Host computer requirements
5
ABOUT MY IRONKEY WORKSPACE W700 DEVICE
IronKey Workspace W700 User Guide
Password-Protected—Only after the user logs in with an authorized password will the drive unlock the
workspace so you can boot into Windows To Go. Do not share your password with anyone. That way, even if
your device is lost or stolen, no one else can access your data.
Self-Destruct Sequence—If the Cryptochip detects physical tampering by a hacker, or if a specified number of
consecutive incorrect password attempts have been entered, it can initiate a permanent self-destruct
sequence that securely erases all onboard data—so remember your password.
Waterproof and Tamper-Resistant—Designed to survive the extremes, IronKey Workspace W700 has a
rugged metal encasing that is injected with an epoxy compound that makes it not only tamper-resistant, but
waterproof to military specifications (MIL-STD-810F).
Device Management—Your device has built-in software that lets you manage device settings. Your company
may also configure your device for centralized management with IronKey Enterprise Server. For more
information, see “Device management” on page 5.
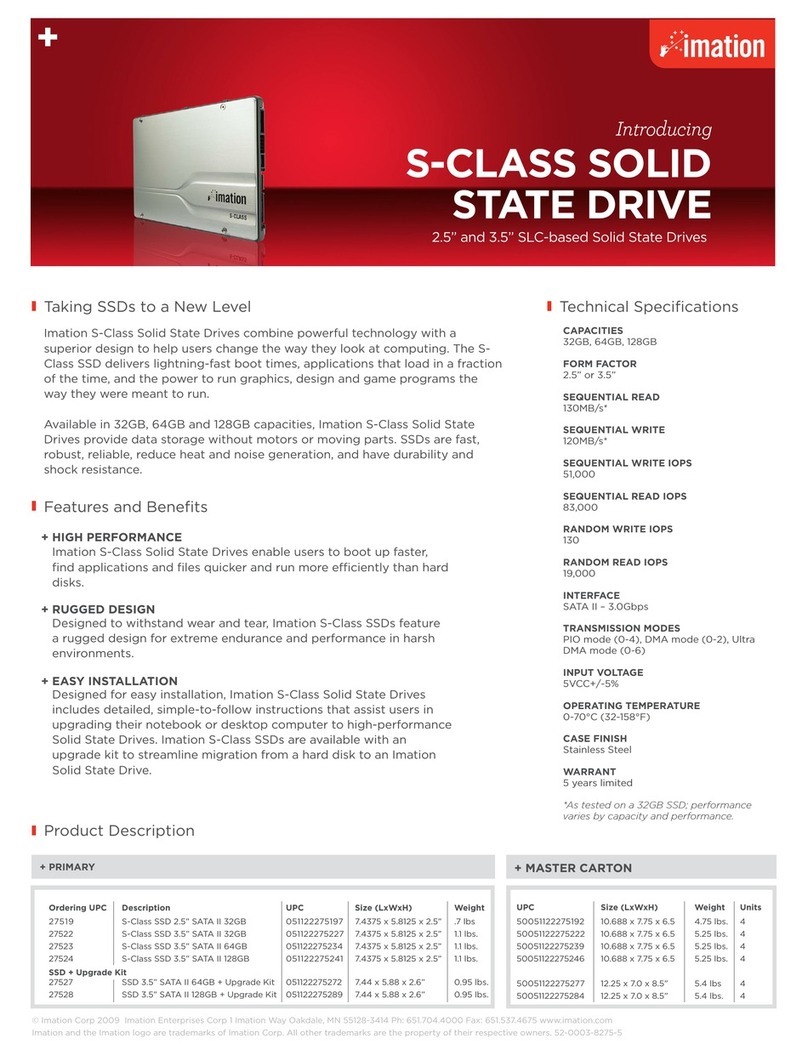
HOST COMPUTER REQUIREMENTS
The host computer must allow you to boot from a USB device. Computers that are certified for use with
Windows 7 or higher can be configured to boot automatically from a USB device. Check with the hardware
manufacturer if you are not sure whether your computer can boot from a USB device. For more information,
see “Booting from a USB drive” on page 14.
• Windows computer that is certified for Microsoft Windows®7 or higher.
• Macintosh computer that supports Windows 8 or higher. Note: You r W700 device must also have
Boot Camp Support Software installed in Windows To Go. Your administrator may have included
this software when your device was provisioned. For more information, see “Booting from a Mac
computer” on page 18.
• USB 3.0 or USB 2.0 port for high-speed data transfer. USB 3.0 ports are typically marked blue or dis-
play the “SS” (Super Speed) symbol. A USB 1.1 port or powered hub will also work, but will be slower.
DEVICE MANAGEMENT
There are two kinds of device management: at the administrative level and at the user level. At the
administative level, your organization can implement IronKey Enterprise Server, a device management system,
to control the policy on your device and provide device updates as well as control access to the device.
Devices controlled by IronKey Enterprise Server are called “Managed devices”. Your administrator will tell you if
you have a managed device.
User management refers to the management options available to you, the user, to control your device. Each
device, whether managed by IronKey Enterprise Server or unmanaged, includes the IronKey Control Panel
application that lets you change device settings, such as your password.
Administrative management
IronKey Enterprise Server is an on-premise server solution that allows IT administrators to remotely manage
your IronKey Workspace W700 device. Devices that are provisioned for Enterprise management are called
“managed devices”. If you have a managed device, you must first activate it before you use Windows To Go.
Activation binds the device to your user account on IronKey Enterprise Server and applies a device policy.
Once activated, your device can receive policy and software updates, and administrators can reset a forgotten
password.