Cisco QuickVPN - PC Instruction Manual
Other Cisco Network Router manuals

Cisco
Cisco WS-C3550-12G User manual

Cisco
Cisco ASR 9000 Series User manual

Cisco
Cisco XR 12000 User manual

Cisco
Cisco Linksys WRT600N User manual

Cisco
Cisco 4948 Series User manual

Cisco
Cisco ASR 1004 Installation guide
Cisco
Cisco ASR 1002-F Installation guide
Cisco
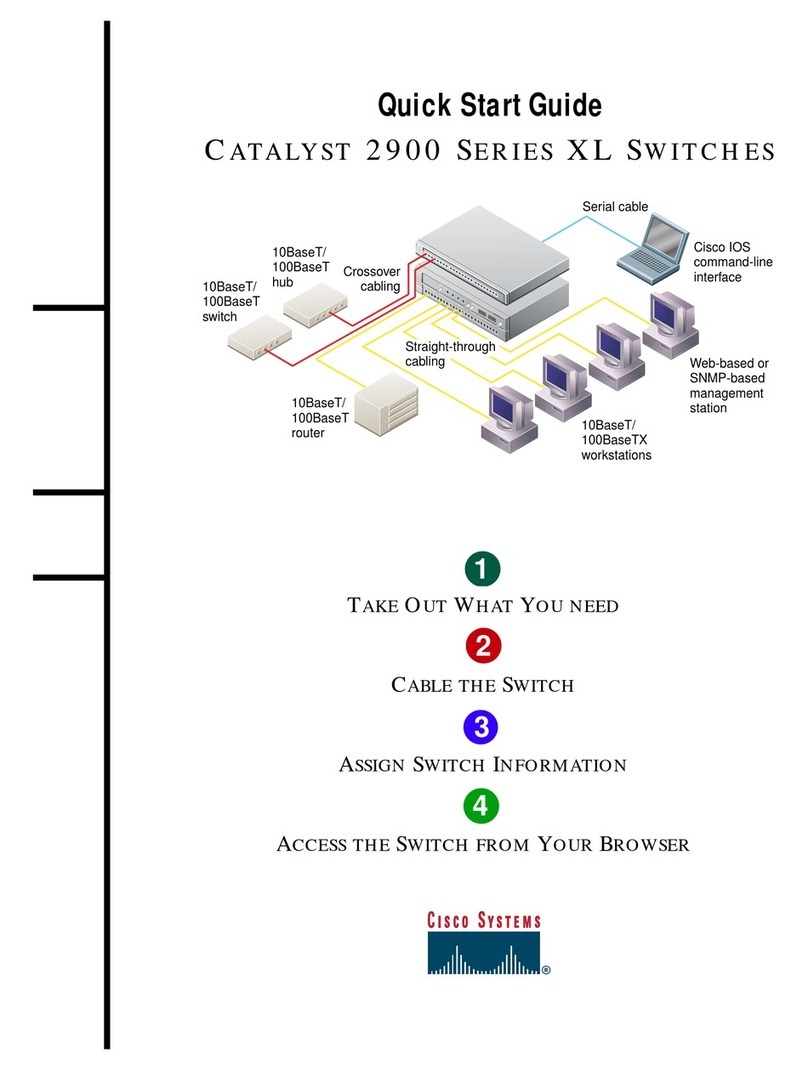
Cisco Catalyst 2900 Series XL User manual

Cisco
Cisco o SOHO 77H User manual
Cisco
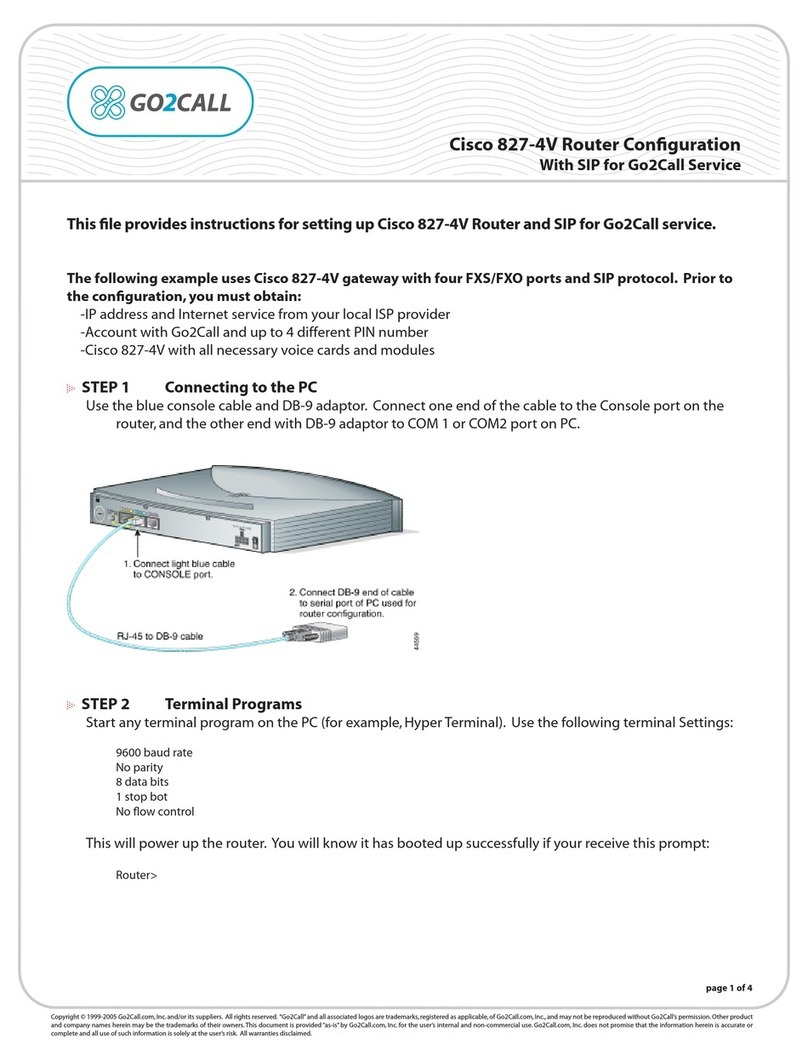
Cisco 827-4V - 827-4V Router - EN Quick guide
Cisco
Cisco 2600 Series Installation guide
Cisco
Cisco 7200 Series Original instructions

Cisco
Cisco XR 12000 User manual

Cisco
Cisco RV042 - Small Business Dual WAN VPN Router User manual

Cisco
Cisco CGR 1120 User manual

Cisco
Cisco RV120W User manual
Cisco
Cisco 2691 Series User manual

Cisco
Cisco ASR 900 Series User manual

Cisco
Cisco 809 Manual

Cisco
Cisco 2691 - VPN Bundle Router Manual































