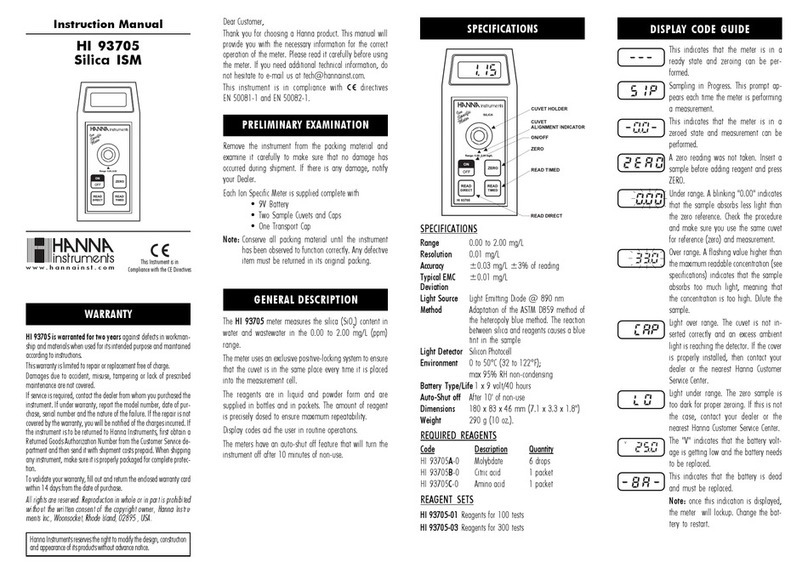
COUNTERFLOW AI ThreatEye NetworkTraffic Recorder Operating and maintenance manual

IN THE BOX
SAFETY, COMPLIANCE, AND PRODUCT DISPOSAL
CLASS ONE LASER PRODUCT
Flex 4x1/10 Gbps
• ThreatEyeTM NetworkTraffic Recorder Unit
• Cable Management Kit
• Sliding Rails
• Power Cords
• Accessory Kit:
• PTP Time Synchronization Cable
• 4 Transceiver Modules (Dual Rate 1/10 Gbps)
• Product Information Guide
• CounterFlow AI Installation Quick Start (this guide)
• CounterFlow AI Software Licensing Agreement
Warning: This unit is fitted with optical transmitter
modules that are class 1 lasers. Use of controls,
adjustments or performance of procedures other than
those specified herein might result in hazardous
light exposure.
Read and take careful note of the guidelines in the
product information guide regarding:
• Safety and precautions that you should take during
the installation
• EMC compliance with FCC and other regulations
• Recycling and disposal of this product
UNPACK AND INSTALL HARDWARE
Unpack the ThreatEyeTM Network Traffic Recorder unit and install it in a rack or similar. See the product
information guide for details about unpacking the ThreatEyeTM Network Traffic Recorder unit.
The unit comes with sliding rails and a cable management arm for mounting into a standard 19-inch rack
system. We recommend installing all cables into the cable management arm to make it easier to access the
unit later without damaging the cables.
• Ensure that the ThreatEyeTM Network Traffic Recorder unit is powered off.
• Plug the transceiver modules into the capture network ports. Make sure that the latch is firmly
secured, and connect the fiber optic cable, if applicable. CAUTION. To avoid exposure to laser light, do not
remove the protective plugs from the transceiver modules until the fiber-optic cables are ready to be
connected. Retain and replace the plugs if the cables are removed.
• Connect a network cable to any management port.
• Connect one or more of the fiber capture network ports to the network that you want to capture
traffic from. All ports are 1 Gbps capable, and depending on your unit, Ports 1 and 2 are also 10 Gbps capable.
• If you need external time synchronization, plug the supplied PTP time synchronization cable into
the connector.
• Connect the power cords to the redundant power supply in the ThreatEyeTM Network Traffic Recorder unit.
The ThreatEyeTM Network Traffic Recorder unit is now connected and ready for initial configuration.
INSTALLATION QUICK START

ThreatEyeTM Network Traffic Recorder
ThreatEyeTM Network Traffic Recorder storage unit
ThreatEyeTM Network Traffic Recorder storage unit
ThreatEyeTM Network Traffic Recorder storage unit
CONFIGURATION
IP ADDRESS
The ThreatEyeTM Network Traffic Recorder has a static IP address of 192.168.100.100.
If you need to change the IP address:
• Plug a monitor and keyboard into the ThreatEyeTM Network Traffic Recorder unit, and power it on.
• Select Configure Network from the menu and press ENTER.
• In the ThreatEyeTM Network Traffic Recorder IP Settings prompt, change the IP address, subnet mask
and/or gateway to your preference.
• Press A and ENTER to apply your changes, or U and ENTER to use DHCP.
Connect to the ThreatEyeTM Network Traffic Recorder UI using your preferred browser. On the dashboard, use
the ADMIN tab to review your settings.
FURTHER DOCUMENTATION
Enter the URL https://yourIPaddress/api where your IPaddress is the IP address or host name of the
ThreatEyeTM Network Traffic Recorder. This opens the interactive API documentation.
Further documentation can be accessed from the Help icon on the ThreatEyeTM Network Traffic Recorder User
Interface toolbar.
For information about iDrac, see the supplied product information guide.
CONNECTING STORAGE UNITS
Using one or more storage interconnect cables, connect the
ThreatEyeTM Network Traffic Recorder storage units through the
external HD Mini-SAS connectors as shown in the image.
Important: Ensure that the HD Mini-SAS connector is correctly
inserted in the ThreatEyeTM Network Traffic Recorder, and locked,
when connecting to a ThreatEyeTM Network Traffic Recorder
storage unit. The connector has a latch tab that physically locks
the connection. The space between the server chassis of the
ThreatEyeTM Network Traffic Recorder unit and the port casing is
very small and can prevent the latch tab from locking into the port
casing. You can test if the connection is locked by gently pulling
the connector cable after you have plugged it in.
6181 Rockfish Gap Turnpike
Crozet, Virginia 22932
Disclaimer: This document is intended for informational purposes only. Any information herein is believed to be reliable. However, CounterFlow AI assumes no responsibility for
the accuracy of the information. CounterFlow AI reserves the right to change the document and the products described without notice. CounterFlow AI and the authors disclaim
any and all liabilities. CounterFlow AI is a trademark used under license by CounterFlow AI A/S. All other logos, trademarks and service marks are the property of the respective
third parties. Copyright © CounterFlow AI A/S 2019. All rights reserved.
Virginia-based CounterFlow is the first security provider to deliver true intelligent packet capture capabilities
and practical application of machine learning, helping security teams conduct smart, real-time analysis on
the data that matters most. The firm arms security teams with a sophisticated foundation to continually
customize and evolve its capture and threat identification techniques to reduce dwell time without
increasing data storage infrastructure footprint and associated costs.
For more information, visit https://counterflow.ai/.
DEFAULT LOGIN
• Username: admin
• Password: pandion
Important: For security reasons,
change the password for the
default admin user.
INITIALIZING STORAGE UNITS
WARNING: All existing data is lost when you initialize a storage unit.
• Click the ADMIN tab.
• In the CONTROL widget, click Factory Reset under Power Controls.
• When the ThreatEyeTM Network Traffic Recorder has reset, the
ThreatEyeTM Network Traffic Recorder storage units are detected
and ready for use.
Table of contents