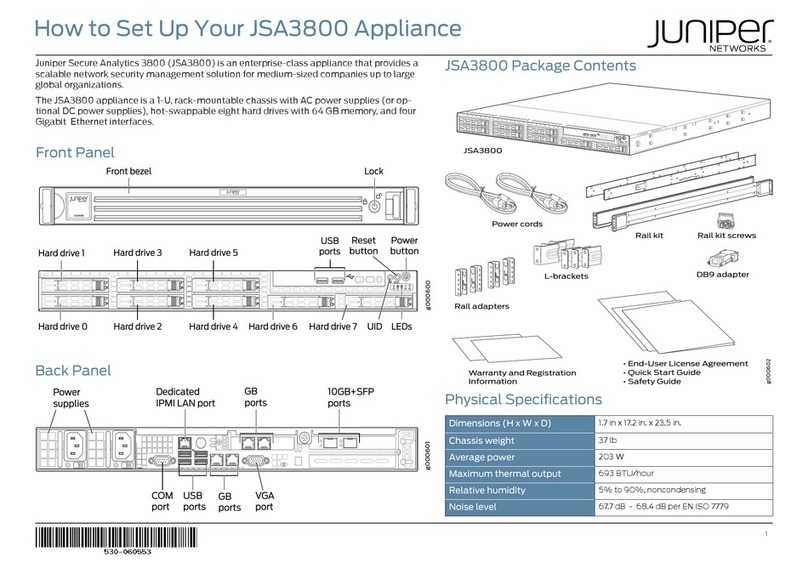
2
Copyright Notice
Copyright © 2013 Juniper Networks, Inc. All rights reserved.
Juniper Networks, Junos, Steel-Belted Radius, NetScreen, and ScreenOS are registered trademarks of Juniper Networks, Inc. in the United States and
other countries. The Juniper Networks Logo, the Junos logo, and JunosE are trademarks of Juniper Networks, Inc.
The following terms are trademarks or registered trademarks of other companies:
JavaTM and all Java-based trademarks and logos are trademarks or registered trademarks of Oracle and/or its affiliates.
All other trademarks, service marks, registered trademarks, or registered service marks are the property of their respective owners.
All specifications are subject to change without notice. Juniper Networks assumes no responsibility for any inaccuracies in this document or for any
obligation to update information in this document. Juniper Networks reserves the right to change, modify, transfer, or otherwise revise this publication
without notice.
FCC Statement
The following information is for FCC compliance of Class A devices: This equipment has been tested and found to comply with the limits for a Class A
digital device, pursuant to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the
equipment is operated in a commercial environment. The equipment generates, uses, and can radiate radio-frequency energy and, if not installed and
used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential
area is likely to cause harmful interference, in which case users will be required to correct the interference at their own expense. The following
information is for FCC compliance of Class B devices: The equipment described in this manual generates and may radiate radio-frequency energy. If it
is not installed in accordance with Juniper Networks’ installation instructions, it may cause interference with radio and television reception. This
equipment has been tested and found to comply with the limits for a Class B digital device in accordance with the specifications in part 15 of the FCC
rules. These specifications are designed to provide reasonable protection against such interference in a residential installation. However, there is no
guarantee that interference will not occur in a particular installation. If this equipment does cause harmful interference to radio or television reception,
which can be determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one or more of the following
measures: Reorient or relocate the receiving antenna. Increase the separation between the equipment and receiver. Consult the dealer or an
experienced radio/TV technician for help. Connect the equipment to an outlet on a circuit different from that to which the receiver is connected.
Caution: Changes or modifications to this product could void the user's warranty and authority to operate this device.
Disclaimer
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT, SUBJECT TO THE MODIFICTAIONS SET FORTH
BELOW ON THIS PAGE, ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED
HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR
JUNIPER NETWORKS REPRESENTATIVE FOR A COPY.
STRM Troubleshooting Guide
Release 2013.2
Copyright © 2013, Juniper Networks, Inc.
All rights reserved. Printed in USA.
Revision History
July 2013—STRM Troubleshooting Guide
The information in this document is current as of the date listed in the revision history.
END USER LICENSE AGREEMENT
The Juniper Networks product that is the subject of this technical documentation consists of (or is intended for use with) Juniper Networks software. Use
of such software is subject to the terms and conditions of the End User License Agreement (“EULA”) posted at http://www.juniper.net/support/eula.html,
as modified by the following text, which shall be treated under the EULA as an Entitlement Document taking precedence over any conflicting provisions
of such EULA as regards such software:
As regards software accompanying the STRM products (the “Program”), such software contains software licensed by Q1 Labs and is further
accompanied by third-party software that is described in the applicable documentation or materials provided by Juniper Networks.