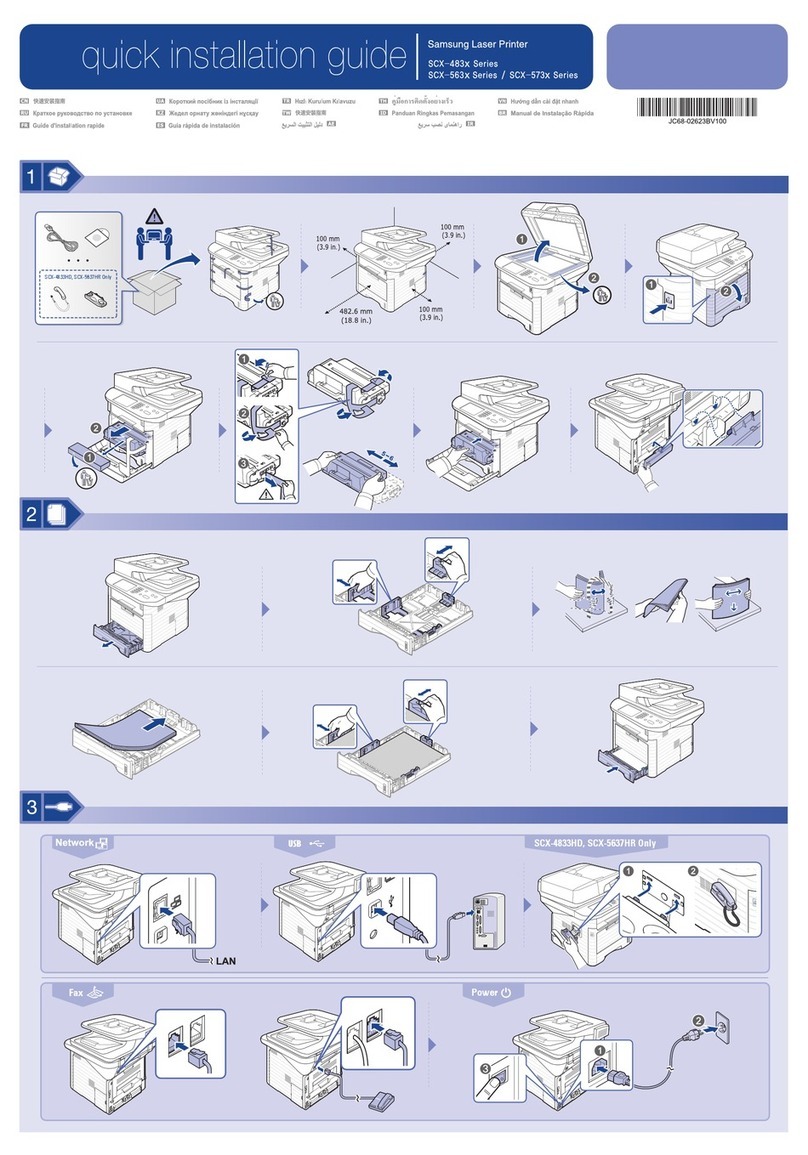
Samsung Multifunction MultiXpress X4220, X4250, X4300, X401, K4250, K4300, K4350, K401 Series
6
Copyright2014 SAMSUNG ELECTRONICS Co., Ltd., All rights reserved
LIST OF TABLES
Table 1: General Specification for TOE......................................................................................................................10
Table 2: Non-TOE Hardware ......................................................................................................................................11
Table 3: Non-TOE Software........................................................................................................................................11
Table 4: Notational Prefix Conventions ......................................................................................................................19
Table 5: Acronyms ......................................................................................................................................................23
Table 6: Security Problem Definition Related Conformance Claim Rationale - Threats............................................26
Table 7: Security Problems Definition Related Conformance Claim Rationale - Organizational Security Policies...27
Table 8: Security Problems Definition Related Conformance Claim Rationale - Assumptions..................................27
Table 9: Security Objectives Related Conformance Claim Rationale –Security Objectives for the TOE..................27
Table 10: Security Objectives related Conformance Claim Rationale –Security Objectives for the Operational
Environment.......................................................................................................................................................28
Table 11: Security Functional Requirements related Conformance Claim Rationale .................................................28
Table 12: Security Assurance Requirements related Conformance Claim Rationale..................................................30
Table 13: TOE type related Conformance Claim Rationale........................................................................................31
Table 14: Threats to User Data for the TOE................................................................................................................32
Table 15: Threats to TSF Data for the TOE ................................................................................................................32
Table 16: Organizational Security Policies..................................................................................................................33
Table 17: Assumptions for the TOE............................................................................................................................33
Table 18: Security Objectives for the TOE .................................................................................................................35
Table 19: Security Objectives for the TOE (Additional).............................................................................................36
Table 20: Security Objectives for Operational Environment.......................................................................................36
Table 21: Completeness of Security Objectives..........................................................................................................38
Table 22: Sufficiency of Security Objectives..............................................................................................................39
Table 23: Users............................................................................................................................................................43
Table 24: User Data.....................................................................................................................................................43
Table 25: TSF Data......................................................................................................................................................44
Table 26: TSF Data......................................................................................................................................................44
Table 27: Functions .....................................................................................................................................................45
Table 28: Attributes.....................................................................................................................................................46
Table 29: External Entities ..........................................................................................................................................46
Table 30: Security Functional Requirements...............................................................................................................47
Table 31: Audit data ....................................................................................................................................................49
Table 32: Common Access Control SFP .....................................................................................................................53
Table 33: TOE Function Access Control SFP .............................................................................................................54
Table 34: Service (PRT, SCN, CPY, FAX) Access Control SFP................................................................................55
Table 35: Management of Security Attributes.............................................................................................................60
Table 36: Management of TSF data ............................................................................................................................62
Table 37: Management Functions ...............................................................................................................................63
Table 38: Security Assurance Requirements (EAL2 augmented by ALC_FLR.2) .....................................................66
Table 39: Completeness of Security Objectives..........................................................................................................80
Table 40: Security Requirements Rationale ................................................................................................................81
Table 41: Dependencies on the TOE Security Functional Components......................................................................84
Table 42 : Management of Security Attributes............................................................................................................89
Table 43: Management of TSF data ............................................................................................................................90
Table 44: Management Functions ...............................................................................................................................90
Table 45: Security Audit Event ...................................................................................................................................91