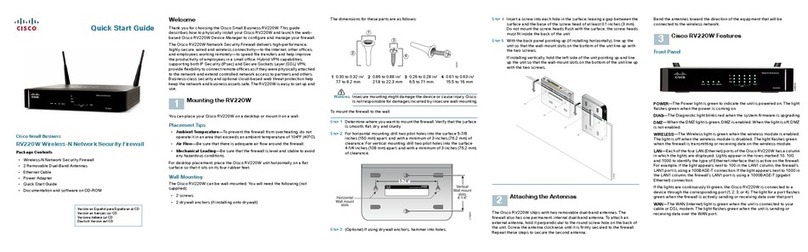
1-2
Firepower 7000 and 8000 Series Installation Guide
Chapter 1 Introduction to the Firepower System
Firepower System Appliances
Firepower System Appliances
A Firepower System appliance is either a traffic-sensing managed device or a managing Firepower
Management Center:
Physical devices are fault-tolerant, purpose-built network appliances available with a range of
throughputs and capabilities. Firepower Management Centers serve as central management points for
these devices, and automatically aggregate and correlate the events they generate. There are several
models of each physical appliance type; these models are further grouped into series and family. Many
Firepower System capabilities are appliance dependent.
Firepower Management Centers
A Firepower Management Center provides a centralized management point and event database for your
Firepower System deployment. Firepower Management Centers aggregate and correlate intrusion, file,
malware, discovery, connection, and performance data, assessing the impact of events on particular hosts
and tagging hosts with indications of compromise. This allows you to monitor the information that your
devices report in relation to one another, and to assess and control the overall activity that occurs on your
network.
Key features of the Firepower Management Center include:
•device, license, and policy management
•display of event and contextual information using tables, graphs, and charts
•health and performance monitoring
•external notification and alerting
•correlation, indications of compromise, and remediation features for real-time threat response
•custom and template-based reporting
Managed Devices
Devices deployed on network segments within your organization monitor traffic for analysis. Devices
deployed passively help you gain insight into your network traffic. Deployed inline, you can use
Firepower devices to affect the flow of traffic based on multiple criteria. Depending on model and
license, devices:
•gather detailed information about your organization’s hosts, operating systems, applications, users,
files, networks, and vulnerabilities
•block or allow network traffic based on various network-based criteria, as well as other criteria
including applications, users, URLs, IP address reputations, and the results of intrusion or malware
inspections
•have switching, routing, DHCP, NAT, and VPN capabilities, as well as configurable bypass
interfaces, fast-path rules, and strict TCP enforcement
•have high availability (redundancy) to help you ensure continuity of operations, and stacking to
combine resources from multiple devices
Yo u must manage Firepower devices with a Firepower Management Center.
Appliance Types
The Firepower System can run on fault-tolerant, purpose-built physical network appliances available
from Cisco. There are several models of each Firepower Management Center and managed device; these
models are further grouped into series and family.