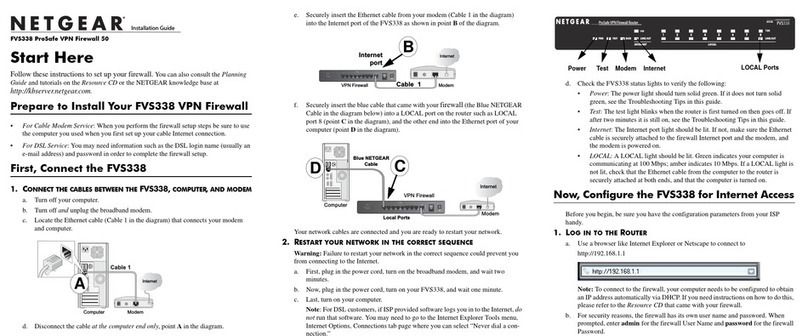
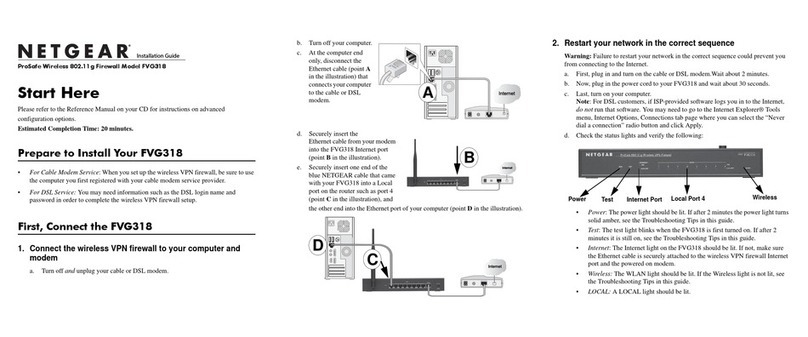
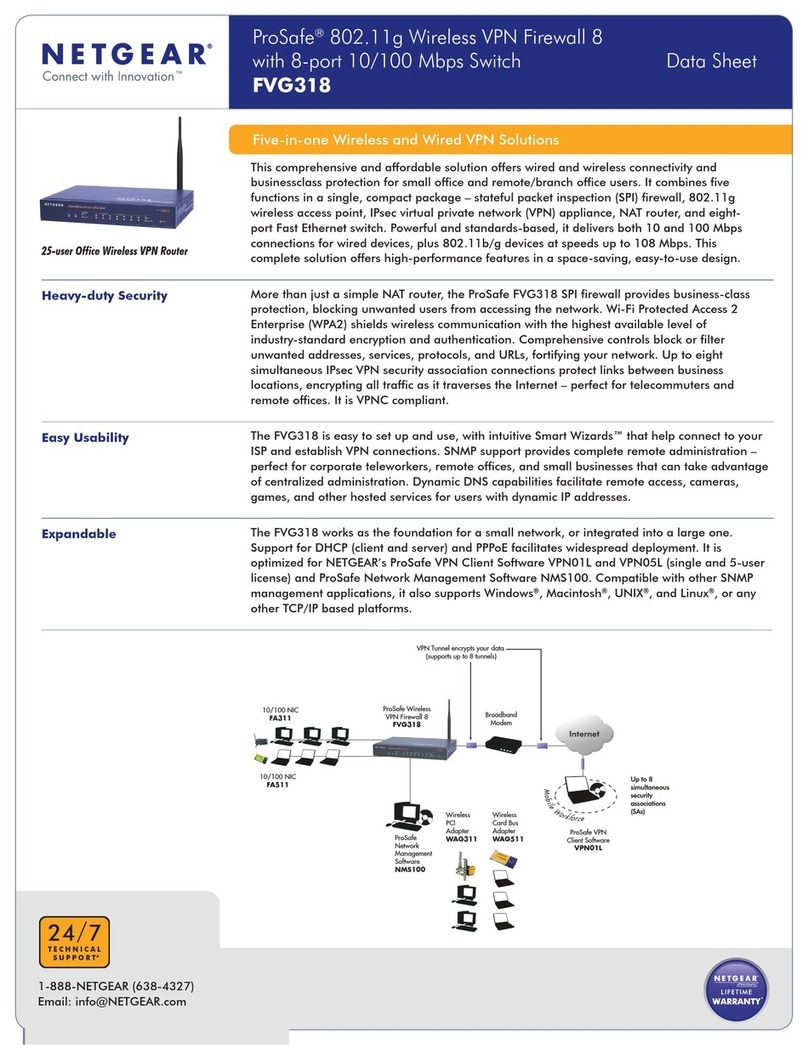
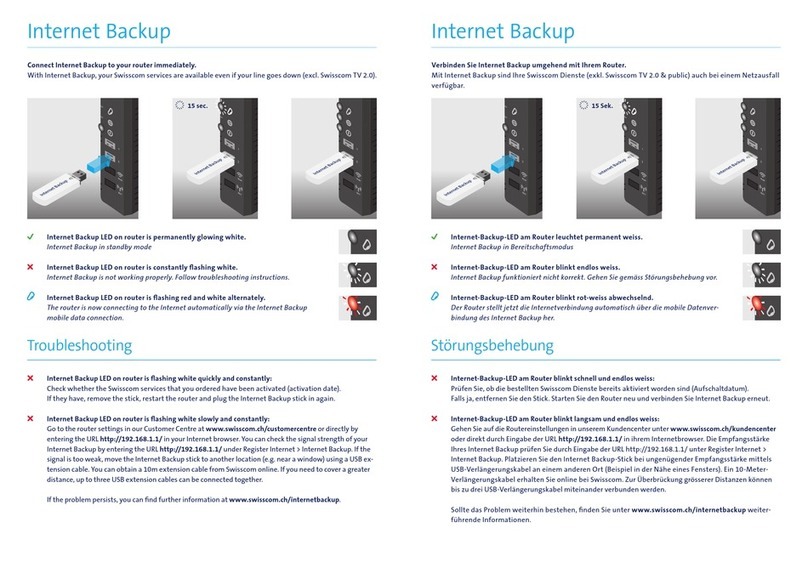
6| Contents
ProSecure Web/Email Security Threat Management (STM) Appliance
Configuring Web Content Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . .109
Configuring Web URL Filtering. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .116
HTTPS Scan Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .119
Specifying Trusted Hosts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .124
Configuring FTP Scans . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .125
Configuring Application Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .127
Setting Scanning Exclusions and Web Access Exceptions . . . . . . . . . . .130
Setting Scanning Exclusions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .130
Setting Access Exception Rules for Web Access. . . . . . . . . . . . . . . . .132
Creating Custom Groups for Web Access Exceptions. . . . . . . . . . . . .139
Creating Custom Categories for Web Access Exceptions . . . . . . . . . .142
Chapter 5 Managing Users, Groups, and Authentication
About Users, Groups, and Domains. . . . . . . . . . . . . . . . . . . . . . . . . . . . .147
Configuring Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .148
Creating and Deleting Groups by Name. . . . . . . . . . . . . . . . . . . . . . . .149
Editing Groups by Name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .150
Creating and Deleting Groups by IP Address and Subnet. . . . . . . . . .151
Configuring User Accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .152
Creating and Deleting User Accounts . . . . . . . . . . . . . . . . . . . . . . . . .153
Editing User Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .154
Configuring Authentication. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .154
Understanding the STM’s Authentication Options . . . . . . . . . . . . . . . .155
Understanding Active Directories and LDAP Configurations . . . . . . . .157
Creating and Deleting LDAP and Active Directory Domains . . . . . . . .161
Editing LDAP and Active Directory Domains . . . . . . . . . . . . . . . . . . . .164
Understanding the ProSecure DC Agent . . . . . . . . . . . . . . . . . . . . . . .164
Requirements for the ProSecure DC Agent Software and
DC Agent Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .165
Downloading ProSecure DC Agent Software, and Creating
and Deleting DC Agents. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .165
Creating and Deleting RADIUS Domains. . . . . . . . . . . . . . . . . . . . . . .167
Editing RADIUS Domains and Configuring VLANs . . . . . . . . . . . . . . .169
Global User Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .170
Viewing and Logging Out Active Users . . . . . . . . . . . . . . . . . . . . . . . . . .172
Chapter 6 Monitoring System Access and Performance
Configuring Logging, Alerts, and Event Notifications. . . . . . . . . . . . . . . .175
Configuring the Email Notification Server. . . . . . . . . . . . . . . . . . . . . . .176
Configuring and Activating System, Email, and Syslog Logs. . . . . . . .177
Configuring Alerts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .182
Monitoring Real-Time Traffic, Security, Statistics, and Web Usage. . . . .184
Understanding the Information on the Dashboard Screen. . . . . . . . . .184
Monitoring Web Usage. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .190
Viewing System Status. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .192
Querying Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .194
Example: Using Logs to Identify Infected Clients. . . . . . . . . . . . . . . . .199