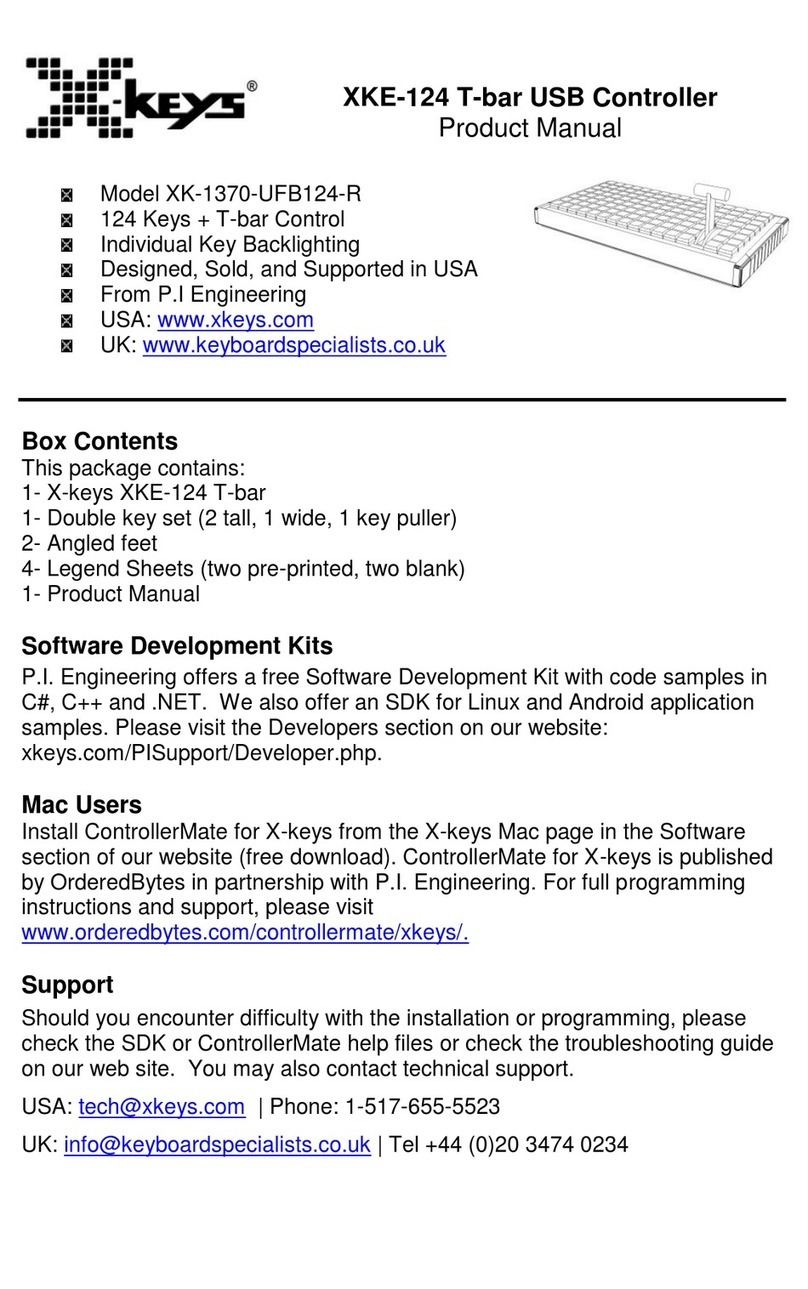
Hewlett Packard Enterprise Aruba 7 Series User manual

Aruba 7XXX Series Controllers
with ArubaOS FIPS Firmware
Non-Proprietary Security Policy
FIPS 140-2 Level 2
Version 1.17
June 2016
Aruba 7200 Series Controllers FIPS 140-2 Level 2 Security Policy

Copyright
© 2016 Hewlett Packard Enterprise Company. Hewlett Packard Enterprise Company trademarks include,
Aruba Networks®, Aruba Wireless Networks®, the registered Aruba the Mobile Edge Company logo, Aruba Mobility Management
System®, Mobile Edge Architecture®, People Move. Networks Must Follow®, RFprotectrotect®, Green Island®. All rights reserved. All
other trademarks are the property of their respective owners. Open Source Code
Certain Hewlett Packard Enterprise Company products include Open Source software code developed by third parties, including
software code subject to the GNU General Public License (GPL), GNU Lesser General Public License (LGPL), or other Open Source
Licenses. The Open Source code used can be found at this site:
http://www.arubanetworks.com/open_source
Legal Notice
The use of Aruba. switching platforms and software, by all individuals or corporations, to terminate other vendors’ VPN client devices
constitutes complete acceptance of liability by that individual or corporation for this action and indemnifies, in full, Aruba. from any and
all legal actions that might be taken against it with respect to infringement of copyright on behalf of those vendors.
Warranty
This hardware product is protected by the standard Aruba warranty of one year parts/labor. For more information, refer to the
ARUBACARE SERVICE AND SUPPORT TERMS AND CONDITIONS.
Altering this device (such as painting it) voids the warranty.
Copyright
© 2016 Hewlett Packard Enterprise Company. Hewlett Packard Enterprise Company trademarks include, Aruba Networks®, Aruba
Wireless Networks®,the registered Aruba the Mobile Edge Company logo, and Aruba Mobility Management System®.
www.arubanetworks.com
1344 Crossman Avenue
Sunnyvale, California 94089
Phone: 408.227.4500
Fax 408.227.4550
2|Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy

Contents
Contents............................................................................................................................................................................. 3
Preface............................................................................................................................................................................... 5
Purpose of this Document............................................................................................................................................... 5
Related Documents ......................................................................................................................................................... 5
Additional Product Information ......................................................................................................................5
Overview............................................................................................................................................................................ 6
Cryptographic Module Boundaries................................................................................................................7
Intended Level of Security ............................................................................................................................................ 10
Physical Security............................................................................................................................................................ 11
Operational Environment .............................................................................................................................................. 11
Logical Interfaces........................................................................................................................................................... 12
Roles and Services........................................................................................................................................................ 13
Crypto Officer Role......................................................................................................................................13
Authentication Mechanisms.........................................................................................................................18
Unauthenticated Services............................................................................................................................19
Non-Approved Services...............................................................................................................................19
Cryptographic Key Management ................................................................................................................................. 19
Implemented Algorithms..............................................................................................................................19
Critical Security Parameters........................................................................................................................22
Alternating Bypass State............................................................................................................................................... 30
Installing the Controller ........................................................................................................................................................ 31
Pre-Installation Checklist............................................................................................................................................... 31
Precautions ..................................................................................................................................................................... 31
Product Examination ...................................................................................................................................31
Package Contents.......................................................................................................................................32
Tamper-Evident Labels................................................................................................................................................. 33
Reading TELs..............................................................................................................................................33
Required TEL Locations..............................................................................................................................34
Applying TELs .............................................................................................................................................42
Ongoing Management .......................................................................................................................................................... 42
Crypto Officer Management.......................................................................................................................................... 42
Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy|3

User Guidance................................................................................................................................................................ 43
Setup and Configuration................................................................................................................................................ 43
Setting Up Your Controller............................................................................................................................................ 43
Enabling FIPS Mode...................................................................................................................................................... 43
Enabling FIPS Mode with the WebUI..........................................................................................................43
Enabling FIPS Mode with the CLI................................................................................................................43
Disabling the LCD........................................................................................................................................44
Disallowed FIPS Mode Configurations ....................................................................................................................... 44
4|Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy

Preface
This security policy document can be copied and distributed freely.
Purpose of this Document
This release supplement provides information regarding the Aruba 7XXX Controllers with FIPS 140-2 Level 2 validation
from Aruba Networks. The material in this supplement modifies the general Aruba hardware and firmware documentation
included with this product and should be kept with your Aruba product documentation.
This supplement primarily covers the non-proprietary Cryptographic Module Security Policy for the Aruba Controller. This
security policy describes how the controller meets the security requirements of FIPS 140-2 Level 2 and how to place and
maintain the controller in a secure FIPS 140-2 mode. This policy was prepared as part of the FIPS 140-2 Level 2
validation of the product.
FIPS 140-2 (Federal Information Processing Standards Publication 140-2, Security Requirements for Cryptographic
Modules) details the U.S. Government requirements for cryptographic modules. More information about the FIPS 140-2
standard and validation program is available on the National Institute of Standards and Technology (NIST) website at:
http://csrc.nist.gov/groups/STM/cmvp/index.html
Related Documents
The following items are part of the complete installation and operations documentation included with this product:
•Aruba 7XXX Mobility Controller Installation Guide
•Aruba 7XXX- series Mobility Controller Installation Guide
•ArubaOS 6.5 User Guide
•ArubaOS 6.5 CLI Reference Guide
•ArubaOS 6.5 Quick Start Guide
•ArubaOS 6.5 Upgrade Guide
•Aruba AP Installation Guides
Additional Product Information
More information is available from the following sources:
•The Aruba Networks Web-site contains information on the full line of products from Aruba Networks:
http://www.arubanetworks.com
•The NIST Validated Modules Web-site contains contact information for answers to technical or sales-related
questions for the product:
http://csrc.nist.gov/groups/STM/cmvp/index.html
Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy|5

Overview
Aruba 7XXX series Mobility Controllers are optimized for 802.11ac and mobile app delivery. Fully
application-aware, the 7XXX series prioritizes mobile apps based on user identity and offers exceptional
scale for BYOD transactions and device densities.
With a new central processor employing eight CPU cores and four virtual cores, the 7XXX series supports
over 32,000 wireless devices and performs stateful firewall policy enforcement at speeds up to 40 Gbps –
plenty of capacity for BYOD and 802.11ac devices.
New levels of visibility, delivered by Aruba AppRF on the controller, allow IT to see applications by user,
including top web-based applications like Facebook and Box.
The 7XXX series also manages authentication, encryption, VPN connections, IPv4 and IPv6 services, the
Aruba Policy Enforcement Firewall™ with AppRF Technology, Aruba Adaptive Radio Management™,
and Aruba RFprotect™ spectrum analysis and wireless intrusion protection.
The Aruba controller configurations validated during the cryptographic module testing included:
•Aruba 7005-F1
•Aruba 7005-USF1
•Aruba 7010-F1
•Aruba 7010-USF1
•Aruba 7024-F1
•Aruba 7024-USF1
•Aruba 7030-F1
Aruba 7030-USF1
Aruba 7205-F1
Aruba 7205-USF1
FIPS Kit: 4011570-01 (Part number for Tamper Evident Labels)
The firmware versions validated are ArubaOS 6.4.4-FIPS and ArubaOS 6.5.0-FIPS
Note: For radio regulatory reasons, part numbers ending with -USF1 are to be sold in the US only. Part
numbers ending with -F1 are considered ‘rest of the world’ and must not be used for deployment in the
United States. From a FIPS perspective, both -USF1 and -F1 models are identical and fully FIPS
compliant.
6|Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy

Physical Description
Cryptographic Module Boundaries
For FIPS 140-2 Level 2 validation, the Controller has been validated as a multi-chip standalone
cryptographic module. The opaque hard plastic (Aruba 7005 Controller only) or metal chassis physically
encloses the complete set of hardware and firmware components and represents the cryptographic
boundary of the module. The cryptographic boundary is defined as encompassing the top, front, left, right,
rear, and bottom surfaces of the chassis.
Figure 1 - The Aruba 7005 controller
Figure 1 shows the front of the Aruba 7005 Controller, and illustrates the following:
•Four Gigabit Ethernet ports
•One Type A USB port
•LINK/ACT and Status LEDs
•Management/Status LED
•Console Connections - RJ-45 and Mini-USB (Disabled in FIPS mode by TELs)
Figure 2 - The Aruba 7010 controller
Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy|7

Figure 2 shows the front of the Aruba 7010 Controller, and illustrates the following:
•Sixteen 10/100/1000 Ethernet ports
•Two Small Form-Factor Pluggable (SFP) Uplink ports
•Two Type A USB ports
•LINK/ACT and Status LEDs
•Management/Status LED
•LCD Panel
•Navigation Buttons (Functionally disabled in FIPS mode)
•Console Connections - RJ-45 and Mini-USB (Disabled in FIPS mode by TELs)
Figure 3 - The Aruba 7024 controller
8|Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy

Figure 3 shows the front of the Aruba 7024 Controller, and illustrates the following:
•Twenty-four 10/100/1000 Ethernet ports
•Two Enhanced Small Form-Factor Pluggable (SFP+) Uplink ports
•One Type A USB ports
•LINK/ACT and Status LEDs
•Management/Status LED
•LCD Panel
•Navigation Buttons (Functionally disabled in FIPS mode)
•Console Connections - RJ-45 and Mini-USB (Disabled in FIPS mode by TELs)
Figure 4 - The Aruba 7030 controller chassis
Figure 4 shows the front of the Aruba 7030 Controller, and illustrates the following:
•Eight 10/100/1000 Ethernet ports
•Eight Small Form-Factor Pluggable (SFP) Uplink ports
•One Type A USB port
•LINK/ACT and Status LEDs
•Management/Status LED
•LCD Panel
•Navigation Buttons (Functionally disabled in FIPS mode)
•Console Connections - RJ-45 and Mini-USB (Disabled in FIPS mode by TELs)
Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy|9

Figure 5 - The Aruba 7205 controller chassis
Figure 5 shows the front of the Aruba 7205 Controller, and illustrates the following:
•Four 10/100/1000 Ethernet ports
•Four Small Form-Factor Pluggable (SFP) Uplink ports
•Two Dual-Purpose Gigabit Uplink Ports
•Two Type A USB ports (one is on the front and one is on the back)
•LINK/ACT and Status LEDs
•Management/Status LED
•LCD Panel
•Navigation Buttons (Functionally disabled in FIPS mode)
•Console Connections - RJ-45 and Mini-USB (Disabled in FIPS mode by TELs)
Intended Level of Security
The 7XXX Controller and associated modules are intended to meet overall FIPS 140-2 Level 2
requirements as shown in Table 1.
Table 1 Intended Level of Security
Section Section Title Level
1 Cryptographic Module Specification 2
2 Cryptographic Module Ports and Interfaces 2
3 Roles, Services, and Authentication 2
10|Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy

4 Finite State Model 2
5 Physical Security 2
6 Operational Environment N/A
7 Cryptographic Key Management 2
8 EMI/EMC 2
9 Self-tests 2
10 Design Assurance 2
11 Mitigation of Other Attacks N/A
Overall Overall module validation level 2
Physical Security
The Aruba Controller is a scalable, multi-processor standalone network device and is enclosed in a robust
steel housing. The controller enclosure is resistant to probing and is opaque within the visible spectrum.
The enclosure of the module has been designed to satisfy FIPS 140-2 Level 2 physical security
requirements.
The Aruba 7XXX Controller requires Tamper-Evident Labels (TELs) to allow the detection of the opening
of the chassis cover and to block the Serial console port.
To protect the Aruba 7XXX Controller from any tampering with the product, TELs should be applied by
the Crypto Officer as covered under “Tamper-Evident Labels” on page 33.
Operational Environment
The operational environment is non-modifiable. The control plane Operating System (OS) is Linux, a real-
time, multi-threaded operating system that supports memory protection between processes. Access to the
underlying Linux implementation is not provided directly. Only Aruba Networks provided interfaces are
used, and the CLI is a restricted command set. The module only allows the loading of trusted and verified
firmware that is signed by Aruba.
Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy|11

Logical Interfaces
All of these physical interfaces are separated into logical interfaces defined by FIPS 140-2, as described
in the following table.
Table 2 FIPS 140-2 Logical Interfaces
FIPS 140-2 Logical Interface Module Physical Interface
Data Input Interface •10/100/1000 Ethernet Ports
•SFP/SFP+ Uplink Ports
•USB Port
Data Output Interface •10/100/1000 Ethernet Ports
•SFP/SFP+ Uplink Ports
•USB Port
Control Input Interface •10/100/1000 Ethernet Ports
•SFP/SFP+ Uplink Ports
Status Output Interface •10/100/1000 Ethernet Ports
•SFP/SFP+ Uplink Ports
•USB Port
•LEDs
Power Interface •Power Supply
Data input and output, control input, status output, and power interfaces are defined as follows:
Data input and output are the packets that use the firewall, VPN, and routing functionality of the modules.
•Control input consists of manual control inputs for power and reset through the power and reset
switch. It also consists of all of the data that is entered into the controller while using the management
interfaces.
•Status output consists of the status indicators displayed through the LEDs, the status data that is
output from the controller while using the management interfaces, and the log file.
•LEDs indicate the physical state of the module, such as power-up (or rebooting), utilization level,
activation state (including fan, ports, and power). The log file records the results of self-tests,
configuration errors, and monitoring data.
•A power supply is used to connect the electric power cable.
The controller distinguishes between different forms of data, control, and status traffic over the network
ports by analyzing the packets header information and contents.
12|Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy

Roles and Services
The Aruba Controller supports role-based authentication. There are two roles in the module (as required
by FIPS 140-2 Level 2) that operators may assume: a Crypto Officer role and a User role. The
Administrator maps to the Crypto-Officer role and the client Users map to the User role.
Crypto Officer Role
The Crypto Officer role has the ability to configure, manage, and monitor the controller. Three
management interfaces can be used for this purpose:
•SSHv2 CLI
The Crypto Officer can use the CLI to perform non-security-sensitive and security-sensitive
monitoring and configuration. The CLI can be accessed remotely by using the SSHv2 secured
management session over the Ethernet ports or locally over the serial port. In FIPS mode, the serial
port is disabled.
•Web Interface
The Crypto Officer can use the Web Interface as an alternative to the CLI. The Web Interface
provides a highly intuitive, graphical interface for a comprehensive set of controller management
tools. The Web Interface can be accessed from a TLS-enabled Web browser using HTTPS (HTTP
with Secure Socket Layer) on logical port 4343.
•SNMPv3
The Crypto Officer can also use SNMPv3 to remotely perform monitoring and use ‘get’ and ‘getnext’
commands.
See the table below for descriptions of the services available to the Crypto Officer role.
Table 3 Crypto-Officer Services
Service Description Input Output
CSP Access
(please see table
6 below for CSP
details)
SSHv2 Provide authenticated and
encrypted remote management
sessions while using the CLI
SSHv2 key agreement
parameters, SSH
inputs, and data
SSHv2 outputs and
data 27, 28 (delete)
Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy|13

Table 3 Crypto-Officer Services
SNMPv3 Provides ability to query
management information SNMPv3 requests SNMPv3
responses 32, 33 (read)
34 (delete)
IKEv1/IKEv2-
IPSec Provide authenticated and
encrypted remote management
sessions to access the CLI
functionality
IKEv1/IKEv2 inputs and
data; IPSec inputs,
commands, and data
IKEv1/IKEv2
outputs, status, and
data; IPSec
outputs, status, and
data
19 (read)
20, 21, 22, 23, 24,
25 and 26 (delete)
Configuring
Network
Management
Create management Users and
set their password and privilege
level; configure the SNMP agent
Commands and
configuration data Status of
commands and
configuration data
32, 33 (read)
34 (delete)
Configuring
Module Platform Define the platform subsystem
firmware of the module by
entering Bootrom Monitor Mode,
File System, fault report,
message logging, and other
platform related commands
Commands and
configuration data Status of
commands and
configuration data
None
Configuring
Hardware
Controllers
Define synchronization features
for module Commands and
configuration data Status of
commands and
configuration data
None
Configuring
Internet Protocol Set IP functionality Commands and
configuration data Status of
commands and
configuration data
None
Configuring
Quality of Service
(QoS)
Configure QOS values for module Commands and
configuration data Status of
commands and
configuration data
None
14|Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy

Table 3 Crypto-Officer Services
Configuring VPN Configure Public Key
Infrastructure (PKI); configure the
Internet Key Exchange
(IKEv1/IKEv2) Security Protocol;
configure the IPSec protocol
Commands and
configuration data Status of
commands and
configuration data
19 (read)
16, 17, 18, 19, 20,
21, 22, 23, 24,25 and
26 (delete)
Configuring DHCP Configure DHCP on module Commands and
configuration data Status of
commands and
configuration data
None
Configuring
Security Define security features for
module, including Access List,
Authentication, Authorization and
Accounting (AAA), and firewall
functionality
Commands and
configuration data Status of
commands and
configuration data
12, 13, 14
(read/write/delete)
Manage
Certificates Install, rename, and delete X.509
certificates Commands and
configuration data;
Certificates and keys
Status of
certificates,
commands, and
configuration
15, 16, 17,18
(write/delete)
HTTPS over TLS Secure browser connection over
Transport Layer Security acting
as a Crypto Officer service (web
management interface)
TLS inputs, commands,
and data TLS outputs,
status, and data 29, 30 and 31
(delete)
Status Function Cryptographic officer may use
CLI "show" commands or view
WebUI via TLS to view the
controller configuration, routing
tables, and active sessions; view
health, temperature, memory
status, voltage, and packet
statistics; review accounting logs,
and view physical interface status
Commands and
configuration data Status of
commands and
configurations
None
IPSec tunnel
establishment for
RADIUS
protection
Provided authenticated/encrypted
channel to RADIUS server IKEv1/IKEv2 inputs and
data; IPSec inputs,
commands, and data
IKEv1/IKEv2
outputs, status, and
data; IPSec
outputs, status, and
data
12 and 19
(read/write/delete)
20, 21, 22, 23, 24, 25
and 26 (write/delete)
Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy|15

Table 3 Crypto-Officer Services
Self-Test Perform FIPS start-up tests on
demand None Error messages
logged if a failure
occurs
None
Configuring
Bypass Operation Configure bypass operation on
the module Commands and
configuration data Status of
commands and
configuration data
None
Updating
Firmware Updating firmware on the module Commands and
configuration data Status of
commands and
configuration data
None
Configuring Online
Certificate Status
Protocol (OCSP)
Responder
Configuring OCSP responder
functionality OCSP inputs,
commands, and data OCSP outputs,
status, and data 27, 28, 29, 30 (read)
Configuring
Control Plane
Security (CPSec)
Configuring Control Plane
Security mode to protect
communication with APs using
IPSec and issue self signed
certificates to APs
Commands and
configuration data,
IKEv1/IKEv2 inputs and
data; IPSec inputs,
commands, and data
Status of
commands, IKEv1/
IKEv2 outputs,
status, and data;
IPSec outputs,
status, and data
and configuration
data, self signed
certificates
12 and 19
(read/write/delete)
20, 21, 23, 22, 24, 25
and 26 (write/delete)
Zeroization The cryptographic keys stored in
SDRAM memory can be zeroized
by rebooting the module. The
cryptographic keys (IKEv1 Pre-
shared key and 802.11i Pre-
Shared Key) stored in the flash
can be zeroized by using
command ‘ap wipe out flash’ or
by overwriting with a new secret.
The other keys/CSPs (KEK,
RSA/ECDSA public key/private
key and certificate) stored in
Flash memory can be zeroized by
using command ‘write erase all.
Command Progress
information All CSPs will be
destroyed.
16|Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy

User Role
Table 4 below lists the services available to User role:
Table 4 User Service
Service Description Input Output
CSP Access (please
see table 6 below for
CSP details)
IKEv1/IKEv2-
IPSec Access the module's IPSec
services in order to secure
network traffic
IPSec inputs,
commands, and data IPSec outputs,
status, and data
20, 21, 22, 23, 24, 25 and
26 (delete)
HTTPS over TLS Access the module’s TLS
services in order to secure
network traffic
TLS inputs,
commands, and data TLS outputs,
status, and data 29, 30, 31 (delete)
EAP-TLS
termination Provide EAP-TLS termination EAP-TLS inputs,
commands and data EAP-TLS outputs,
status and data 29, 30, 31 (read/delete)
802.11i Shared
Key Mode Access the module’s 802.11i
services in order to secure
network traffic
802.11i inputs,
commands and data 802.11i outputs,
status and data 36, 37 and 38 (delete)
802.11i with EAP-
TLS Access the module’s 802.11i
services in order to secure
network traffic
802.11i inputs,
commands and data 802.11i outputs,
status, and data 36, 37 and 38 (delete)
Self-Tests Run Power-On Self-Tests and
Conditional Tests None Error messages
logged if a failure
occurs
None
Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy|17

Authentication Mechanisms
The Aruba Controller supports role-based authentication. Role-based authentication is performed before
the Crypto Officer enters privileged mode using admin password via Web Interface or SSHv2 or by
entering enable command and password in console. Role-based authentication is also performed for
User authentication.
This includes password and RSA/ECDSA-based authentication mechanisms. The strength of each
authentication mechanism is described below.
Table 5 Estimated Strength of Authentication Mechanisms
Authentication Type Role Strength
Password-based authentication Crypto Officer Passwords are required to be a minimum of eight characters and a
maximum of 32 with a minimum of one letter and one number. If six
(6) integers, one (1) special character and one (1) alphabet are used
without repetition for an eight (8) digit PIN, the probability of
randomly guessing the correct sequence is one (1) in 251,596,800
(this calculation is based on the assumption that the typical standard
American QWERTY computer keyboard has 10 Integer digits, 52
alphabetic characters, and 32 special characters providing 94
characters to choose from in total. The calculation should be 10 x 9 x
8 x 7 x 6 x 5 x 32 x 52 = 251, 595, 800). Therefore, the associated
probability of a successful random attempt during a one-minute
period is approximate 1 in 251,596,800, which is less than 1 in
100,000 required by FIPS 140-2.
Password-based authentication
(WPA2-PSK) User
Same authentication mechanism strength as CO role above.
Password-based authentication
(IKEv1) User
A 64 ASCII (128 HEX) character pre-shared string is randomly
chosen by the administrator. It may consist of upper and lower case
alphabetic characters, numeric characters and 32 special characters.
The probability of randomly guessing the correct sequence is one (1)
in 94^64. This calculation is based on the assumption that the
typical standard American QWERTY computer keyboard has 10
Integer digits, 52 alphabetic characters, and 32 special characters
providing 94 characters to choose from in total. Therefore, the
associated probability of a successful random attempt is
approximately 1 in 94^64, which is less than 1 in 1,000,000 required
by FIPS 140-2.
RSA-based authentication
(IKEv1, IKEv2 and TLS) User The module supports 2048-bit RSA keys authentication during
IKEv1, IKEv2 and TLS. RSA 2048 bit keys correspond to 112 bits of
security. Assuming the low end of that range, the associated
probability of a successful random attempt is 1 in 2^112, which is
less than 1 in 1,000,000 required by FIPS 140-2.
18|Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy

ECDSA-based authentication
IKEv1, IKEv2 and TLS User ECDSA signing and verification is used to authenticate to the module
during IKEv1/IKEv2. Both P-256 and P-384 curves are supported.
ECDSA P-256 provides 128 bits of equivalent security, and P-384
provides 192 bits of equivalent security. Assuming the low end of
that range, the associated probability of a successful random attempt
during a one-minute period is 1 in 2^128, which is less than 1 in
100,000 required by FIPS 140-2.
Unauthenticated Services
The Aruba Controller can perform VLAN, bridging, firewall, routing, and forwarding functionality without
authentication. These services do not involve any cryptographic processing.
Additional unauthenticated services include performance of the power-on self-test and system status
indication via LEDs.
Non-Approved Services
The following non-approved services are available in non-FIPS mode.
•IPSec/IKE with Diffie-Hellman 768-bit/1024-bit moduli, DES, HMAC-MD5 and MD5
•SSHv1 using RC4
Please note that all CSPs will be zeroized automatically when switching from FIPS mode to non-FIPS
mode, or from non-FIPS mode to FIPS mode.
Cryptographic Key Management
Implemented Algorithms
The firmware in each module contains the following cryptographic algorithm implementations/crypto
libraries to implement the different FIPS approved cryptographic algorithms that will be used for the
corresponding security services supported by the module in FIPS mode:
•ArubaOS OpenSSL library algorithm implementation
•ArubaOS Crypto library algorithm implementation
•ArubaOS UBootloader library algorithm implementation
•Aruba Hardware Crypto Accelerator algorithm implementation
Below are the detailed lists for the FIPS approved algorithms and the associated certificate implemented
by each algorithm implementation.
•Aruba Hardware Crypto Accelerator algorithm implementation:
oAES (Certs. #2477 and #3014)
oTriple-DES (Certs. #1516 and #1770)
oSHS (Certs. #2096 and #2522)
oHMAC (Certs. #1520 and #1906)
oRSA (Certs. #1266 and #1573)
Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy|19

The above hardware algorithm certificates were tested on Broadcom XLP series processors by Broadcom
Corporation. Aruba Networks purchased the processors and put them in the Aruba modules to support
bulk cryptographic operations. Please be aware that there is no partnership between Aruba Networks and
Broadcom Corporation.
The firmware supports the following cryptographic implementations.
•ArubaOS OpenSSL library implements the following FIPS-approved algorithms:
oAES (Cert. #2900)
oSP800-135rev1 KDF CVL (Cert. #326)
oDRBG (Cert. #528)
oECDSA (Cert. #524)
oHMAC (Cert. #1835)
oKBKDF (Cert. #32)
oRSA (Cert. #1528)
oSHS (Cert. #2440)
oTriple-DES (Cert. #1726)
•ArubaOS Crypto library implements the following FIPS Approved Algorithms:
oAES (Cert. #2884)
oSP800-135rev1 KDF CVL (Cert. #314)1
oECDSA (Cert. #519)
oHMAC (Cert. #1818)
oRSA (Cert. #1518)
oSHS (Cert. #2425)
oTriple-DES (Cert. #1720)
•ArubaOS UBOOT Bootloader library implements the following FIPS-approved algorithms:
oRSA (Cert. #1517)
oSHS (Cert. #2424)
Non-FIPS Approved but Allowed Cryptographic Algorithms
•Diffie-Hellman (key agreement; key establishment methodology provides 112 bits of encryption
strength)
•EC Diffie-Hellman (key agreement; key establishment methodology provides 128 or 192 bits of
encryption strength)
•RSA (key wrapping; key establishment methodology provides 112 bits of encryption strength)
•NDRNG
Note: RSA key wrapping is used in TLS protocol implementation.
Non-FIPS Approved Cryptographic Algorithms
1Only the IKEv2 KDF is active on this algorithm implementation
20|Aruba 7XXX Series Controllers FIPS 140-2 Level 2 Security Policy
This manual suits for next models
1
Table of contents
Other Hewlett Packard Enterprise Controllers manuals