bizhub C658/C558/C458 Contents-1
Contents
1 Security
1.1 Introduction ..................................................................................................................................... 1-2
Administrators.................................................................................................................................... 1-2
Compliance with the ISO15408 Standard ......................................................................................... 1-2
Operating Precautions ....................................................................................................................... 1-2
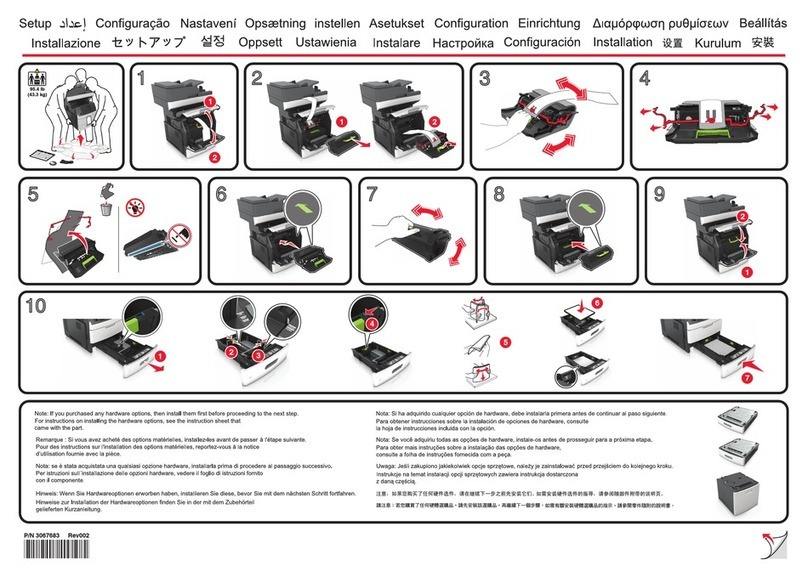
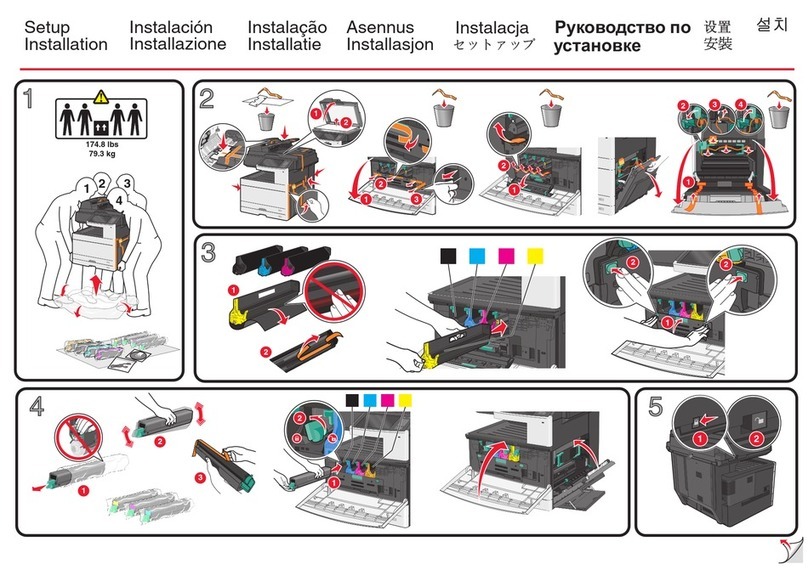
INSTALLATION CHECKLIST.............................................................................................................. 1-4
1.2 Security Functions .......................................................................................................................... 1-7
Check Count Clear Conditions .......................................................................................................... 1-7
1.3 Precautions for Operation Control ................................................................................................ 1-9
Roles of the Owner of the Machine ................................................................................................... 1-9
Roles and Requirements of the Administrator................................................................................... 1-9
Password Usage Requirements ........................................................................................................ 1-9
External authentication server control requirements ....................................................................... 1-10
Security function operation setting operating requirements............................................................ 1-10
Operation and control of the machine ............................................................................................. 1-10
Machine Maintenance Control......................................................................................................... 1-12
Precautions for using the printer driver............................................................................................ 1-12
1.4 Miscellaneous................................................................................................................................ 1-13
Password Rules ............................................................................................................................... 1-13
Precautions for Use of Various Types of Applications..................................................................... 1-14
Encrypting communications ............................................................................................................ 1-14
IPsec setting .................................................................................................................................... 1-14
Print functions.................................................................................................................................. 1-15
IPP printing ...................................................................................................................................... 1-15
Items of Data Cleared by Overwrite All Data Function .................................................................... 1-16
Fax functions.................................................................................................................................... 1-16
USB keyboard.................................................................................................................................. 1-16
Different types of boxes................................................................................................................... 1-17
Hardware and software used in the machine .................................................................................. 1-17
Firmware integrity verification function............................................................................................ 1-17
CS Remote Care function................................................................................................................ 1-18
Terminating a Session and Logging out .......................................................................................... 1-18
Authentication error during external server authentication.............................................................. 1-18
2 Administrator Operations
2.1 Accessing the Administrator Mode............................................................................................... 2-2
2.1.1 Accessing the Administrator Mode.................................................................................................... 2-2
2.1.2 Accessing the User Mode.................................................................................................................. 2-8
2.2 Enhancing the Security Function................................................................................................. 2-12
2.2.1 Items cleared by HDD Format ......................................................................................................... 2-14
2.2.2 Setting the Password Rules............................................................................................................. 2-15
2.2.3 Setting the Enhanced Security Mode .............................................................................................. 2-17
2.3 Protecting Machine from Illegal Firmware Update.................................................................... 2-20
Setting the FW Update (USB) Password ......................................................................................... 2-20
2.4 Preventing Unauthorized Access ................................................................................................ 2-23
Setting Prohibited Functions When Authentication Error ................................................................ 2-23
2.5 Canceling the Operation Prohibited State.................................................................................. 2-25
Performing Release Setting ............................................................................................................. 2-25
2.6 Setting the Authentication Method ............................................................................................. 2-27
2.6.1 Setting the Authentication Method .................................................................................................. 2-27
2.6.2 Setting the External Server .............................................................................................................. 2-30
2.7 ID & Print Setting Function........................................................................................................... 2-33
Setting ID & Print.............................................................................................................................. 2-33