Regulatory Information ................................................................................................................................................................................................................3
1
Introduction ........................................................................................................................................................................................................................1
Welcome ......................................................................................................................................................................................................................................1
2
Web Access and Login.........................................................................................................................................................................................................2
2.1 LAN ......................................................................................................................................................................................................................................................................2
3
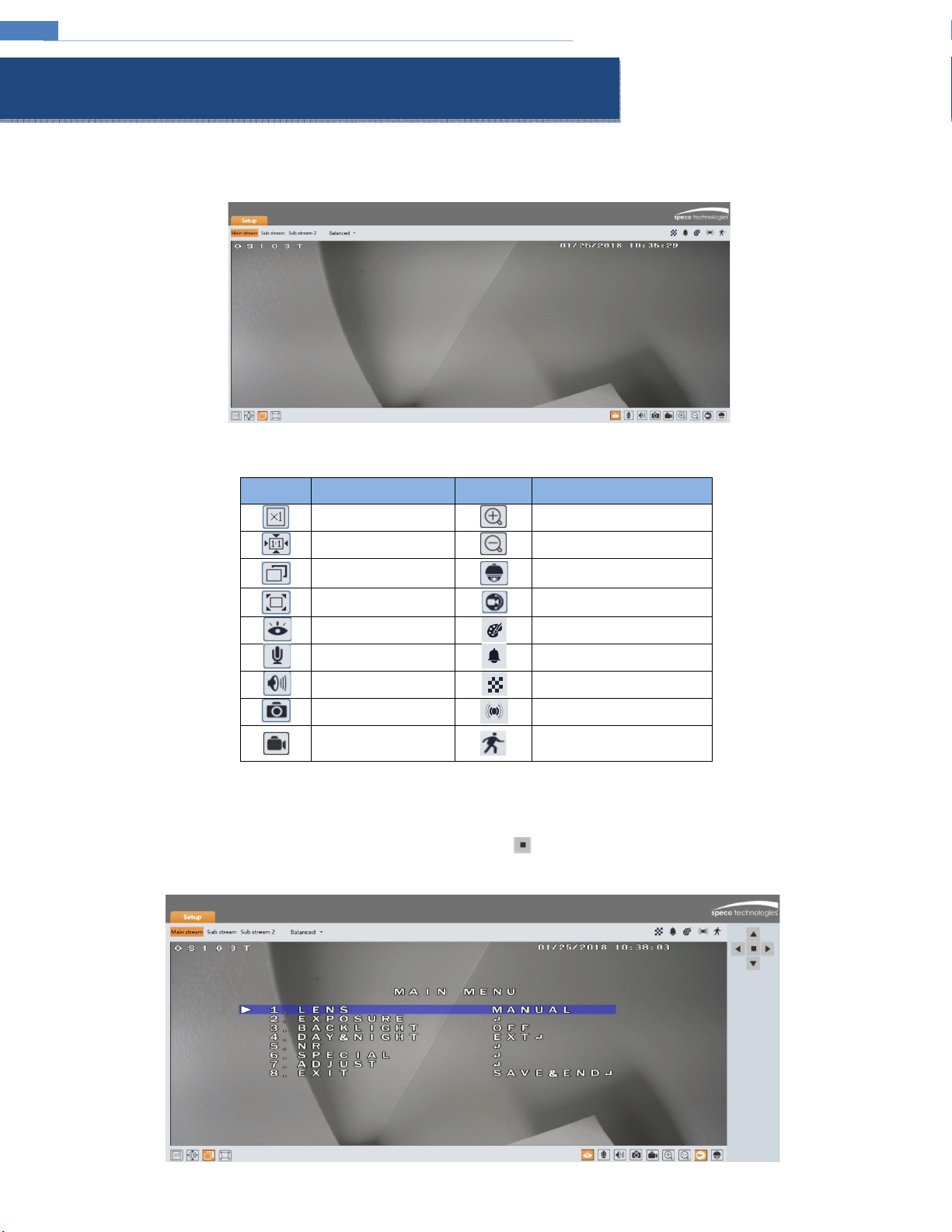
Live View .............................................................................................................................................................................................................................3
4
Device Configuration...........................................................................................................................................................................................................5
4.1 System Configuration........................................................................................................................................................................................................................................... 5
4.1.1 System Information ............................................................................................................................................................................................................................5
4.1.2 Date and Time.....................................................................................................................................................................................................................................5
4.1.3 Local Recording...................................................................................................................................................................................................................................5
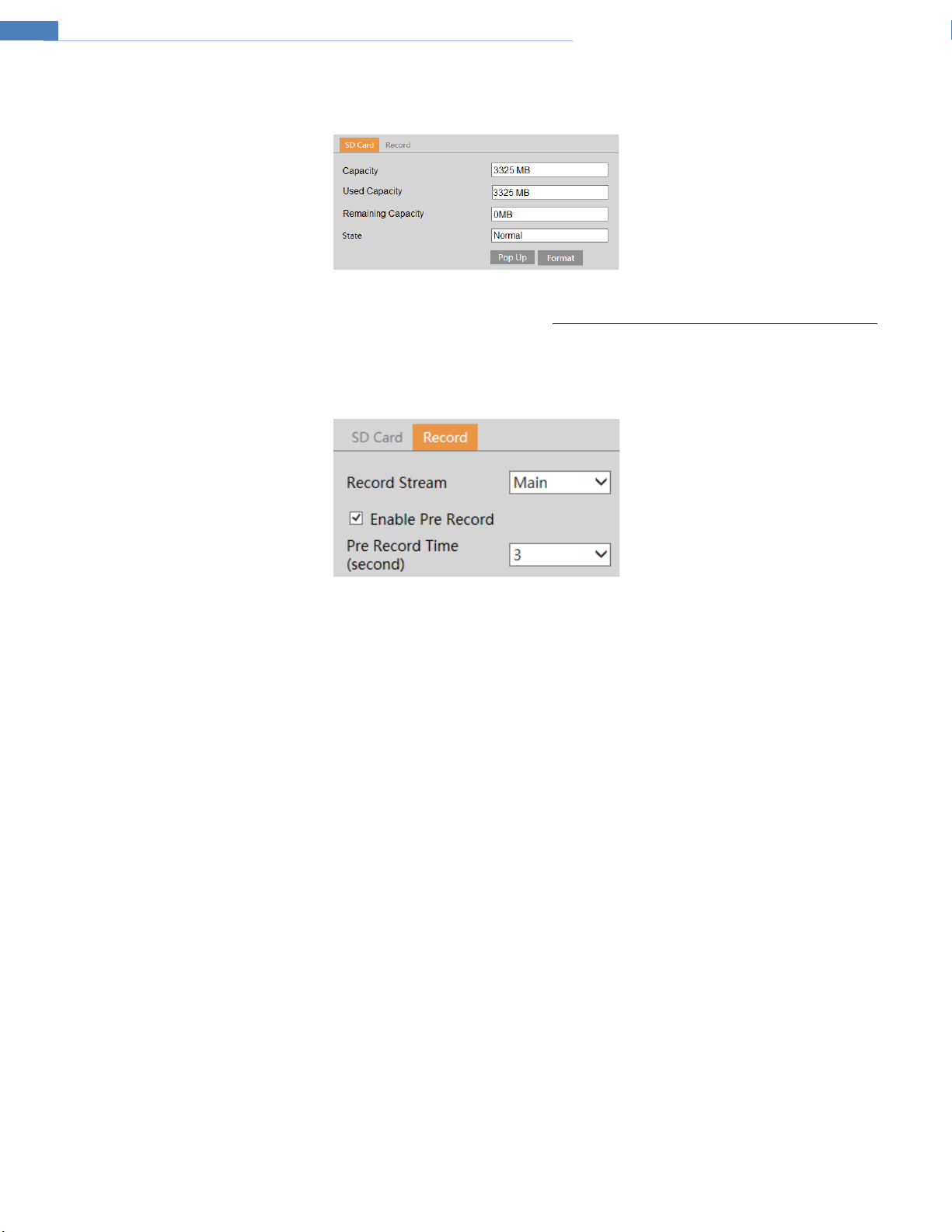
4.1.4 Storage ...............................................................................................................................................................................................................................................6
4.2 Video Configuration.............................................................................................................................................................................................................................................7
4.2.1 Image Configuration ...........................................................................................................................................................................................................................7
4.2.2 Video / Audio Setup............................................................................................................................................................................................................................8
4.2.3 OSD Configuration ..............................................................................................................................................................................................................................8
4.2.4 Privacy Mask.......................................................................................................................................................................................................................................9
4.2.5 Region of Interest Configuration......................................................................................................................................................................................................... 9
4.3 PTZ Configuration .............................................................................................................................................................................................................................................. 10
4.4 Event Setup........................................................................................................................................................................................................................................................ 11
4.4.1 Motion Detection ............................................................................................................................................................................................................................. 11
4.4.2 Alarm In (Sensor Input)..................................................................................................................................................................................................................... 12
4.4.3 Alarm Out ......................................................................................................................................................................................................................................... 13
4.4.4 Alarm Server..................................................................................................................................................................................................................................... 13
4.5 Analytics Configuration...................................................................................................................................................................................................................................... 14
4.5.1 Object Removal................................................................................................................................................................................................................................. 14
4.5.2 Abnormality...................................................................................................................................................................................................................................... 15
4.5.3 Line Crossing..................................................................................................................................................................................................................................... 16
4.5.4 Intrusion ........................................................................................................................................................................................................................................... 16
4.6 Network Setup................................................................................................................................................................................................................................................... 18
4.6.1 TCP/IP............................................................................................................................................................................................................................................... 18
4.6.2 Port...................................................................................................................................................................................................................................................18
4.6.3 DDNS ................................................................................................................................................................................................................................................ 19
4.6.4 SNMP................................................................................................................................................................................................................................................ 19
4.6.5 RTSP.................................................................................................................................................................................................................................................. 20
4.6.6 UPnP................................................................................................................................................................................................................................................. 20
4.6.7 Email.................................................................................................................................................................................................................................................21
4.6.8 FTP....................................................................................................................................................................................................................................................21
4.7 Security Configuration ....................................................................................................................................................................................................................................... 23
4.7.1 User Admin....................................................................................................................................................................................................................................... 23
4.7.2 Online User....................................................................................................................................................................................................................................... 24
4.7.3 Block and Allow Lists......................................................................................................................................................................................................................... 24
4.8 Maintenance Configuration ...............................................................................................................................................................................................................................24
4.8.1 Backup and Restore.......................................................................................................................................................................................................................... 24
4.8.2 Reboot.............................................................................................................................................................................................................................................. 25
4.8.3 Upgrade............................................................................................................................................................................................................................................ 25
4.8.4 Log....................................................................................................................................................................................................................................................25
5
Search................................................................................................................................................................................................................................26
5.1 Image Search ..................................................................................................................................................................................................................................................... 26
5.2 Video Search...................................................................................................................................................................................................................................................... 27
5.2.1 Local Video Search............................................................................................................................................................................................................................ 27
5.2.2 SD Card Video Search........................................................................................................................................................................................................................ 27
Appendix ....................................................................................................................................................................................................................................28
Appendix 1 Troubleshooting ......................................................................................................................................................................................................28