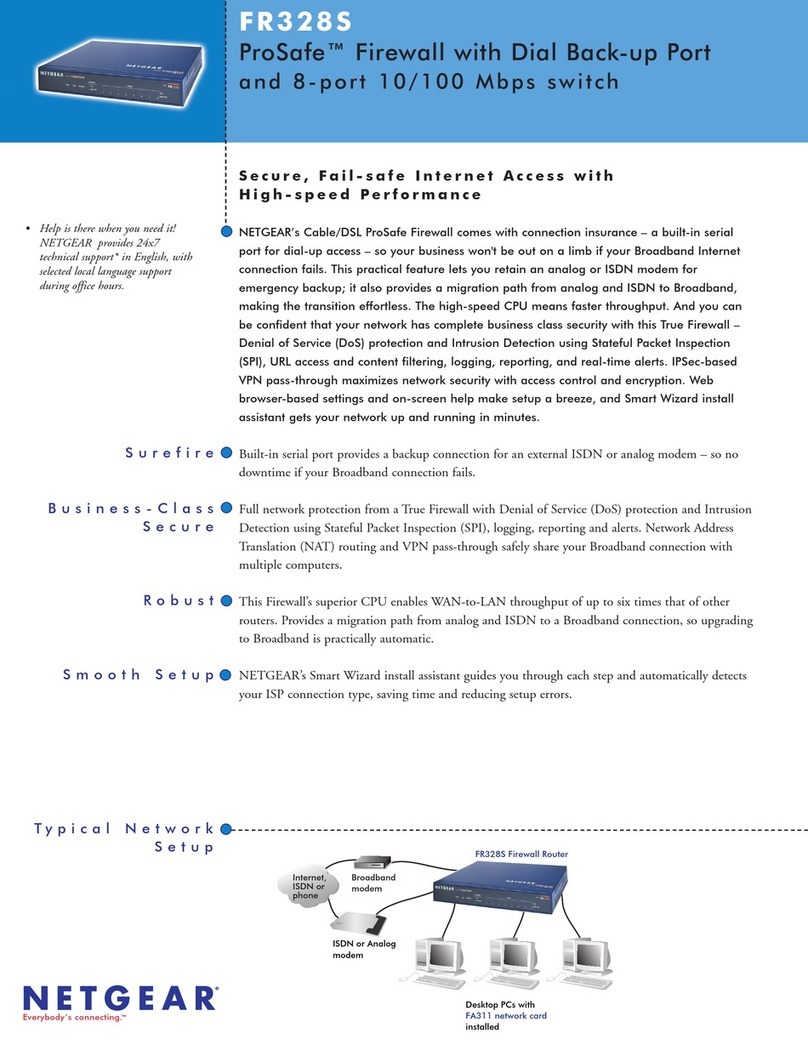
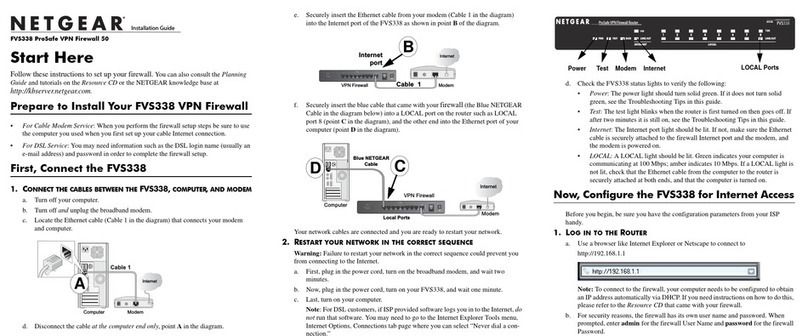
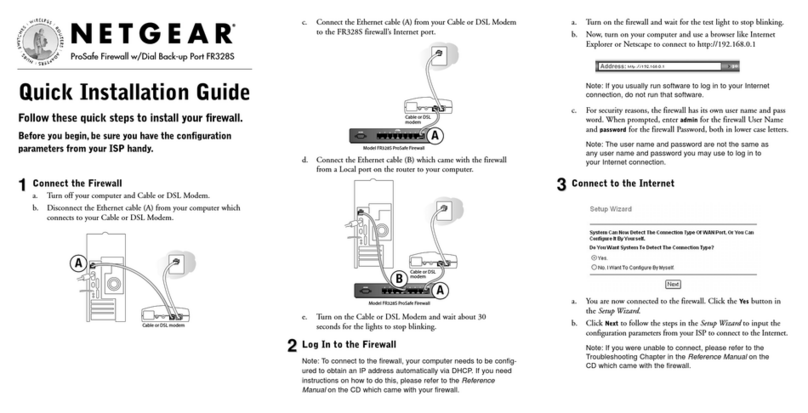
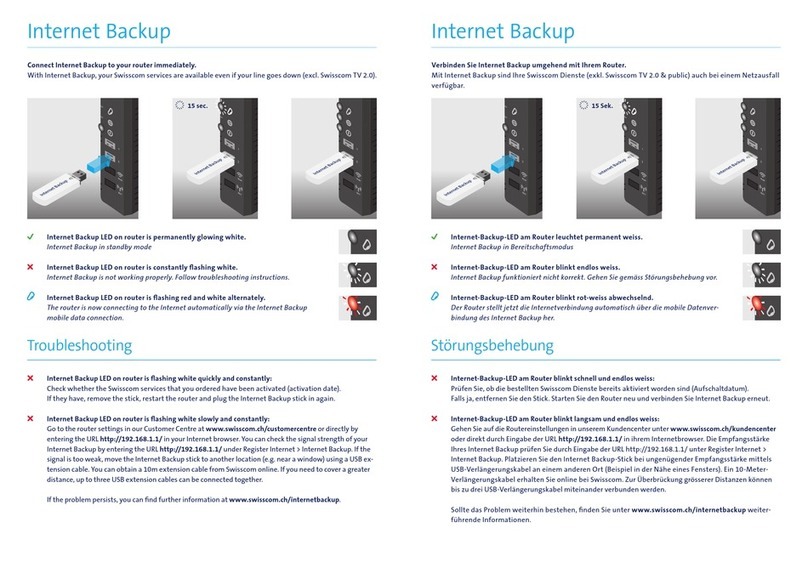
Contents vii
BETA
Outbound Rule Example: Blocking Instant Messenger .....................................5-7
Order of Precedence for Rules ................................................................................5-8
Default DMZ Server .................................................................................................5-8
Respond to Ping on Internet WAN Port ...................................................................5-9
Services ........................................................................................................................5-10
Using a Schedule to Block or Allow Specific Traffic ......................................................5-12
Time Zone ..............................................................................................................5-13
Getting E-Mail Notifications of Event Logs and Alerts ..................................................5-14
Viewing Logs of Web Access or Attempted Web Access .............................................5-16
Syslog ....................................................................................................................5-17
Chapter 6
Basic Virtual Private Networking
Overview of VPN Configuration ......................................................................................6-2
Client-to-Gateway VPN Tunnels ..............................................................................6-2
Gateway-to-Gateway VPN Tunnels .........................................................................6-2
Planning a VPN ..............................................................................................................6-3
VPN Tunnel Configuration ..............................................................................................6-5
How to Set Up a Client-to-Gateway VPN Configuration .................................................6-5
Step 1: Configuring the Client-to-Gateway VPN Tunnel on the FVG318 .................6-6
Step 2: Configuring the NETGEAR ProSafe VPN Client on the Remote PC ...........6-9
Monitoring the Progress and Status of the VPN Client Connection .......................6-16
Transferring a Security Policy to Another Client ....................................................6-18
Exporting a Security Policy ..............................................................................6-18
Importing a Security Policy ..............................................................................6-19
How to Set Up a Gateway-to-Gateway VPN Configuration ..........................................6-20
Procedure to Configure a Gateway-to-Gateway VPN Tunnel ................................6-21
VPN Tunnel Control ......................................................................................................6-26
Activating a VPN Tunnel ........................................................................................6-26
Start Using a VPN Tunnel to Activate It ...........................................................6-26
Using the VPN Status Page to Activate a VPN Tunnel ....................................6-26
Activate the VPN Tunnel by Pinging the Remote Endpoint .............................6-27
Verifying the Status of a VPN Tunnel .....................................................................6-29
Deactivating a VPN Tunnel ....................................................................................6-30
Using the Policy Table on the VPN Policies Page to Deactivate a VPN Tunnel 6-30
Using the VPN Status Page to Deactivate a VPN Tunnel ...............................6-31