Hirschmann BAT54-Rail User manual

BAT54-Rail/F..
Release
7.54
06/08
Technical Support
HAC-Support@hirschmann.de
User Manual
Configuration
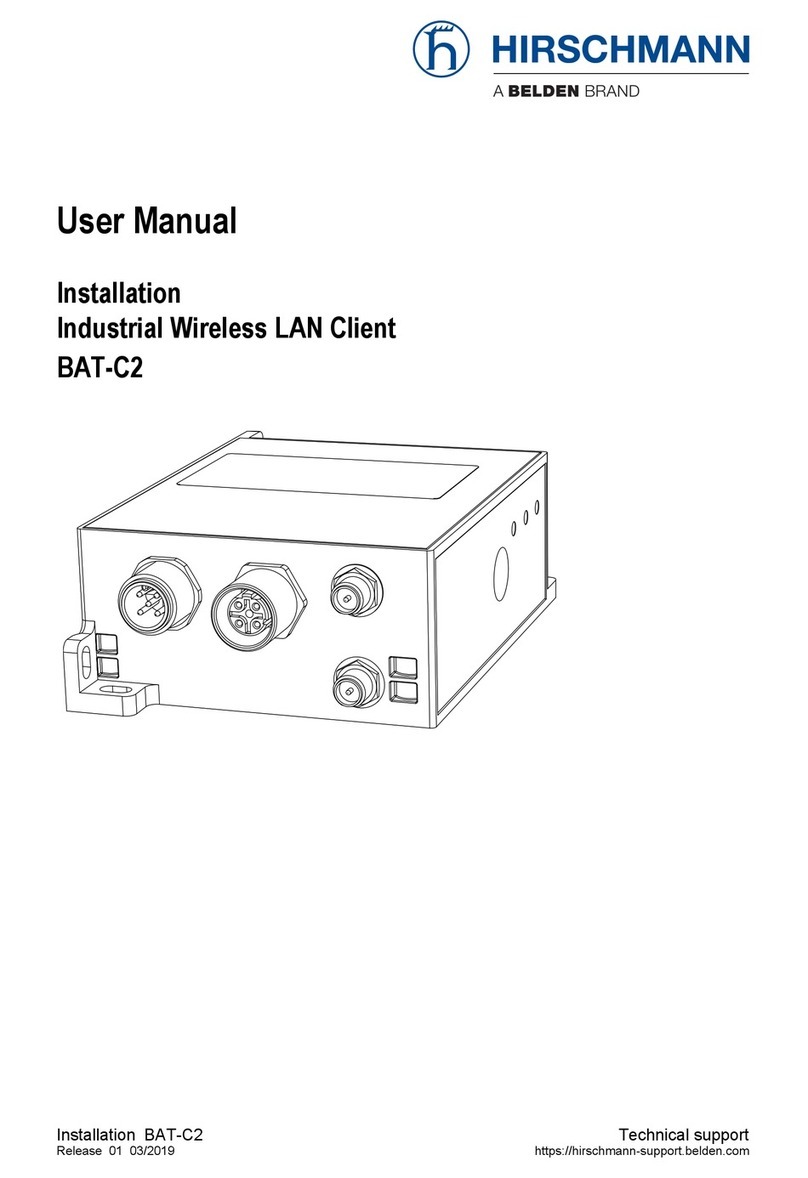
Dualband Industrial Wireless LAN Access Point/Client
BAT54-Rail, BAT54-Rail FCC,
BAT54-F, BAT54-F FCC, BAT54-F X2
BAT54-F X2 FCC

Windows®, Windows Vista™, Windows XP® and Microsoft® are registered trademarks of Mi-
crosoft, Corp. LCOS is registered trademarks of LANCOM Systems GmbH.
The naming of copyrighted trademarks in this manual, even when not specially indicated, should
not be taken to mean that these names may be considered as free in the sense of the trademark
and tradename protection law and hence that they may be freely used by anyone.
© 2008 Hirschmann Automation and Control GmbH
Manuals and software are protected by copyright. All rights reserved. The copying, reproduction,
translation, conversion into any electronic medium or machine scannable form is not permitted,
either in whole or in part. An exception is the preparation of a backup copy of the software for
your own use. For devices with embedded software, the end-user license agreement on the en-
closed CD applies.
This product includes software developed by the OpenSSL Project for use in the OpenSSL Tool-
kit http://www.openssl.org/.
This product includes software developed by the NetBSD Foundation, Inc. and its contributors.
The performance features described here are binding only if they have been expressly guaran-
teed in the contract. This publication has been created by Hirschmann Automation and Control
GmbH according to the best of our knowledge. Hirschmann reserves the right to change the con-
tents of this manual without prior notice. Hirschmann can give no guarantee in respect of the
correctness or accuracy of the details in this publication.
Hirschmann can accept no responsibility for damages, resulting from the use of the network
components or the associated operating software. In addition, we refer to the conditions of use
specified in the license contract.
Printed in Germany (30.6.2008)
Hirschmann Automation and Control GmbH
Stuttgarter Straße 45-51
72654 Neckartenzlingen
Tel. +49 1805 141538

BAT54-Rail/F..
Release
7.54
06/08 3
Contents
1 Preface 15
2 System design 19
2.1 Introduction 19
3 Wireless LAN – WLAN 21
3.1 What is a Wireless LAN? 21
3.1.1 Standardized radio transmission by IEEE 21
3.1.2 Operation modes of Wireless LANs and base stations 25
3.2 Development of WLAN security 33
3.2.1 Some basic concepts 33
3.2.2 WEP 35
3.2.3 WEPplus 37
3.2.4 EAP and 802.1x 37
3.2.5 TKIP and WPA 40
3.2.6 AES and 802.11i 42
3.2.7 Summary 44
3.3 Protecting the wireless network 45
3.3.1 LEPS—BAT Enhanced Passphrase Security 46
3.3.2 Standard WEP encryption 48
3.3.3 Background WLAN scanning 49
3.4 Configuration of WLAN parameters 52
3.4.1 WLAN security 53
3.4.2 General WLAN settings 62
3.4.3 WLAN routing (isolated mode) 63
3.4.4 The physical WLAN interfaces 64
3.4.5 The logical WLAN interfaces 78
3.4.6 Additional WLAN functions 82
3.5 Extended WLAN protocol filters 87
3.5.1 Protocol filter parameters 88
3.5.2 Procedure for filter test 90
3.5.3 Redirect function 91
3.5.4 DHCP address tracking 92

4BAT54-Rail/F..
Release
7.54
06/08
3.6 Client mode 93
3.6.1 Basic configuration 94
3.6.2 Advanced configuration 98
3.6.3 The roaming table 100
3.7 IEEE 802.11i for point-to-point connections in the WLAN 101
3.7.1 Antenna alignment for P2P operations 102
3.7.2 Configuration 104
3.7.3 Access points in relay mode 107
3.7.4 Security for point-to-point connections 107
3.7.5 LEPS for P2P connections 108
3.7.6 Geometric dimensioning of outdoor wireless network links
109
3.8 Establishing outdoor wireless networks 112
3.8.1 Geometrical layout of the transmission path 112
3.8.2 Antenna power 114
3.8.3 Emitted power and maximum distance 117
3.8.4 Transmission power reduction 117
3.9 Bandwidth limits in the WLAN 117
3.9.1 Operating as an access point 117
3.9.2 Operating as a Client 118
3.10 WLAN according to 802.11h 119
3.10.1 Standards 119
3.10.2 Radio channels in the 5 GHz band: 122
3.10.3 Frequency ranges for indoor and outdoor use 123
4 Configuration and management 125
4.1 Configuration tools and approaches 125
4.2 Configuration software 126
4.3 Searching and configuring devices 127
4.4 Configuration using different tools 128
4.4.1 LANconfig 128
4.4.2 WEBconfig 131
4.4.3 Telnet 133
4.4.4 TFTP 137
4.4.5 SNMP 138
4.4.6 Encrypted configuration with SSH access 139
4.4.7 SSH authentication 140
4.5 Working with configuration files 142

BAT54-Rail/F..
Release
7.54
06/08 5
4.6 New firmware with Hirschmann FirmSafe 143
4.6.1 This is how Hirschmann FirmSafe works 143
4.6.2 How to load new software 145
4.7 How to reset the device? 148
4.8 Managing administrators rights 150
4.8.1 Rights for the administrators 150
4.8.2 Administrators' access via TFTP and SNMP 151
4.8.3 Configuration of user rights 153
4.8.4 Limitation of the configuration commands 155
4.8.5 HTTP tunnel 156
4.9 Named loopback addresses 159
4.9.1 Loopback addresses with ICMP polling 160
4.9.2 Loopback addresses for time servers 161
4.9.3 Loopback addresses for SYSLOG clients 162
5 LANtools network management 165
5.1 Switch UI language 166
5.2 Project management with LANconfig 166
5.2.1 User-specific settings for LANconfig 169
5.2.2 Directory structure 170
5.2.3 Multithreading 171
5.2.4 Better overview in LANconfig with more columns 172
5.2.5 Manual and automatic searches for firmware updates 173
5.2.6 Password protection for SNMP read-only access. 175
5.2.7 Device-specific settings for communications protocols 177
5.2.8 LANconfig behavior at Windows startup 179
5.3 Scripting 181
5.3.1 Applications 181
5.3.2 Scripting function 182
5.3.3 Generating script files 183
5.3.4 Uploading configuration commands and script files 186
5.3.5 Multiple parallel script sessions 190
5.3.6 Scripting commands 190
5.3.7 WLAN configuration with the wizards in LANconfig 194
5.4 Group configuration with LANconfig 196
5.4.1 Create a group configuration 197
5.4.2 Update device configurations 199
5.4.3 Update group configurations 200
5.4.4 Using multiple group configurations 200

6BAT54-Rail/F..
Release
7.54
06/08
5.5 Rollout Wizard 201
5.5.1 General settings in the Rollout Wizard 201
5.5.2 Variables 202
5.5.3 Actions to be executed by the Rollout Wizard 203
5.5.4 Actions for managing the Rollout Wizard 204
5.6 Display functions in LANmonitor 205
5.7 LANmonitor—know what's going on 208
5.7.1 Extended display options 209
5.7.2 Enquiry of the CPU and Memory utilization over SNMP
210
5.7.3 Monitor Internet connection 210
5.7.4 Tracing with LANmonitor 212
5.8 Visualization of larger WLANs 214
5.8.1 Start the WLANmonitor 215
5.8.2 Search for access points 215
5.8.3 Add access points 216
5.8.4 Organize access points 216
5.8.5 Rogue AP and rogue client detection with the
WLANmonitor 217
5.9 Messaging 222
6 Diagnosis 225
6.1 Trace information—for advanced users 225
6.1.1 How to start a trace 225
6.1.2 Overview of the keys 225
6.1.3 Overview of the parameters 226
6.1.4 Combination commands 227
6.1.5 Trace filters 227
6.1.6 Examples of traces 228
6.1.7 Recording traces 228
6.2 SYSLOG storage in the device 229
6.2.1 Activate SYSLOG module 230
6.2.2 Configuring the SYSLOG client 230
6.2.3 Read-out SYSLOG messages 231
6.3 The ping command 232
6.4 Monitoring the switch 233
6.5 Cable testing 234

BAT54-Rail/F..
Release
7.54
06/08 7
7 Security 237
7.1 Protection for the configuration 237
7.1.1 Password protection 237
7.1.2 Login barring 239
7.1.3 Restriction of the access rights on the configuration 240
7.2 The security checklist 244
8 Firewall 249
8.1 Threat analysis 249
8.1.1 The dangers 249
8.1.2 The ways of the perpetrators 250
8.1.3 The methods 250
8.1.4 The victims 251
8.2 What is a Firewall? 252
8.2.1 Tasks of a Firewall 252
8.2.2 Different types of Firewalls 253
8.3 The BAT Firewall 259
8.3.1 How the BAT Firewall inspects data packets 259
8.3.2 Special protocols 262
8.3.3 General settings of the Firewall 264
8.3.4 Parameters of Firewall rules 268
8.3.5 Alerting functions of the Firewall 274
8.3.6 Strategies for Firewall settings 279
8.3.7 Hints for setting the Firewall 281
8.3.8 Configuration of Firewall rules 285
8.3.9 Firewall diagnosis 295
8.3.10 Firewall limitations 301
8.4 Intrusion Detection 302
8.4.1 Examples for break-in attempts 302
8.4.2 Configuration of the IDS 303
8.5 Denial of Service 304
8.5.1 Examples of Denial of Service Attacks 304
8.5.2 Configuration of DoS blocking 307
8.5.3 Configuration of ping blocking and Stealth mode 309
9 Quality of Service 311
9.1 Why QoS? 311

8BAT54-Rail/F..
Release
7.54
06/08
9.2 Which data packets to prefer? 312
9.2.1 Guaranteed minimum bandwidths 313
9.2.2 Limited maximum bandwidths 315
9.3 The queue concept 315
9.3.1 Queues in transmission direction 315
9.3.2 Queues for receiving direction 317
9.4 Reducing the packet length 318
9.5 QoS parameters for Voice over IP applications 320
9.6 QoS in sending or receiving direction 324
9.7 QoS configuration 325
9.7.1 Evaluating ToS and DiffServ fields 325
9.7.2 Defining minimum and maximum bandwidths 328
9.7.3 Adjusting transfer rates for interfaces 329
9.7.4 Sending and receiving direction 331
9.7.5 Reducing the packet length 331
9.8 QoS for WLANs (IEEE 802.11e) 333
10 Virtual LANs (VLANs) 335
10.1 What is a Virtual LAN? 335
10.2 This is how a VLAN works 335
10.2.1 Frame tagging 336
10.2.2 Conversion within the LAN interconnection 337
10.2.3 Application examples 338
10.3 Configuration of VLANs 340
10.3.1 The network table 341
10.3.2 The port table 341
10.3.3 Configuration with LANconfig 342
10.3.4 Configuration with WEBconfig or Telnet 344
10.4 Configurable VLAN Protocol ID 345
10.5 Configurable VLAN IDs 346
10.5.1 Different VLAN IDs per WLAN client 346
10.5.2 Special VLAN ID for DSLoL interfaces 346
10.6 VLAN tags on layer 2/3 in the Ethernet 347
10.6.1 Configuring VLAN tagging on layer 2/3 348
10.7 VLAN tags for DSL interfaces 349
10.8 VLAN Q-in-Q tagging 350

BAT54-Rail/F..
Release
7.54
06/08 9
11 Routing and WAN connections 353
11.1 General information 353
11.1.1 Bridges for standard protocols 353
11.1.2 What happens in the case of a request from the LAN?
354
11.2 IP routing 355
11.2.1 The IP routing table 355
11.2.2 Policy-based routing 358
11.2.3 Local routing 361
11.2.4 Dynamic routing with IP RIP 362
11.2.5 SYN/ACK speedup 365
11.3 Configuration of remote stations 366
11.3.1 Peer list 366
11.3.2 Layer list 368
11.4 IP masquerading 369
11.4.1 Simple masquerading 370
11.4.2 Inverse masquerading 372
11.4.3 Free translation of TCP/IP ports on masked connections
375
11.4.4 De-Militarized Zone (DMZ) 376
11.4.5 Unmasked Internet access for server in the DMZ 377
11.5 Demilitarized Zone (DMZ) 379
11.5.1 Assigning interfaces to the DMZ 379
11.5.2 Assigning network zones to the DMZ 380
11.5.3 Address check with DMZ and intranet interfaces 381
11.6 Advanced Routing and Forwarding 382
11.6.1 Introduction 382
11.6.2 Defining networks and assigning interfaces 386

10 BAT54-Rail/F..
Release
7.54
06/08
11.7 Changes in other services 391
11.7.1 DHCP server 391
11.7.2 DHCP relay server 398
11.7.3 NetBIOS proxy 399
11.7.4 RIP 400
11.7.5 Automatic generation of VPN rules 406
11.7.6 Firewall rules for certain local networks 407
11.7.7 Virtual routers 408
11.7.8 Default routes filter 409
11.7.9 Extended port forwarding 410
11.7.10 IPX router 412
11.7.11 Assigning logical interfaces to bridge groups 413
11.7.12 Remote bridge 414
11.7.13 PPPoE Servers 415
11.8 Load balancing 415
11.8.1 DSL port mapping 417
11.8.2 Direct DSL channel bundling 420
11.8.3 Dynamic load balancing 420
11.8.4 Static load balancing 421
11.8.5 Configuration of load balancing 422
11.9 N:N mapping 425
11.9.1 Application examples 426
11.9.2 Configuration 430
11.10 Establishing connection with PPP 434
11.10.1 The protocol 434
11.10.2 Everything o.k.? Checking the line with LCP 436
11.10.3 Assignment of IP addresses via PPP 437
11.10.4 Settings in the PPP list 438
11.11 DSL Connection with PPTP 439
11.12 Extended connection for flat rates—Keep-alive 440
11.13 Callback functions 440
11.13.1 Callback for Microsoft CBCP 441
11.13.2 Fast callback 442
11.13.3 Callback with RFC 1570 (PPP LCP extensions) 443
11.13.4 Overview of configuration of callback function 443

BAT54-Rail/F..
Release
7.54
06/08 11
11.14 serial interface 444
11.14.1 Introduction 444
11.14.2 System requirements 445
11.14.3 Installation 445
11.14.4 Set the serial interface to modem operation 446
11.14.5 Configuration of modem parameters 447
11.14.6 Direct entry of AT commands 449
11.14.7 Statistics 450
11.14.8 Trace output 450
11.14.9 Configuration of remote sites for V.24 WAN interfaces
450
11.14.10 Configuration of a backup connection on the serial in-
terface 452
11.14.11 Contact assignment of BAT modem adapter kit 453
11.15 Manual definition of the MTU 453
11.15.1 Configuration 454
11.15.2 Statistics 454
11.16 WAN RIP 454
11.17 The rapid spanning tree protocol 456
11.17.1 Classic and rapid spanning tree 457
11.17.2 Improvements from rapid spanning tree 457
11.17.3 Configuring the Spanning Tree Protocol 458
11.17.4 Status reports via the Spanning Tree Protocol 461
12 More services 465
12.1 Automatic IP address administration with DHCP 465
12.1.1 The DHCP server 465
12.1.2 DHCP—'on', 'off', 'auto', 'client' or 'forwarding'? 466
12.1.3 How are the addresses assigned? 467
12.2 Vendor Class and User Class Identifier on the DHCP Client 472
12.3 DNS 473
12.3.1 What does a DNS server do? 473
12.3.2 DNS forwarding 474
12.3.3 Setting up the DNS server 475
12.3.4 URL blocking 478
12.3.5 Dynamic DNS 479
12.4 Accounting 481

12 BAT54-Rail/F..
Release
7.54
06/08
12.5 The SYSLOG module 484
12.5.1 Setting up the SYSLOG module 484
12.5.2 Example configuration with LANconfig 484
12.6 Time server for the local net 486
12.6.1 Configuration of the time server under LANconfig 487
12.6.2 Configuration of the time server with WEBconfig or Telnet
488
12.6.3 Configuring the NTP clients 488
12.7 Scheduled Events 491
12.7.1 Regular Execution of Commands 491
12.7.2 CRON jobs with time delay 492
12.7.3 Configuring the CRON job 493
12.8 PPPoE Servers 495
12.8.1 Introduction 495
12.8.2 Example application 495
12.8.3 Configuration 498
12.9 RADIUS 500
12.9.1 How RADIUS works 502
12.9.2 Configuration of RADIUS as authenticator or NAS 502
12.9.3 Configuring RADIUS as server 509
12.10 Extensions to the RADIUS server 511
12.10.1 New authentication method 511
12.10.2 EAP authentication 512
12.10.3 RADIUS forwarding 513
12.10.4 RADIUS server parameters 515
12.11 RADSEC 517
12.11.1 Configuring RADSEC for the client 517
12.11.2 Certificates for RADSEC 518
13 Appendix 519
13.1 Error messages in LANmonitor 519
13.1.1 General error messages 519
13.1.2 VPN error messages 519
13.2 SNMP Traps 523
13.3 Radio channels 524
13.3.1 Radio channels in the 2,4 GHz frequency band 524
13.3.2 Radio channels in the 5 GHz frequency band 524
13.3.3 Radio channels and frequency ranges for Indoor and Out-
door operating 526

BAT54-Rail/F..
Release
7.54
06/08 13
13.4 RFCs supported 528
13.5 Glossary 529
14 Index 533

14 BAT54-Rail/F..
Release
7.54
06/08

Preface
BAT54-Rail/F..
Release
7.54
06/08 15
1 Preface
UUser manual installation and user manual configuration
The documentation of your device consists of two parts: The user manual in-
stallation and the user manual configuration.
DThe hardware of the BAT devices is documented in the respective user
manual installation. Apart from a description of the specific feature set of
the different models, you find in the user manual installation information
about interfaces and display elements of the devices, as well as instruc-
tions for basic configuration by means of the wizards.
DYou are now reading the user manual configuration. The user manual
configuration describes all functions and settings of the current version of
LCOS, the operating system of all BAT routers and BAT Router Access
Points. The user manual configuration refers to a certain software version,
but not to a special hardware.
It completes the user’s manual and describes topics in detail, which are
valid for several models simultaneously. These are for example:
DSystems design of the LCOS operating system
DConfiguration
DManagement
DDiagnosis
DSecurity
DRouting and WAN functions
DFirewall
DQuality of Service (QoS)
DVirtual Local Networks (VLAN)
DWireless Networks
DFurther server services (DHCP, DNS, charge management)

Preface
16 BAT54-Rail/F..
Release
7.54
06/08
ULCOS, the operating system of BAT devices
All BAT routers and BAT Router Access Points use the same operating sys-
tem: LCOS. The operating system is not attackable from the outside, and
thus offers high security. The consistent use of LCOS ensures a comfortable
and constant operation of all BAT products. The extensive feature set is
available throughout all BAT products (provided respective support by hard-
ware), and continuously receives further enhancements by free, regular soft-
ware updates.
This user manual configuration applies to the following definitions of soft-
ware, hardware and manufacturers:
D’LCOS’ describes the device-independent operating system
D’BAT’ stands as generic term for all BAT routers and BAT Router Access
Points
D’Hirschmann’ stands as shortened form for the manufacturer, Hirschmann
Automation and Control GmbH, Germany
UValidity
The present user manual configuration applies to all BAT routers and BAT
Router Access Points with firmware version 7.54 or better.
The functions and settings described in this user manual configuration are
not supported by all models and/or all firmware versions.
Illustrations of devices, as well as screenshots always represent just exam-
ples, which need not necessarily correspond to the actual firmware version.
USecurity settings
For a carefree use of your device, we recommend to carry out all security set-
tings (e.g. Firewall, encryption, access protection, charge lock), which are not
already activated at the time of purchase of your device. The LANconfig wiz-
ard ’Check Security Settings’ will support you accomplishing this. Further in-
formation regarding this topic can be found in chapter ’Security’ →page 237.
We ask you additionally to inform you about technical developments and ac-
tual hints to your product on our Web page www.hirschmann.com, and to
download new software versions if necessary.
UThis documentation was created by …
... several members of our staff from a variety of departments in order to en-
sure you the best possible support when using your BAT product.

Preface
BAT54-Rail/F..
Release
7.54
06/08 17
In case you encounter any errors, or just want to issue critics enhancements,
please do not hesitate to send an email directly to:
info@hirschmann.com

Preface
18 BAT54-Rail/F..
Release
7.54
06/08

System design
BAT54-Rail/F..
Release
7.54
06/08
2.1
Introduction
19
2 System design
2.1 Introduction
The BAT operating system LCOS is a collection of different software mod-
ules, the BAT devices themselves have different interfaces to the WAN and
LAN. Depending on the particular application, data packets flow through dif-
ferent modules on their way from one interface to another.
The following block diagram illustrates in abstract the general arrangement
of BAT interfaces and LCOS modules. In the course of this user manual con-
figuration the descriptions of the individual functions will refer to this illustra-
tion to show important connections of the particular applications and to
deduce the resulting consequences.
The diagram can thus explain for which data streams the firewall comes into
play, or, in case of address translations (IP masquerading or N:N mapping),
at which place which addresses are valid.
Notes regarding the respective modules and interfaces:
DThe IP router takes care of routing data on IP connections between the
interfaces from LAN and WAN.
Firewall / IDS / DoS / QoS
/ Policy Based Routing
IP router
Load Balancing
LAN bridge with “isolated mode”
Virtual LANs (VLAN)
N:N mapping
ISDN
ADSL
DSL
LAN
WLAN-1-1
to
WLAN-1-8
DMZ
DSLoL
Configuration &
management:
WEBconfig, Telnet,
TFTP
VPN / PPTP
DHCP client / PPP
IP module: NetBIOS, DNS,
DHCP server, RADIUS,
RIP, NTP, SNMP, SYS-
LOG, SMTP
IPX router
LAN interfaces
WAN interfaces
IP masquerading
VPN services
LANCAPI
Assignment via Switch
WLAN-2-1
to
WLAN-2-8
MAC/protocol filter
Filter
Filter
IPX over PPTP/VPN
Encryption:
802.11i/WPA/
IP-Redirect
BAT
user manage-
ment
RADIUS
client / server
Assignment via Switch
Assignment over Switch
Switch
Port-Mapping
LAN
DSL
DSLoL
DMZ
Assignment via Switch

System design
20
2.1
Introduction
BAT54-Rail/F..
Release
7.54
06/08
DWith IP redirect requests in the LAN are redirected to a specific computer
DThe firewall (with the services “Intrusion Detection”, “Denial of Service”
and “Quality of Service”) encloses the IP router like a shield. All connec-
tions via the IP router automatically flow through the firewall as well.
DBAT devices provide either a separate LAN interface or an integrated
switch with multiple LAN interfaces as interfaces to the LAN.
DBAT Router access points resp. BAT routers with wireless modules offer
additionally one or, depending on the respective model, also two wireless
interfaces for the connection of Wireless LANs. Depending on the model
every wireless interface can build up to eight different wireless networks
(“multi SSID”).
DA DMZ interface enables for some models a ’demilitarized zone’ (DMZ),
which is also physically separated within the LAN bridge from other LAN
interfaces.
DThe LAN bridge provides a protocol filter that enables blocking of dedicat-
ed protocols on the LAN. Additionally, single LAN interfaces can be sep-
arated by the “isolated mode”. Due to VLAN functions, virtual LANs may
be installed in the LAN bridge, which permit the operating of several logi-
cal networks on a physical cabling.
DApplications can communicate with different IP modules (NetBIOS, DNS,
DHCP server, RADIUS, RIP, NTP, SNMP, SYSLOG, SMTP) either via
the IP router, or directly via the LAN bridge.
DThe functions “IP masquerading” and “N:N mapping” provide suitable IP
address translations between private and public IP ranges, or also be-
tween multiple private networks.
DProvided according authorization, direct access to the configuration and
management services of the devices (WEBconfig, Telnet, TFTP) is pro-
vided from the LAN and also from the WAN side. These services are pro-
tected by filters and login barring, but do not require any processing by
the firewall. Nevertheless, a direct access from WAN to LAN (or vice ver-
sa) using the internal services as a bypass for the firewall is not possible.
DThe IPX router and the LANCAPI access on the WAN side only the ISDN
interface. Both modules are independent from the firewall, which controls
only data traffic through the IP router.
DThe VPN services (including PPTP) enable data encryption in the Internet
and thereby enable virtual private networks over public data connections.
DDepending on the specific model, either xDSL/Cable, ADSL or ISDN are
available as different WAN interfaces.
DThe DSLoL interface (DSL over LAN) is no physical WAN interface, but
more a “virtual WAN interface”. With appropriate LCOS settings, it is pos-
sible to use on some models a LAN interface as an additional xDSL/Ca-
ble interface.
Other manuals for BAT54-Rail
1
This manual suits for next models
2
Table of contents
Other Hirschmann Wireless Access Point manuals
Hirschmann
Hirschmann BAT450-F User manual
Hirschmann
Hirschmann BAT867-R User manual

Hirschmann
Hirschmann BAT-R User manual
Hirschmann
Hirschmann BAT54-F User manual
Hirschmann
Hirschmann BAT54-F Series User manual
Hirschmann
Hirschmann BAT series User manual
Hirschmann
Hirschmann BAT450-F User manual

Hirschmann
Hirschmann BAT54 User manual

Hirschmann
Hirschmann BAT 11b User manual

Hirschmann
Hirschmann BAT54-Rail User manual