACK
Acknowledge.
ACL
Bluetooth Asynchronous Connectionless Link. An Asynchronous packet-switched connection between two
devices created on the LMP level. ACL link is primarily used for data transmission. Bluetooth links are
either of the ACL type or SCO type. See also SCO.
Active Mode
The operational status of a slave Bluetooth unit within a Piconet. In the active mode, the Bluetooth unit
actively participates on the channel. The master schedules the transmission based on traffic demands to
and from the different slaves. In addition, it supports regular transmissions to keep slaves synchronized to
the channel. Active slaves listen in the master-to-slave slots for packets. If an active slave is not addressed,
it may sleep until the next new master transmission. Bluetooth supports up to seven active slaves within
a Piconet.
AG
Audio Gateway. See also HS profile.
AM_ADDR
Bluetooth Active Member Address. A temporary address assigned to an active member of a Piconet. The
AM-ADDR may be assigned 1 through 7 where zero denoted the Piconet broadcast address. See also
BD_ADDR, which refers to the fixed MAC address of a Bluetooth device.
AP
Access Point. A hardware / software entity which provides the Bluetooth unit access to some external net-
work. See also LAP and NAP.
API
Application Programming Interface.
Application Layer
The group of protocols at the user level. The application layer in the Bluetooth protocol layers will contain
those protocols involved with the user interface (UI).
AR_ADDR
Bluetooth Access Request Address. AR_ADDR is assigned to a parking slave by the master. The ARADDR
is used by parked slaves w hen initiating a request for unparking.
ARQ
Automatic Repeat reQuest. An error control scheme in which packets are either acknowledged or retrans-
mitted. An ARQ scheme provides a reliable communication link and is implemented in the Bluetooth base-
band layer.
AT Command Handler
A module that handles the AT commands which control a phone or modem (between a DTE and a DCE).
authentication The process of verifying the identity of the device on the other end of the link. Bluetooth
authentication procedure is based on the stored link key or by entering a passkey (PIN) (also referred to
Page 10

as pairing).
authenticated device
A device whose identity has been verified during the lifetime of the current link based on the authentication
procedure.
authenticate using a passkey
The procedure where a user is requested to enter a passkey during the link establishment procedure, where
the devices did not share a common link key beforehand. This differs from the bonding procedure where
the user enters the passkey without it being requested.
authorization
The process of deciding if a certain device is allowed to have access to a specific service. This is where
the concept of trust exists. Trusted devices (the device is authenticated and indicated as “trusted”), are
allowed access services. Un -trusted or unknown devices may require authorization based on user interac-
tion before it is allowed access to the services. Authorization always includes authentication.
BAP
Bluetooth Access Point
BB, BaseBand
A Bluetooth layer. The baseband describes the specifications of the digital signal processing part of the
hardware -- the Bluetooth link controller, which carries out the baseband protocols and other low -level
link routines.
BD_ADDR
Bluetooth Device Address. A unique 48-bit address, distinguishing between different Bluetooth transceiv-
ers.
Bluetooth
An open specification for wireless communication of data and voice. It is based on a low -cost short-range
radio link facilitating protected ad hoc connections for stationary and mobile communication environ-
ments.
Bluetooth clock
The master timing mechanism defined by the master of the piconet. Every Bluetooth unit has an internal
system clock, which determines the timing and hopping of the transceiver.
Bluetooth device class
A parameter that indicates the type of device and which types of services that are supported. The class is
received during the discovery procedure.
Bluetooth passkey
The name of the Bluetooth PIN code . The term “Bluetooth passkey” is used in the UI. See Bonding.
BNEP
Bluetooth Network Encapsulation Protocol. The protocol to be used by the Bluetooth PAN profiles. This layer
encapsulates packets from various networking protocols, which are transported directly over the
L2CAP Layer.
Page 11

bonding
Bonding is the creation of a relationship between two devices. The bond is a link key. The relationship is
created when the link key is exchanged between two devices. The devices are known to each other prior
to the bonding procedure. A user initiates the bonding procedure and enters a passkey with the explicit
purpose of creating a bond between two devices. This differs from the authentication using a passkey pro-
cedure where the user is requested to enter a passkey during the establishment of the link.
Browser
An application that allows interaction with Internet web pages.
BT
Bluetooth.
channel
In Bluetooth, a logical connection on L2CAP layer between two devices serving a single application or
higher layer protocol.
Circuit Switched
The application of a network where a dedicated resources are used to transmit information. Only one user
may employ the line resources at a time.
Circuit Switched Bluetooth
The application of a Bluetooth network where dedicated time slots are used to transmit Bluetooth data.
See also SCO.
CL
Connectionless.
class of device , CoD
See Bluetooth device class. Also abbreviated as CoD.
CO
Connection-oriented.
CODEC
Coder/Decoder. A device that converts analog to digital, and digital to analog for transmission over a digi-
tal communications system. The Codec sometimes also applies additional digital processing.
connect to service
The establishment of a connection to a service. If not already done, this includes establishment of a physi-
cal link, link and channel connection as well.
connectable device
Any Bluetooth device within range that will respond to paging and set-up connection.
CP
Capability Provider. A Capability Provider is a module within the local device that provides a service to
other modules. Protocol stack modules (RFCOMM, L2CAP) are Capability Providers. So are “application
interface modules” such as OBEX and CTS-AT. In fact, any module that registers a port that other modules
can connect to is a Capability Provider.
Page 12

CT profile
Cordless Telephony Profile. Defines the protocols and procedures that shall be used by devices implement-
ing the ‘3-in-1 phone’ use case. The entities defined in this profile are gateway (GW) and terminal (TL).
CVSD
Continuous Variable Slope Delta Modulation. A robus t voice modulation method.
DAC
Device Access Code. It is used during page, page scan and page response sub-states. It is a code derived
from the unit’s BD_ADDR.
DCE
Data Circuit-Terminating Equipment. In serial communications, DCE refers to a device in-between the
communication endpoints . The task of the DCE is to facilitate the communications process within the com-
munication network; typically a modem. See also DTE.
Device Discovery
The mechanism to request and receive the Bluetooth address, clock, and class of device, used page scan
mode, and names of devices.
device security level
Access to a device can be denied based on the required device security level. There are two levels of
device security: trusted device and un-trusted device. See also service security level.
DH
Data-High Rate. Data packet type used with ACL link for high rate data. See also DM.
discoverable device
A Bluetooth device in range that will respond to an inquiry message.
DM
Data - Medium Rate. Data packet type used with ACL link for medium rate data. See also DH.
DTE
Data Terminal Equipment. In serial communications, DTE refers to a device at the endpoint of the com-
munications path; typically a computer or terminal.
DTMF
Dual Tone Multiple Frequency.
DUN profile
Dial Up Network profile. Defines the protocols and procedures that shall be used by devices implementing
the usage model called ‘Internet Bridge’ (typically modems and cellular phones). The entities defined in
this profile are gateway (GW) and data terminal (DT).
DV
Data Voice. Data packet type use with SCO link for data and voice.
E1/T1
Page 13

The most common standard distribution interface. European E1 provides 2.048 Mbps in 30 64-kbps voice
channels + 2 64kbps signaling channels, while American T1 provides 1.544 Mbps in 24 64-kbps voice
channels + a single 8kbps framing channel.
FEC
Forward Error Correction.
FH
Frequency Hopping.
GA profile
Generic Access profile. Describes requirements related to modes and access procedures that are to be
used by transport and application profiles. Most important, this profile defines discovery, link establish-
ment and security procedures. The entities defined in this profile are tw o Bluetooth devices.
GFSK
Gaussian Frequency Shift Keying. This is the modulation used in the radio layer of the Bluetooth system.
GOE profile
Generic Object Exchange Profile. The most basic Bluetooth profile. Defines modes and access procedures
that are to be used by transport and application profiles. The entities defined in this profile are client and
server.
HA
Host Application. A software program that uses Bluetooth.
HCI
Host Controller Interface. A protocol Stack Layer that provides a command interface to the LMP and
Baseband layers.
Hold mode
Devices synchronized to a piconet can enter power -saving modes in which device activity is lowered. The
master unit can put slave units into HOLD mode, where only an internal timer is running. Slave units can
also demand to be put into HOLD mode. Data transfer restarts instantly when units transition out of Hold
mode. It has an intermediate duty cycle (medium power efficient) of the 3 power saving modes: sniff, hold
and park.
host
A software and hardware platform in which the Bluetooth package runs.
HS profile
Headset Profile. Defines the protocols and procedures that shall be used by devices implementing the
usage model called ‘Ultimate Headset’. The entities defined in this profile are headset (HS) and audio
gateway (AG, typically a cellular phone).
HSM
Host-specific Mechanism.
HV
High quality Voice. An SCO link voice packet. HV packets do not have a CRC and are never retransmitted.
Page 14

Idle mode
A device is in idle mode when it has no established links to other devices. In this mode, the device may
discover other devices. In general, a device sends inquiry codes to other devices. Any device that allows
inquiries will respond with information. The device might then decide to establish a link.
initiator
The Bluetooth device initiating an action to another Bluetooth device. The device receiving the action is
called the acceptor. The initiator is typically part of an established link.
Inquiry Procedure
The inquiry procedure enables a device to discover which devices are in range, and determine the address-
es and clocks for the devices. After the inquiry procedure has completed, a connection can be established
using the paging proc edure. Note: a device should by in Inquiry scan mode to be discovered.
intelligent peripheral
A peripheral that is capable of exchanging information with the handset. Information may include battery
status, charging status, data storage status, or other high-level functionality. Also referred to as a smart
peripheral.
Internet Bridge
Method of using a wireless modem for connecting to Internet access.
IP
Internet Protocol. The protocol by which data is sent from one computer to another on the Internet.
ISM
Industrial, Scientific, Medical - the unlicensed frequency band in which Bluetooth operates (2.4 –2.483
GHz).
Key Management
The handling and control of encryption keys.
known device
A device for which at least the BD_ADDR is stored.
L2CAP
Logical Link Controller and Adaptation Protocol. The data link layer of the Bluetooth protocol stack. This
layer of the Bluetooth protocol stack supports higher -level protocol multiplexing, packet segmentation and
reassembly, and the conveying of quality of service information.
L_CH
Logical Channel. A channel that is used to transmit data over a physical Bluetooth link.
LA profile
LAN access profile. Defines LAN Access using PPP over RFCOMM. The entities defined in this profile are
LAN Access point (LAP) and Data terminal (DT).
LAN
Local Area Network. A group of computers and associated devices that share a common communications
Page 15

line and typically share the resources of a single server within a local geographic area (for example, within
an office building).
LAP
LAN Access Point. One of the entities defined in the LA profile. The LAP is an AP, which acts like a router
between a Bluetooth Piconet and an external Network.
link
Shorthand for an ACL link.
LC
Link Controller. The Link Controller manages the link to the other Bluetooth devices. It is the low-level
baseband protocol handler.
LCP
Link Control Protocol.
link key
The authentication key used to establish a link between devices. See also bonding.
LM
Link Manager. The Link Manager software entity carries out link setup, authentication, link configuration,
and other aspects of managing the Bluetooth physical link. Resides w ithin the Bluetooth hardware.
LMP
Link Manager Protocol. Defines communication procedures between link managers.
LMP-authentication
An LMP level procedure for verifying the identity of a remote device. The procedure is based on a chal-
lenge-response mechanism using a random number, a secret key and the BD_ADDR of the noninitiating
device. The secret key used can be a previously exchanged link key or an initialization key created by using
a PIN (as used when pairing).
lmp-pairing
A LMP procedure that authenticates two devices based on a PIN and subsequently creates a common link
key that can be used as a basis for a trusted relationship or a (single) secure connection. The procedure
consists of the steps: (1) creation of an initialization key (based on a random number and a PIN), (2) lmp-
authentication based on the initialization key, and (3) creation of a common link key.
LocDev
Local Device. A Bluetooth device which initiates a SDP procedure. A Local Device is typically a master
device on the piconet. However, a Local Device may not always have a master connection relationship to
other devices. See also RemDev.
MAC
Media Access Control.
MAC Address
3-bit address to distinguish between units participating in the piconet.
Page 16

Management Entity
Management Entity. The portion of the Bluetooth implementation that mediates the internal functions of
the Bluetooth stack.
master device
A device that initiates an action or requests a service on a piconet. See also LocDev. The Master’s BD_ADDR
and clock are used to generate the frequency hopping sequence of all Bluetooth devices in the piconet.
MTU
Maximum Transmission Unit. The largest size packet or frame, specified in bytes, that can be sent in a
packet or frame-based network.
NAK
Negative Acknowledge.
Name Discovery
The mechanism to request and receive a device name.
NAP
Network Access Point. One of the entities defined in the PAN profile. The NAP is an AP, which acts like a
bridge or a router between a Bluetooth Piconet and an external Network.
non-connectable mode
A device that does not respond to paging (an attempt to establish a communication link) is said to be in
non-connectable mode. See also connectable mode.
non-discoverable , non-discoverable mode
A device that cannot respond to an inquiry is said to be in non-discoverable mode.
non-pairable mode
A device that does not accepts pairing is said to be in non-pairable mode. The opposite of non-pairing
mode is pairable mode.
OBEX
OBject EXchange Protocol - protocol defining a way to exchange data objects between devices. Adapted
to Bluetooth from the IrDA standard.
Packet Switched
A network that routes data packets based on an address contained in the data packet is said to be a packet
switched network. Multiple data packets can share the same network resources.
Packet Switched Bluetooth
The application of routing Bluetooth data packets on a network using addresses contained in the Bluetooth
data packets. A baseband state where a device transmits page messages and processes any eventual
responses.
Page Scan state
A mode where a device listens for page messages containing its own device access code (DAC).
Page state
Page 17

A mode that a device enters when searching for services. The LocDev sends out a page to notify other
devices that it wants to know about the other devices and/or their services.
paged device
A paged device is typically contacted by a paging device to establish a communication link.
paging
A procedure of attempting to establish a communication link.
paging device
A paging device is typically attempting to establish a communication link with other devices. See initia-
tor.
Paging Procedure
With the paging procedure, an actual connection can be established. The paging procedure typically follows
the inquiry procedure. Only the Bluetooth device address is required to set up a connection. Knowledge
about the clock will accelerate the setup procedure. A unit that establishes a connection will carry out a
page procedure and will automatically be the master of the connection.
pairable mode
A device that accepts pairing. is said to be in pairable mode. The opposite of pairing mode is nonpairable
mode.
paired device
A device with which a link key has been exchanged (either before connection establishment was requested
or during connecting phase). See also pre-paired device and un-paired device.
pairing
The creation and exchange of a link key between two devices. The devices (LocDev and RemDev) use the
link key for future authentication when exchanging information. Pairing procedure is based on a common
link key. The link key is also referred to as a bond. Pairing can also establish a link by the user entering a
PIN, which is authenticated by the device providing the service.
PAN
Personal Area Network. A group of mobile communication and computing devices that share a small geo-
graphic space (for example, a room) , within which they have non-wired communication channel (typically
based on radio w aves or infrared).
PAN profile
Personal area network profile. A Bluetooth profile that describes how two or more Bluetooth enabled
devices can form an ad-hoc network and how the same mechanism can be used to access a remote network
through a network access point. The entities defined in this profile are PAN user (PANU), network access
point (NAP) and group ad-hoc network (GAN).
Park mode
In the PARK mode, a device is still synchronized to the piconet but does not participate in the traffic. Parked
devices have given up their MAC address and occasional listen to the traffic of the master to resynchronize
and check on broadcast messages. It has the lowest duty cycle and best power efficiency of all 3 power
saving modes: Sniff, Hold and Park.
Page 18

PCMCIA
Personal Computer Memory Card International Association.
PDA
Personal Digital Assistant.
Phone Services Database
The portion of the Bluetooth implementation that stores information about device services, both local
services and remote services.
Physical channel
A synchronized Bluetooth RF hoping sequence in a piconet.
Piconet
A collection of devices connected via Bluetooth wireless technology in an ad hoc fashion. A piconet starts
with two connected devices, such as a portable PC and an Access Point, and may grow to eight connected
devices. All Bluetooth devices are peer units and have identical implementations. However, when esta
lishing a piconet, one unit will act as a master and the other(s) as slave(s) for the duration of the piconet
connection. All devices hare the same physical channel utilizing the same Frequency-hopping sequence,
defined by the master device clock and BD_ADDR.
PIM
Personal Information Manager.
PIN
Personal Identification Number. The Bluetooth PIN is used to authenticate two devices that have not previ-
ously exchanged link key. By exchanging a PIN, the devices create a trusted relationship. The PIN is used
in the pairing procedure to generate the initial link that is used for further identification.
PIN(BB)
The PIN used on the baseband level. The PIN(BB) is used by the baseband mechanism for calculating the
initialization key during the paring procedure. (128 bits)
PIN(UI)
The PIN used on the user interface level. The PIN(UI) is the character representation of the PIN that is
entered on the UI level.
POTS
Plain Old Telephone system. A landline telephone connection system.
PPP
Point-to-Point Protocol. A way of implementing the IP and other networking protocols over a dial-up or
other serial link.
pre-paired device
A device with which a link key was exchanged, and, before link establishment. See also paired device and
un-paired device.
PRNG
Pseudo Random Noise Generation.
Page 19
Table of contents
Other Berkeley Varitronics Systems Test Equipment manuals

Berkeley Varitronics Systems
Berkeley Varitronics Systems Cicada User manual

Berkeley Varitronics Systems
Berkeley Varitronics Systems Gazelle User manual

Berkeley Varitronics Systems
Berkeley Varitronics Systems Squid-4G Setup guide

Berkeley Varitronics Systems
Berkeley Varitronics Systems Grasshopper User manual
Popular Test Equipment manuals by other brands

DL-Systeme
DL-Systeme LTG 750 Instructions for use

SPX
SPX GE-50576-A User's operation manual

Keysight Technologies
Keysight Technologies 16454A Operation and service manual

Würth
Würth 1952 006 920 Translation of the original operating instructions

Testboy
Testboy TB 50 operating instructions

Volvo
Volvo Alcolock operating instructions