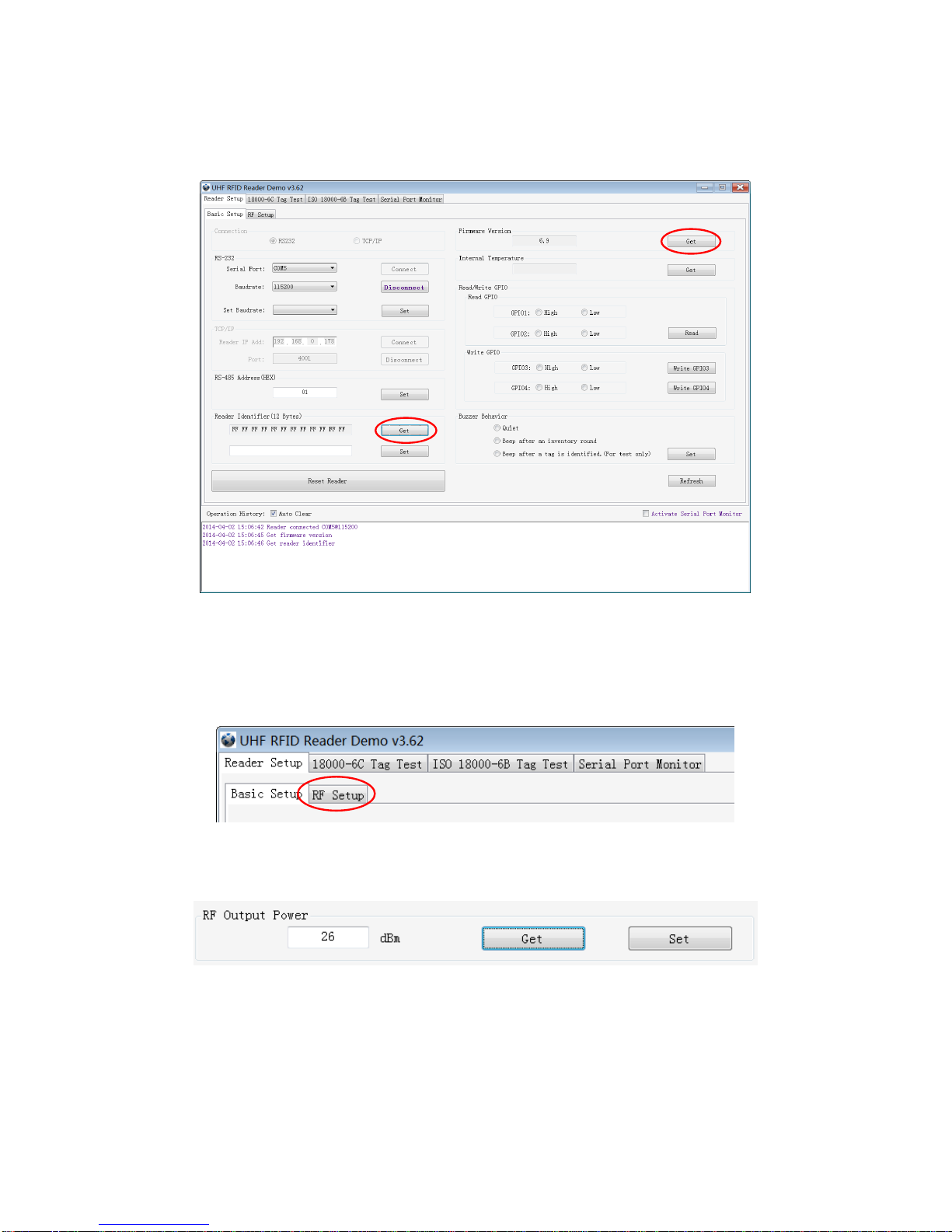
7
the carrier frequency.
Frequency range the reader supports: 865MHz-868MHz(ETSI), 902MHz -928MHz(FCC).
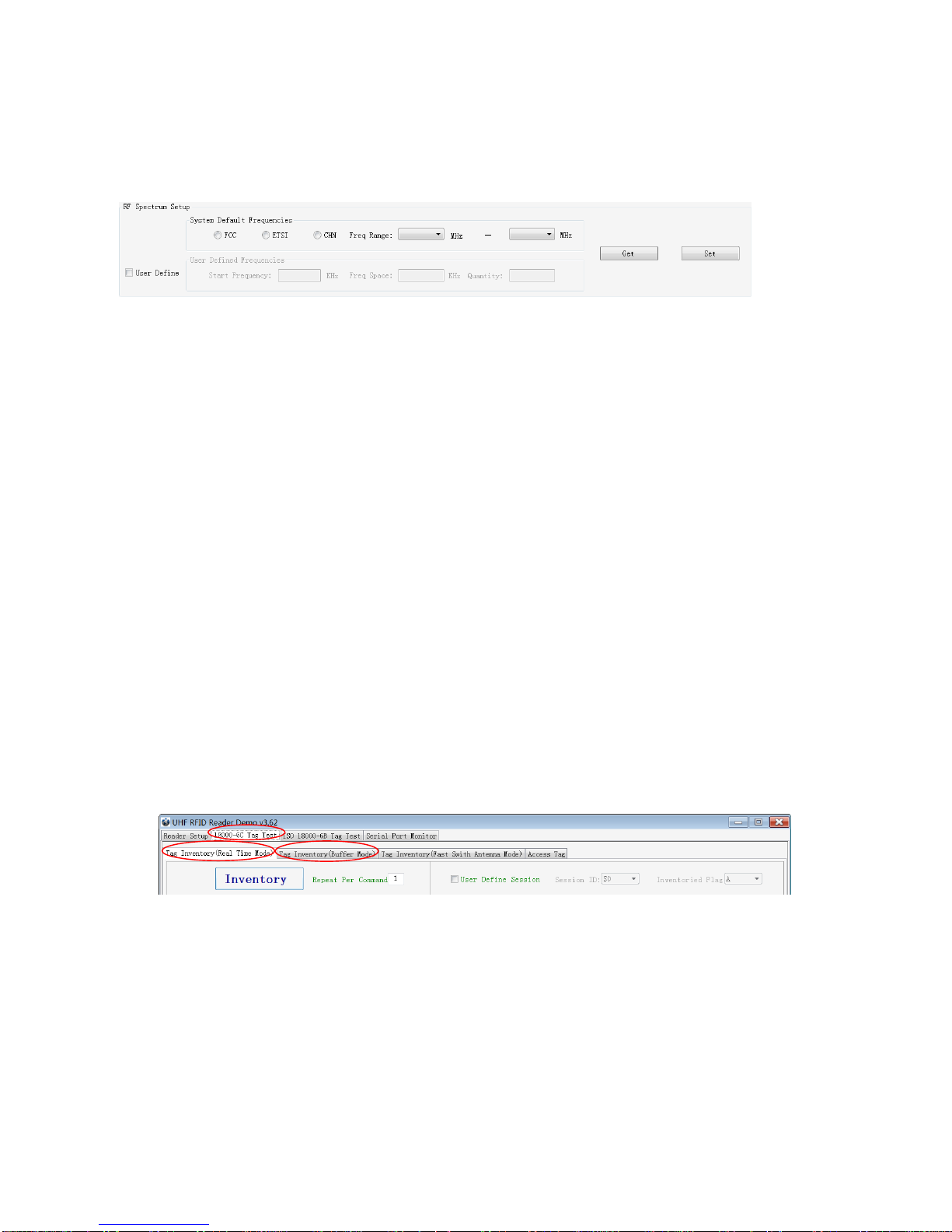
You can set the reader in RF Spectrum Setup->User Define, as illustrate below:
Users can set RF spectrum via these three parameters: Start Frequency, Frequency Interval, The number
of Frequency points.
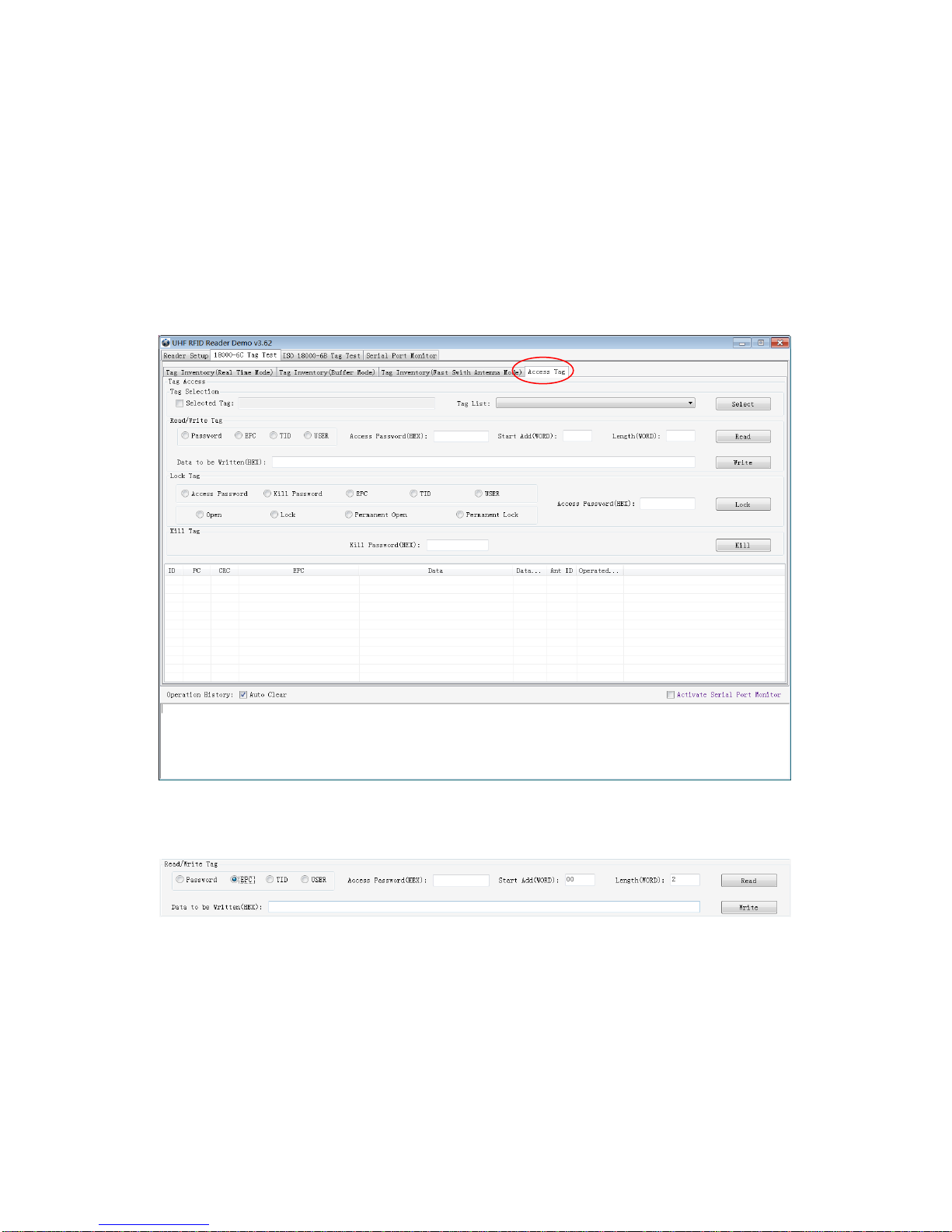
2.3 ISO-18000-6C tag inventory
Connect the Reader correctly. Tag operation could be started when RF Setup is completed.
Tag inventory means reader identifying multiple tags’EPC number at the same time. This is the core
function of UHF RFID Reader and one of the standards to judge a reader’s performance.
2.3.1 Real Time Mode & Buffer Mode
The most commonly used mode for tag inventory isReal-time Mode. Data will be uploaded meanwhile
you can get the tags’EPC number instantly. RSSI and Parameter of Frequency are changed and
recorded in real time. Due to its dual CPU architecture, performance of multi-tag identification under
Real-time mode is the best.
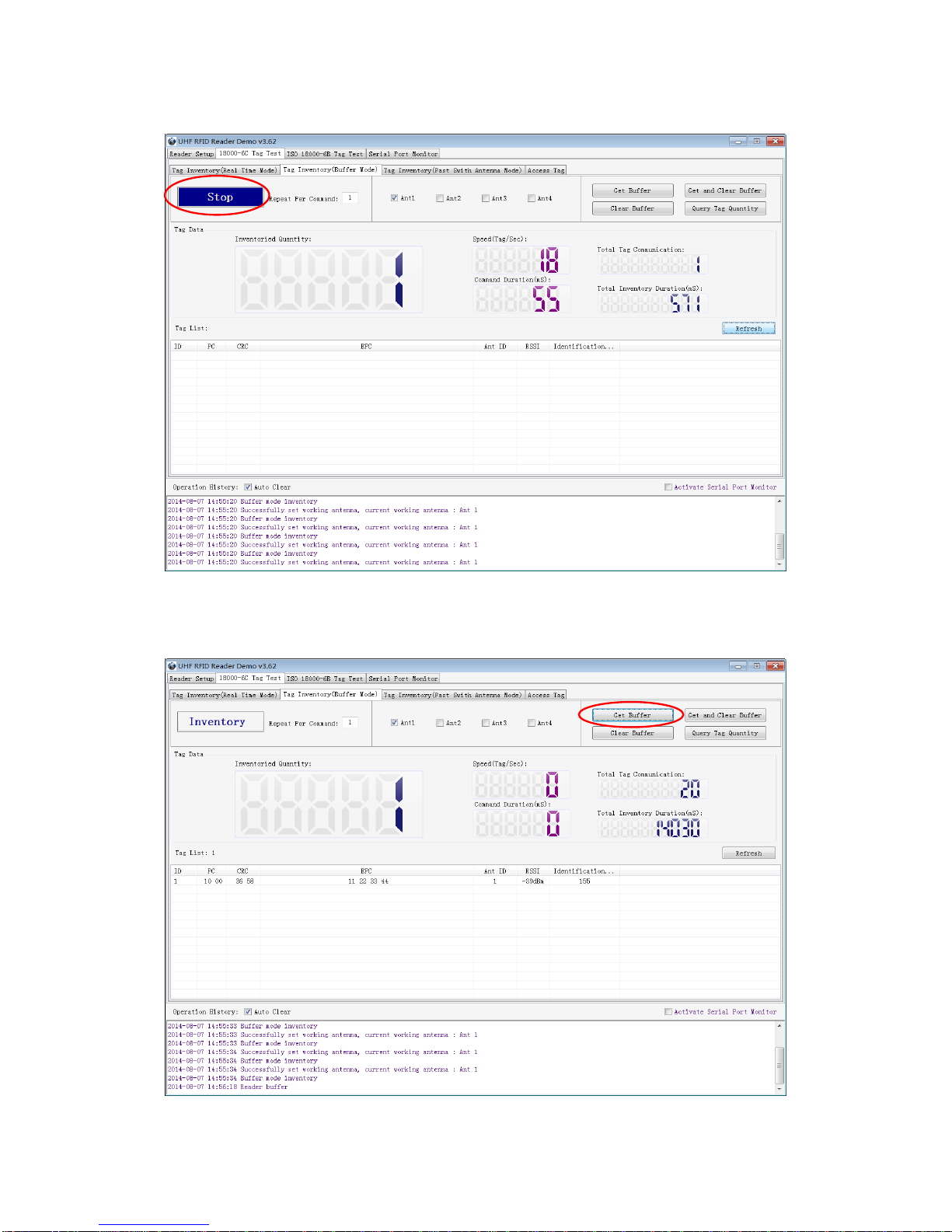
The other is Buffer Mode, the data will be cached and uploaded together when you need them. Under
this mode, the data are without repeat data and can keep in small volume, because the data will be
filtered before being uploaded. But it will take some time to filter duplicate data when reader identifies a
large number of tags. Therefore, its identification efficiency will be slightly lower than real-time mode. Note:
Tags can’t be operated when you extract data in the cache.
Users can choose the appropriate method based on actual situation as illustrated below:
Method NO.1: Real-time Mode
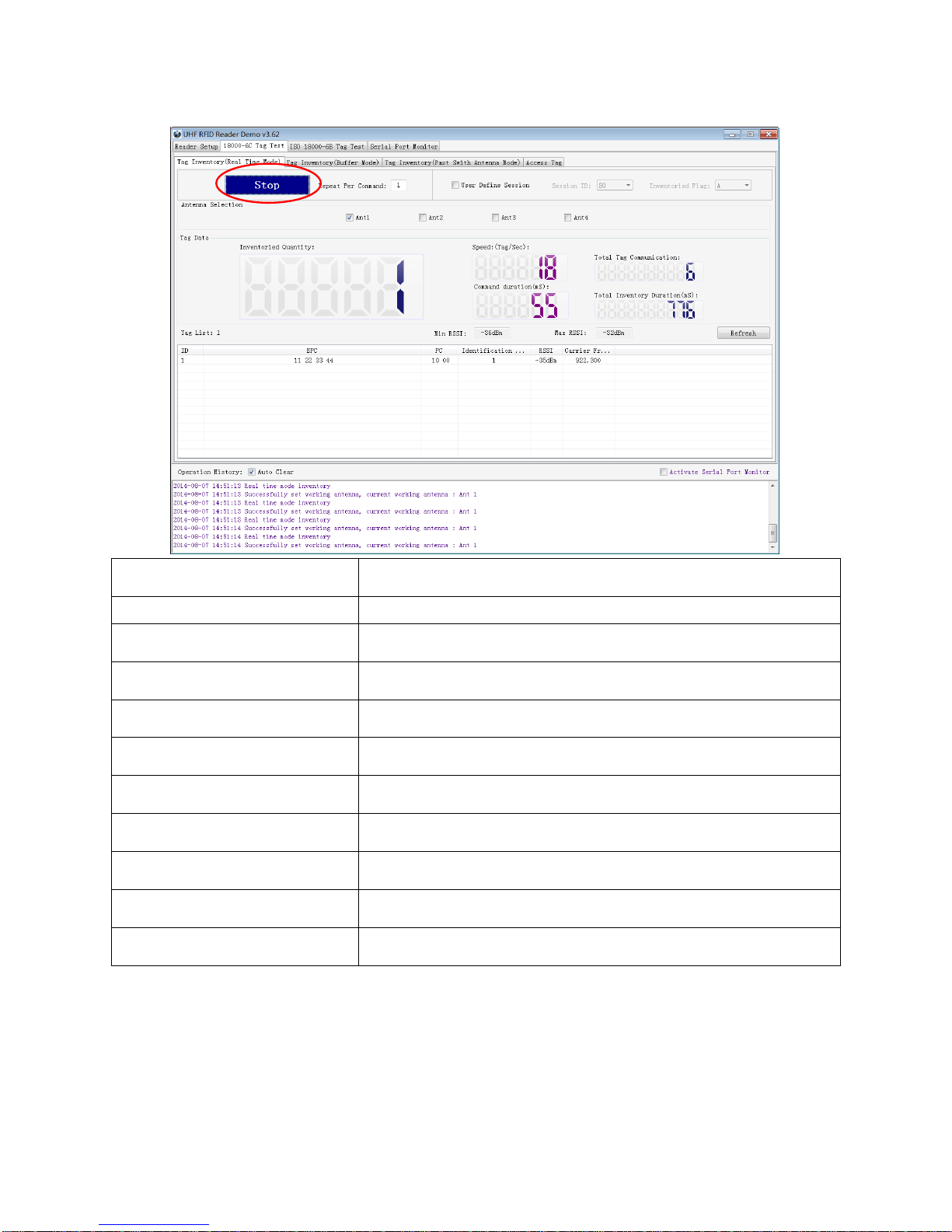
1. Click Tag Inventory (Real Time Mode). Select the connected antenna(s) port. Set the number of
Repeat Per Command, which is the times of repeat inventory command. For example, inventory
command will execute anti-collision algorithm one time when you set the value to 1. It will execute
anti-collision algorithm two times when you set the value to 2...
2. Click Inventory, you will find that the EPC number is uploaded immediately and it is real-time updating.
The reader will keep inventory until you click stop as shown below: