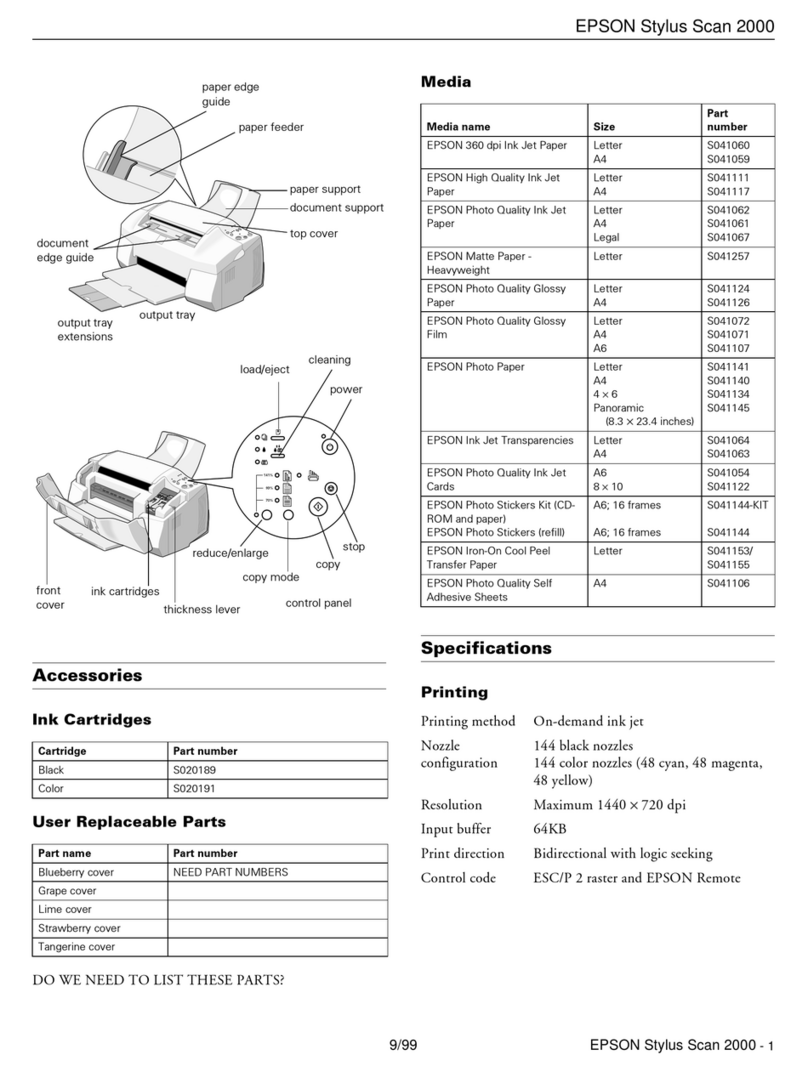
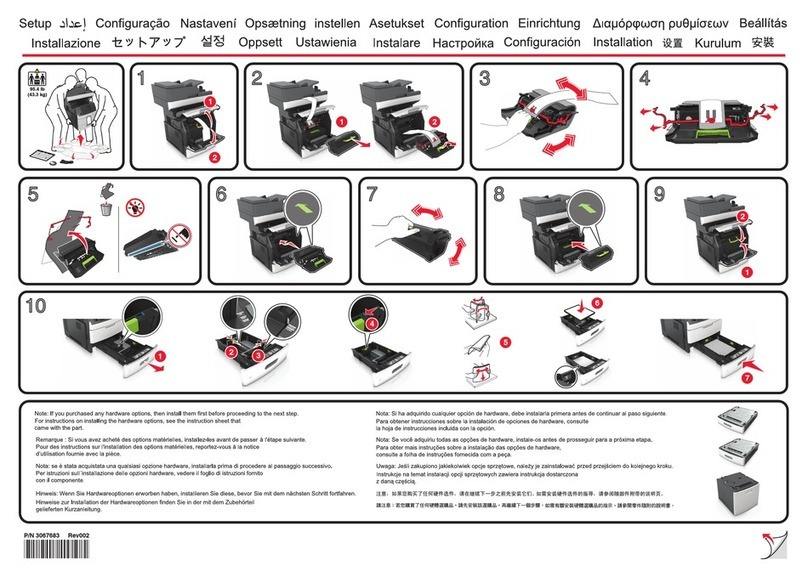
Chapter 2 Management
List of Machine Management Settings..................................................................2-2
Setting Security Codes..............................................................................................2-4
Setting the Administrator Password......................................................................2-4
Setting the Protect Passcode ..................................................................................2-7
Closed Communication ...........................................................................................2-10
Setting Closed Transmission ................................................................................2-10
Setting Closed Reception ......................................................................................2-11
Setting Passcode Polling .......................................................................................2-12
Setting the Passcode .............................................................................................2-14
Communication and Range of Passcodes .............................................................2-15
Setting ID Check Transmission ............................................................................2-17
Confirming the Destination Before Transmission............................................2-19
Setting the Destination Confirmation Function..................................................2-19
Setting the Confirmation Dial Functions ............................................................2-20
Prohibiting Transmission to Multiple Destinations ........................................2-23
Security Reception...................................................................................................2-24
Activating the PIN mask.........................................................................................2-26
Function Protect Settings ......................................................................................2-28
Setting Function Protection..................................................................................2-29
Using Function Protection....................................................................................2-31
Setting Mode Protection.........................................................................................2-33
Setting User Authentication ..................................................................................2-35
Setting the Authentication Method......................................................................2-35
Managing User Access/Cost Accounting .............................................................2-38
Setting the Currency Unit ....................................................................................2-38
Specifying the Charge Settings ............................................................................2-40
Erasing the Accounting Data ...............................................................................2-42
Specifying the Network Settings..........................................................................2-43
Specifying the TCP/IP Settings ............................................................................2-46
Registering LDAP Servers....................................................................................2-57
Specifying the Archive Settings............................................................................2-69
Setting an E-mail Gateway ..................................................................................2-73
Setting the Automatic Logout Time .....................................................................2-76
Mirroring the Machine Settings ...........................................................................2-78
Mirroring Methods ................................................................................................2-78
Importing / Exporting Using USB Memory.........................................................2-79
Directly Copying Via the Network .......................................................................2-84