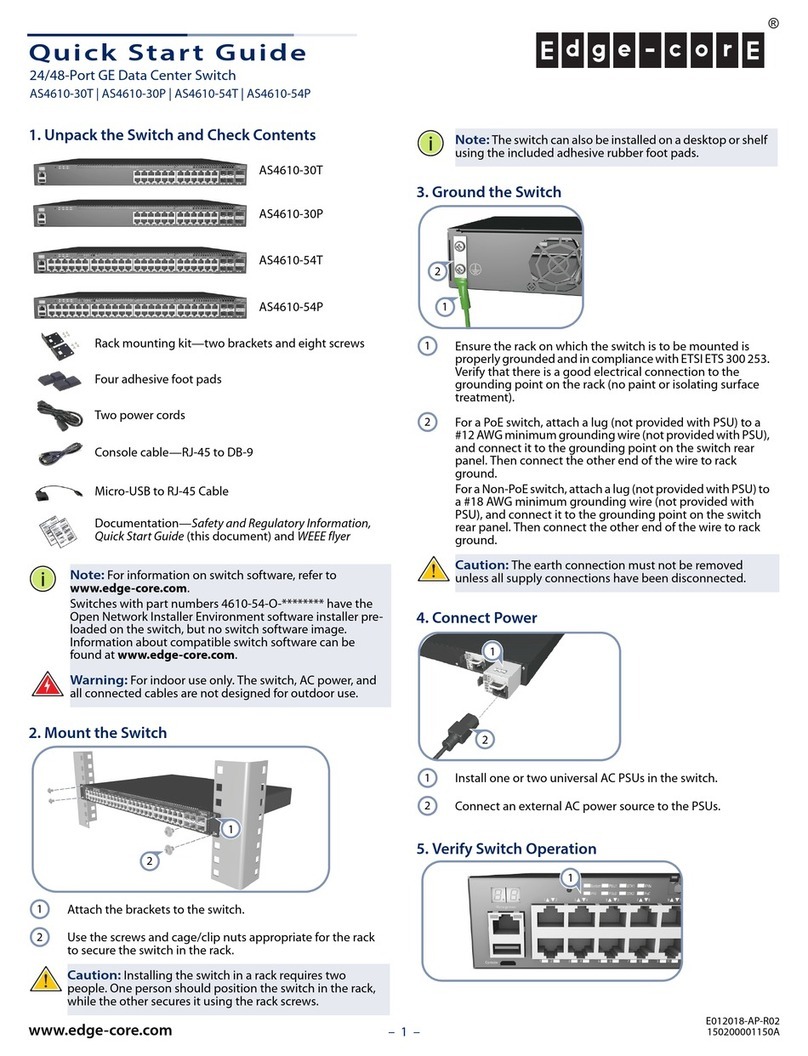
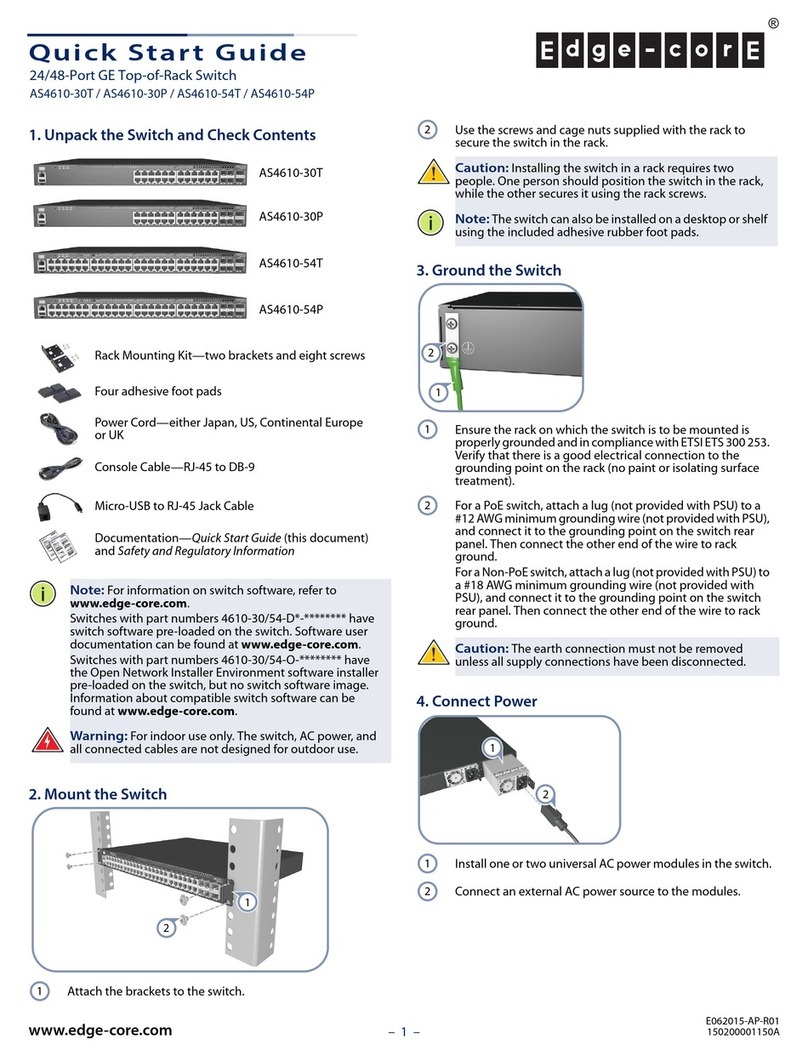
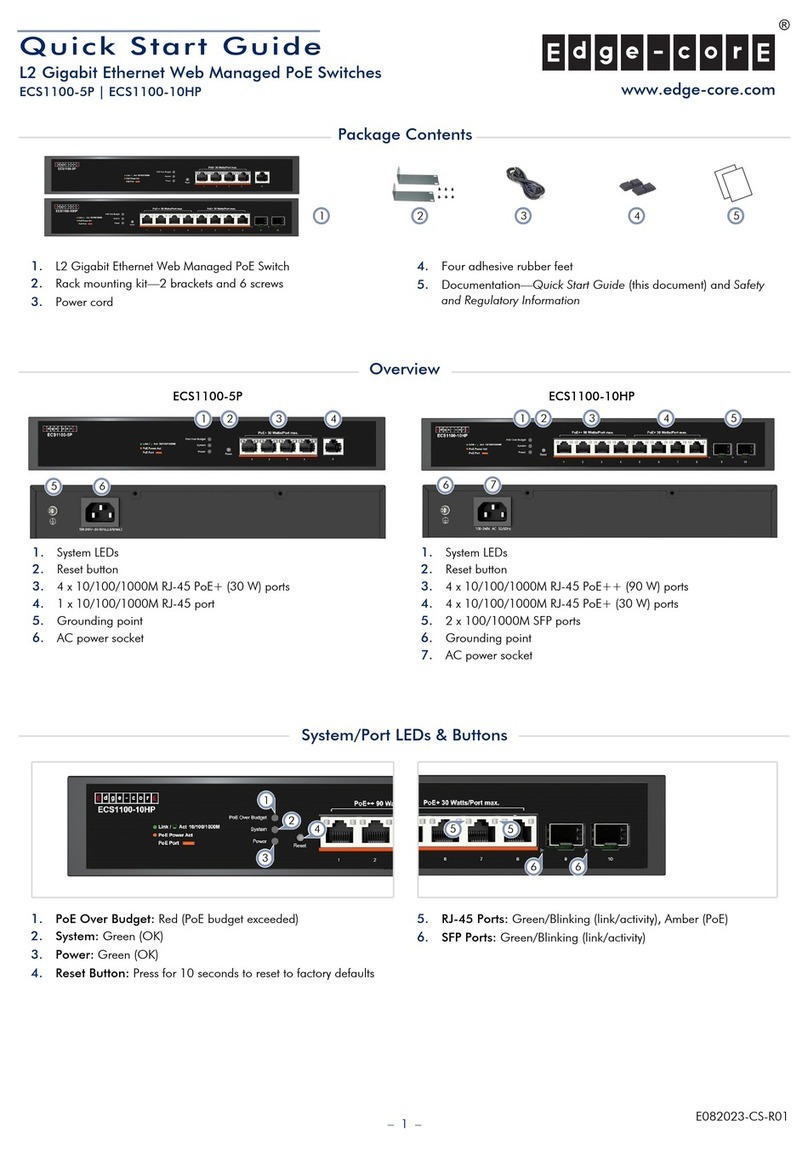
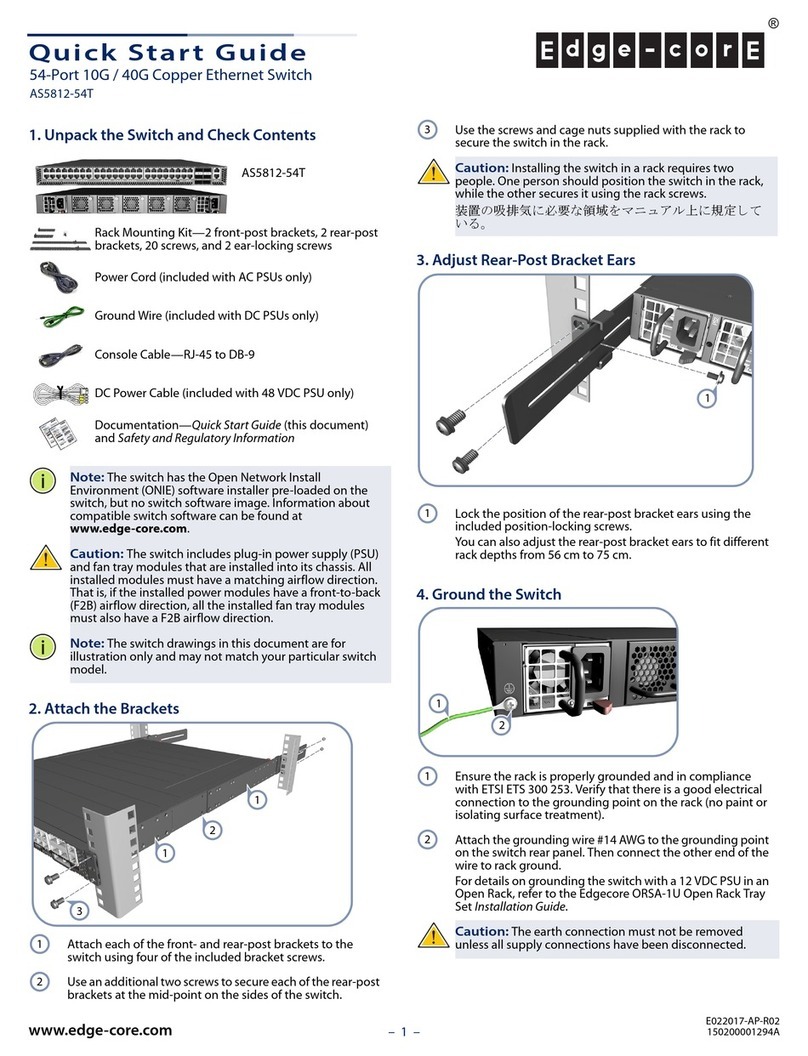
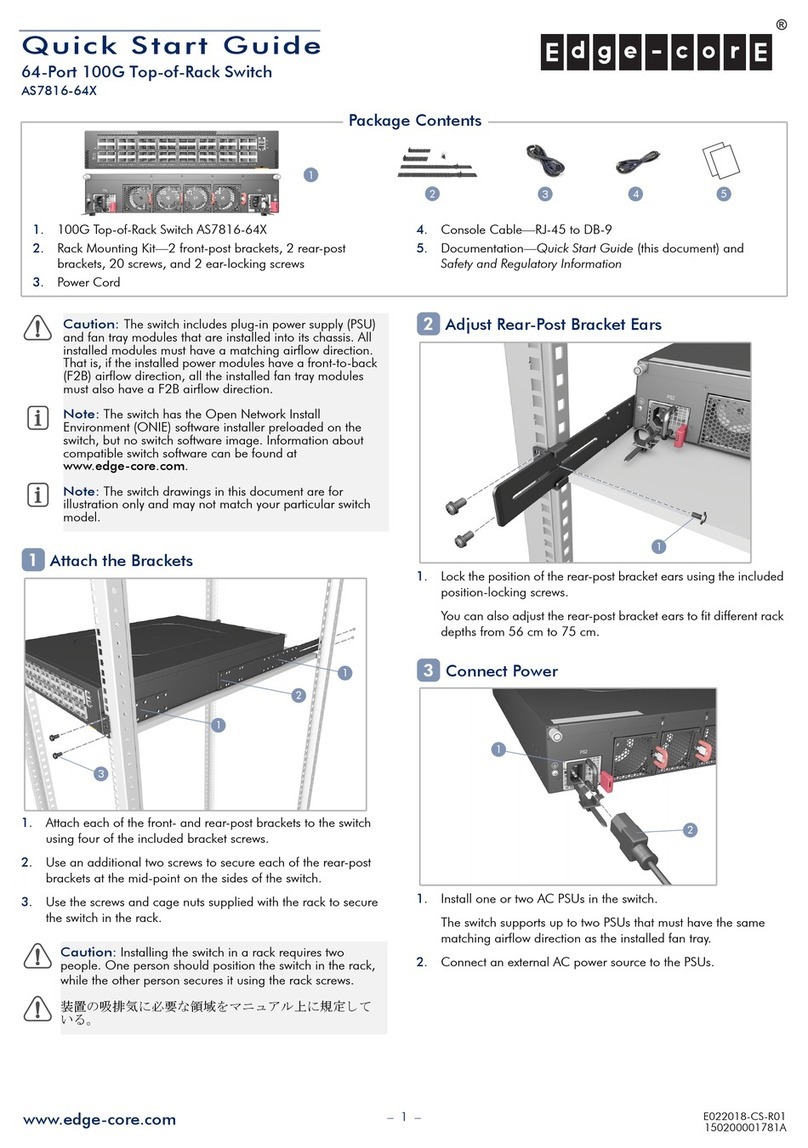
5
5.1.3 Remove VLAN ............................................................................................................................................... 30
5.1.4 Editing VLAN ................................................................................................................................................. 31
5.1.5 View port mode ............................................................................................................................................ 33
5.1.6 Change the port mode is trunk..................................................................................................................... 33
5.1.7 Change the port mode is hybrid ................................................................................................................... 34
5.2 VOICE VLAN......................................................................................................................................................... 35
5.2.1 View voice VLAN information ....................................................................................................................... 35
5.2.2 Configure voice VLAN global......................................................................................................................... 35
5.2.3 Configure voice VLAN port............................................................................................................................ 36
5.2.4 Configure voice VLAN OUI ............................................................................................................................ 36
5.2.5 Voice device address..................................................................................................................................... 37
5.3 SURVEILLANCE VLAN.............................................................................................................................................. 37
5.3.1 View surveillance VLAN information ............................................................................................................ 37
5.3.2 Configure surveillance VLAN......................................................................................................................... 38
5.3.3 MAC settings and surveillance device........................................................................................................... 38
5.3.4 MAC settings and surveillance device........................................................................................................... 39
6FAULT/SAFETY................................................................................................................................................. 40
6.1 ATTACK PREVENTION............................................................................................................................................... 40
6.1.1 ARP snooping ................................................................................................................................................ 40
6.1.2 Port security.................................................................................................................................................. 42
6.1.3 DHCP snooping.............................................................................................................................................. 43
6.1.4 CPU Guard..................................................................................................................................................... 46
6.2 PATH DETECTION.................................................................................................................................................... 47
6.2.1 Path/Tracert detection ................................................................................................................................. 47
6.2.2 Cable detection............................................................................................................................................. 48
6.3 PORT ERROR DISABLE .............................................................................................................................................. 49
6.4 DDOS PROTECTION................................................................................................................................................ 50
6.5 LOOP DETECTION.................................................................................................................................................... 51
6.5.1 Enable loopback detection ........................................................................................................................... 51
6.5.2 Choose the port to configure........................................................................................................................ 52
6.6 STP..................................................................................................................................................................... 52
6.6.1 Enable STP function ...................................................................................................................................... 53
6.6.2 STP port settings ........................................................................................................................................... 53
6.7 ACCESS CONTROL ................................................................................................................................................... 54
6.7.1 ACL access control list................................................................................................................................... 54
6.7.2 Application ACL............................................................................................................................................. 57
6.8 IGMP SNOOPING................................................................................................................................................... 59
6.8.1 IGMP snooping.............................................................................................................................................. 59
6.8.2 MLD............................................................................................................................................................... 61
6.9 IEEE 802.1X........................................................................................................................................................ 63
6.10 AAA.................................................................................................................................................................... 65
6.10.1 RADIUS...................................................................................................................................................... 65
6.10.2 TACACS+ ................................................................................................................................................... 67
7SYSTEM MANAGEMENT................................................................................................................................... 69
7.1 SYSTEM SETTINGS ................................................................................................................................................... 69
7.1.1 Management VLAN....................................................................................................................................... 69
7.1.2 System restart............................................................................................................................................... 71
7.1.3 User Management ........................................................................................................................................ 71